tsunekoh
@tsunek0h
Followers
870
Following
4K
Media
38
Statuses
425
Security Researcher, macOS, Arm-based Windows, @[email protected]
Joined May 2018
Looks like more MacSync: 4d751dd363298589cb436d78cd302f9d794ae1e3670722a464884be908671a9c - Zoom lookalike. thanks @malwrhunterteam :) Written in Objective-C, which is beautiful and a great start to a Monday. Look a how pretty that binja Pseudo-ObjC is.♥️ Brackets! 🧵
1
9
33
If you’re interested in how to conceal the fact that reflectively loaded in-memory payloads have no backing file, feel free to check out my reflective loader implementation (based on @patrickwardle’s one). By using this, you can specify a fake backing file.
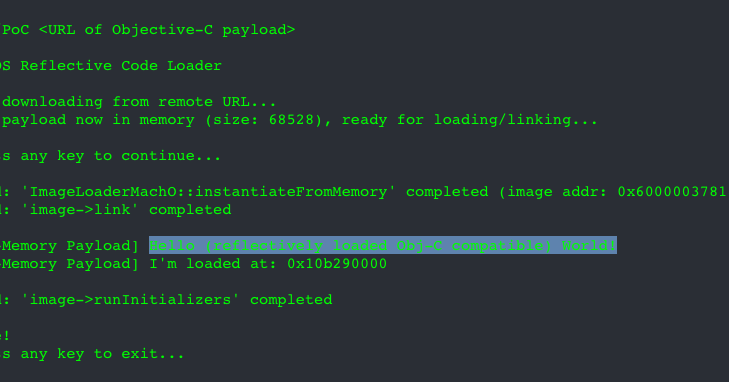
Want to run your compiled Mach-O payloads directly from memory without worrying if they'll be detected or captured? 😈 🔥 New blog post: "Reflective Code Loading on macOS (Part II)" https://t.co/ZfOjG1Quvq macOS 26? ✔️ Objective-C payloads? ✔️ Detection ideas (limited)? ✔️
1
13
68
Want to run your compiled Mach-O payloads directly from memory without worrying if they'll be detected or captured? 😈 🔥 New blog post: "Reflective Code Loading on macOS (Part II)" https://t.co/ZfOjG1Quvq macOS 26? ✔️ Objective-C payloads? ✔️ Detection ideas (limited)? ✔️
objective-see.org
Apple silently 'broke' in-memory code loading on macOS ...let's restore it!
1
48
125
I've updated the XPRSecretConfig repository. https://t.co/f4Pi74q7vo This repo tracks XProtect Remediator's encrypted hidden configurations, such as YARA rules, regular expressions, and file paths. I'll continue monitoring how XPR evolves.
github.com
0
5
22
@L0Psec Just wait, mind-blowing swift is already on-deck for the next release! (my co-workers cringing at me over-promising...)
1
1
12
The writeup to our #OBTS talk “CrashOne - A Starbucks Story - CVE-2025-24277“ with @gergely_kalman is up at Iru’s website. This was a cool sandbox escape + lpe on macOS. https://t.co/Vd6sRJzyk0
the-sequence.com
Researchers uncover and exploit CVE-2025-24277, a macOS osanalyticshelperd sandbox escape and privilege escalation flaw.
2
14
57
@nullcon is one of the best conferences I've been to, I highly recommend submitting!
Submit your CFP for #NullconGoa2026 & share your cutting-edge research, breakthrough hacks, or next-gen security innovations with the global hacker community. CFP Deadline: 20th November 2025 Speaker Benefits / Submission Guidelines: https://t.co/ovC2vyqTZZ
#CFP #cybersecurity
0
1
4
Apple also introduced new APIs to implement the Conductor scanner. In this update, the GKTicket, XPCloudKitAPI, GKHash, and XPTicketDatabase classes were newly added to XPPluginAPI.
0
0
5
But I’m not entirely sure about this, though — if anyone has more information on this behavior, I’d really appreciate hearing from you.
2
0
5
I suspect some bugs in macOS prior to 15.4 may have caused these inconsistencies, and the Conductor scanner was introduced to resolve them.
1
0
4
I haven’t analyzed all of its behavior yet, but the scanner seems to delete entries in the Ticket database if the fetched tickets are not revoked. So, it appears to be designed to fix inconsistencies between the local Ticket database and the fetched tickets.
1
0
5
If it finds such hashes, it fetches the corresponding tickets using the CloudKit API.
1
0
4
It opens the /var/db/SystemPolicyConfiguration/Tickets database, which contains registered notarization tickets (see https://t.co/QUT7rCYGz5), then searches for revoked entries using “SELECT hash, hash_type FROM tickets WHERE (flags & ?1) != 0.” (where ?1 is bound to 1).
redcanary.com
Gatekeeper is the centerpiece of Apple’s effort to protect macOS users from malicious software and other untrusted code.
1
0
5
The scanner first checks if the OS version is greater than 15.4. If so, it always returns the status “Success,” then exits. Otherwise, it performs remediation actions. (2/n)
1
0
5
Last week, Apple updated XProtect Remediator from version 153 to 156. In this update, Apple added a new scanner called Conductor. I finally had time to analyze this scanner, so I’d like to share some of the details in this post. (1/n)
3
13
45
The new "XPScripts.yr" file mentioned by @howardnoakley is potentially interesting. 2 Yara rules related to AppleScript (osascript). One for browsers and another for known crypto wallets.
Apple has released updates to XProtect and XProtect Remediator https://t.co/tE4PZ6pLcI via @howardnoakley
0
4
20
#OBTS was so much fun! I had the chance to attend some amazing talks and gained new insights that inspired fresh ideas for my future research. I also received valuable feedback on my own work, which gave me several points to re-examine. I’ll be tackling them one by one.
1
3
20
Slides from my #OBTS v8 talk "Dylib Hijacking on macOS: Dead or Alive?" 🍎☠️🤔 https://t.co/57Pjtvlnzt Turns out that dylib hijacking is (still) alive and well on macOS (26 included) due to three issues/flaws in Apple's mitigations
speakerdeck.com
Over a decade ago, a much younger Patrick revealed how macOS (née OS X) was vulnerable to what had long been considered a Windows-only attack: dynamic l…
1
24
102