Cryptcreed
@cryptcreed
Followers
21
Following
314
Media
1
Statuses
73
Cyber Security Enthusiast. Love to discover new things. Certified Ethical Hacker v10.
Joined March 2019
"A majority of the bugs were only possible due to automated asset discovery, but still required some manual inspection and exploitation." This is an important point, automation is only part of the puzzle! Great blog @infosec_au
https://t.co/tIiK9bkqZT
assetnote.io
2
60
202
I wrote a post on @assetnote's blog about hacking in bug bounties for the last four years. This should give you a good idea on what I've been reporting and how I find bugs and incorporate them back into our platform. https://t.co/BhL4DiQlaB
assetnote.io
12
312
768
Python 4 FAQ. 1. The version after 3.9 is 3.10; in fact it already exists (in github master). 2. If there ever is a version 4, the transition from 3 to 4 will be more like that from 1 to 2 rather than 2 to 3.
141
704
4K
I just uploaded some of the most common file types for my Patrik's Bug Bounty Tools mind map here: SVG: https://t.co/IJhzII3XNf PDF: https://t.co/gyA2RxQbpZ XMIND: https://t.co/PUC8ur6ldT PNG: https://t.co/zKucgzsACm enjoy! 🥰🥳👑 #bugbountytips
#BugBounty
10
277
738
RT @sectest9: RT @aufzayed: CAPTCHA BYPASS TECHNIQUES #bugbounty #bugbountytip #bugbountytips #cybersecurity #infosec
https://t.co/Q2w8KG8eaR
honeyakshat999.medium.com
Q.what is captcha???? according to Wikipedia- A CAPTCHA is a type of challenge-response test used in computing to determine whether or…
0
8
8
hey hackers, started a write up series on find your first bug https://t.co/PxxaKbBCvQ
#bugbounty #bugbountytips #bugbountytip #100DaysOfCode @InsiderPhD @stokfredrik @theXSSrat @Alra3ees
4
166
341
Easily generate a custom wordlist from any domain: echo "
https://t.co/Aps3n9I4or" | subfinder -silent | hakrawler -plain -usewayback -scope yolo | sed $'s/[:./?=:]/\\\n/g' | anew
9
136
390
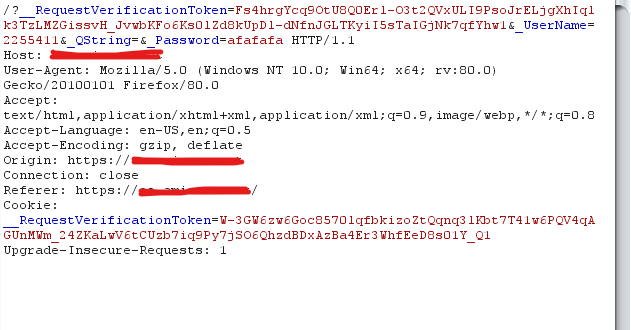
Try this when testing webapps: 1. Set up burp in browser1 2. Do a password reset request in browser1 3. Open the password reset email in browser2 and copy the token 4. Search your Burp history for the token, if it is there, you've got yourself a nice easy account takeover!
15
351
1K
#bugbounty #bugbountytip
#Android The Easiest way to find deeplink patterns search on google - targetscheme:// deeplink OR On github - "targetscheme://" deeplink
2
18
54
alert() with no parenthesis, back ticks, brackets, quotes, braces, etc. by @stealthybugs a=8,b=confirm,c=window,c.onerror=b;throw-a
10
107
432
Video Tuts on Debugging Automation Basics for Vuln. Researchers https://t.co/phSySsB1Yx *Debug Events *Breakpoints *Registers, Memory Thread & Module Manipulation *Hook API *Writing Your First Fuzzer #vulnerability #bugbountytips #bugbounty #fuzzing #ReverseEngineering #malware
youtube.com
0
44
83
Trick for bypass the rate-limit.. (it worked for me in many companies) #bugbountytips #bugbountytip #bugbounty
6
327
954
Hey! I just published this writeup on medium. Please do read it and let me know how was it. https://t.co/psjppmscwb Big thanks to @pdiscoveryio for such amazing tools. Thanks to @ADITYASHENDE17 for great tips #bugbountytips
#bugbounty
#cybersecurity
vedanttekale20.medium.com
Hello infosec community! I’m back again to share an interesting finding with you. Little bit about me, my name is Vedant and I’m a bug…
6
66
184
Sharing my OSCP notes. I hope it will help you guys! https://t.co/e0z9jPLA26
5
94
244
-1-Pentest-Cheat-Sheets: https://t.co/PIFX99L91R -2-Web Application Cheatsheet (Vulnhub): https://t.co/Av5Lii2cdS -3- A cheatsheet with commands that can be used to perform kerberos attacks : https://t.co/FddXUeA1Tm
#OSINT #bugbountytip #pentest #redteam #hacking
github.com
This cheatsheet is aimed at the CTF Players and Beginners to help them understand Web Application Vulnerablity with examples. - Ignitetechnologies/Web-Application-Cheatsheet
1
118
282
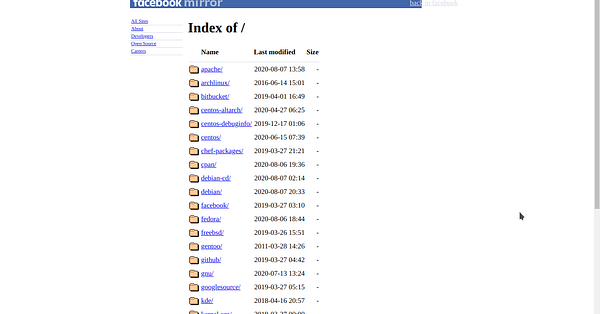
I just published Reflected XSS in Facebook’s mirror websites Hope you will like it. Feedbacks are appreciated
link.medium.com
Heyyy Everyoneee,
25
175
489
If you hate analyzing JS files with strange variable names and minified versions, you should give a look at
1
35
114
Here's the playlist for all my recent Recon talks at a single place: https://t.co/5Ub14RqKVX Slides: https://t.co/2QCd9QktPV Will keep on adding more to the same place. :) #bugbounty #infosec #websecurity #bugbountytips
#recon
youtube.com
You can find every talk on application security or bug bounty delivered by me over various platforms here in this playlist.
3
84
171
A common question asked is how do I best prepare for OSCP? This list of OSCP-Like boxes from @TJ_Null + writeups from @rana__khalil are great resources to use heading into the PWK lab! Machine List: https://t.co/i9Ubg457VY Rana's Writeups: https://t.co/eNOjnEHihk
#OSCP #PWK
1
65
171
https://t.co/Idhljfvkix Always try to fetch hidden web directories In subdomains of the target #bugbountytips #bugbounty #cybersecurity
link.medium.com
Description:
1
90
193