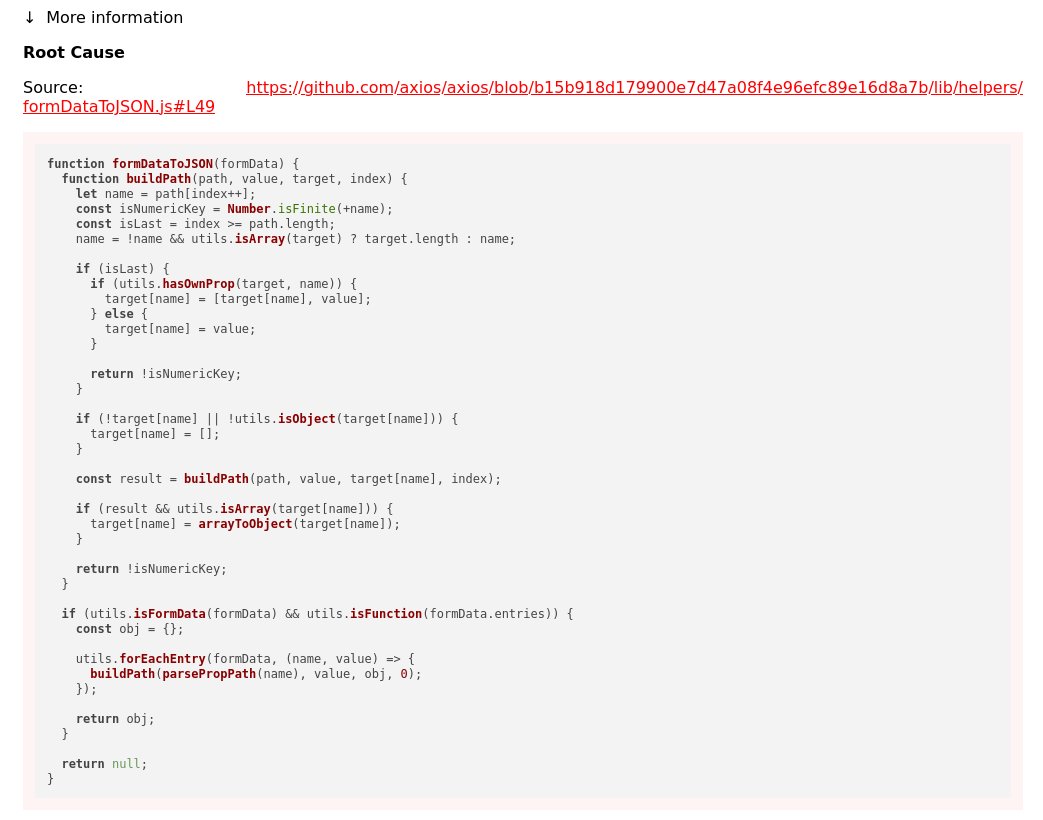
Ryan Barnett (B0N3)
@ryancbarnett
Followers
5K
Following
5K
Media
724
Statuses
6K
Web App Defender | Bug Hunter/Triager | Purple Team | Detection Engineering | Author | Senior Threat Research Manager @Akamai_research | OWASP Project Leader ✝️
Joined April 2010
@BlackHatEvents Briefings time slots are now posted! @4ng3lhacker and I will be presenting on Thursday, Aug 7th at 10:20am. #BHUSA #LetsGo .
0
3
9
RT @phrack: Going to @defcon?! We'll have 9500 print copies of Phrack, and Sunday @ noon @netspooky @richinseattle and @chompie will be on….
0
62
0
RT @BugBountyDEFCON: Don't miss @Portswigger's "Awards: Top 10 Web Hacking Techniques of 2024" on Sunday, August 10 at 11:30 AM inside the….
0
4
0
I was testing out the Activescan++ suspect transform updates prepping for our upcoming @BlackHatEvents talk. Worked like a charm. Then I used the new "Explore" issue AI functionality. It took the issue data based on the behavior and identified a full-width XSS bypass. #impressed.
Five major AI capabilities arrived in Burp Suite Professional:. ✨Explore Issue.✨Explainer.✨AI-generated recorded logins.✨False positive reduction.✨AI-powered extensibility. Each one helps you tackle complex tasks faster and smarter 👉
2
6
36
RT @infinitelogins: We're less than two weeks away from @defcon, and all the hard work and hundreds of hours poured into Bug Bounty Village….
0
10
0
RT @BugBountyDEFCON: Did you know that the Bug Bounty Village CTF is an official @DEFCON contest? Make sure to register now at https://t.co….
0
5
0
I do not agree this is an either/or scenario. I have my own perspectives on #BugBounty value propositions including other motivations for orgs to run BB programs including “threat actor” simulation to verify exploitability of vulns and fix prioritization.
A bug bounty program is economically beneficial to a firm when the firm has low in-house efficiency in finding a vulnerability . *or* . when the firm faces a high proportion of coopetitive hackers (bug reporters who would otherwise pose a security risk by misusing vulnerability.
2
0
4
RT @WeldPond: A bug bounty program is economically beneficial to a firm when the firm has low in-house efficiency in finding a vulnerabilit….
0
3
0
RT @PortSwigger: Today, James Kettle (@albinowax) delivered an internal preview of ‘HTTP/1.1 Must Die!’. One dev (kind of) joked, “If James….
0
4
0
RT @PortSwigger: 🤝 Meet the Researchers. Join the Movement. If you're heading to Black Hat or DEF CON in Las Vegas, don’t miss our informa….
0
11
0
RT @ctbbpodcast: HackerNotes TLDR for episode 131! — ►⠀V1 Instance metadata Service Protections Bypass: An old wri….
blog.criticalthinkingpodcast.io
0
9
0
RT @Rhynorater: Another mind-blowing episode with @avlidienbrunn. Very technical episode with critical impact.
0
4
0
RT @TonyLauro: Hey friends! From zero-days to sunburnt servers, we’re diving into what’s trending in cyber risk this summer! Check me out o….
0
1
0
RT @yeswehack: We’re proud to sponsor @BugBountyDEFCON this year again 😎. Meet @Brumens2 & Anthony Silva for #BugBountyTips, #Dojo demos, o….
0
6
0
RT @akamai_research: Akamai SIG has done a thorough analysis of the SharePoint vuln CVE-2025–53770 and found more than 20% of observed envi….
0
8
0
Our @akamai_research response - Understand the SharePoint RCE: Exploitations, Detections, and Mitigations.
akamai.com
Get an in-depth look at the Microsoft SharePoint vulnerability, the exploitation activity, and Akamai’s detection and mitigation strategies.
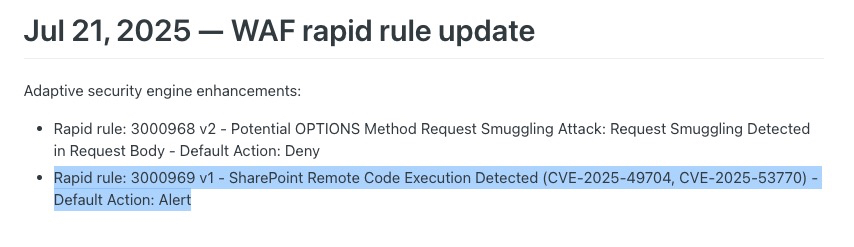
Akamai researchers have released a rule to detect the critical SharePoint RCE vulnerabilities CVE-2025-49704 and CVE-2025-53770. We will be releasing a blog with further vulnerability details and ITW activity in the coming days, stay tuned. AAP rule:
0
2
10