MachineHunter
@InfPCTechStack
Followers
383
Following
299
Media
190
Statuses
997
Security Researcher, UEFI, Windows Kernel, TPM (RT is mainly for me to read them later...)
Joined April 2019
Slides of my #BHUSA talk Shade BIOS has been uploaded! https://t.co/19aiR4MDUk Github link is below https://t.co/WiOm3MwFHc Thank very much for attending my presentation! I’m sorry I wasn’t able to talk to many of you, as I was feeling unwell throughout the #BlackHatEvents
1
8
24
If you have info about a #security issue or vulnerability, the #UEFI USRT will help to determine the scope of the vulnerability and then assist member companies in the coordination of responses to reported vulnerabilities. Learn more: https://t.co/1b8pFVYu3Y
0
1
0
機密VMの提供が始まったっぽい。 引用: 「機密VMプラン」の提供開始のお知らせ | さくらのクラウドニュース
cloud.sakura.ad.jp
さくらのクラウドに関連するニュースをお届けします
0
33
108
メモ。Gigazine記事 Macのチップが再びインテル製に? https://t.co/AHS0Rnx0cc X86アーキテクチャに移ると言うのではなく、ArmアーキテクチャのチップをIntel工場で作るという話。トランプ政権対応らしい。 「Intel Inside(インテルはいってる)」と言えるのかな?
gizmodo.jp
いろいろ大人の事情もあるらしい。Apple(アップル)が独自に設計する最新のM5ならびにA19チップは、ほとんどがTSMCによって製造供給されています。でも、ここにIntel(インテル)がApple向けにCPUの製造を請け負うという構図が加わってくる可能性を、著名アナリストのミンチー・クオ氏が明かしましたよ! アップルとインテルが再び手を握る?いまはすっかり昔の話となってしまいましたが、Macに
0
3
4
A ton of great info here about what Apple does for their secure boot chain: “A Reverse Engineer’s Anatomy of the macOS Boot Chain & Security Architecture”
stack.int.mov
1.0 The Silicon Root of Trust: Pre-Boot & Hardware Primitives The security of the macOS platform on Apple Silicon is not defined by the kernel; it is defined by the physics of the die. Before the...
1
30
100
Even when an SD card looks completely destroyed, its data isn't always lost.💡
255
127
725
HPE showed off its next-generation AMD EPYC "Venice" socket SP7 supercomputing platform at SC25, along with its Slingshot 400 interconnect
servethehome.com
HPE showed off its next-generation AMD EPYC "Venice" socket SP7 supercomputing platform at SC25 along with its Slingshot 400 interconnect
0
15
45
🧵⬇️Low level security timeline update!⬆️ 2025-11-09 Part 1 After over a year, I've finally updated the Low Level PC/Server Attack & Defense Timeline! https://t.co/o3eq6IQzDQ The 2025 highlights are in this thread, because there are too many for a post. 👇
1
13
21
* Video, description & slides: https://t.co/CfkZtujVJ4 * Full event recap (blog post): https://t.co/EFWwt9AOzj * Upcoming events: https://t.co/tmaX9yWLZ4
3mdeb.com
"3mdeb events offer in-depth conferences and workshops focused on embedded systems and firmware development. Join us and stay updated on the latest tech news."
0
2
1
Russian hackers sneak a full Linux virtual machine inside Windows to run undetected
cybernews.com
Russian hackers are abusing Microsoft Hyper-V to create a hidden Linux virtual machine within the victim’s host, enabling them to run undetected malware.
1
6
32
The @surface UEFI feature to "sandbox" UEFI/SMM is open source and available for anyone to integrate. It includes support for QEMU. I would love to see this get integrated into @Dasharo_com or @coreboot_org tianocore payloads for increased security: https://t.co/JO9CAD7p4l
2
18
64
Windowsの新しい管理者権限保護「Administrator Protection」で、既存の「UAC Bypass」が難しくなりそうです。結構見逃されがちですが、Windowsが管理者権限を扱う方法が変わるので、マルウェア対策の観点では重要な変更です。(10月28日のWindows 11 24H2/25H2 向け KB5067036
Windowsの新しい管理者権限保護「Administrator Protection」について https://t.co/9cjwYvuKMK
3
161
510
メモ Steam、セキュアブート/TPM検出機能を追加。人気FPSの必須要件への備え https://t.co/Z1SwbUgQHu ゲームのアンチチート対策にTPMを活用しているのはVALORANTが有名だが、Steamも続く?
xenospectrum.com
Valveが運営する世界最大のPCゲームプラットフォーム「Steam」が、最新のベータ版クライアントに「セキュアブート」および「TPM」の有効状態を検出する機能を追加した。これは、今後の大型タイトルでチート対策としてこれ ... Read more
0
1
3
The Netwide Assembler 3.01 is ready and supports the full ISA of #DiamondRapids and #NovaLake: https://t.co/KIoPhulNRt
#APX #AVX10_2 #AVX10_VNNI_INT #AMX_FP8 #AMX_TF32 #AMX_COMPLEX #AMX_AVX512 #AMX_MOVRS
Nasm 2.16 #Intel #Crestmont #GraniteRapids
#AVX512_FP16
#AVX_IFMA
#AVX_VNNI_INT8
#AVX_NE_CONVERT
#RAO_INT
#CMPccXADD
#RDMSRLIST
#WRMSRNS
#PREFETCHTIT0 Only #AMX_FP16 is missing (1 instruction: TDPFP16PS) https://t.co/gWk3NNJOTo
1
18
90
China releases 'UBIOS' standard to replace UEFI — Huawei-backed BIOS firmware replacement charges China's domestic computing goals
tomshardware.com
Support for chiplets, heterogeneous computing, and a step away from U.S.-based standards are key features of China's BIOS replacement.
30
144
560
From a breadboard to a real USB device! I wired up a microcontroller and made it talk to my Mac as a serial port. 💻🔌 You can get a stable multi-Mbit/s connection with just jumper wires. The link is below. 👇
1
2
5
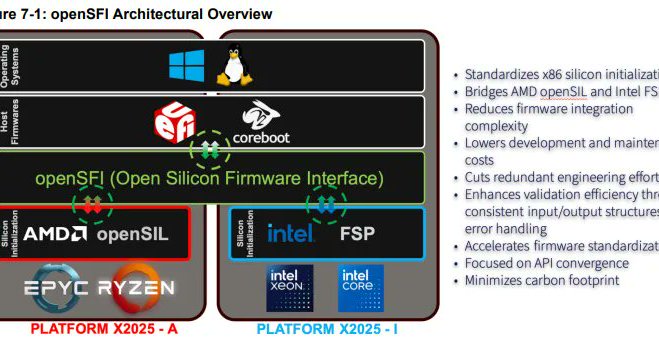
openSFI Is A Very Interesting Collaboration Between @AMD & @Intel For Better Firmware Unification Exciting! 😍 https://t.co/3Lm9djyC8C
phoronix.com
An interesting technical collaboration between AMD and Intel as well as other industry players like Google, Bytedance, Microsoft, MiTAC, HPE, and others is openSFI
0
21
75
次世代チップはレーザーで冷却 https://t.co/TvLmeG2l8d 半導体にレーザーを当てて光の形で熱エネルギーを放出させる「フォトニック冷却」技術。発熱部をスポットで冷やせるから効率が高く、放出光は電気に変換できるからエネルギーの無駄も少ない。 実用化に向けて開発が進められている(実証段階)
spectrum.ieee.org
Can lasers really cool computer chips by turning heat into light? Dive into the science behind photonic cooling and its potential to transform computing.
10
384
1K
Just got back from @osfc_io and @UEFIForum DevCon! Here’s a quick thread on our @binarly_io contributions and a few of my favorite presentations🧵
1
7
12
Pulling back the curtain on #NVIDIA GPUs - microcontrollers, isolation, threat models, and hardening. What it all means for real attackers? All of that and more in our DEF CON talk👇 https://t.co/yZJaDkI17I
#DEFCON #GPU #Security #Firmware #Hardware
Forgot to mentioned that our talk "How to secure unique ecosystem shipping 1 billion+ cores?" has been accepted to @defcon #defcon33 as well! https://t.co/OsuNhKaLu1
0
6
14