Verichains
@Verichains
Followers
6K
Following
263
Media
77
Statuses
316
A leading finance security firm, trusted by top clients such as Binance, Bullish, Bybit, Galaxy Digital, BNB, Polygon, SUI, Aptos and many banks.
Joined March 2018
Verichains is glad to have helped unveil the root cause behind the largest Web3 hack—$1.4 billion on @Bybit_Official’s Multisig @Safe Wallet! This hack is a strong wake-up call as Web3 security isn’t just about on-chain transactions or smart contracts — it also relies on
Bybit Hack Forensics Report As promised, here are the preliminary reports of the hack conducted by @sygnia_labs and @Verichains Screenshotted the conclusion and here is the link to the full report: https://t.co/3hcqkXLN5U
5
7
49
The successful use of our Revela tool to analyze the exploit and scan for similar vulnerabilities across the Sui ecosystem demonstrates the power of advanced decompilation tools in post-incident analysis and vulnerability detection. By enabling rapid identification of issues,
0
0
5
We applaud the @SuiNetwork team for their swift action in leveraging our Revela tool to identify and alert affected projects. Their fast response not only mitigated immediate risks but also set a strong example of responsible security coordination for the broader ecosystem.
1
0
5
⚠️ Note: All mentioned projects have since upgraded to fix the issue. This post is intended as a transparency measure and public awareness effort. ⚠️ Turbo Finance is a special case. While the vulnerable function was not actively used, it was present in the deployed contract,
0
0
4
🔍 Our investigation using our Revela-next uncovered the same math flaw from the $260M Cetus exploit in @KriyaDEX, @FlowX_finance, and @Turbos_finance on @SuiNetwork. 🛠️ All projects have already fixed & upgraded their contracts. Read more:
blog.verichains.io
Cetus attack reveals broader risk — Kriya, FlowX, and Turbo Finance were vulnerable too.
3
3
14
🚨 URGENT: The $260M Cetus Protocol hack exposed a vulnerability in math library which could be used by other projects. We've already identified a few projects likely also vulnerable. Make sure to review your code NOW to prevent similar exploits happen. Details:
3
7
14
The root cause is a wrong constant in the overflow check of checked_shlw(u256) math function, which was meant to prevent 256-bit values from wrapping when shifted left by 64 bits. Because that constant is too large, sufficiently big shifts silently wrap modulo 2²⁵⁶, collapsing
0
0
3
We have updated our blog with more details of the exploited venerability. Note that this vulnerability may affect other projects that use the same vulnerable math function.
0
0
2
https://t.co/NxaGMq81Lz Watch Revela-next, our AI-assisted Move decompiler, in action as it dissects the Cetus Protocol and demonstrates how Revela helps identify critical flaws in smart contract logic!
0
1
3
🚨 Just released: Our analysis of the $260M exploit targeting @CetusProtocol on the @SuiNetwork! Using our Revela-next AI-assisted Move Decompiler, we uncovered how attackers exploited a flaw in liquidity math to drain funds. Learn the details and key takeaways to secure your
8
17
70
OP_NET 🤝 VERICHAINS We’re proud to partner with @Verichains, a proven leader in blockchain security 🛡 Security isn't optional for Bitcoin’s future. It’s the foundation everything is built on. Together, we are making OP_NET’s Bitcoin-native smart contracts and DeFi safe and
103
239
408
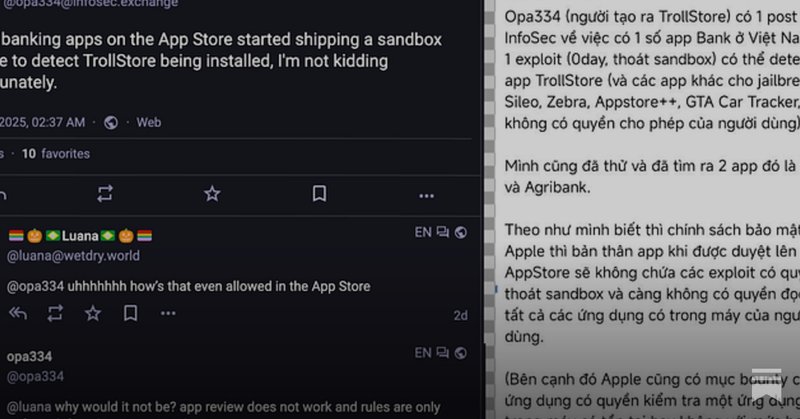
We have just published an analysis on the technique currently exploited by certain Mobile Banking Apps on the Apple App Store to scan installed applications on users’ iOS devices without their consent. Works on all/latest iOS versions. https://t.co/JWumvNuqUJ
blog.verichains.io
Technical analysis reveals that BIDV and Agribank mobile banking apps exploit private iOS API side channel issue to detect other apps installed on users’ iPhone/iPad devices.
1
7
28
During our investigation of the Bybit incident involving the Safe{Wallet} UI backdoor, we quickly developed a minimal interface for interacting with Safe smart contract wallets. This lightweight tool offers essential functionality for Safe Protocol interactions via a simple
2
6
24
Amid the $1.5B Bybit hack, secure crypto management is vital. Our lightweight interface lets you easily interact with Safe smart wallets without the official UI. https://t.co/KvrsCYMqIj
#SafeProtocol #Crypto
github.com
Minimal UI to work with Safe Protocol. Contribute to verichains/safe-protocol-minimal development by creating an account on GitHub.
1
4
10
@Bybit_Official @safe tldr; The benign JavaScript file of https://t.co/Vp8djEl1UA appears to have been replaced with malicious code on February 19, 2025, at 15:29:25 UTC, specifically targeting Ethereum Multisig Cold Wallet of @Bybit_Official. The attack was designed to activate during the next
1
0
9