Dray Agha
@Purp1eW0lf
Followers
6K
Following
10K
Media
519
Statuses
13K
Hunt & Response Senior Manager @HuntressLabs || "Competition is the law of the jungle, but cooperation is the law of civilisation” - Kropotkin
Joined November 2014
Blue team notes is a GitHub cheatsheet of one-liners and scripts I’ve found helpful during incident response and general blue team work
github.com
You didn't think I'd go and leave the blue team out, right? - GitHub - Purp1eW0lf/Blue-Team-Notes: You didn't think I'd go and leave the blue team out, right?
4
72
227
Has my content ever helped you? I'd appreciate you making it known 🥰 After more than 6 years of free content, for the 1st time ever I've been nominated for a #SANSDMA Award 👀🎉 Voting is open until October 8 and I'm alongside other worthy recipients🙏 https://t.co/ctp1FxUDtv
2
6
29
As of Thurs Aug 14th we're seeing clear indications that a threat actor has now weaponised and is exploiting vulnerabilities in Axis camera software (CVE-2025-30023/4/5/6) which was presented at DEFCON. Props to @Cyber4a53 for find. https://t.co/ktPlOJkekW CC: @HuntressLabs 👇
3
27
64
🔐 Advice from Huntress Disable SonicWall VPN if possible If not, restrict by IP & segment networks No SonicWall comms yet, contact their support IoCs we can share IPv4s: 142.252.99[.]59 45.86.208[.]240 77.247.126[.]239
2
7
24
🚨 SonicWall Exploitation (Zero Day?) 🚨 Huntress is tracking active intrusions via SonicWall devices. Threat actors are bypassing MFA, pivoting to domain controllers, deploying ransomware (likely Akira), and creating users for persistence. Pace suggests possible zero-day
5
73
200
New @Huntress blog! @Purp1eW0lf and I share some old defense evasion tactics from a well-commented script used by Xinglocker in 2021 still being used today! Make sure you can detect them! #detectionengineering #ransomware
https://t.co/kISGPUhjJg
huntress.com
When a clearly commented script revealed an attacker's tactics, Huntress prevented encryption. Read on to learn more about the evolution of recycled ransomware playbooks used by multiple threat...
1
20
51
Got a new @HuntressLabs blog out today taking a look at some intrusion analysis methodology with practical examples - check it out! https://t.co/cb61n4nFCB
huntress.com
Transform raw Windows event data into actionable insights. Learn expert methodologies for intrusion analysis, authentication events, credential dumping, and RDP activity to stay ahead of threats.
5
52
204
Ludushound shows the power of community driven innovation in cybersecurity. @bagelByt3s created an awesome tool to convert bloodhound data into a working lab in 🏟️ Ludus. Replicate complex live environments with automation - and get back to the fun stuff! https://t.co/19qfjRwaOA
specterops.io
LudusHound is a tool for red and blue teams that transforms BloodHound data into a fully functional, Active Directory replica environment via the Ludus framework for controlled testing.
1
89
263
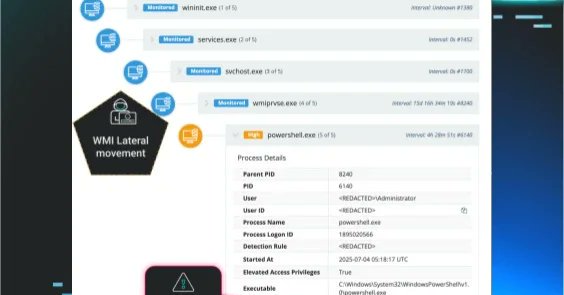
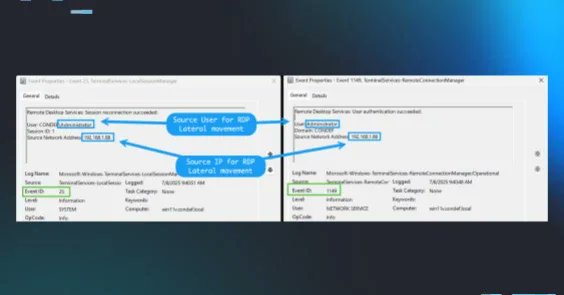
Interesting hands-on-keyboard case today @HuntressLabs -> Suspected VPN initial access -> TA used this to RDP to DC & RDS -> TA created a hidden accounts for persistence -> TA attempted to clear logs for defence evasion -> Huntress evicted TA 😎
5
26
174
Did you know TypedPaths artifact can be helpful to detect the FileFix?
13
55
270
The /proc/net/packet file on Linux shows you all open raw sockets that are grabbing network traffic. I'm going to show you what is in this file and provide a script that lists all processes sniffing traffic to help find malicious sniffers.
8
165
1K
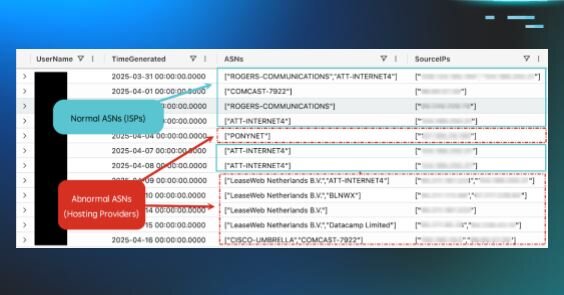
Got a new blog out today with my colleagues @xorJosh & @Purp1eW0lf looking at how we utilize ASNs during hunts & investigations at @HuntressLabs - check it out! https://t.co/APjy6rSEdl
huntress.com
Autonomous system numbers are like the address book of the internet, and not every IP address belongs to a “friendly” address. Learn more about how the Huntress Hunt & Response teams utilize ASNs.
1
25
64
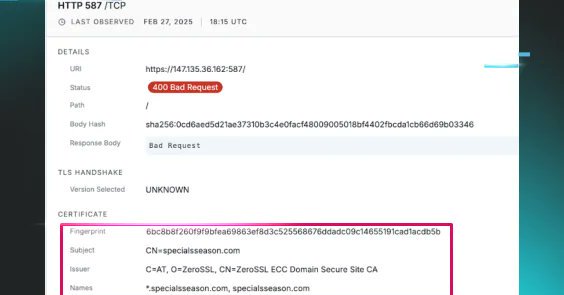
🚨 [ New blog ] out today with my 🐐 colleagues @xorJosh and @Purp1eW0lf - this case started with a simple brute force and ended with some really interesting findings - check it out! https://t.co/WllSCwpwAl
huntress.com
Discover how a seemingly simple brute force attack led to the uncovering of a suspected ransomware-as-a-service operation. This ecosystem appears to be leveraged by initial access brokers, driving an...
0
15
36
Got a new @HuntressLabs blog out today looking at a case that @Purp1eW0lf @xorJosh and I worked on recently - VPN compromise, lateral movement, Veeam exploitation & some methodology notes throughout that newer folks might find particularly interesting! https://t.co/VHIlySEXdM
huntress.com
Explore the inner workings of real-world cyberattacks and gain insight into the challenges faced by Huntress threat analysts. Discover the critical role of investigative techniques and their import...
3
13
57
Fake Generative AI App leads to NetSupport RAT infection
2
9
21
Suspected initial access malware spreading via fake captcha, utilising trycloudflare domains
3
20
115
@birchb0y has an really amazing blog on similar activity he previously looked into: https://t.co/iAqo5by1yl
alden.io
Recent infostealer malware campaign utilizing fake Homebrew websites to deliver Cuckoo and AtomicStealer.
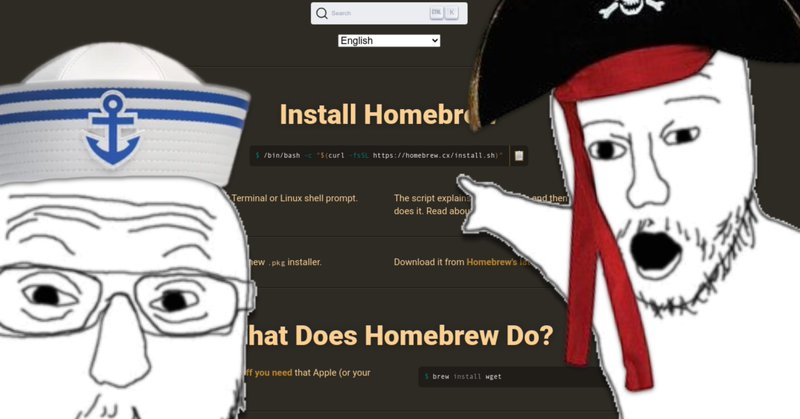
⚠️ Developers, please be careful when installing Homebrew. Google is serving sponsored links to a Homebrew site clone that has a cURL command to malware. The URL for this site is one letter different than the official site.
1
7
26
🚨 The RMM threat landscape is evolving! 🚨 Recent attacks, like those highlighted by @HuntressLabs 🛡️ & CERT-UA 🇺🇦, show how adversaries 🎭 weaponize RMM tools 🛠️ for persistence 🔒 & lateral movement ↔️. 🔍 Enter LOLRMM: your 🧙♂️ ally in detecting 👀 & preventing 🚫 RMM abuse.
0
23
40