Daniel Tan
@DanielSlothx
Followers
200
Following
1K
Media
96
Statuses
400
Web3 security researcher | Smart contract audit lead | Saved $200K tokens from the Phemex CEX hack | Contributor to audit agent @AgentLISA_ai
Blockchain
Joined February 2010
#HackerLostFunds Due to the hacker took his/her own funds(21 $BTC and 152K $XRP) into the attack, after the liquidation, the hacker's $2.7M assets were reduced to zero.
0
0
1
#VenusRescue The @VenusProtocol team RESCUED $13M stolen funds from the hacker by force liquidating the hacker's collateral that included the hacker's own $2.7M, due to the hacker deposited the stolen assets back to the Venus protocol in the attack. https://t.co/h0jsun5RS4
1
0
1
#Monero 51% hashrate experiment. #Qubic announced that they achieved over 51% hashrate dominance, resulting in six blocks being reorganized and sixty blocks orphaned on the Monero chain.
Another busy but historic week in Qubic! During the Epoch 173 we have reached over 51% of total Monero hashrate and earned over $240k in mining rewards. Profitability report is in the link below⏬
0
0
1
3⃣Missing slippage control in tax swap leading to potential loss of funds https://t.co/ub8ok35fmj The corresponding Code4rena Virtuals protocol competition reward result:
0
0
0
All 3 vulnerabilities: 1⃣Unrestricted access to addValidator allows anyone to add validators https://t.co/uDuLvFf5QC 2⃣Burning tokens does not decrease the total supply, leading to incorrect accounting. https://t.co/D18XA7SXkd
1
0
0
Then just wait a few minutes for the #AgentLisa scan results, submit it to #Code4rena and earn rewards $$$ 🤑🤑🤑💸💸💸💵💵💵 https://t.co/mDxa8sCVab
1
0
2
To re-produce how the audit agent #AgentLISA find the bug, we just need to copy paste the repository of the virtuals protocol audit competion to the LISA chat box, then select the target smart contract(s) https://t.co/T1YNVNVsS6 2/n
1
0
2
#AgentLisa It is interesting and unbelievable that the audit agent @AgentLISA_ai makes me find 1 high bug and 2 medium bugs on the #Code4rena #Virtuals protocol audit competition and earn a total $39 reward. @code4rena @virtuals_io 1/n https://t.co/mDxa8sCVab
2
0
14
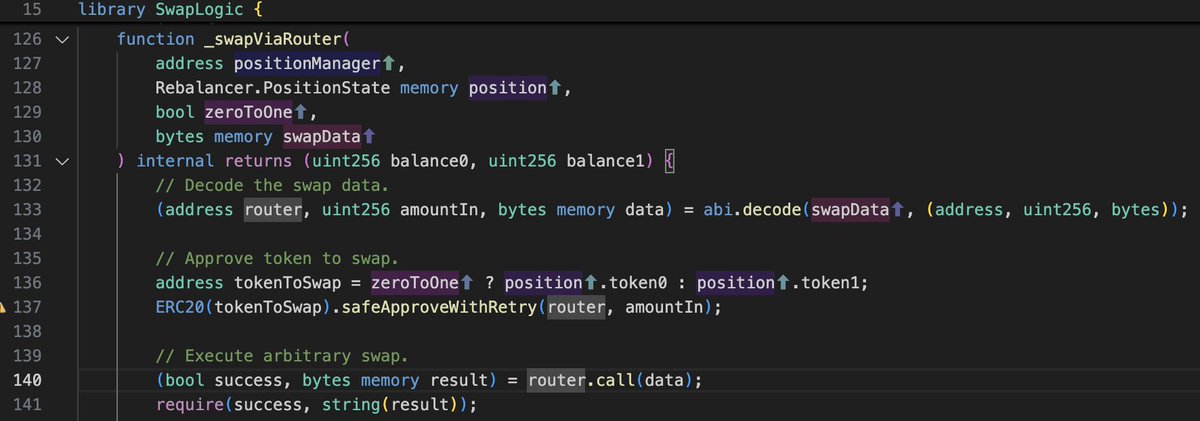
#ArcadiaFi $3.5M hack. I always try to summary a hack into one tweet, but this time it seems hard for this one due to the the hack traverses many contracts. Under the hood, an unchecked malicious `router` address is injected to drain the victims' asset.
🚨 On 15th July 2025, Arcadia Finance (@ArcadiaFi) was exploited for ~3.5M USD due to an unchecked external call in SwapLogic._swapViaRouter(). Read the full hack analysis here: https://t.co/F6qw02OEnL
0
0
2
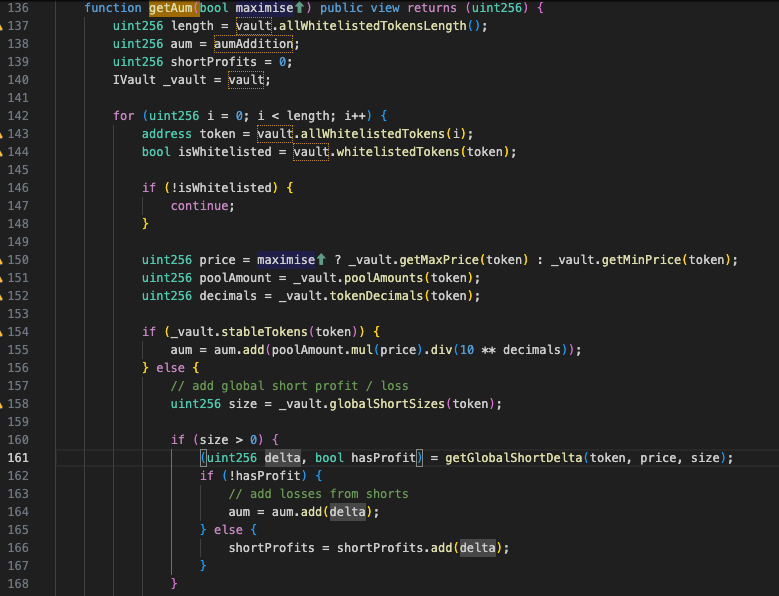
#GMX $40M hack. A hacker manipulates the AUM(Assets Under Management) value that determines the GLP value after minting the GLP and before unstaking GLP by reenter the GMX:Vault to get profit.
0
0
1
Product link: https://t.co/pii8g0ScVv Scan 3+ contracts with LISA (free credits: LISAGOLIVE). Use AgentLisa to safeguard your or your clients' smart contract(assets)!
agentlisa.ai
LISA is an LLM-powered Intelligent Security Analyzer for Solidity Smart Contracts
0
0
0
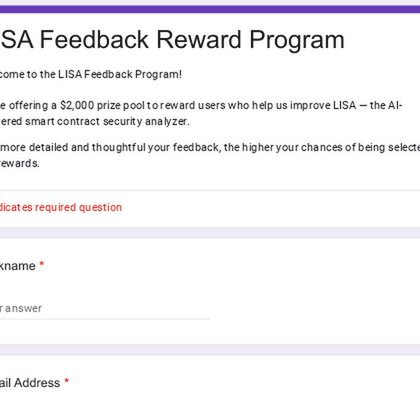
#AgentLISA is an LLM-powered smart contract analyzer that achieves 90% Detection on OWASP Smart Contract Top 10. We’re offering $2,000 in rewards to users who share actionable feedback to help us improve! https://t.co/IIOs7j4O3F
docs.google.com
Welcome to the LISA Feedback Program! We're offering a $2,000 prize pool to reward users who help us improve LISA — the AI-powered smart contract security analyzer. The more detailed and thoughtful...
1
0
1
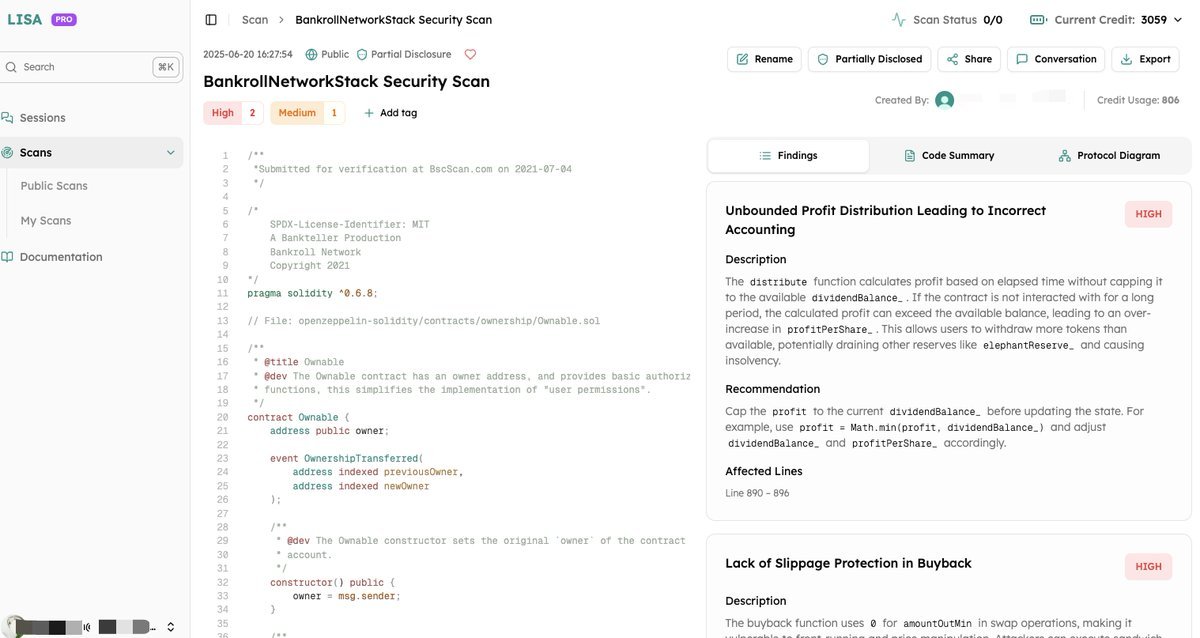
#Bankroll expoit. An reward calculation error in the `distribute` function resulted in a total loss of $65K, which is detected by an AI Audit platform @AgentLISA_ai ( https://t.co/pii8g0ScVv).
#AI is unbelievable. #LISA #AIAudit
🔍 #LISA detects the critical vulnerability behind @Bankroll_Status' $65K loss. The flaw lies in the `distribute` function: profit calculations weren't capped to the available `dividendBalance_`, leading to inflated rewards and reserve drainage (e.g., `elephantReserve_`). 💡
0
0
0
Another analysis from @neeksec
https://t.co/FJYKXP82zN
After investigating the Cetus exploit transaction, I believe I have identified the root cause of the bug. The issue stems from a type casting from u256 to u64 within the get_amount_by_liquidity function.
0
0
2
#Cetus $223M exploit. Under the hood, an arithmetic overflow issue in the `checked_shlw` function was exploited by the hacker to gain extra liquidity when adding the liquidity, which results in $233M loss($162M of them has been frozen)
.@CetusProtocol was reported to have suffered a security incident resulting in a loss of ~$223M: $162M worth of funds has been frozen on the #Sui, while $60M has already been transferred to #Ethereum. Due to the lack of advanced forensic tools comparable to Phalcon Explorer
1
0
3
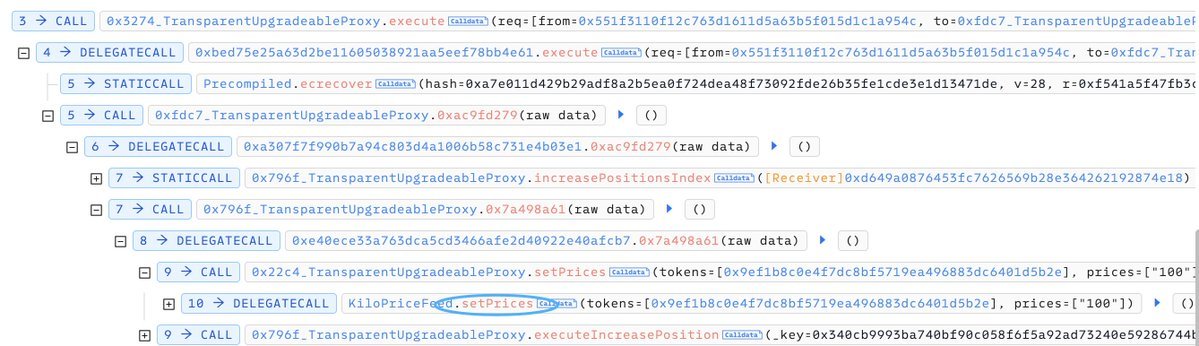
#KiloEx $7.4M exploit. A hack exploited the `MinimalForwarder` contract, using a forged signature to impersonate trusted roles, due to the critical access control flaw in the contract, and gained unauthorized access to the `KiloPriceFeed::setPrices()` function & manipuated prices
🚨 Security Incident Announcement: KiloEx Vault Exploit Dear KiloEx Community, We regret to inform you that the KiloEx Vault has been exploited. The attacker’s wallet address is: 0x00fac92881556a90fdb19eae9f23640b95b4bcbd We urge all partner protocols and platforms to
0
0
4
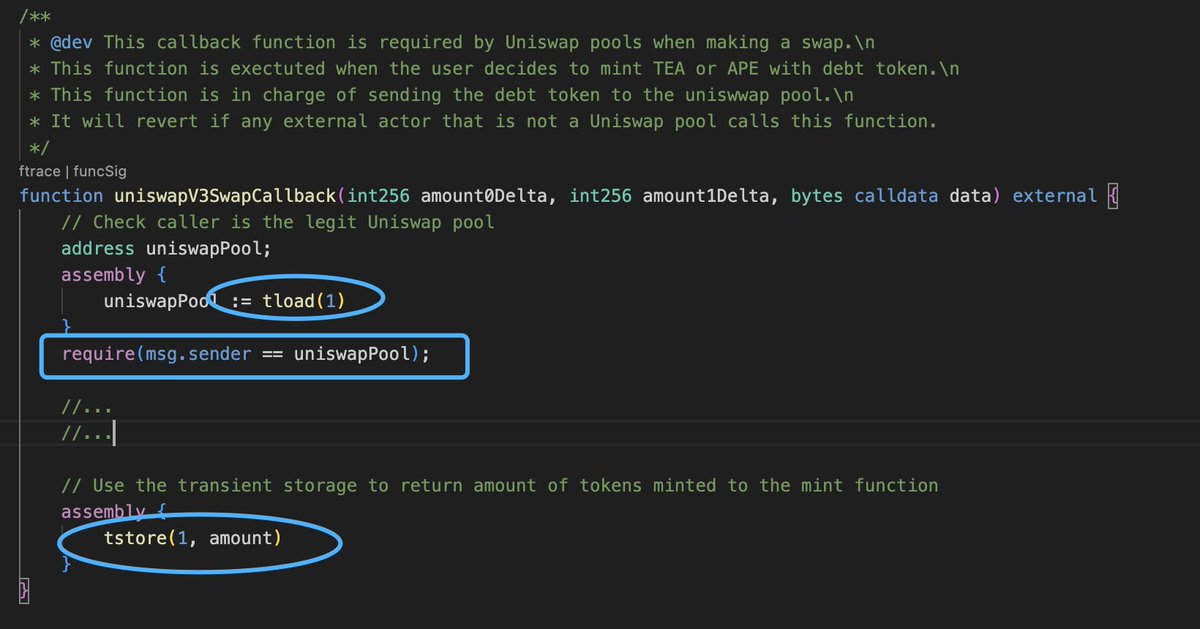
#SIR exploit. A hacker manipulated the value stored on the #transientstorage to by-pass the caller check, due to the check condition loads value from the transient storage, which was manipulated by the hacker due to the contract does not clear the transient storage at right point
So we go the worst news a protocol could received and got hacked for our entire TVL ($355k). I (@Xatarrer) would like to not throw the towel here as I truly believe in SIR. If you also believe in the core protocol and have any idea on how to proceed forward, please DM.
0
0
0
#Bybit exploit. On February 21, 2025, a hacker compromised Bybit's Safe multi-sig wallet frontend, resulted in $1.4B asset loss The #Sygnia report indicates its root cause was malicious code from #Safe{Wallet}'s infrastructure. No compromise was detected within Bybit's systems
Bybit Hack Forensics Report As promised, here are the preliminary reports of the hack conducted by @sygnia_labs and @Verichains Screenshotted the conclusion and here is the link to the full report: https://t.co/3hcqkXLN5U
1
0
0
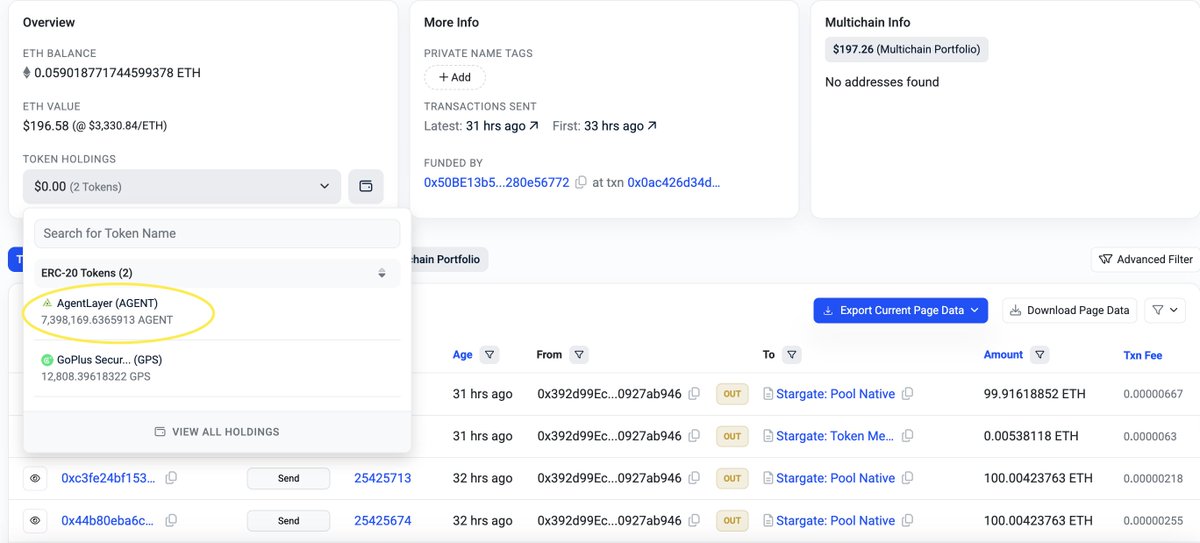
#Phemex attack. We saved $200K worth tokens from the Phemex hacker by quickyly blacklisting the hacker before the hacker dumping the tokens.
AGENT Token Security Update Our team has successfully blacklisted hacker's wallet addresses to prevent further transfers and attacks. We've implemented robust security measures to protect the onchain assets, ensuring that AGENT token remains secured. https://t.co/SpYyjdvxLE
4
1
11