Jacob P
@jmpsecurity
Followers
25
Following
92
Media
4
Statuses
102
Joined September 2020
A follow up on last week’s FileFix blog. FileFix (Part 2) https://t.co/pIcrbQnccc
6
63
223
I believe there is a simple way to remediate #ESC15 Wrote a PowerShell script for it: https://t.co/kUnS9UW7T8 🧵 1/5
github.com
Contribute to JonasBK/Powershell development by creating an account on GitHub.
2
34
97
Want to check for #ESC15 ? Use the following cypher with #BloodHound MATCH p=(:Base)-[:MemberOf*0..]->()-[:Enroll|AllExtendedRights]->(ct:CertTemplate)-[:PublishedTo]->(:EnterpriseCA)-[:TrustedForNTAuth]->(:NTAuthStore)-[:NTAuthStoreFor]->(:Domain) WHERE
2
66
202
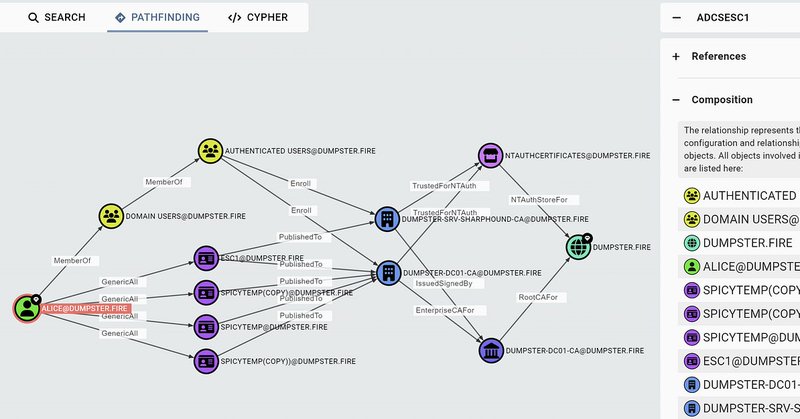
More ADCS attack paths in BloodHound! 🧩🔍 This blog post is about implicit mapping abuse and how we have implemented ESC6, ESC9, and ESC10.
Ready for more AD CS in BloodHound? After covering ESC1, Golden Certificates, & ESC3, @Jonas_B_K is back with Part 3, focusing on new edges with ESC6, ESC9, and ESC10 domain escalation techniques. Check out the latest post to learn more! ⤵️
0
4
8
I have written a blogpost with Jakob Mollerup about the diffence between NT AUTHORITY\SERVICE and NT SERVICE\ALL SERVICES because we found the existing documentation to be a bit too brief #Windows #sysinternals
https://t.co/Qo2YEEC2Bl
itm8.dk
Hvad er en itm8? Vi er præcis, hvad navnet siger: Din m8* (*mate), der er ekspert i IT. Vi er din partner til 360 graders IT.
0
9
18
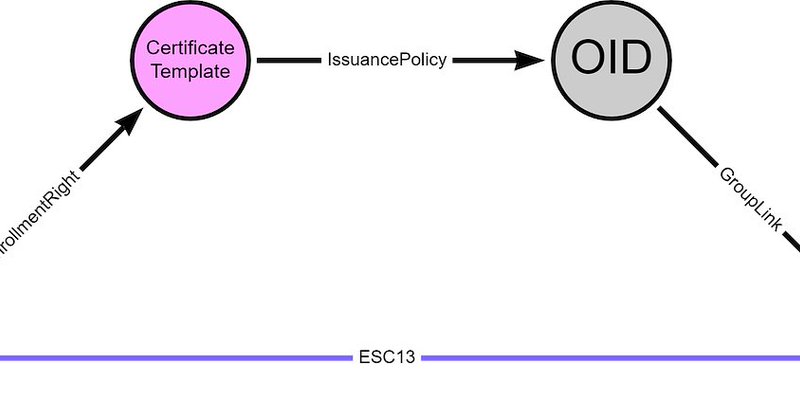
Wrote a blog post about a new ADCS abuse technique involvering issuance policies and OID group links 📝
posts.specterops.io
It is possible to configure an Active Directory Certificate Services (ADCS) certificate template with an issuance policy having an OID…
4
84
194
ADCS attack paths in BloodHound! 🥳 This blog post breaks down the implementation of the ESC1 requirements and guides you on effectively leveraging BloodHound to identify attack paths that include ESC1 privileges. https://t.co/ubWPm2xdLO
posts.specterops.io
Since Will Schroeder and Lee Christensen published the Certified Pre-Owned whitepaper, the BloodHound Enterprise team at SpecterOps has…
4
117
287
I am releasing my book on email security for free, you can get it here: https://t.co/CFG1GIj1x4 Share as you wish. Merry Xmas to all my fellow hackers
leanpub.com
Learn how to attack and defend email infrastructures
1
2
0
Last week @_wald0 and I presented a webinar about the workings of ADCS and how we are implementing the ADCS attack paths in BloodHound. You can watch the recording here :)
ICYMI: Our ADCS Attack Paths in BloodHound webinar presented by @_wald0 & @Jonas_B_K is now available to view on demand! Learn all about the latest feature in BloodHound 👉 https://t.co/V5zega2BBN
0
3
16
New #BloodHound documentation: Getting started with BloodHound Community Edition It's describing a short step-by-step process of deploying and using #BloodHoundCE
https://t.co/0dQdSAjroF
bloodhound.specterops.io
0
1
3
Is it an issue if I can modify the msDS-ExternalDirectoryObjectId on myself? @_dirkjan
1
0
0
If ever there is still someone using RSH out there, you should consider moving away from it: https://t.co/tqRKNb4m5M
bencteux.fr
Netkit-rcp is vulnerable to a command injection in filenames used as copy arguments.
0
1
1
Our ‘What is Tier Zero’ blog post is out! 🚀 https://t.co/8O3V3kFoGf It'll be the first in a series where we'll deep-dive into the critical assets of AD and Azure. We will build out a Tier Zero table with all the assets we consider throughout the series.
posts.specterops.io
Tier Zero is a crucial group of assets in Active Directory (AD) and Azure. Its purpose is to protect the most critical components by…
2
66
149
Let's define Tier Zero! 📽️🔼 Join @elad_shamir and me for our webinar "Defining the Undefined: What is Tier Zero?" on June 22nd. It will be the first in a @SpecterOps series on this topic where we'll deep-dive into the critical assets of Active Directory and Azure.
Join @elad_shamir & @Jonas_B_K on Thurs., June 22 in part one of our webinar series to define the critical identities & resources once and for all across Active Directory and Azure. Register: https://t.co/MPJ3oYfpiK
0
3
5
0
0
0
My Active Directory Tiering webinar is now on YouTube. Check it out :) https://t.co/3j8TVRTgFH
0
2
7
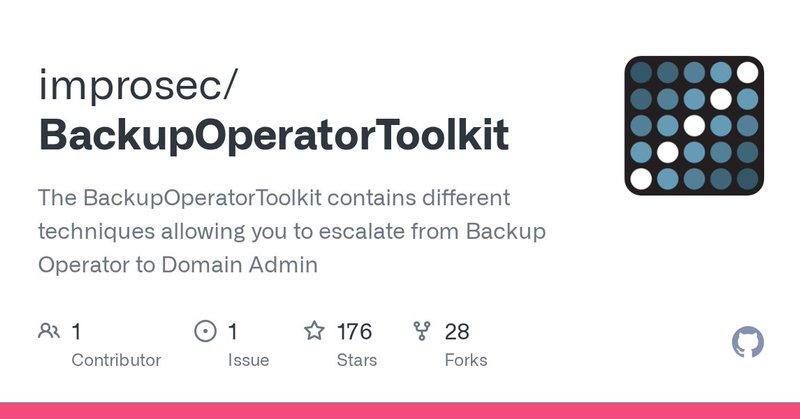
Released a new Backup Operator to Domain Admin tool. It contains 4 different methods for escalation, more methods will be added:
github.com
The BackupOperatorToolkit contains different techniques allowing you to escalate from Backup Operator to Domain Admin - improsec/BackupOperatorToolkit
1
61
179