Arun
@dazzyddos
Followers
2K
Following
7K
Media
89
Statuses
4K
RT @RedSeerSecurity and An Otaku. Views are my own.
Loading...
Joined January 2017
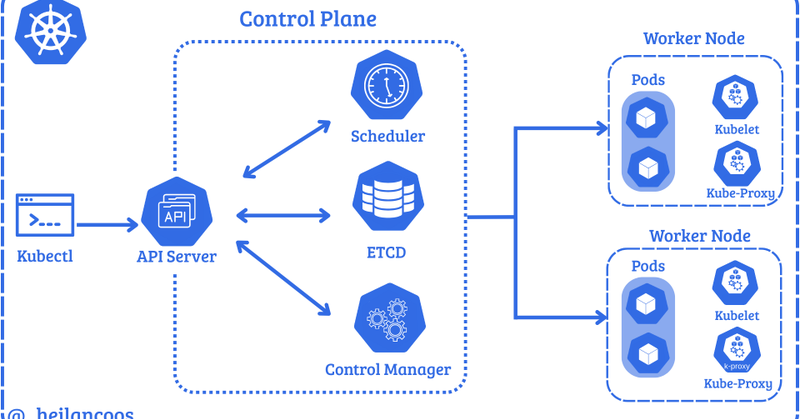
I fell down the Kubernetes security rabbit hole. So I wrote a deep-dive on attack techniques, detection engineering, and scripts to test everything in a lab. Shoutout to @GrahamHelton and @raesene for their previous work! https://t.co/5wlHqIZD8X
heilancoos.github.io
What attackers do in Kubernetes and how to catch them.
3
76
341
One-shot ESC1 + unPAC BOF for Havoc and CS. The certificate request includes the target's SID in the SAN to comply with strong mapping requirements (KB5014754). Hope it’s useful https://t.co/vPaDur297s
2
43
204
Tool Spotlight: IAM Vulnerable IAM Vulnerable is an open source playground that spins up intentionally vulnerable IAM configs so you can practice finding and exploiting real privesc paths safely.
1
2
14
Field Notes on Malware: The Evolution of C2 Evasion and What It Means for Detection - @deceptiq_
https://t.co/VLfD7BhqO9
deceptiq.com
Understanding how C2 frameworks evolve their evasion techniques and what this means for detection strategies.
1
19
99
Dusting off the ol' blog with some notes on Azure Storage Accounts attacks and detections.
hausec.com
In Azure land, there’s many resources for many reasons. Throughout the cloud security part of my career, I’ve seen environments use many different types of resources but the most common…
1
8
30
Fully autonomous AI hacker to find actual exploits in your web apps. Shannon has achieved a 96.15% success rate on the hint-free, source-aware XBOW Benchmark. https://t.co/EQgOtnhCyk
github.com
Fully autonomous AI hacker to find actual exploits in your web apps. Shannon has achieved a 96.15% success rate on the hint-free, source-aware XBOW Benchmark. - KeygraphHQ/shannon
2
101
595
[RELEASE] As promised, I’m releasing the first blog post in a series. It covers the gaps still present in current stack-based telemetry and how Moonwalking can be extended to evade detection logic and reach “on-exec” memory encryption. Enjoy ;) https://t.co/4Yf28y7cT4
klezvirus.github.io
TL;DR
8
99
309
A single hypervisor breach can put hundreds of virtual machines at risk. We’ve seen Akira and others shift to ESXi/Hyper-V for mass impact. ✅ They use legit tools (like openssl) ✅ Bypass EDR ✅ Encrypt VMDKs directly 📃 @RussianPanda9xx @Purp1eW0lf
https://t.co/nWxBC2Tb65
2
20
112
Wanting more from today's #BHEU talk on SCOM? Check out this two part blog series! 1️⃣ @unsigned_sh0rt maps SCOM’s roles, accounts, & trust boundaries, then shows how attackers can chain insecure defaults into full management group compromise. https://t.co/Ai4TqTtc4O 🧵: 1/2
specterops.io
TL:DR; SCOM suffers from similar insecure default configurations as its SCCM counterpart, enabling attackers to escalate privileges, harvest credentials, and ultimately compromise the entire manage...
1
53
124
New blog by Outflank’s @KyleAvery: Linux process injection leveraging seccomp to inject shared libraries into Linux processes without LD_PRELOAD, ptrace nor elevated privileges. Parent-to-child injection at any ptrace_scope level 💪😎 Tech details here: https://t.co/aSv7XlT1Ah
1
52
150
SCOM is one of the most deployed, but least researched, System Center products. @synzack21 breaks down how it works + how to build a lab to test new tradecraft.
specterops.io
Yet another System Center Ludus configuration for your collection. https://github.com/Synzack/ludus_scom
1
46
102
"Offense and defense aren't peers. Defense is offense's child." - @JohnLaTwC We built an LLM-powered AMSI provider and paired it against a red team agent. Then, @0xdab0 wrote a blog about it: https://t.co/jnCNIlYBII A few observations from the experiment: >>> To advance, we
6
51
176
I'm releasing research soon detailing a technique to take over Kubernetes clusters. It allows running arbitrary commands in EVERY pod in the cluster using only a commonly granted "read only" RBAC permission. Oh and it's not logged by Kubernetes AuditPolicy 👀
5
27
160
New post: Field Notes on Malware A look at how C2 frameworks are evolving their evasion techniques and what it means for detection. https://t.co/93vAnlxMar
1
30
71
My gift for Thanksgiving 💜 I wrote for you the blog post I always wanted to read! Happy holiday!🦃 PLEASE READ IT!!! https://t.co/Pr3P3jOh8s
wiz.io
Attackers abuse OAuth flows like device code phishing and ROPC to bypass MFA and gain persistence in Azure. Here's how to detect them with Entra ID logs.
9
81
235
NTLM relays failing because of EPA? 😒 @zyn3rgy & @Tw1sm break down how to enumerate EPA settings across more protocols + drop new tooling (RelayInformer) to make relays predictable. Check out their blog for more:
specterops.io
It's important to know if your NTLM relay will be prevented by integrity protections such as EPA, before setting up for and attempting the attack. In this post, we share how to solve this problem for...
1
54
170
Added my ICMP, NTP and Websocket C2 channel examples to the public repo. https://t.co/GLmksKiBY7 Also accompanying blog post explaining the template: https://t.co/3zvoKvUdDl pls no flame bad code :D Websocket channel in action:
3
25
144
Looks like @nullcon Berlin talks are out, so you can watch @rotemsalinas and me in my return to doing conference talks! We have some nice info about Microsoft EPM, a cool exploitation trick with the Cloud Filter driver, and a no-fix LPE for you here :) https://t.co/C8luIaCXdI
4
17
62
Just published a summary of "modern" Windows authentication reflection attacks. Turns out reflection never really died. 😅 https://t.co/2YxXlaRMMC
decoder.cloud
Authentication reflection has been around for more than 20 years, but its implications in modern Windows networks are far from obsolete. Even after all the patches Microsoft has rolled out over the…
3
79
223
Hunting EDR Freeze... A recent EDR-Freeze technique by @TwoSevenOneT can suspend a given EDR process. Now it's time to hunt it down with few logs and clever correlation. The post: https://t.co/td3lT9nCwM
#redteam #blueteam #maldev Hunting EDR Freeze... A recent EDR-Freeze
4
46
183