𝙽𝙴𝚃𝚁𝙴𝚂𝙴𝙲
@netresec
Followers
9K
Following
6K
Media
530
Statuses
4K
Experts in Network Forensics and Network Security Monitoring. Creators of #NetworkMiner, #CapLoader, #PacketCache, #PolarProxy and #RawCap.
Joined November 2011
New network forensics training scheduled! 📅 February 23-26, 2026 ⏲️ 13:00 to 17:00 CET (7am to 11am EDT) 🌍 Live online https://t.co/TkPpSvcLej
netresec.com
I will teach a live online network forensics training on February 23-26. The full title of the class is Network Forensics for Incident Response, where we will analyze PCAP files containing network...
0
4
12
Why are Big Tech companies are funding the radical overhaul of the U.S. justice system? They are giving money to organizations with goals to decarcerate repeat offenders and to eliminate cash bail. Choose Unplugged - a company that believes in a strong, thriving America.
0
10
40
Keylog of attacker's hands-on keyboard actions from BackConnect VNC session
1
0
3
Here's one of the screenshots from the BackConnect VNC sessions in the blog post
1
0
1
Extracting VNC screenshots and keylog data from #Latrodectus 🕷️ BackConnect https://t.co/GIAcl9Dfit
netresec.com
I recently learned that the great folks from The DFIR Report have done a writeup covering the Latrodectus backdoor. Their report is titled From a Single Click: How Lunar Spider Enabled a Near...
1
11
43
Have you integrated APOL1 genetic testing into your practice? Discover the No-Cost APOL1 Genotyping Program for eligible patients sponsored by Vertex Pharmaceuticals—helping you deliver precision care without added cost. Learn more today!
21
24
230
NetworkMiner 3.1 Released! 🔑 More usernames, passwords and hostnames 💻 Improved user interface 👾 Better details from malware C2 traffic https://t.co/aiCVVTw6Uu
netresec.com
This NetworkMiner release brings improved extraction of artifacts like usernames, passwords and hostnames from network traffic. We have also made some updates to the user interface and continued our...
1
28
88
We've now updated our PCAP-over-IP blog post to include information about pcap-broker and an example on how to run it in a docker container. https://t.co/JJsz6iDS1B
netresec.com
PCAP-over-IP is a method for reading a PCAP stream, which contains captured network traffic, through a TCP socket instead of reading the packets from a PCAP file. A simple way to create a PCAP-over...
0
0
2
pcap-broker lets you distribute real-time PCAP-over-IP streams with sniffed traffic to multiple clients. Thanks to @YunZhengHu for releasing it! https://t.co/PFfIlWhQ7N
github.com
PCAP-over-IP server written in Golang. Contribute to fox-it/pcap-broker development by creating an account on GitHub.
2
5
27
We are excited that we were once again part in the coordinated international operation #OpEndgame 📣, taking action against the notorious information and credential stealer #Rhadamanthys 🕵️ We assisted in the takedown of threat actor infrastructure and share a full list of
7
32
120
Operation Endgame’s latest phase targeted the infostealer Rhadamanthys, Remote Access Trojan VenomRAT, and the botnet Elysium. Read more in our press release: https://t.co/IHnIahrWo0
5
70
148
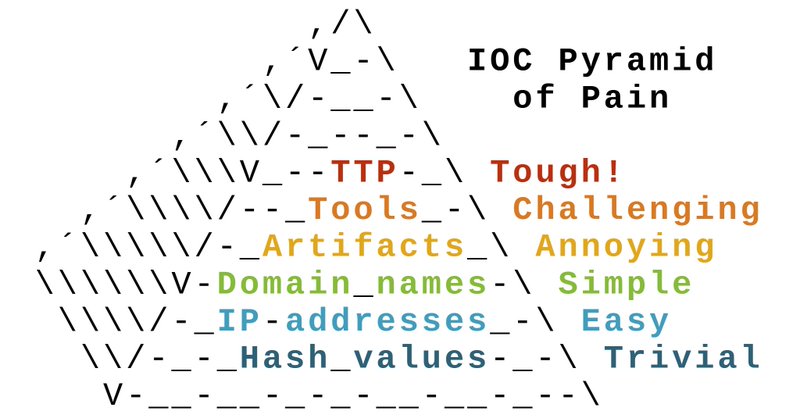
Here's a CC0 licensed copy-paste friendly version of our ASCII art Pyramid of Pain: https://t.co/wSWePxXC6y
infosec.exchange
Here's a copy-paste friendly version of our ASCII Pyramid of Pain License: CC0 ``` ,/\ ,´V_-\ IOC Pyramid ,´\/-__-\ of Pain ,´\\/-_--_-\ ,´\\\V_--TTP-_\ Tough! ,´\\\\/--_Tools_-\ Challenging ,´\\\\...
0
0
2
Monitoring for too many old indicators not only costs money, it can even inhibit detection of real intrusions. 📆 Include "last seen" when publishing IOCs ❌ Prune old IOCs 📜 Prioritize long lived IOCs over short lived ones https://t.co/7PvNbgsbRX
netresec.com
Are you importing indicators of compromise (IOC) in the form of domain names and IP addresses into your SIEM, NDR or IDS? If so, have you considered for how long you should keep looking for those...
1
3
9
The analyzed #PureRAT sample looks very similar to the one @darkrym11 recently blogged about. It even uses the same C2 157.66.26.209:56001. https://t.co/xMUcKNX51J
1
0
0
The coming years will split companies into two groups: those that become AI-native and those left catching up. The innovators who harness AI now will define the winners of tomorrow. Follow me for strategic insights on leading through the AI revolution.
6
13
113
The technical detail in this #PureRAT analysis by Heejae Hwang (황희재) is fantastic! https://t.co/2ULvBtADK5
1
21
100
The use of TLS is pretty much mandatory for HTTP/2, yet this #Nezha backoor POSTS HTTP/2 data over TCP port 80 without encryption! 🔥 172.245.52[.]169:80 🔥 c.mid[.]al:80 https://t.co/KAbizTOq24
https://t.co/ymXjczpsUm
This was used to install Nezha agent, and Nezha was used to deploy Ghost RAT on the endpoint. This was only the beginning though, full details including research into potential victim locations with this malicious Nezha Agent can be found below 👇 https://t.co/A17y5FPmo0
2
9
58
@Cloudflare You are still serving the malicious EXE+YAML combo mentioned in @Huntress blog via rism.pages.dev. Please kill this domain 🙏 🔥 rism[.]pages[.]dev/config.yml 🔥rism[.]pages[.]dev/microsoft.exe
1⃣ The @Huntress team uncovered a campaign by a likely China-nexus threat actor. The most novel finding is use of a publicly available tool called Nezha as a post-exploitation C2 agent. This is the first public reporting of the tool I've seen.
1
3
7