szymon
@TH3_GOAT_FARM3R
Followers
390
Following
2K
Media
9
Statuses
296
All my tweets are my own and not of my goats
Joined February 2017
RT @singe: Wifi hacking can be a useful tool, but people are out here grinding on WPA2 handshake cracking tutorials & menu driven attack to….
0
19
0
RT @sensepost: Did we mention it's all in the cloud and you can get extended lab access and office hours after support . .
0
1
0
Sadly @brucon is coming to an end. It was a fun conference with great beer! Thank you to all those involved 😁.
1
0
7
@felmoltor @brucon can't promise it will work though xD also make sure you charge your badge tonight.
0
0
1
RT @0xcon_jhb: We've just opened up the #0xcon2024 CFP! Details are at If you've been working on something interes….
0
9
0
RT @singe: South Africans 🇿🇦 in Vegas attending Black Hat USA or DefCon - let’s meetup at Rhythm & Riffs [1] in Mandalay Bay tomorrow (Tues….
0
12
0
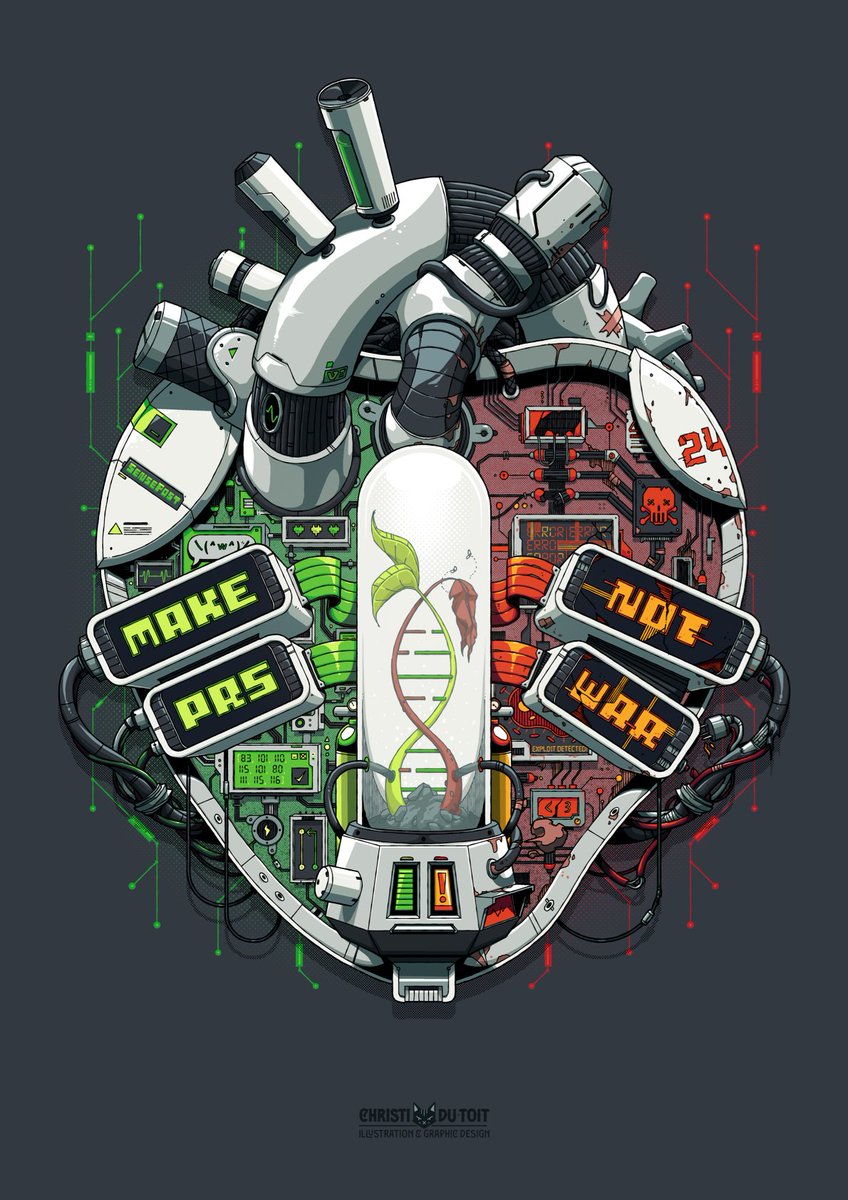
i can't wait for this to be on a tshirt! :D.
We have a long history of yearly artworks @sensepost, and this year I got to carry the baton forward. I'm excited to reveal our 2024 artwork: "make pr's, not war". An art piece almost literally from my heart. 🧵
0
0
9
It’s a really cool product! I have been messing around with it after @leonjza pointed it out to me :D.
Finally got around to running my own Sublime instance instead of hosted. Managed to get Caddy server working in front of it for the reverse proxy, accessing over Tailscale :)
0
1
2
I enjoy this attack because of the low effort and high reward. The emails we have obtained disclosed a lot. Felipe took it further by tainting those emails which made this a whole lot more fun!.
Building on work @_w_m__ was doing internally for a long time and still having good success in a recent Red Team, @felmoltor just published a tool called "mail-in-the-middle" that automates weaponising mail sent to typo'd domains. Check out the blog post!.
0
1
4
RT @VortimoTech: Your browser does not need another shitty Chrome Extension. But if you're into #OSINT, you'll need OSINT-Tool. Get it a….
0
5
0
Come see @felmoltor talk about CSP in 5min @sectorca!.
Join Felipe Molina de la Torre (@felmoltor) at 4:00 in 718B to dive into Content Security Policy. He'll reveal six new bypasses that abuse excessive trust in third-parties such as Amazon AWS, Facebook, JSDelivr, Hotjar, and others. #sectorca
0
0
1
RT @sherl0ck__: Join @n30m1nd and I as we talk about converting JavaScript NaNs into WebKit RCEs in about 2.5 hrs at #OBTS v6!.
0
8
0
RT @sensepost: Traditional methods of blinding EDR's are to remove hooks. In this post @vikingfr investigates a new technique (and tool) fo….
0
130
0
RT @sensepost_train: Dive into hackers' minds, methods, & tools with our immersive @sensepost Hands-on Hacking Fundamentals course at @sect….
0
4
0