Jai Minton
@CyberRaiju
Followers
7,009
Following
1,199
Media
256
Statuses
1,038
An Australian researcher who does cyber things | Defender @HuntressLabs | Former Principal @CrowdStrike | | Posts = own views.
XwkhWh9sd1BNcxIhUR9vdQJgZgM=
Joined April 2018
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
#บางกอกคณิกาep3
• 221011 Tweets
#WeAreSeriesEP7
• 206329 Tweets
PondPhuwin WeAre EP7
• 77881 Tweets
Robert Fico
• 52866 Tweets
#Aぇヤンタン
• 49556 Tweets
サーティワン
• 43623 Tweets
Slovakia
• 41672 Tweets
バッカーノ
• 22542 Tweets
よくばりフェス
• 18556 Tweets
PIERROT
• 16712 Tweets
$MISTY
• 15355 Tweets
松本健吾
• 15326 Tweets
キダ・タローさん
• 15314 Tweets
Bコース
• 13327 Tweets
#水曜日のダウンタウン
• 12644 Tweets
トネリコ
• 12490 Tweets
スロバキア
• 11898 Tweets
Aコース
• 10393 Tweets
リリムハーロット
• 10270 Tweets
FGOフェス
• 10207 Tweets
水銀体温計
• 10005 Tweets
Last Seen Profiles
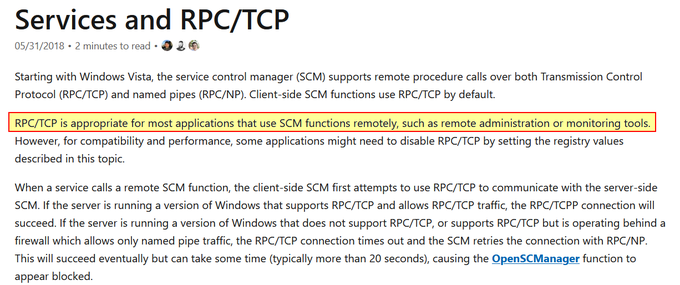
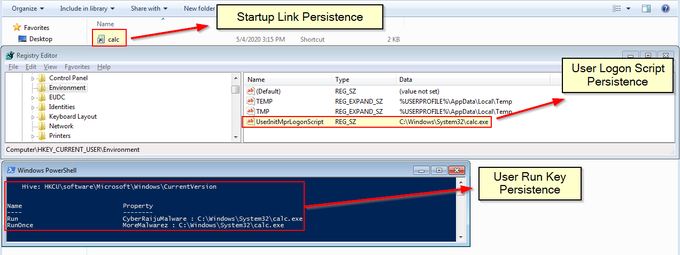
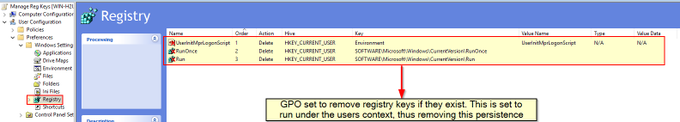
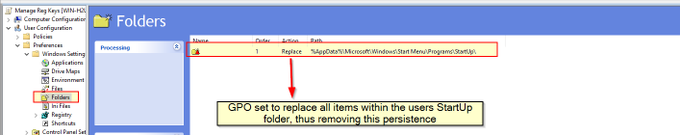
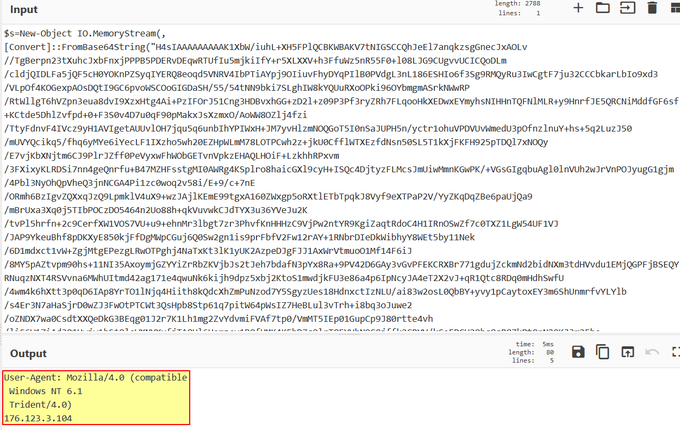
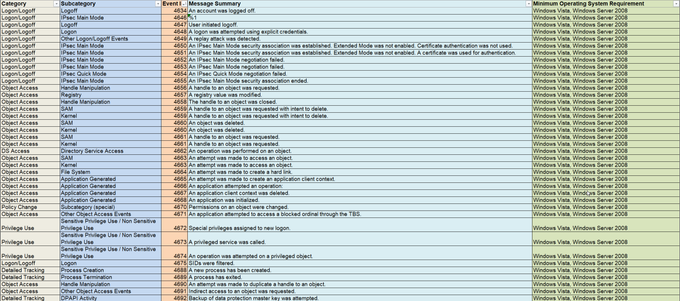
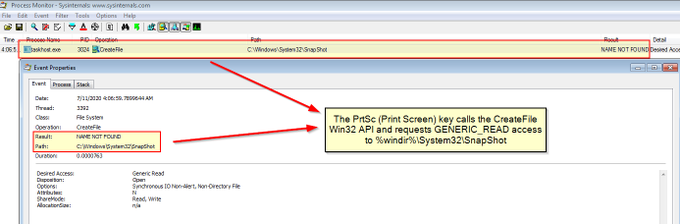
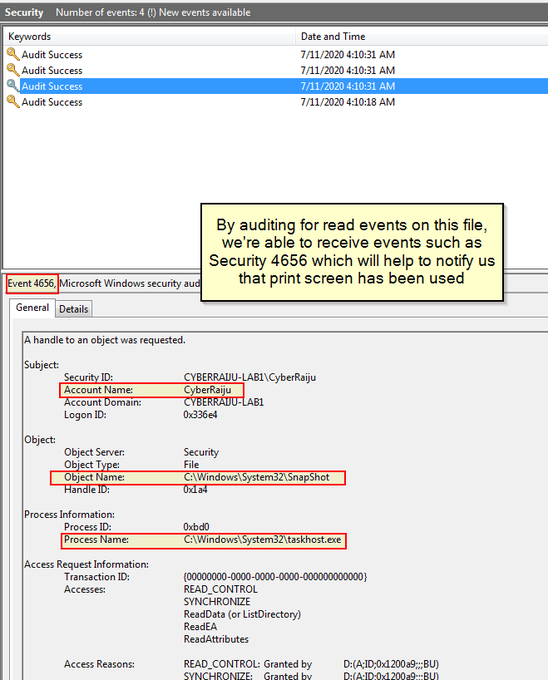
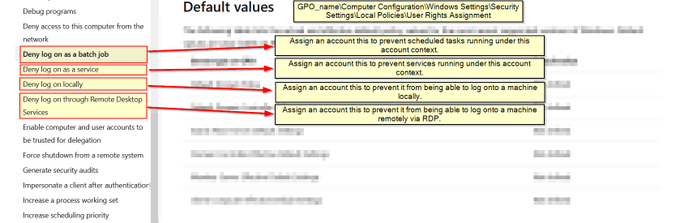
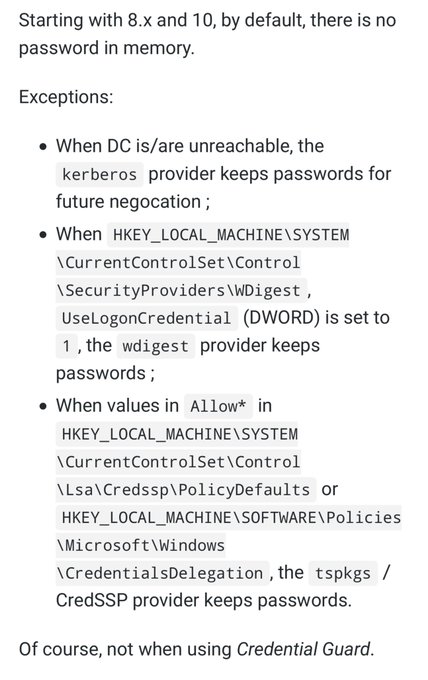
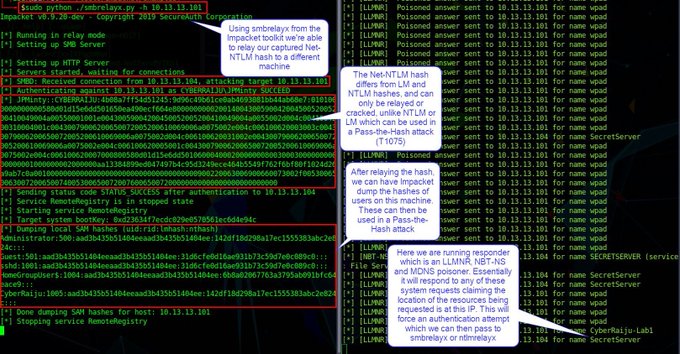
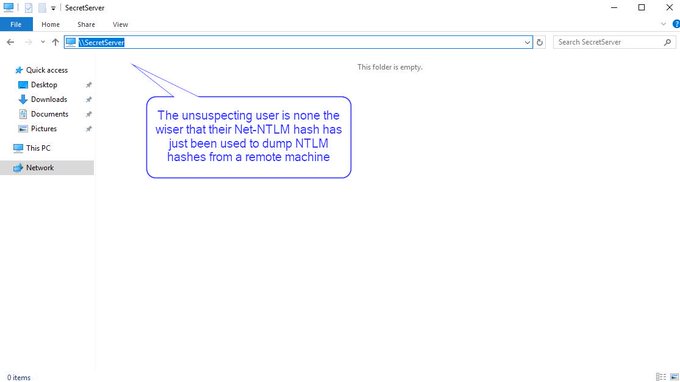
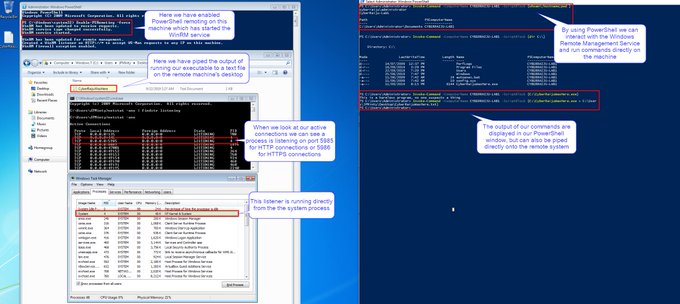
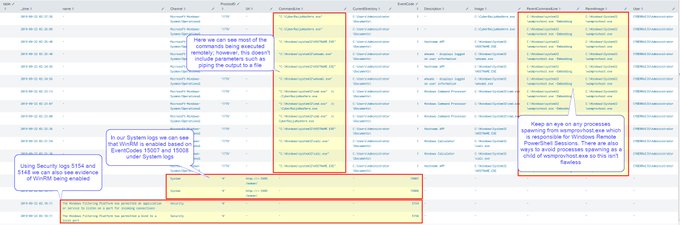
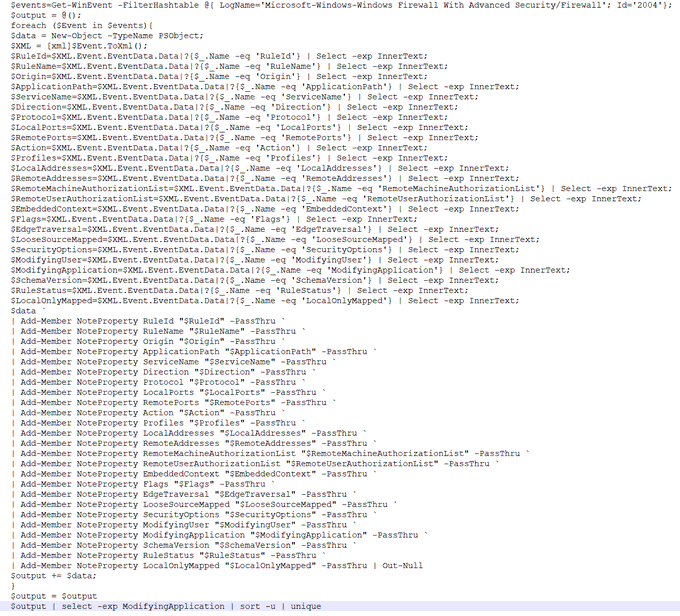
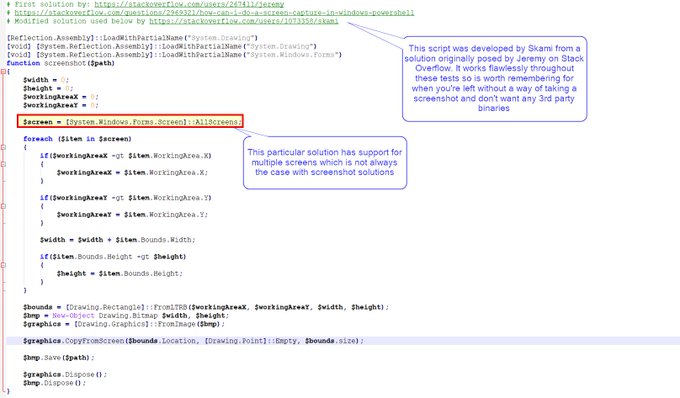
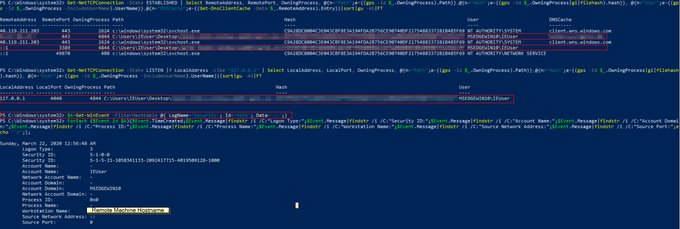
I've been compiling a Windows
#cheatsheet
of common commands and areas of interest for
#DFIR
including common tool-sets (more information to come). This can be found below, any comments or feedback is always welcome.
35
364
806
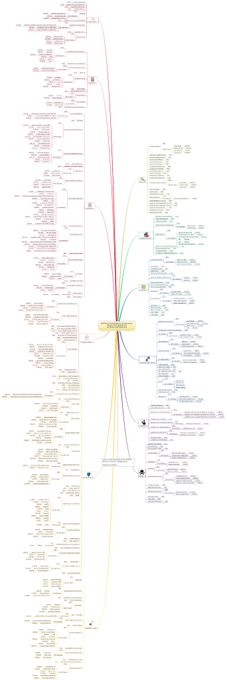
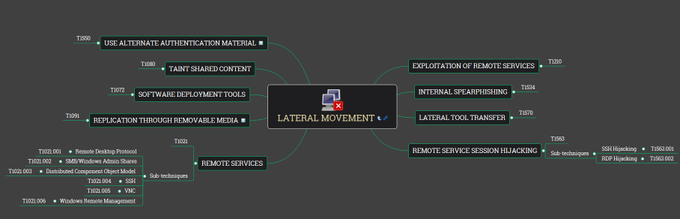
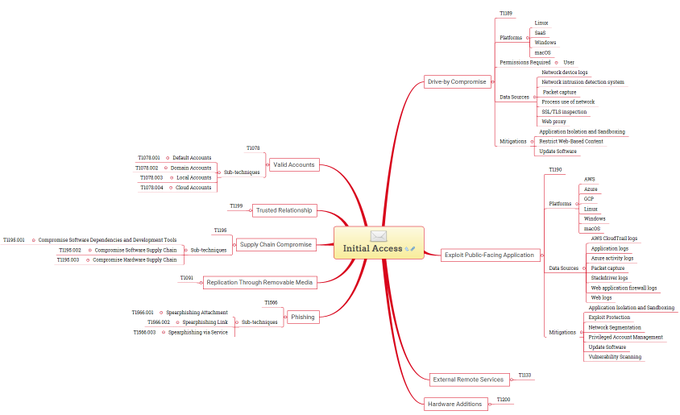
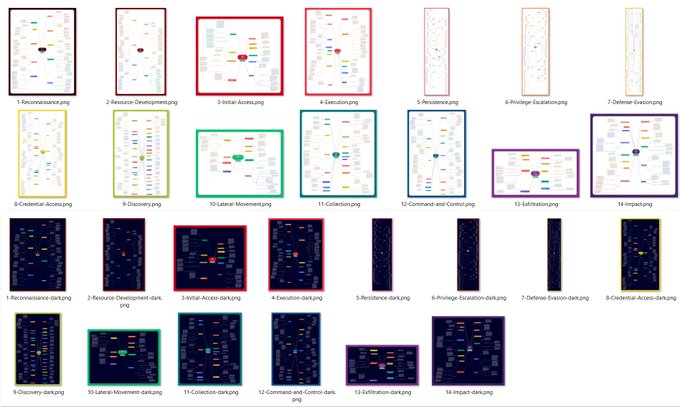
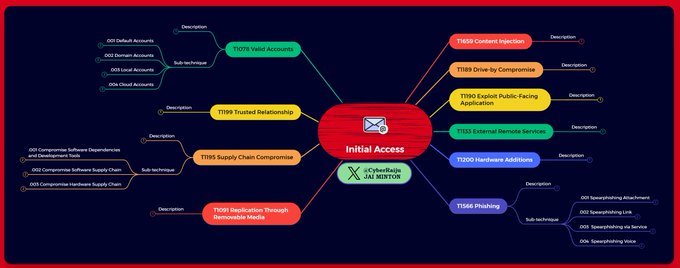
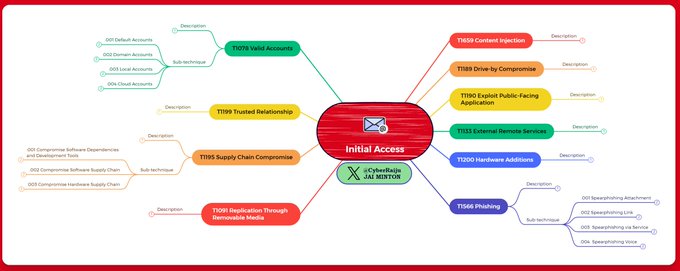
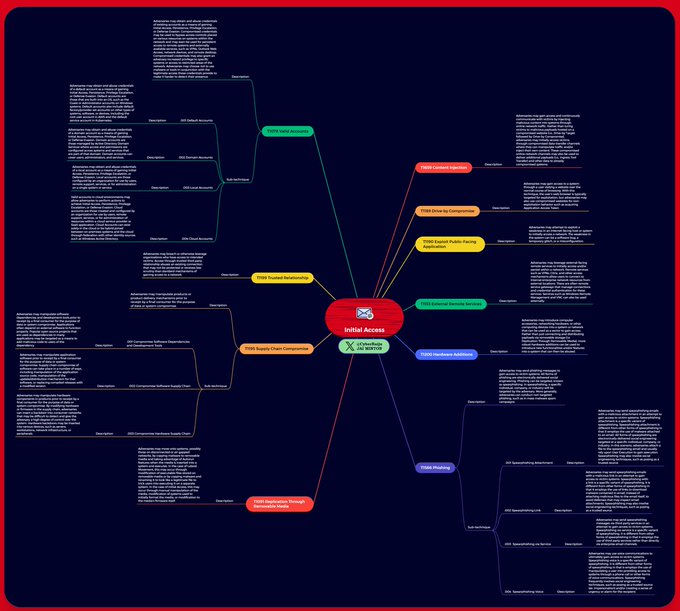
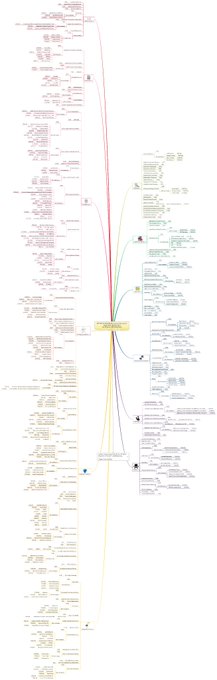
MITRE ATT&CK Mind Maps!
I've mapped the latest MITRE ATT&CK techniques, sub-techniques and IDs to a mind map and made it available.
Freemind (no colour) and XMind formats + PNG download.
Colours mapped to
@olafhartong
's "The ATT&CK Rainbow of Tactics"
4
134
379
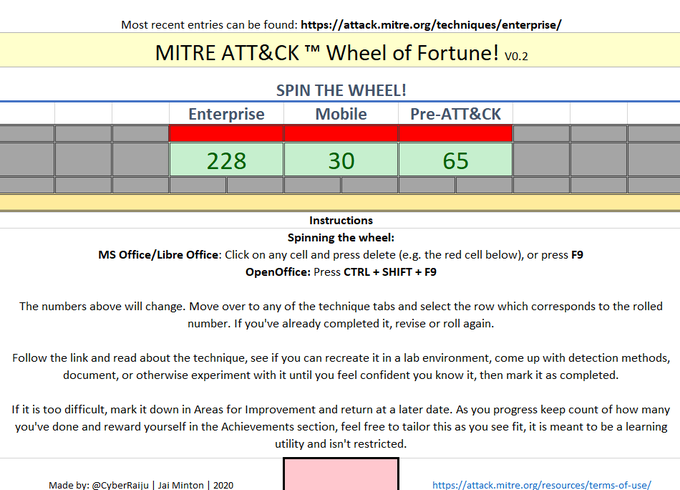
Let's use MITRE ATT&CK™ as a learning tool.
I threw together MITRE ATT&CK Wheel of Fortune. This is a spreadsheet which uses NO macros and helps select an ATT&CK method to learn, and track your progress.
#MentoringMonday
This can be downloaded below:
1
87
222
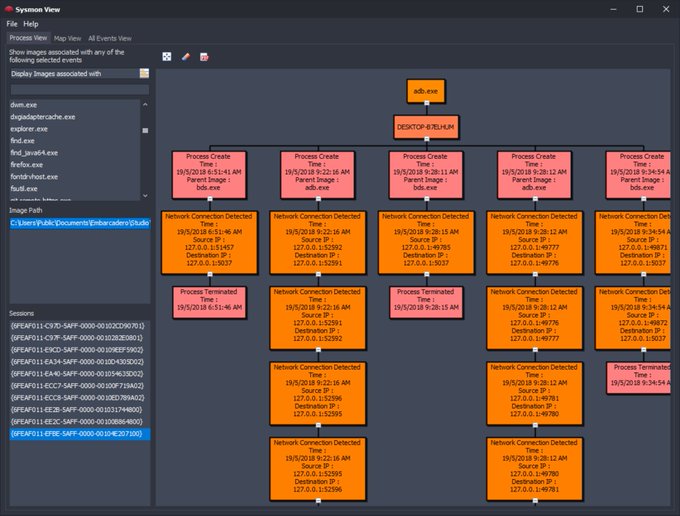
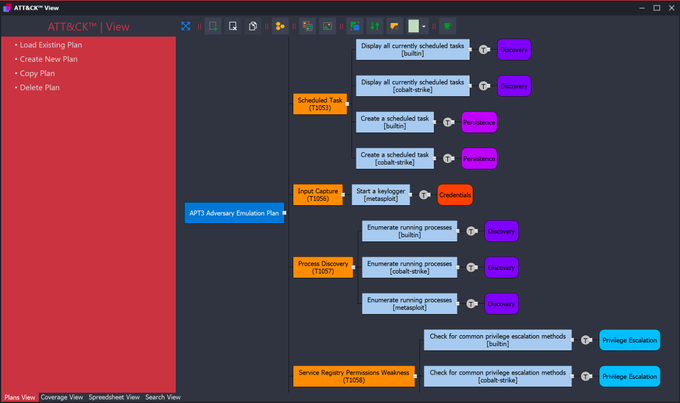
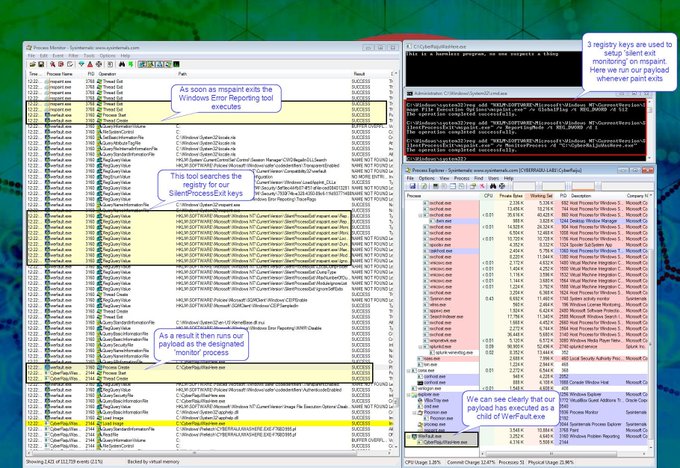
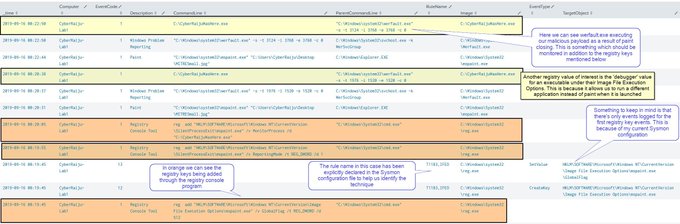
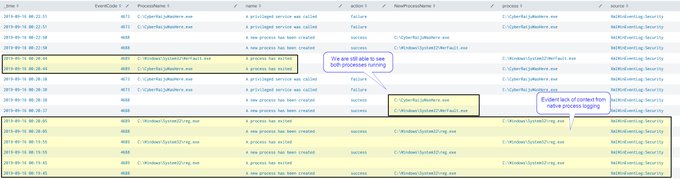
For those using Sysmon or MITRE in their analysis, I'm going to point you in the direction of
@nader_shalabi
and the excellent tools he's created for working with these.
This includes Sysmon View and ATT&CK™ View as shown below.
0
83
207
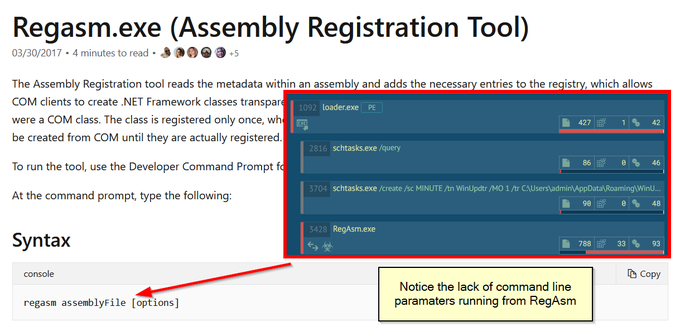
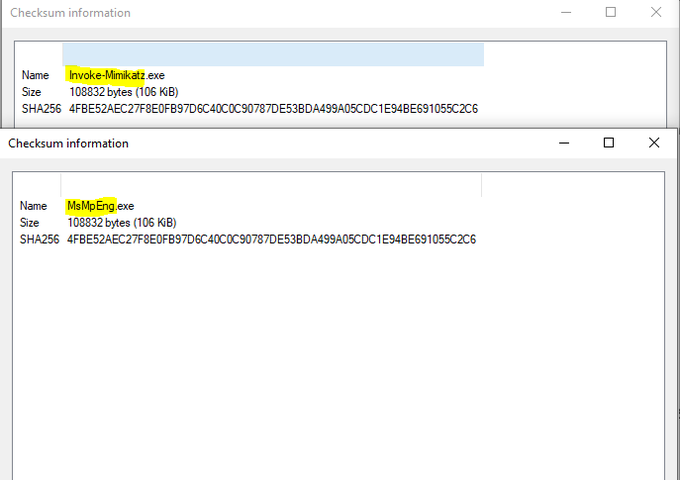
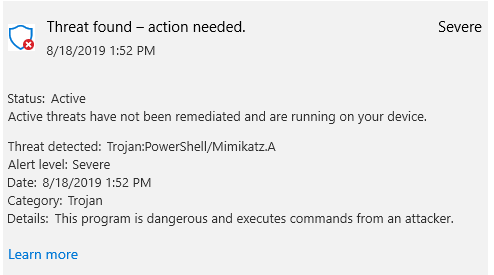
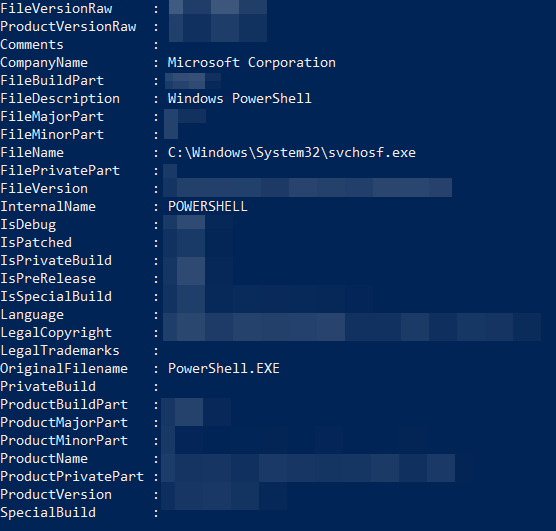
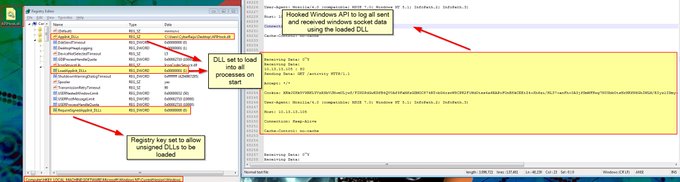
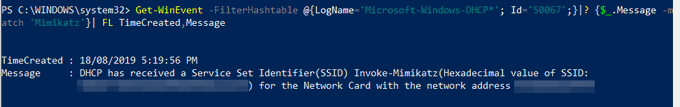
Created a copy of the MsMpEng.exe (Windows Defender Antimalware Service), renamed it to 'Invoke-Mimikatz', and Windows Defender is now a "Trojan". Defender doesn't like seeing Invoke-Mimikatz in a command line. Even the signed Defender executable isn't safe. Beware the
#mimikatz
.
18
58
137
Brief update, given the popularity, the Windows
#DFIR
and
#IncidentResponse
#Cheatsheet
has been updated including additional header highlighting for readability and will no doubt continue to grow. This is now on a custom domain with a redirect setup.
1
46
106
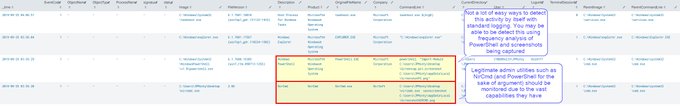
@GossiTheDog
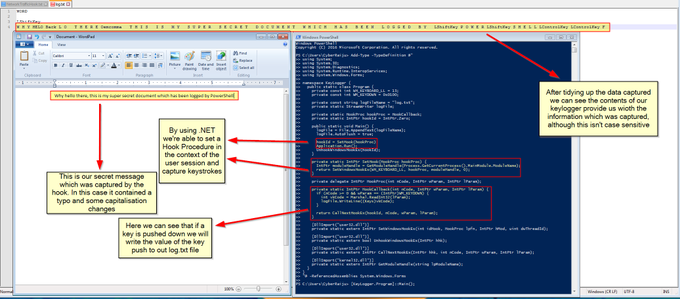
Here's some of the analysis one of my bright colleagues
@sneakymonk3y
has done in his own research.... lots of methods.
2
34
101
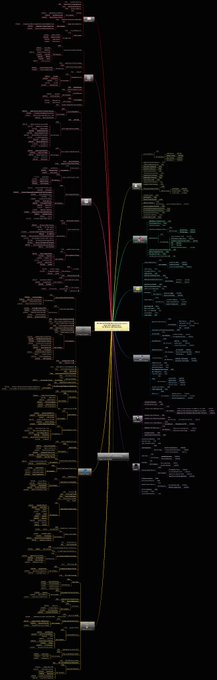
MITRE ATT&CK V7.0 (July 2020) Mind Map now available with minor changes including new sub-techniques added since the V7.0 beta.
The update can be found (So long as Github isn't down):
Changelog:
MITRE ATT&CK Mind Maps!
I've mapped the latest MITRE ATT&CK techniques, sub-techniques and IDs to a mind map and made it available.
Freemind (no colour) and XMind formats + PNG download.
Colours mapped to
@olafhartong
's "The ATT&CK Rainbow of Tactics"
4
134
379
0
35
88
I've just made my
@KringleCon
#Holidayhack
Challenge Write-up public.
Or for those who want the direct PDF:
This is 150 picture-filled pages detailing every challenge and how they can be solved.
Enjoy, hope you learn something.
5
26
85
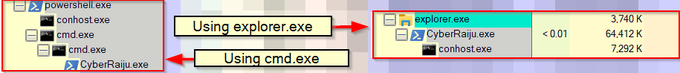
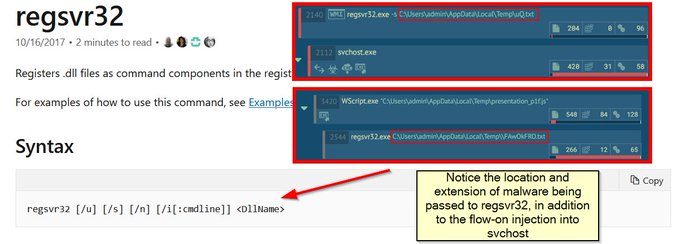
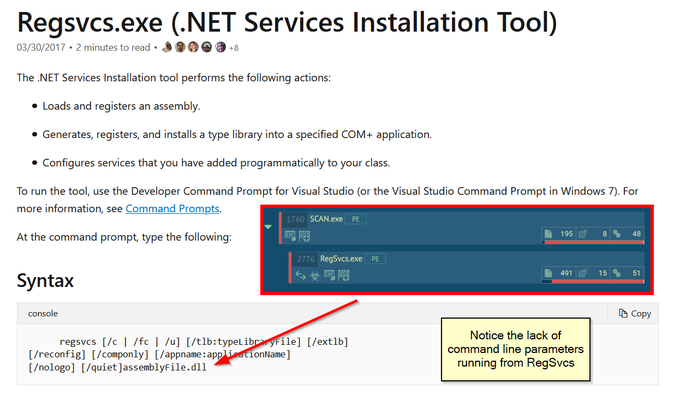
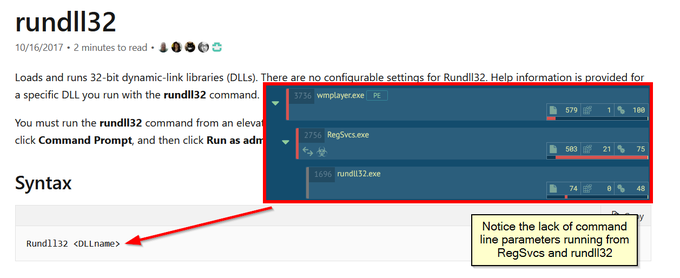
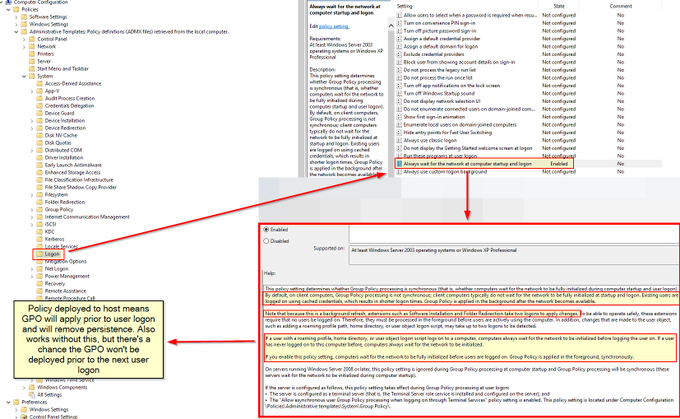
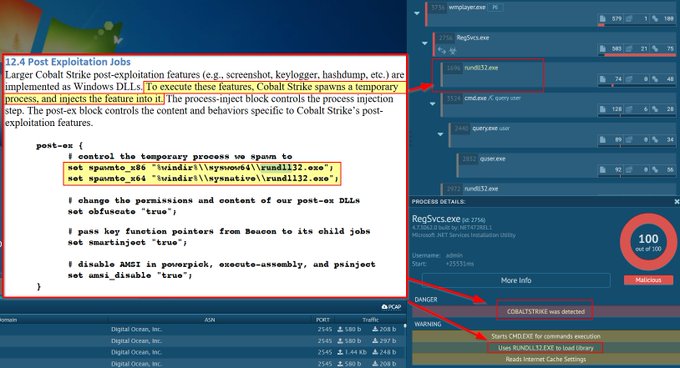
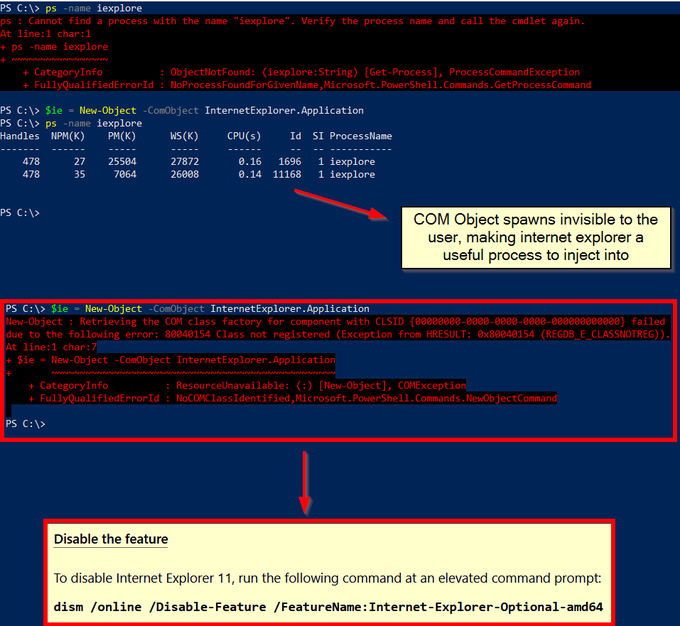
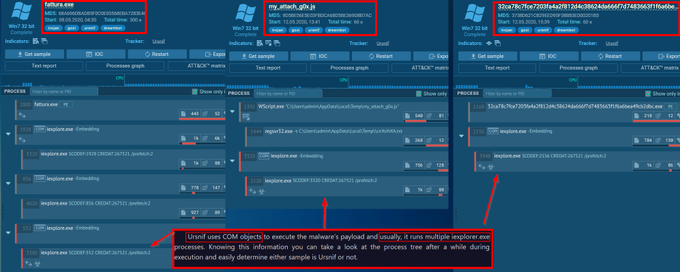
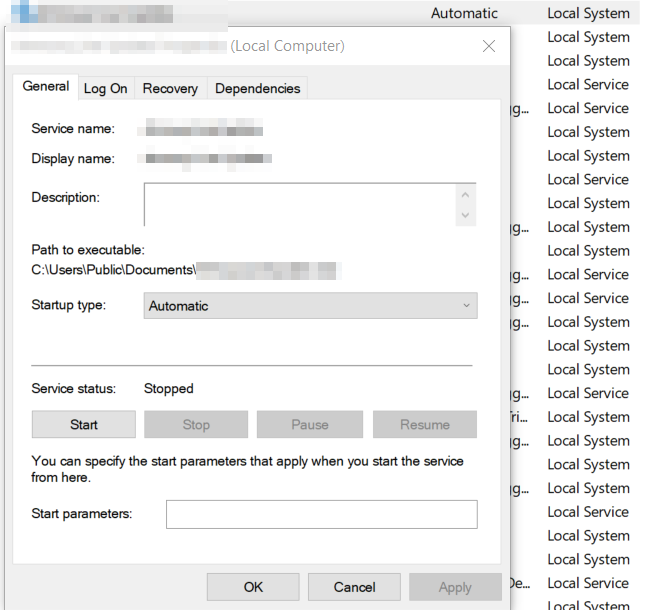
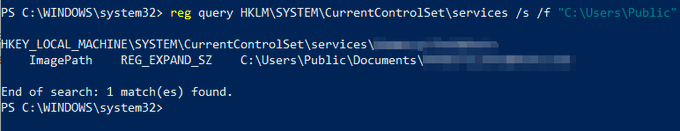
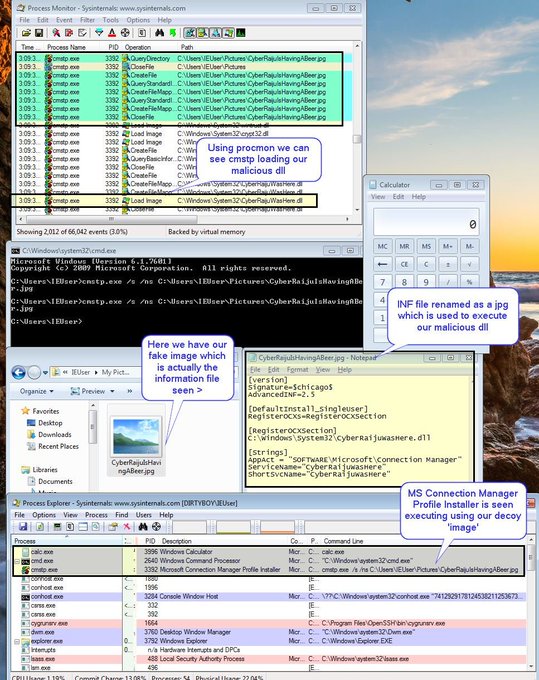
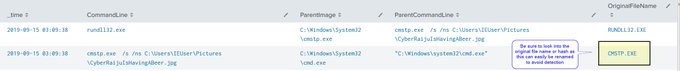
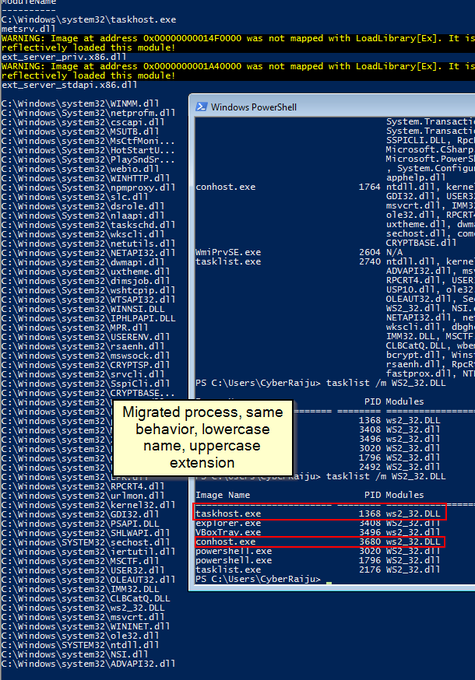
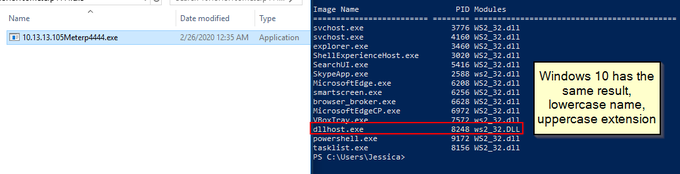
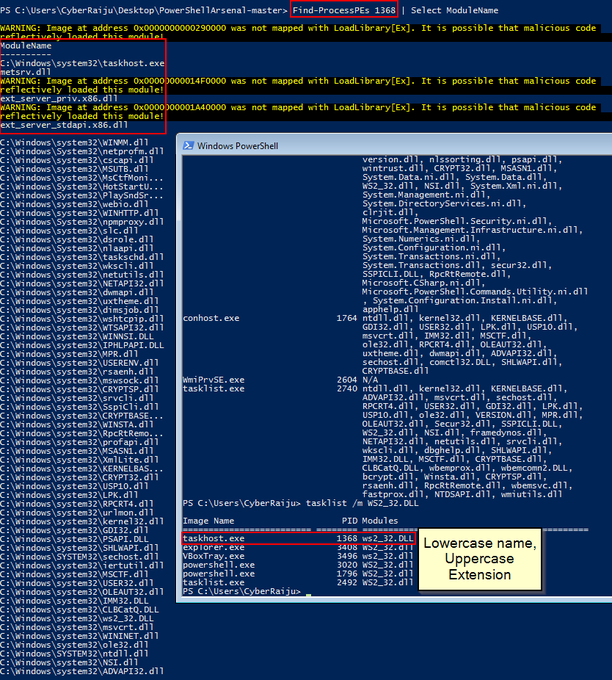
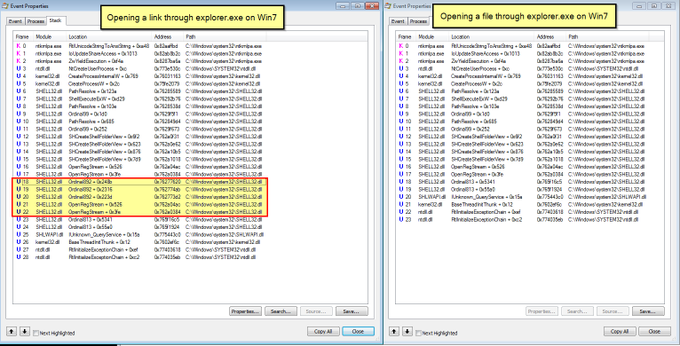
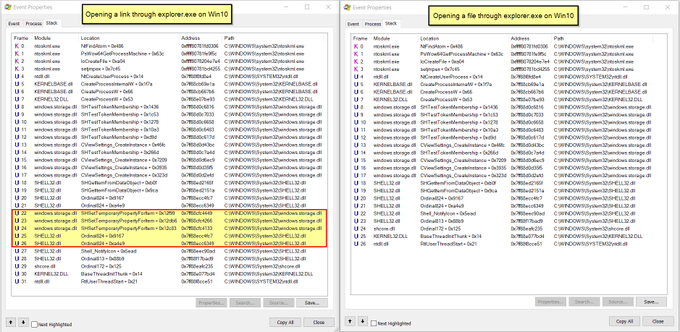
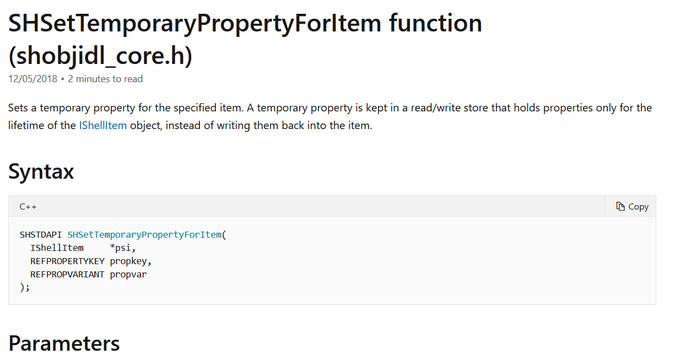
Let's look back at injecting into rundll32. Another telltale sign may be the version (32 or 64 bit) of rundll32 being injected into.
If your normal processes use 64-bit version (\System32), but then the 32-bit version runs (\SysWoW64) e.g. spawnto_x86, this may be worth flagging
1
25
77
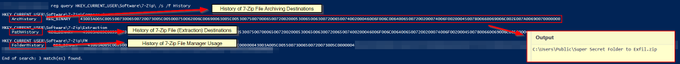
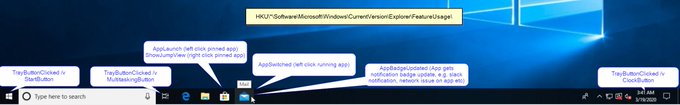
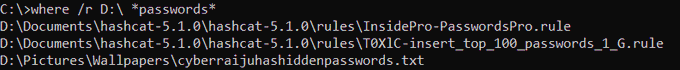
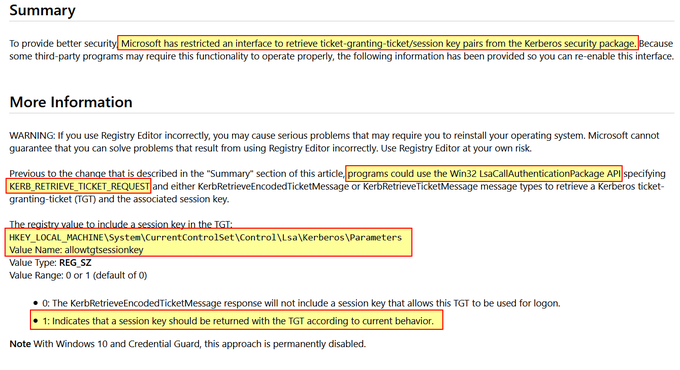
Now in blog format, a quick read of my research into the relatively new 'FeatureUsage' registry key and some potential DFIR use cases.
In addition to event logs, a number of other artifacts can provide valuable information, such as registry keys. In this blog, we discuss a new registry artifact called “FeatureUsage,” found in builds of Windows 10 version 1903 and later. via
@CyberRaiju
0
21
74
4
18
70
To help combat imposter syndrome, this year for
@KringleCon
I've created videos showing my failures and success in an edutaining way. I also recreated KringleCon as a JRPG playable game for my write-up. Enjoy!
Game🎮:
YouTube📺:
7
14
69
Final result: Approx 80% of the Lab environment and 90% of the exam environment compromised.👨💻
Today I received my confirmation.
Officially OSCP certified!🎉
Now I can return to Twitter after a bit of a hiatus for some more research and tech related tweets.
✌️
10
1
69
MalAPI:
Created by
@mrd0x
, this website aims to map Windows APIs to common techniques used by malware. Useful for reverse engineers as this helps to map functions which are used within a binary to possible malicious capability.
1
8
64
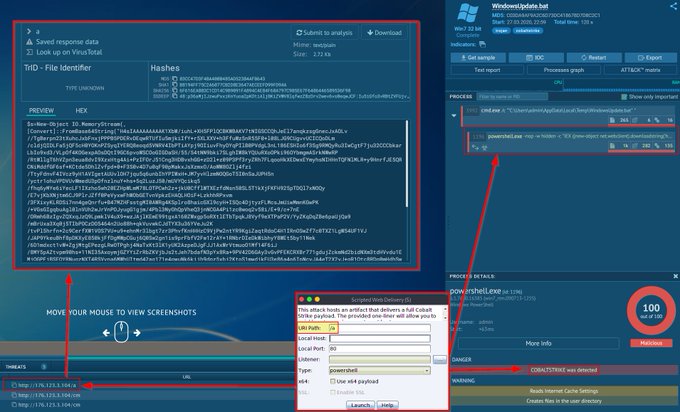
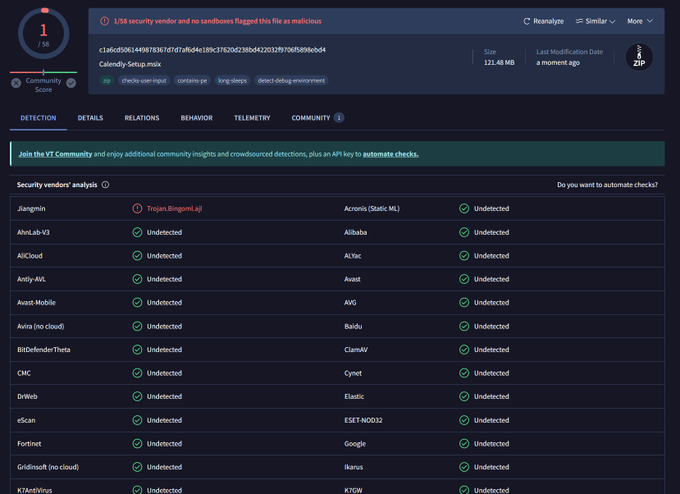
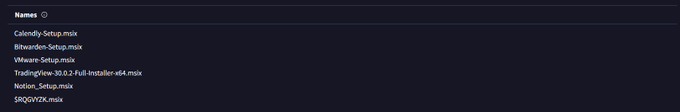
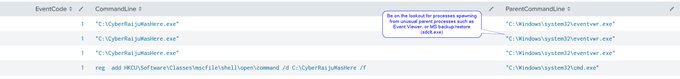
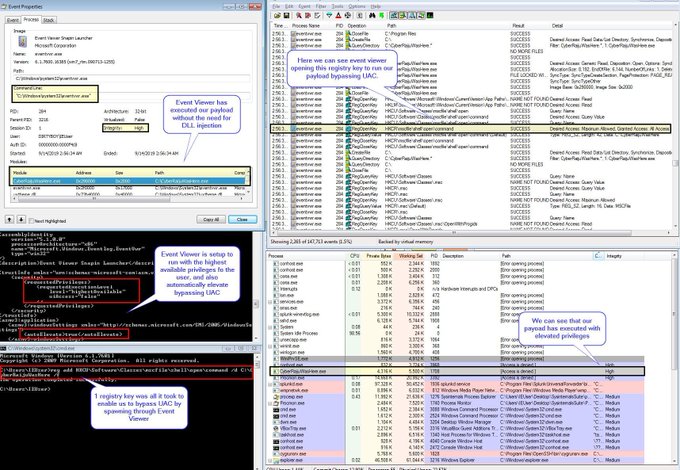
If you're not across MSIX installers you need to be! The
@Huntress
SOC hunting operations is seeing this malicious sample which has been active for 2 weeks and has near 0 on VT.
Masquerading as Calendly, Bitwarden, Vmware, TradingView, Notion, and Asana.
2
26
61
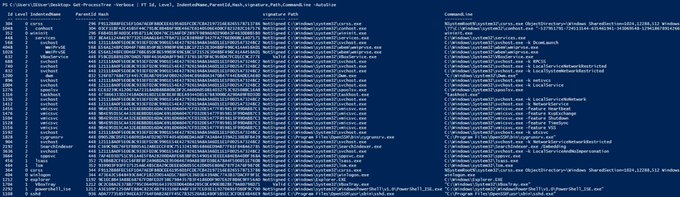
I quite like process trees (as opposed to lists) which show parent child relationships. As such I forked a PowerShell module from
@raboof
and made some minor adjustments to add support for file hashes, signing certs, command line execution. May be useful.
2
24
60
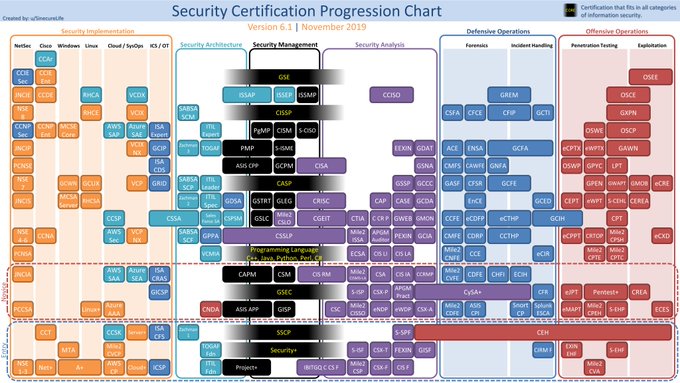
For those looking at different
#Security
#Certifications
, this is a nice way of presenting a lot of information by SinecureLife. Just don't forget the benefit of a home lab and hands on experience...
User:
()
Reddit:
0
30
58