Sean Hopkins
@_seahop
Followers
191
Following
1K
Media
31
Statuses
645
Red teamer, terrible coder. Black Badge Defcon30.
Joined August 2021
Fun little time sink creating a red team logger. Feel free to play around, give some feedback, and if there is enough interest I'll put some more time in to it. https://t.co/mAqORgY28O
github.com
Logging tool intended for red team usage. Contribute to seahop/Clio development by creating an account on GitHub.
0
0
4
The Only Git Command List You'll Need to Bookmark → Daily Lifesavers: • git status — Your repo’s daily health check • git add . — “Take everything, I’m ready” • git commit -m "msg" — The diary entry for your work • git push — Send it to the world • git pull --rebase —
18
127
648
Custom Mach-O Image Loader with in-memory Mach-O loader https://t.co/WxQldyQcZP
#redteam
0
2
14
Reduced Docker image size from 2.1GB to 180MB. Deployments 8x faster. The original Dockerfile: - Started with ubuntu:latest - Installed everything via apt - Included dev dependencies - Copied entire project directory - Left build artifacts - No layer optimization The problems:
88
234
3K
Forget common backdoors — a DLL hijack in Windows Narrator can grant SYSTEM-level persistence at login. In our new blog, @Oddvarmoe shows how attackers abuse accessibility features and what defenders should monitor. Read now!
trustedsec.com
2
70
193
A Rust-based tool that generates Windows PE executables containing data patterns designed to trigger YARA rule matches.
github.com
Contribute to Sam0rai/guilty-as-yara development by creating an account on GitHub.
0
4
23
rolled out a bof for getting the dpapi_system key used by mimikatz /system: when ingesting master keys. If that's something you need it's live at https://t.co/lIBsG7JXWA
3
59
241
Last month, @d_tranman and I gave a talk @MCTTP_Con called "COM to the Darkside" focusing on COM/DCOM cross-session and fileless lateral movement tradecraft. Check out the slides here: https://t.co/1KNln1ldzF Recording should be released soon.
github.com
Slides and resources from MCTTP 2025 Talk. Contribute to bohops/COM-to-the-Darkside development by creating an account on GitHub.
1
80
250
Redirect any Windows TCP and UDP traffic to HTTP/Socks5 proxy
github.com
Redirect any Windows/MacOS TCP and UDP traffic to HTTP/Socks5 proxy - InterceptSuite/ProxyBridge
3
58
254
Credential Guard was supposed to end credential dumping. It didn't. @bytewreck just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled. Read for more ⤵️
specterops.io
Uncovering the protection mechanisms provided by modern Windows security features and identifying new methods for credential dumping.
4
306
659
[Crystal Kit] Evasion kit for Cobalt Strike. https://t.co/RYlbXGn1bQ
github.com
Evasion kit for Cobalt Strike. Contribute to rasta-mouse/Crystal-Kit development by creating an account on GitHub.
8
86
331
My very first Crystal Palace shared library 🤗 https://t.co/LTeeIXkvkh
github.com
Crystal Palace library for proxying Nt API calls via the Threadpool - rasta-mouse/LibTP
1
24
123
Why should Microsoft's Nested App Authentication (NAA) should be on your security team's radar? @Icemoonhsv breaks down NAA and shows how attackers can pivot between Azure resources using brokered authentication.
specterops.io
In depth walkthrough for using nested app authentication (NAA), or BroCI, for offensive engagements to access information and resources.
0
21
63
EDR vendors secure their sales pipelines but neglect monitoring GitHub for exposed installer tokens -leaving customers vulnerable to abuse and over-licensing. Adversaries likely exploit these tokens to build sandboxes for payload testing. Here are search patterns to help
6
50
313
Beyond Beacon: Writing BOF and a Native Rust COFF Loader https://t.co/Di8EmEGAuN
#redteam
0
6
19
I was today years old when I learnt that you can run ELF using ld-linux. Useful when the executable bit is not set (and you can't change it).
11
248
714
Solid overview of OPSEC considerations when operating with Sliver C2 by @zimnyaatishina 💪 #redteam #c2 #malware #opsec
https://t.co/lXHuoQFYTJ
tishina.in
tl;dr sliver version: 1.15.29 the article has been corrected many times the latest fix is about the most egregious mistake made here: I have assumed that sliver uses direct syscalls and it actually d…
2
32
140
Lance Cain & Daniel Mayer shared examples of Jamf exploitation techniques available to threat actors in their #BHUSA briefing today, which included the introduction of two new tools: JamfHound & Eve.
2
12
41
GitHub - 0pepsi/Linux-persistence: A no-reboot, in-memory Linux persistence PoC leveraging namespace joining, user-namespace elevation, and self‑deletion.
github.com
A no-reboot, in-memory Linux persistence PoC leveraging namespace joining, user-namespace elevation, and self‑deletion. - 0pepsi/Linux-persistence
0
71
356
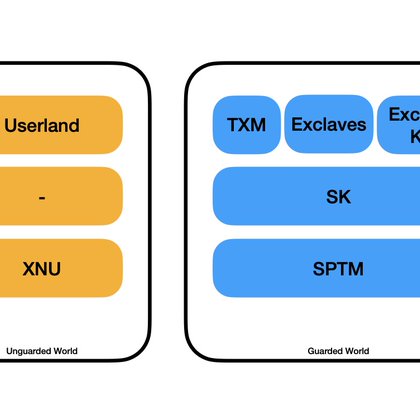
There is a party at #GLx and you have been invited. Brand new training course giving you a deep dive into #SPTM, #TXM, #SK and #Exclaves
antid0te.sg
There is a party at GLx and you have been invited. Antid0te is organising an online deep dive into SPTM, TXM, SK and Exclaves Training in December 2025 and January 2026. Instructor: Stefan Esser (
1
8
33
hashcat v7.0.0 released! After nearly 3 years of development and over 900,000 lines of code changed, this is easily the largest release we have ever had. Detailed writeup is available here: https://t.co/fxAIXNXsEr
22
374
1K