Andy Greenberg (@agreenberg at the other places)
@a_greenberg
Followers
70,762
Following
1,121
Media
452
Statuses
8,935
WIRED writer, author of SANDWORM and now TRACERS IN THE DARK: The Global Hunt for the Crime Lords of Cryptocurrency. Andy.01 on Signal. agreenberg @wired .com
New York
Joined April 2007
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Rio Grande do Sul
• 271028 Tweets
Madonna
• 179326 Tweets
Ole Miss
• 99839 Tweets
DAVI NO PODPAH
• 99268 Tweets
Sony
• 99092 Tweets
Porto Alegre
• 79629 Tweets
Star Wars
• 74103 Tweets
#SmackDown
• 67575 Tweets
Hope Hicks
• 65127 Tweets
みどりの日
• 47120 Tweets
スパコミ
• 43243 Tweets
WNBA
• 36846 Tweets
Mark Hamill
• 36427 Tweets
#TheAmazingDigitalCircus
• 33719 Tweets
Keyshia
• 25521 Tweets
Thiago Silva
• 18939 Tweets
Quintana
• 17921 Tweets
#Maythe4thBeWithYou
• 16033 Tweets
設営完了
• 15619 Tweets
Pomni
• 13485 Tweets
Caitlin Clark
• 12632 Tweets
Benedetti
• 11766 Tweets
Luke Skywalker
• 10425 Tweets
G7最下位の70位
• 10316 Tweets
Last Seen Profiles
I interviewed
@DDoSecrets
cofounder Emma Best about
#BlueLeaks
, 269 gigs of files from 200+ law enforcement orgs, given to Best's secret-spilling group by a source aligned w/ Anonymous. Likely the most significant Anonymous operation in nearly a decade.
26
880
2K
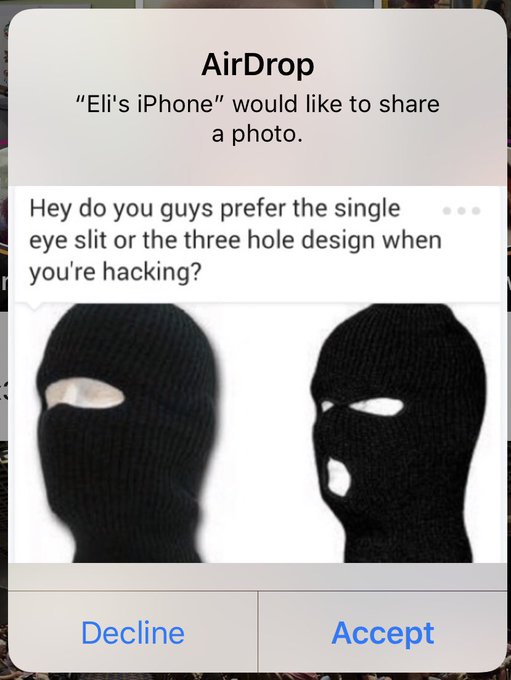
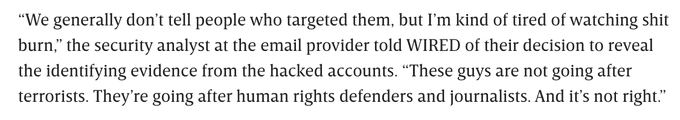
As simple as that giveaway might sound, finding it required
@SentinelOne
mapping out the whole hacking campaign, and one very badass source at an email provider coming forward with the key info.
5
409
1K
I went to Ukraine to tell this
@wired
cover story, behind the blackout-inducing cyberattacks plaguing the country:
56
1K
1K
All this Bellingcat-style attribution work is very fun and gratifying to be involved in. But the focus should remain on the defendants in the case, known as the Bhima Koregaon 16. Of those 16, 13 are in jail. One, 84-year-old priest Stan Swamy, died there. As
@juanandres_gs
says:
15
399
1K
Citizen Lab's
@jsrailton
went a step further: He added the official's number as a contact in WhatsApp, and found his profile included a selfie pic. The face in the pic matched photos of the man at police press conferences and even a news photo taken at one the activist's arrests.
3
330
987
US gov agencies are warning of a new malware toolkit that can target industrial control systems (ICS) from power grids to oil & gas. Dragos calls it "Pipedream," and
@cnoanalysis
says it’s "the most expansive ICS attack tool anyone has ever documented."
57
669
984
To confirm the police official's identity,
@0xzeshan
then found the email and phone number the official had added to the hacked accounts in multiple breached/leaked databases and an archived version of the Pune Police website.
1
295
945
Confirming
@briankrebs
reporting that Chinese group Hafnium has now exploited Microsoft Exchange zero-days to hack tens of thousands of networks. One researcher says 30k servers in the US alone, hundreds of thousands globally. "China just owned the world."
36
746
907
My book Sandworm, on Russia's years-long cyberwar in Ukraine, has spiked in sales since Russia's full-scale invasion began. So I'm donating royalties for the first half of 2022 to Ukrainian victim aid non-profits. (ht to
@anneapplebaum
who set the example)
35
206
879
Huge shift: In 2015/2016, blackouts Russia's GRU hackers caused in Ukraine took US gov *years* to attribute publicly. NotPetya, GRU's global cyberattack that massively affected Americans in 2017, took 8 months. Now GRU sneezes and it's called out in days.
117
290
793
Ars Technica's
@dangoodin001
is one of the most technically knowledgeable reporters I know. Now he's being sued by Keeper Security for writing up a report of Keeper's software vulnerabilities made by a Google researcher. This is gross, litigious bullying.
23
487
723
Final thanks to all who contributed to this truly collaborative work:
@ArsenalArmed
, who proved the original evidence fabrication,
@TomHegel
&
@juanandres_gs
who will be speaking on this at Black Hat,
@amnesty
,
@citizenlab
,
@jsrailton
,
@0xZeshan
, and one unnamed security analyst.
8
132
491
@SCFGallagher
@caitlin__kelly
Her best friend is a giant blue ox and she brushes her teeth with pine trees. Once she got so sad she dropped her ax and dragged it behind her, creating the Grand Canyon.
0
10
443
For the first time, Signal has released a breakdown of its costs, which will reach $50 million a year by 2025. Its president
@mer__edith
says this isn’t just an appeal for donations. It’s a way to highlight the surveillance profit model they’re up against.
11
197
450
Just when you start to worry that
@moxie
might have lost his cyberpunk edge as CEO of the relatively grown-up non-profit behind Signal, he lays hands on a Cellebrite device that "fell off a truck," hacks it and demos the bugs in a Hackers-themed video:
9
121
435
Feds have arrested the admin of Bitcoin Fog, the longest-running dark web Bitcoin-laundering service. It helped hide $336M over 10 years. How'd they find him? With exactly the follow-the-money techniques his service was meant to defeat. h/t
@SeamusHughes
!
13
229
427
Dutch researcher
@0Xiphorushas
has detailed a new physical access technique that could let hackers break into any of millions of PCs via their Thunderbolt ports. The good news is it requires unscrewing the case briefly. The bad news is it's unpatchable.
12
271
431
This weekend, pro-Russian saboteurs halted more than 20 Polish trains, possibly to hamper Ukraine's war effort.
@LukOlejnik
figured out how they did it: A "radio-stop" command anyone can broadcast at a certain frequency with as little as $30 of equipment.
12
204
425
This piece, the longest Wired has published in the magazine in over a decade, is paywall-free for one more day.
(Also, hope it makes you want to subscribe to Wired so my colleagues and I can have jobs.)
12
132
388
P4x wants to send a message not only to NK to stop targeting US hackers (see
@lilyhnewman
from last year ) but also to US agencies he feels have done little to support/protect targeted individuals: “If no one’s going to help me, I’m going to help myself."
6
76
360
Big thing
#1
to me: After more than two years of silence from governments around the world on the "Olympic Destroyer" cyberattack that sabotaged the 2018 Winter Olympics in Korea () the US has finally (!) blamed Russia and condemned the attack.
13
127
351
Big thing
#2
: Three-plus years after Sandworm unleashed NotPetya, the worst cyberattack in history () the US has named 4 men directly involved, even noting how Andrienko & Pliskin "celebrated" afterwards. A kind of accountability that's long been lacking.
10
143
317