SolidityScan
@SolidityScan
Followers
4K
Following
2K
Media
733
Statuses
3K
Automated smart-contract auditing platform by @credshields
Joined June 2022
🚀 Big news! SolidityScan is now integrated with @soneium, bringing seamless smart contract security to your fingertips. Easily access security scores, gain real-time insights into vulnerabilities, and explore full threat reports — directly from verified contracts on Soneium.
4
1
25
Expected behavior: Users can withdraw up to 50% of their current balance. Actual behavior: Something’s off…. Can you spot the bug that’s breaking the logic? 🔍. Join the #FindTheBug challenge and put your smart contract skills to the test!. #SmartContracts #BugHunt #Web3
3
0
3
RT @CredShields: 🚨 We’re now LIVE!. Join CredShields and @HackenProof for an AMA on the future of Web3 protection: Crowdsourced Security vs….
0
3
0
@SuperRare Hack Metadata:. On Ethereum. Attack Transaction: 0xf5b6531ead5023568b5063b131068a6dd4d8c9eac66a51666982d99af1a0d520. Attacker's Address: 0x5B9B4B4DaFbCfCEEa7aFbA56958fcBB37d82D4a2. Victim Contract (RareStakingV1): 0xfFB512B9176D527C5D32189c3e310Ed4aB2Bb9eC. Stolen funds are still.
0
0
1
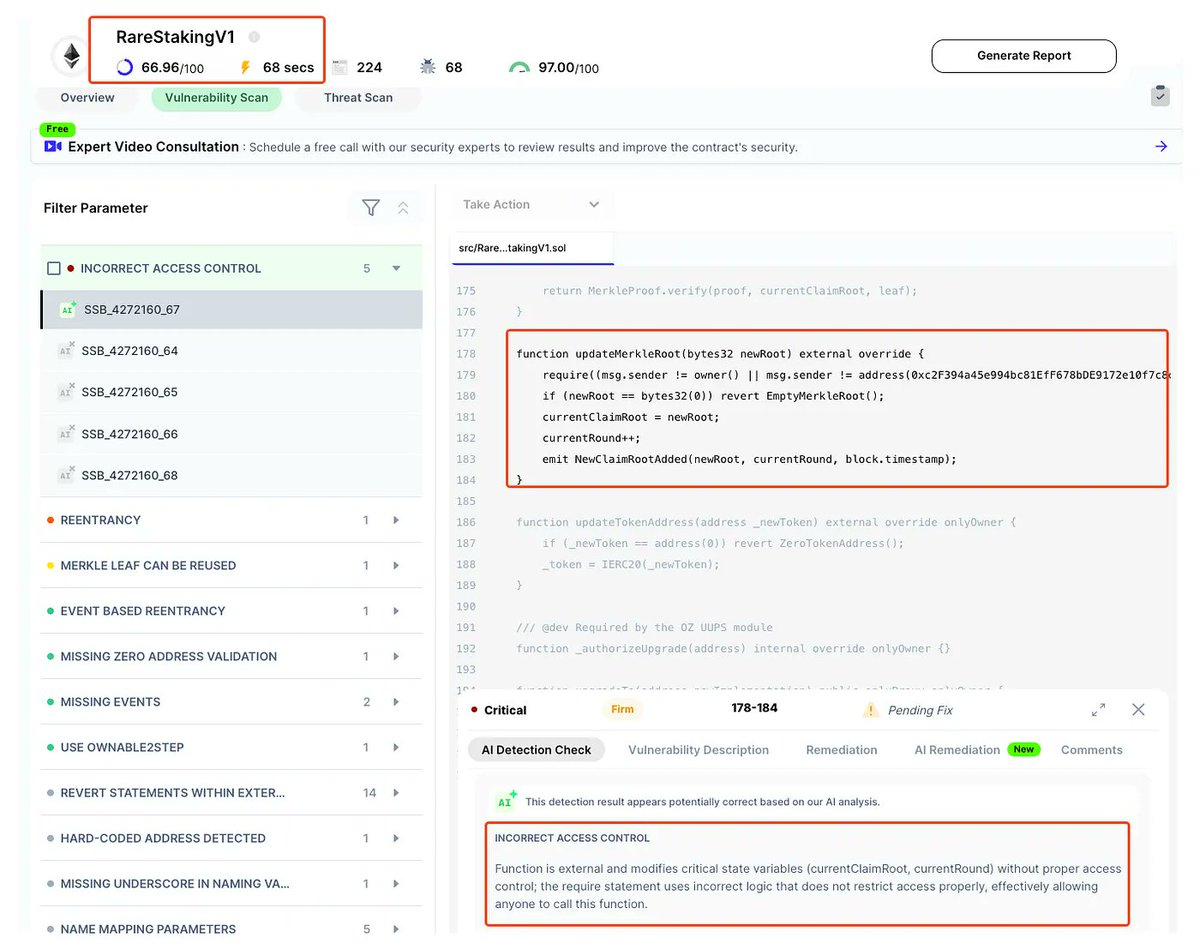
On 28th July, 2025, SuperRare's (@SuperRare) RareStakingV1 contract was hacked, losing ~$730K USD (~11.9M $RARE) due to a flawed access control in updateMerkleRoot() function's require check. SolidityScan was able to detect SuperRare's access control bug in just one scan!
6
4
11
RT @CredShields: 🚨 Live now!. Join CredShields and @Resonancesec as we break down the Arcadia Finance Hack and its impact on smart contract….
0
2
0
RT @CredShields: CredShields and @Resonancesec are unpacking the Arcadia Finance Hack — diving deep into what went wrong, key takeaways, an….
0
2
0
Bob just patched the classic Uniswap V2 oracle library by upgrading it to pragma solidity ^0.8.0. He says it protects against old arithmetic bugs. Can you spot the high-risk bug?. Take on the #FindTheBug challenge and uncover the flaw!. #SmartContracts #BugHunt #Web3
1
0
7
@ArcadiaFi A malicious contract abused the Rebalancer’s trusted context to drain funds from healthy user accounts. 📍 Victim Contract (RebalancerSpot):. 📤 Attack Transaction:. 🕵️♂️Attacker Address:.
basescan.org
Aggregated Transfer of 11 NFTs Across 2 Tokens | Success | Jul-15-2025 04:05:45 AM (UTC)
0
0
3
🚨 On 15th July 2025, Arcadia Finance (@ArcadiaFi) was exploited for ~3.5M USD due to an unchecked external call in SwapLogic._swapViaRouter(). Read the full hack analysis here:.
The team is aware of unauthorized transactions via a Rebalancer. Remove all permissions for asset managers. More information will follow.
3
1
9
🚨 Bitcoin hits $122K! 🚨. A new all-time high for the world’s largest crypto. Institutional demand is surging, ETF inflows are booming, and $122K could just be the beginning. The next phase of crypto is officially underway. #Bitcoin
0
1
6
@GMX_IO The attacker abused ETH refund logic in executeDecreaseOrder() and exploited stale AUM calculations in GLP pricing—manipulating unrealized short losses to inflate AUM and redeem GLP for more than it was worth. Here are all the addresses involved in the hack:. Victim Contracts:.-.
0
0
4
🚨 On July 9, 2025, GMX (@GMX_IO) V1 was exploited for ~$42M after a malicious contract hijacked execution flow in a refund-based reentrancy-like vulnerability. Read Full GMX Hack Analysis:
blog.solidityscan.com
Overview:
1
2
7
CredShields is on the ground at @EthCC 2025!. EthCC[8] is underway in Cannes, France, and we’re excited to be part of the action from June 30 to July 3. Join us to explore how CredShields is helping secure the next generation of blockchain projects through cutting-edge audit
0
1
2