Adli Wahid
@adliwahid
Followers
2K
Following
34K
Media
335
Statuses
11K
Tweets are personal. Bee photos on Instagram https://t.co/X9rcu4SmNT
Brisbane, Queensland
Joined June 2009
So excited that the Japanese edition of my global best-selling book, The Palestine Laboratory, is out with @Iwanami_Shinsho on 9 December. More details here:
iwanami.co.jp
パレスチナを兵器や監視技術の実験場として利用し、それらを世界中に輸出するイスラエルの実態を、綿密な調査を通じて暴き出す。 アントニー・ローウェンスティン 著
ユダヤ系オーストラリア/ドイツ人ジャーナリスト Antony Loewensteinの世界的ベストセラー『#パレスチナ実験場:世界に輸出されるイスラエルの占領技術』(岩波書店)が、ついに完成! 微力ながら、序文の翻訳と解説を担当。詳細は下に追加していきます。まずは、ご紹介↓ https://t.co/Z6v62dvZ47
12
46
161
🔐 https://t.co/R2t2w20XUW — One feed. All BSD security advisories. Stay patched. Stay secure. → https://t.co/dfEZRcdTK5
#BSD #InfoSec #OpenBSD #FreeBSD #NetBSD #pfSense #SysAdmin
bsdsec.net
Deadsimple BSD Security Advisories and Announcements
0
19
41
BREAKING: A new UN report finds that Israel’s assault on Gaza - with the destruction of health care, education, infrastructure, even the banking system - has erased 69 years of human development, marking the worst economic collapse ever recorded. This is not war: it is genocide.
3K
36K
69K
K7 Labs analyse a campaign ongoing in Brazil, spreading malware via WhatsApp web from the victim’s machine to their contacts by using the open-source WhatsApp automation script from GitHub whilst also loading a banking trojan into memory. https://t.co/iHX7VPEAP5
3
18
54
K7's Praveen Babu analyses a Python-based malware sample that uses multi-stage obfuscation. https://t.co/ylHGvT9Q9h
0
11
49
Jamf Threat Labs analyses DigitStealer, a new macOS infostealer that uses advanced hardware checks and multi-stage attacks to evade detection and steal sensitive data. https://t.co/0B509wsB84
0
12
40
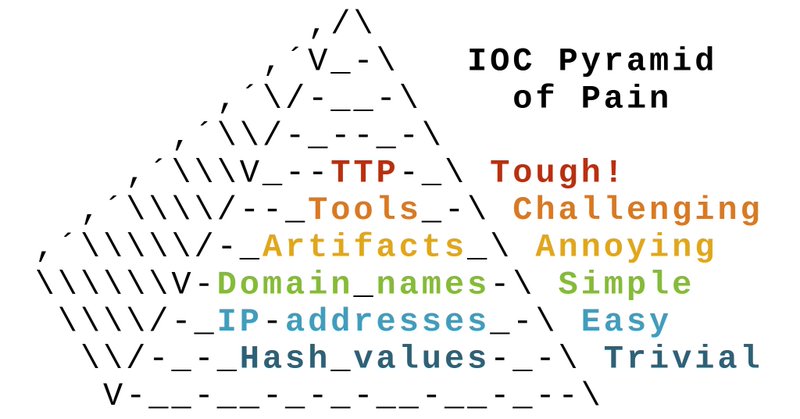
Monitoring for too many old indicators not only costs money, it can even inhibit detection of real intrusions. 📆 Include "last seen" when publishing IOCs ❌ Prune old IOCs 📜 Prioritize long lived IOCs over short lived ones https://t.co/7PvNbgsbRX
netresec.com
Are you importing indicators of compromise (IOC) in the form of domain names and IP addresses into your SIEM, NDR or IDS? If so, have you considered for how long you should keep looking for those...
1
3
9
Suricata 7.0.13 and 8.0.2 packages are now available for Ubuntu on Ubuntu PPA. Check it out here: https://t.co/YZjUQOThjp
#Suricata7 #Suricata8 #Suricata
forum.suricata.io
More about Suricata 7.0.13 and 8.0.2 features, improvements and release notes : Suricata 7.0.13 and 8.0.2 packages are now available for Ubuntu on Ubuntu PPA (Launchpad). 20.04 Focal 22.04 Jammy...
0
3
7
👀 OpenSource Malware an open database for tracking malicious open-source packages from npm, PyPI, GitHub repos! Great source of intel feed for supply-chain attacks! 👇 https://t.co/y6ELpxxX1S
8
131
707
Elastic Security Labs publishes nightMARE, a Python library (v0.16) for malware analysis and for building configuration extractors. https://t.co/Cdofl8Lazn
0
42
146
👀 A malicious MCP server spotted in the wild! The Postmark MCP server (used to send and track emails through Postmark API) introduced a suspicious behavior in version 1.0.16. The attacker cloned the legitimate Postmark MCP code and added a malicious BCC line, then published it
2
15
53
The Resecurity HUNTER Team warns of a mass exploitation of CVE-2025-61882 in Oracle E-Business Suite, enabling remote code execution. Several victims received extortion emails from Cl0p in late September 2025. https://t.co/n9tecnB77M
1
10
26
This is NOT the first genocide that happens under "our" watch. It is the first genocide that WE, The People, can and will stop. Against all odds and adversities.
nearly 30% of the population of Amsterdam, an estimated quarter of a million people, flood the streets of the city wearing red in solidarity with Palestine.
1K
13K
48K
Keeping track of your DF/IR webinars so you don't have to.
1
13
24
🥷 FLARE-On 12 starts today - prepare yourself with this episode of Behind the Binary 👇 https://t.co/4edhmjnMm7
open.spotify.com
Behind the Binary by Google Cloud Security · Episode
0
6
31
Three vulnerabilities (CVE-2025-20333, CVE-2025-20362, CVE-2025-20363) affecting Cisco ASA and FTD software are under active exploitation. We discuss the lifecycle of zero-day vulnerabilities and the phenomenon of “patch-or-perish.” https://t.co/zTcQCf8hFP
1
54
139
👀 New Microsoft threat report shows how attackers are using AI for evasion and obfuscation in a phishing campaign! One part is very interesting, the team spotted 5 AI fingerprints in the code. But instead of hiding the attack (the initial goal), these fingerprints actually
7
50
197
🎙️ Behind the Binary: Did you miss our latest episode on crypto heists and Web3? We dove into the "Wild West" of Web3 and decentralized finance, where thefts and hacks are now more common than in traditional finance. Blas Kojusner, Robert Wallace, and Joseph Dobson joined us to
open.spotify.com
Behind the Binary by Google Cloud Security · Episode
0
3
8