security_dumpster
@securitydumpstr
Followers
149
Following
158
Media
4
Statuses
73
303: @ https://t.co/I4aYuNOKKY Life long snowboarder and opportunist threat hunter | my views are my own
Joined July 2023
RT @SophosXOps: Sophos analysts are investigating a new infection chain for the GOLD BLADE cybercriminal group’s custom RedLoader malware,….
0
7
0
RT @SophosXOps: Sophos MDR has observed 2 distinct social engineering campaigns using a technique referred to as ClickFix spiking during M….
0
8
0
RT @SophosXOps: In November, Sophos MDR noted a rapid decline in detections for the Rockstar2FA phishing as a service platform. Its rise wa….
trustwave.com
Trustwave SpiderLabs has been actively monitoring the rise of Phishing-as-a-Service (PaaS) platforms, which are increasingly popular among threat actors.
0
4
0
Just put out this research on MiTM PaaS kits Rockstar/ FlowerStorm. While my name is on this, the primary researchers Josh Rawles (@ig3thack3d4u ) and Jordon Olness deserve the lions share of credit. They’re both brilliant to work with and hats off to them
news.sophos.com
A sudden disruption of a major phishing-as-a-service provider leads to the rise of another…that looks very familiar
0
2
4
My (and my copresenter Colin Cowie) @MSFTBlueHat talk “Patterns in the Shadows: Scaling Threat Hunting and Intelligence for the Modern Adversary” is on YouTube, hope you enjoy!
0
0
5
RT @DrAzureAD: My @MSFTBlueHat talk "Deprecating Azure AD Graph API is Easy and Other Lies We Tell Ourselves" is now on Youtube! .Link to r….
0
39
0
RT @LabsSentinel: 🔥 New from @philofishal , @syrion89 and @TomHegel:. 🇰🇵 BlueNoroff Hidden Risk | Threat Actor Targets Macs with Fake Crypt….
sentinelone.com
SentinelLABS has observed a suspected DPRK threat actor targeting Crypto-related businesses with novel multi-stage malware.
0
20
0
RT @ElbridgeColby: "China’s ‘mind-boggling’ space capabilities worry US, says Space Force chief. Beijing’s tech is more concerning than rep….
politico.eu
Beijing’s tech is more concerning than reports of Russian space nukes, said General B. Chance Saltzman.
0
50
0
RT @Glacius_: Hey :). We published a blog talking about ORB networks and a summarise of the purpose, use cases and more:. .
team-cymru.com
Explore how threat actors use Operational Relay Box (ORB) networks to evade detection, hide malicious activity, and complicate cyber defense efforts. Talk to an expert.
0
27
0
RT @naksyn: This has been one of my favorites for a while, but now it's time to let it go. Here's my preferred way of getting the KeePass d….
0
51
0
RT @a_greenberg: Sophos detailed to me its 5-year cat-and-mouse game with Chinese hackers repeatedly exploiting its firewalls. The company….
wired.com
Sophos went so far as to plant surveillance “implants” on its own devices to catch the hackers at work—and in doing so, revealed a glimpse into China's R&D pipeline of intrusion techniques.
0
468
0
RT @BushidoToken: Recent trick related to .RDP files used by the SVR 🇷🇺 is worth threat hunting for. Basically they’re doing what this @B….
0
80
0
RT @decoder_it: OK, I promise to stop spamming about relays with NTLM/Kerberos 😅. But if you're a member of the Distributed COM or Performa….
0
75
0
Great approach’s lined out👇, highly recommend the read.
📢Topic: Threat Hunting Metrics. I've said this before, and I'll say it again because it pains me to see teams with talented individuals compelled to use this poor metric as a KPI. 🚨The Hunt count number per Hunter is a BAD metric!!🚨. As I previously wrote about it in a blog.
0
0
2
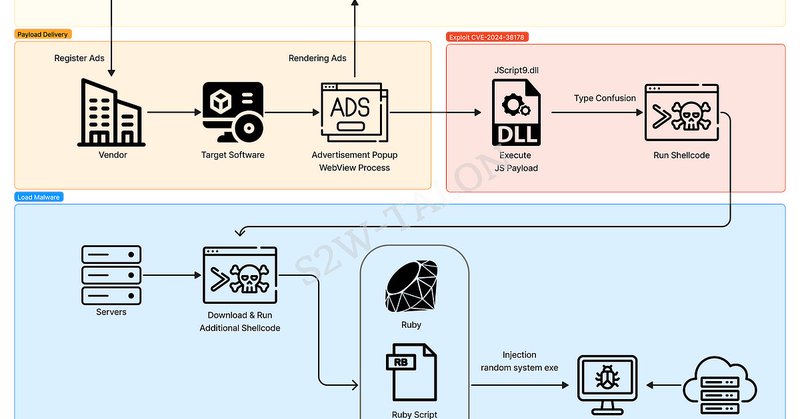
RT @2RunJack2: 🚨 ITW Zero-Day Vulnerability Discovery: #APT37 (#Scarcruft) 🚨. For Responsible Disclosure, we disclose relevant details at t….
medium.com
Author: Hosu Choi, Minyeop Choi | S2W Talon
0
12
0
RT @evstykas: My DEF CON 32 talk "Behind Enemy Lines: Engaging and Disrupting Ransomware Web Panels" is up on YouTube!..
0
16
0
RT @MSFTBlueHat: 📣SPEAKER ANNOUNCEMENT📣. We're excited to announce our next #BlueHat speakers: Mark Parsons (@securitydumpstr) and Colin Co….
0
1
0
RT @Maxwsmeets: The calendar for the Fall/Winter Virtual Research Workshop Series is out: .
virtual-routes.org
We tackle the impact of digital and emerging technologies on global affairs
0
6
0