Ian Campbell
@neurovagrant
Followers
2K
Following
16K
Media
2K
Statuses
53K
Security ops engineer and researcher for @DomainTools, writer, voracious reader. he/him. Opinions here mine only. Autistic/depressed/anxious/hungry.
Massachusetts
Joined January 2009
This is a stand out part of this piece by @tqbf for me. Prompt Engineering is kind of a fluff word at this point. But Context Engineering is where I spend most of my time. I've been talking to @DanielMiessler about everything boiling down to context and scaffolding for a bit
3
2
14
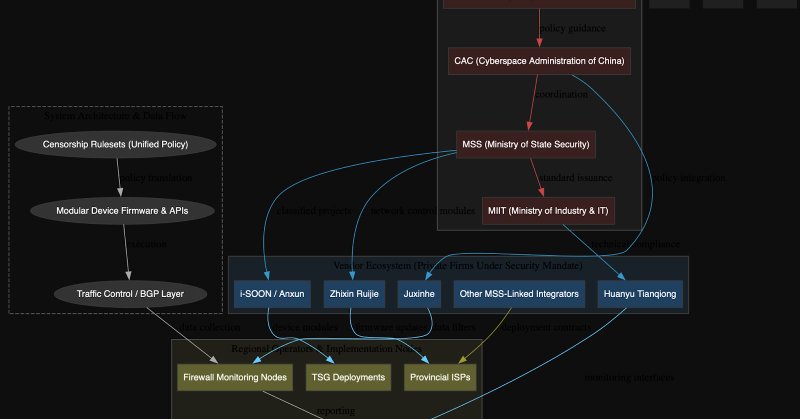
Part 2 of @DomainTools research is out: Inside the Great Firewall Part 2: Technical Infrastructure https://t.co/RrCCR3muN3
dti.domaintools.com
See the Great Firewall's technical blueprint. DomainTools Investigations details the TSG core, packet interception methods, and routines that detect tools like V2Ray/Psiphon.
0
23
83
I've been watching the Vertex analysts game this out, and I have to say... It's gonna be LIT 💚
Join us the day before @CYBERWARCON (Nov 18) for a hands-on Synapse challenge! Investigate a real-world data theft scenario, eat snacks, & earn bragging rights + our first-ever custom challenge coin. https://t.co/9eDea63rpy
0
4
8
My team's Great Firewall dump deep dive part 2, on the GFW technical infrastructure, is now up! As before, not my research, but reading and editing it and going through the details left me shaken as far as capabilities go. #geopolitics #cybersecurity
🧵DTI researchers leveraged the leaked data from China’s Great Firewall to map the core design of the censorship stack in Part 2 of Inside the Great Firewall. Read the technical deep dive here: https://t.co/HHLs1OG0hM
#Cybersecurity #ThreatIntel #China #GreatFirewall
0
0
2
Microsoft casually patched CVE-2025-59287 last week, which is an easy to find & exploit pre-auth RCE in the WSUS! Mind that, vulnerable versions go back to 2012 (oldest still supported OS ver.). Yeah Microsoft invented SDLC yada yada, but can someone explain that? It's not even a
3
17
129
Shout out to Silobreaker for putting out *really* well-done weekly geopolitical briefs that provide substantial, timely, and relevant analysis without feeling like a chore to make time for. #threatintel #infosec #cybersecurity
https://t.co/QZCqxJAweN
https://t.co/fm2aydUHwb
linkedin.com
The Silobreaker Geopolitical Risk briefs cover the latest geopolitical trends and potential risks.
0
0
0
Hey folks, just a reminder I'll be at BSides NoVA this weekend, giving a talk on DNS and domain intel in investigative journalism! It's an intersection of passions for me, so I'm wicked excited. https://t.co/TK6vemSg8O
bsidesnova-2025.sessionize.com
Across two businesses, dozens of training sessions, and hundreds of grants for access, we’ve spent more than a decade enabling the use of DNS and domain intelligence for investigative journalists....
0
0
0
This Phrack timeline of the Kimsuky dump is wiiiiiiild. https://t.co/XtUN8c1IQF (we did some deeper analysis of the dump, linked below, but wow...) ( https://t.co/7vVR7VncAb )
0
1
1
If you need something to read this morning, we published research on Friday around an activity cluster targeting 18+ interests, especially gambling and porn. Well. Also tax websites. Which I suppose is an adult interest. Sigh. #threatintel #infosec
https://t.co/EoFM9cDEC3
dti.domaintools.com
Starting in September 2024, a financially motivated cluster of more than 80 spoofed domain names and lure websites began targeting users with fake applications and websites themed as government tax...
0
0
0
Prompt||GTFO events have been extremely educational for me as an AI skeptic, as well as fun and entertaining. Worth checking them out. Google Form for getting the invite (or applying to present): https://t.co/Pbjyg6cUfN LinkedIn post with more info: https://t.co/tDNKBiWbtv
linkedin.com
Agenda for our upcoming episode this Thursday, the 9th. Michael Brown and Riccardo Schirone from Trail of Bits will be joining us to discuss their AIxCC tools and code. To watch live/submit a talk,...
0
0
0
We been doin some fun stuff lately even more fun stuff coming soon. Feels like I've reached a place where around every corner lies a fascinating rabbit-hole, especially thanks to my teammates.
New from DTI: A financially-motivated cluster of spoofed domains disguised as age 18+ social media content, government tax sites, consumer banking, and online gambling apps targeting Windows and Android users. Learn more ⬇️ https://t.co/D4HMH0a8Mf
#Cybercrime #ThreatIntel
0
0
0
The pattern is simple: - Dev gives vague instruction - AI has production access - Literal interpretation - Catastrophic damage Your SOC won't flag it. Your SIEM won't alert. The attack comes from inside, from tools you authorized.
1
1
9
Introducing a new attack vector: AI-Induced Destruction. After a shared volume of incident responses, we can confirm: AI coding assistants are now a legitimate threat category. Not sci-fi. Not theoretical. Happening daily. Thread (1/4)
4
19
47
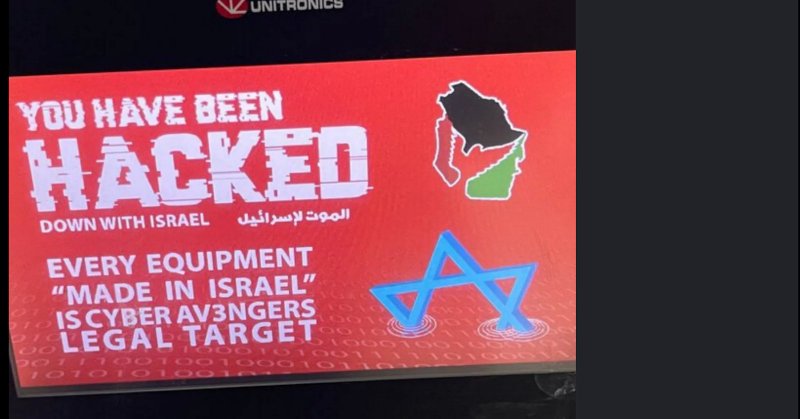
CyberAv3ngers: From Infrastructure Hacks to Propaganda Machines in the Iran-Israel Cyber War https://t.co/AYNLVbex3T
@DomainTools
dti.domaintools.com
As the conflict between Iran and Israel escalated in early 2025, it quickly expanded beyond missiles and airstrikes into a broader battle for digital and psychological dominance. Among the most...
0
8
7
Looking for smart reads & listens in cyber? @Neurovagrant shares what’s buzzing on our team’s radar this week: 🎧 @MaltegoHQ's Human Element 📚 @citizenlab 📰 @NextgovFCW 🔍 @threatinsight Full list 👉
dti.domaintools.com
Recommended cybersecurity podcasts, books, blog posts, reports, and essential tools from DomainTools Investigations
1
3
3
DTI reveals a phishing campaign targeting defense and aerospace firms linked to the Ukraine conflict. The infrastructure uses mail servers to spoof organizations and steal credentials, motivated by cyber espionage. https://t.co/uh5cArj8JT
#Ukraine #phishing #CyberEspionage
0
4
3
.@neurovagrant shares his top cybersecurity picks: podcasts, blogs, research papers, and more! Starting with "To Catch a Thief: China's Rise to Cyber Supremacy" by @nicoleperlroth. Episode 1 features @DAlperovitch. Three episodes out now! https://t.co/2ijFiNJj9M
0
4
3