Katie🌻Moussouris (she/her/she-ra/she-hulk) 🪷
@k8em0
Followers
110K
Following
268K
Media
8K
Statuses
54K
@LutaSecurity CEO @payequitynow MIT&Harvard visiting scholar, @MasonNatSec fellow, 1/2 Chamoru, hacker @k8em0.bsky.social Legacy blue check
@k8em0.bsky.social
Joined July 2008
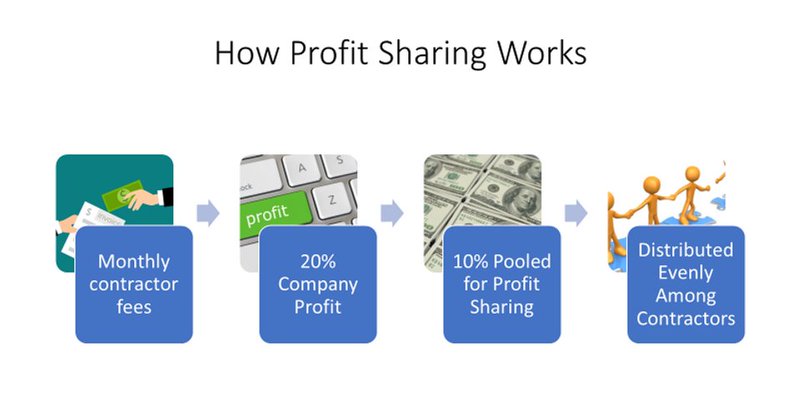
@LutaSecurity is announcing our new Workforce Platform private alpha with automatic profit-sharing, inviting US individuals & companies to apply. This is an evolution in capitalism & how we work & succeed together. Blog: Apply:
lutasecurity.com
Luta Security is inviting US based workers and companies to try their profit-sharing workforce platform alpha.
4
13
51
RT @DecipherSec: When we launched in 2018, the first piece on the site was part one of our four-part oral history of @L0phtHeavyInd. We wer….
decipher.sc
In the beginning, there was a hat factory. Factory is probably too grand a word for it, but the space that would eventually become the first home of L0p...
0
5
0
RT @LutaSecurity: @LutaSecurity is proud to be a returning sponsor for @SentinelOne @labscon_io 🌺. September 17-20, 2025. .
0
2
0
RT @bindinghook: 🎤 Speaking at #BindingHookLive: @k8em0, founder and CEO of @LutaSecurity. 📩 Request your invite: h….
0
5
0
RT @RachelTobac: It has begun: AI tools are being used to perform OSINT to determine which orgs and people to target in a hack, write infos….
0
153
0
RT @mzbat: For the record, the girlies are all still out here crushin’ it 5+ years later. 💅🏼 🔥 ❤️. @InfoSystir @snipeyhead @k8em0 @cxstephe….
0
10
0
Is lack of engagement on this platform with identical posts on other platforms getting many more genuine interactions with less than 1/6 the audience due to an algorithmic shadow ban here or bot followers or both?.
8
1
8
Who is behind. Advanced. Security. Solutions.🍑.?.
Step 1. Put up website with completely insane prices. Step 1.1 Seed the information space with flashy screenshots. Step 2. Collect free 0days from suckers thinking they’ll get millions for their hard work. Step 3. Profit. 0day > underpants gnomes.
0
0
3
RT @joernchen: Today I have a more serious topic than usual, please consider reposting for reach:. My wife and I are urgently looking for a….
0
112
0
Signs point to internal process dysfunction, especially if they fired an employee who ultimately got this fixed. Process & maturity gaps are things a bug bounty platform alone won’t fix. It’s exactly why orgs ask @LutaSecurity to manage end-to-end programs.
lutasecurity.com
Luta Security is your expert partner for implementing and auditing bug bounty and vulnerability disclosure programs and conducting comprehensive security maturity assessments.
0
0
5
Nice work by @BobDaHacker in figuring out several hacks of @McDonalds as well as the trickiest hack of all:. How to report the bugs to get them fixed. We see a lot of orgs still struggling to run solid Vulnerability Disclosure Programs, let alone bug bounties./ht @vxunderground.
Found huge security flaws @McDonalds - crew members could access sites reserved for corporate employees with internal functions, API keys exposed, and more. Had to call their HQ and pretend to know people just to report it 🤦. They fixed it but fired my friend who helped. Full.
1
2
19
If you think you saw me in Vegas, no you didn’t.
6
1
33
RT @TheRegister: Lazarus Group rises again, this time with malware-laden fake FOSS
theregister.com
Infosec In Brief: PLUS: Slow MFA rollout costs Canucks $5m; Lawmakers ponder Stingray ban; MSFT tightens Teams; And more!
0
8
0
In the early days of bank & credit card company penetration testing, I loved being hired by banks to rob them. Some of these hacks may still work today. Many safeguards rely on automated & manual checks we told them to put in place decades ago. Also: Money is completely made up.
When you make a Bank ACH transaction, it’s literally just an SFTP upload. Sent as a NACHA file, it's 940 bytes of ASCII text. Bank-to-Bank transactions cost ~0.2 cents. As long as it travels via encrypted tunnel; it’s compliant!. Here’s how the quirky system works:
4
9
44
One of the strangest myths about vulnerability disclosure policies & programs is that they have always been ways for vendors to receive vulnerability reports. Nah, these policies were borne out of hackers telling vendors when to expect public disclosure to inform & protect users.
@midwestneil @caseyjohnellis @brysonbort For any newcomers who are reading along: .There were certainly Disclosure policies before Microsoft’s, but they were mostly from hackers, like RFPolicy by rain forest puppy. I based Microsoft’s & Symantec Vuln Research’s Disclosure policies on AtStake’s, which was based on RFP’s.
5
12
45
No more AI that uses DEI?. Better stop all those voice commands & voice outputs then. Them’s a disability accommodation right thar.
2
2
13
RT @NCSC: 🚨Today, the NCSC is revealing that Russian military intelligence has been responsible for deploying a sophisticated malware dubbe….
ncsc.gov.uk
Cyber threat group APT 28 has been responsible for deploying a sophisticated malware against user email accounts as part of its operations.
0
94
0
Let’s get into some #GoodTrouble today.
Healthy wildlife and communities depend on a healthy democracy. The legacy of the late great #JohnLewis was rooted in the fight for voting access for all Americans. This fight continues – Good Trouble Lives On!. To find a #GoodTroubleLivesOn event, visit
0
0
1