Lee Archinal
@ArchinalLee
Followers
606
Following
6K
Media
105
Statuses
3K
Log junkie trying to share what I know through training and posts. Privileged to be a #BlackHatUSA trainer!
Some SIEM/EDR/XDR
Joined June 2019
Super fun working on this lab with the @XintraOrg gang!! Enjoy and let us know your feedback! #ScatteredSpider #MuddledLibra #UNC3944
NEW LAB: Scattered Spider (UNC3944) 🕷️🕸️ Scattered Spider hits indie studio AB Projekt Blue, deploying ransomware and stealing unreleased game code. Test your skills on: 👀 Social Engineering & MFA Fatigue 👀 Credential Theft via OST Files 👀 Bring Your Own Vulnerable Driver
2
4
41
How do #malware behaviors inform hunt strategy? Find out July 31 in Intel 471’s live, hands-on workshop. Real telemetry, real IOAs, guided by our #threatintel and #threathunting teams. Sign up: https://t.co/xPDKlbYsRQ
#cybersecurity #CTI
0
2
5
Intel 471: This post will examine one of the top pro-Russian hacktivist groups, new ones that have entered the scene and the impact of these groups. https://t.co/xjqeRWKfY5
@Intel471Inc
2
25
41
🚨 New Threat Actor Profile by @intel_anastasia From the shadows of Conti, Black Basta emerged as one of the most prolific ransomware gangs in recent years—until a massive internal leak exposed everything. 🔍 In our latest profile, we trace the group’s Conti lineage, breakdown
0
13
30
🌟New report out today!🌟 Hide Your RDP: Password Spray Leads to RansomHub Deployment Analysis and reporting completed by @tas_kmanager, @iiamaleks and UC2 🔊Audio: Available on Spotify, Apple, YouTube and more! https://t.co/jL4oy28kS0
thedfirreport.com
Key Takeaways Initial access was via a password spray attack against an exposed RDP server, targeting numerous accounts over a four-hour period. Mimikatz and Nirsoft were used to harvest credential…
1
38
113
Check out this opportunity to work with an awesome team! #ThreatHunting #ThreatIntel
🔎 We're Hiring: Senior Security Analyst We're looking for a full-time Senior Security Analyst with a passion for dissecting intrusions and translating technical findings into actionable insights. Check out the full job description and apply here 👉
0
1
2
CTI teams are under pressure to mature fast. In this #SANS webcast, Intel 471’s Ashley Jess shares insights on integrating #geopolitics and measuring CTI value using frameworks like CTI-CMM & CU-GIRH. Watch the full discussion: https://t.co/q1F8RuJEOH
#CTI #cybersecurity
intel471.com
The SANS Institute has released its SANS 2025 CTI Survey report, an influential pulse-check of cyber threat intelligence (CTI) trends, challenges, and use cases. On May 21, 2025, Ashley Jess, a...
0
6
27
🚨Kroger cybersecurity is hiring! Check out the postings here: https://t.co/RWaq7jZgzZ
#cyberjobs #hiring
9
34
91
Join Intel 471's Level 2 Threat Hunting Workshop on Execution tomorrow, May 14 from 12 - 1 PM EDT. Investigate PowerShell abuse, LOLBins, macro payloads, and more using real-world data. Finish the challenge, earn your #threathunting badge. Register now: https://t.co/z5dsi27bvk
0
1
5
📉DFIR Labs Weekend Discount📉 Use this discount code to receive 10% off all DFIR Labs cases! Discount expires May 5th 04:00 UTC ⏲️Buy now, use anytime over the next 3 months. ➡️Discount code: WeekendDiscount20250502 Access DFIR Labs:
store.thedfirreport.com
Explore Real-World Cybersecurity Intrusions with Our Interactive DFIR Labs Our cloud-based DFIR (Digital Forensics and Incident Response) Labs offer a hands-on learning experience, using real data...
0
12
37
🌟New report out today!🌟 Navigating Through The Fog Analysis and reporting completed by @angelo_violetti, and reviewed by @svch0st. Audio: Available on Spotify, Apple, YouTube and more! https://t.co/aN5xFoYATD
thedfirreport.com
Key Takeaways An open directory associated with a ransomware affiliate, likely linked to the Fog ransomware group, was discovered in December 2024. It contained tools and scripts for reconnaissance…
0
34
76
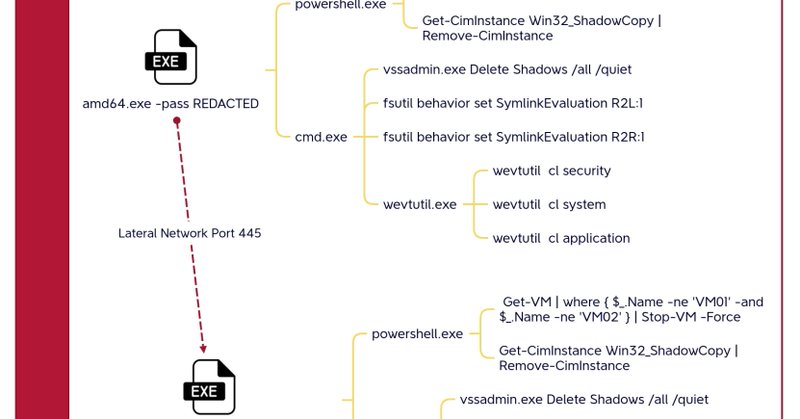
“For this case we observed TXT records being utilized for C2 communication rather than MX records. This can be identified by the "type: 16" in the Sysmon logs seen above. Below is a sample list that, while not exhaustive, provides a clear example of the traffic patterns:” 1/2
2
28
134
#Cybersecurity truly is a collaborative endeavor. We asked Steve Orrin from @intel to share his insights on how the government and commercial sides can work together to stay ahead of #CYBER threats. #informationsecurity
0
1
1
🚨 VanHelsing Ransomware hit 3 victims within weeks of launch. Cross-platform, $500K ransoms, and growing fast. Intel 471 is tracking it, read the full report: https://t.co/ejkEhQkrIt
#vanhelsing #ransomware #emergingthreats #threathunting #cybersecurity
0
3
4
Happy Monday everyone! Here is your #readoftheday! Source: @cyfirma
https://t.co/R26xRN71Mf A nice collection of #TTPs and #behaviors associated with #VoltTyphoon! Enjoy and #HappyHunting
@Intel471Inc @CyborgSecInc #ThreatIntel #ThreatHunting
cyfirma.com
Volt Typhoon is a Chinese state-sponsored hacker group that has been targeting critical infrastructure in the United States and other...
0
1
2
LockBit 4.0 enhances its stealth with PowerShell abuse, security feature bypasses, and obfuscated exfiltration. Intel 471 tracks its evolving tactics, read the full report here: https://t.co/GBiTWciNxn
#emergingthreat #lockbit #threathunting #threatintel
0
6
14
Threat hunting is about focus. Knowing where to spend your time is what sets tactical hunters apart. Join Out of the Woods live tomorrow for an interactive discussion on what drives real results. Our hosts will be engaging in real time on Discord. 🔗 https://t.co/y6JvJqWule
0
2
3