ESET Research
@ESETresearch
Followers
31,655
Following
30
Media
841
Statuses
3,582
Security research and breaking news straight from ESET Research Labs.
Joined July 2009
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
#IanxSB19xTerry
• 323435 Tweets
Rio Grande do Sul
• 123680 Tweets
Madonna
• 122345 Tweets
Boeing
• 110851 Tweets
suho
• 96797 Tweets
#MOONLIGHTOutNow
• 71740 Tweets
Özgür Özel
• 67441 Tweets
RPWP CONCEPT PHOTO 2
• 61899 Tweets
Irak
• 60580 Tweets
Nathan
• 52183 Tweets
عدنان البرش
• 34678 Tweets
#無責任でええじゃないかLOVE
• 28117 Tweets
KPLC
• 15237 Tweets
Canna
• 11795 Tweets
Ivar Jenner
• 11185 Tweets
Ernando
• 10819 Tweets
ALGS
• 10743 Tweets
Last Seen Profiles
Breaking.
#ESETResearch
discovered a new data wiper malware used in Ukraine today. ESET telemetry shows that it was installed on hundreds of machines in the country. This follows the DDoS attacks against several Ukrainian websites earlier today 1/n
62
2K
3K
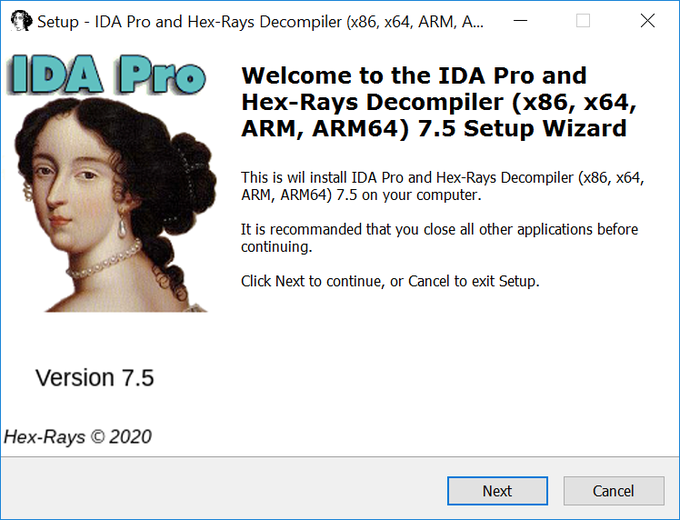
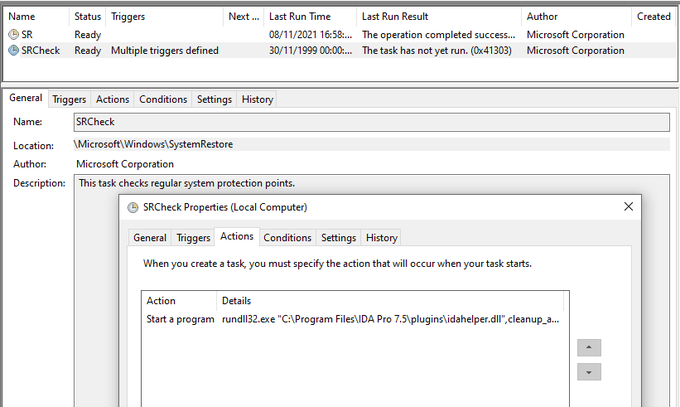
#ESETresearch
discovered a trojanized IDA Pro installer, distributed by the
#Lazarus
APT group. Attackers bundled the original IDA Pro 7.5 software developed by
@HexRaysSA
with two malicious components.
@cherepanov74
1/5
19
973
2K
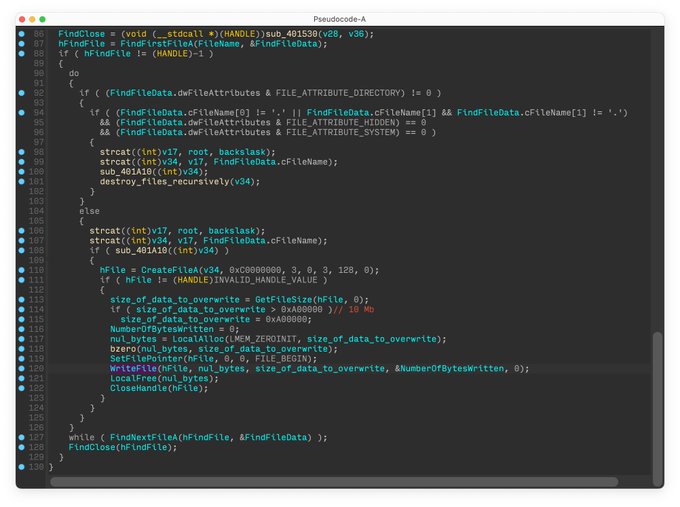
#BREAKING
#ESETresearch
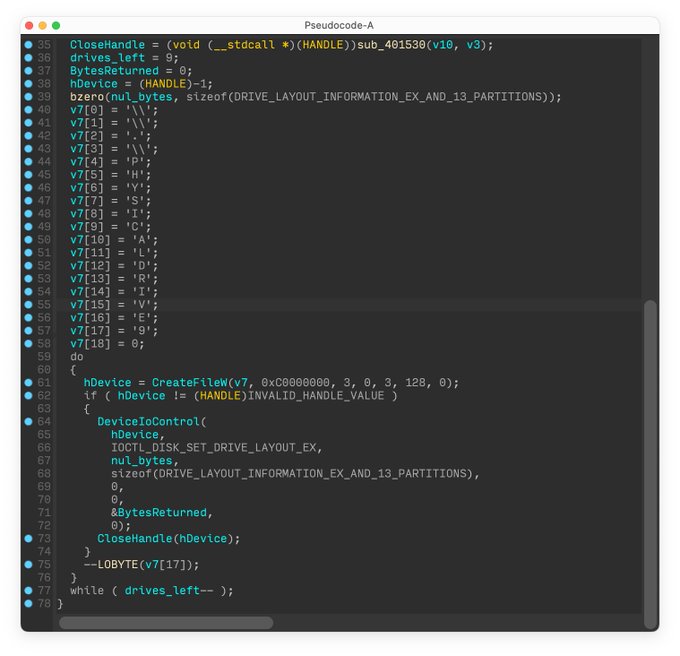
warns about the discovery of a 3rd destructive wiper deployed in Ukraine 🇺🇦. We first observed this new malware we call
#CaddyWiper
today around 9h38 UTC. 1/7
26
679
1K
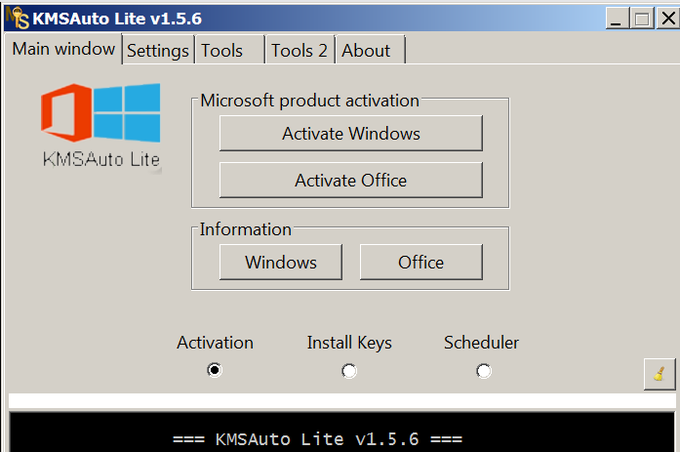
In November 2021,
#ESETresearch
saw how
#Lazarus
attackers installed one of their payloads into C:\ProgramData\KMSAutoS\KMSAuto.bin and, thus, disguised it as a well-known Windows activation tool. By this camouflage as a crack, it almost slipped under our radar.
@pkalnai
1/5
13
424
1K
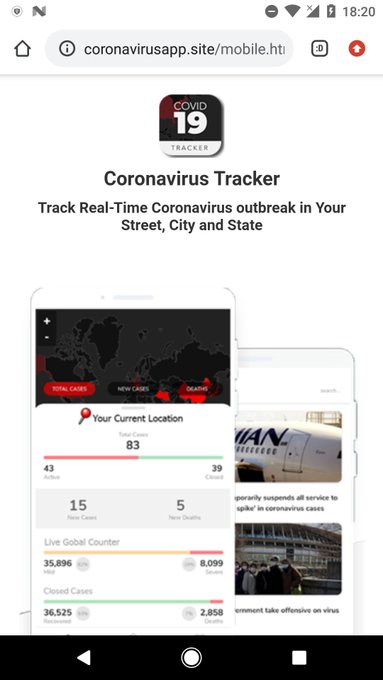
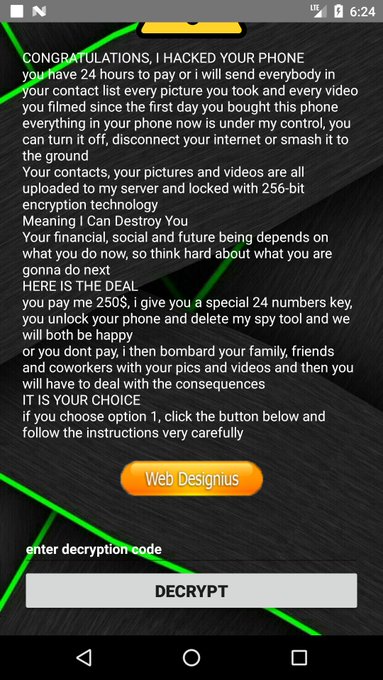
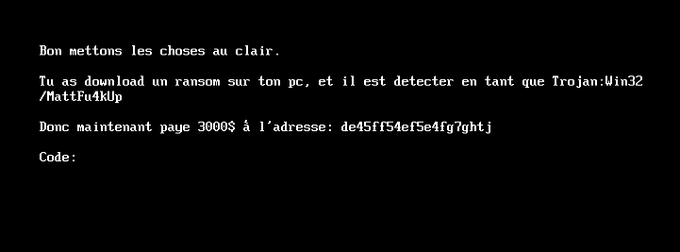
#ESETresearch
ALERT:
#COVID19
#Android
#Ransomware
: If you installed malicious Coronavirus Tracker app that locked your smartphone and requested ransom, use "4865083501" code to unlock it. Key is hardcoded.
@LukasStefanko
Details:
20
776
898
#BREAKING
#ESETresearch
helped analyze a
#Sandworm
campaign against an energy company in
#Ukraine
🇺🇦 using
#CaddyWiper
and a new version of the infamous
#Industroyer
malware.
#WarInUkraine
1/5
10
369
602
#BREAKING
On January 25th
#ESETResearch
discovered a new cyberattack in 🇺🇦 Ukraine. Attackers deployed a new wiper we named
#SwiftSlicer
using Active Directory Group Policy. The
#SwiftSlicer
wiper is written in Go programing language. We attribute this attack to
#Sandworm
. 1/3
4
250
473
#ESETResearch
analyze first in-the-wild UEFI bootkit bypassing UEFI Secure Boot even on fully updated Windows 11 systems. Its functionality indicates it is the
#BlackLotus
UEFI bootkit, for sale on hacking forums since at least Oct 6, 2022.
@smolar_m
1/11
10
252
448
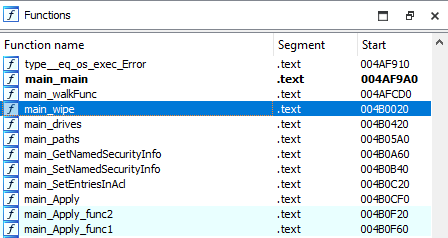
🇺🇦
#BREAKING
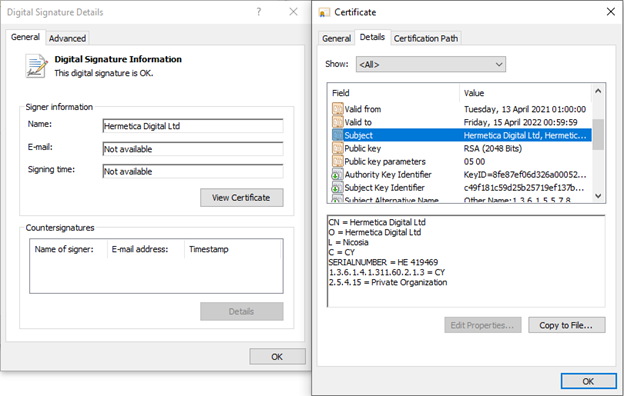
#ESETresearch
continues to investigate the
#HermeticWiper
incident. We uncovered a worm component
#HermeticWizard
, used to spread the wiper in local networks. We also discovered another wiper, called
#IsaacWiper
deployed in
#Ukraine
. 1/4
6
252
389
#ESETresearch
has published a comprehensive whitepaper comparing all known malware frameworks designed to breach air-gapped networks. Read more:
@adorais
@0xfmz
1/7
5
162
322
#ESETresearch
uncovers new Mac malware DazzleSpy, delivered using watering hole on a pro-democracy Hong Kong radio station website. Payload was launched as root without user interaction, using exploits for Safari and macOS.
@marc_etienne_
@cherepanov74
1/7
3
172
322
On November 21st
#ESETResearch
detected and alerted
@_CERT_UA
of a wave of ransomware we named
#RansomBoggs
, deployed in multiple organizations in Ukraine🇺🇦. While the malware written in .NET is new, its deployment is similar to previous attacks attributed to
#Sandworm
. 1/9
2
168
302
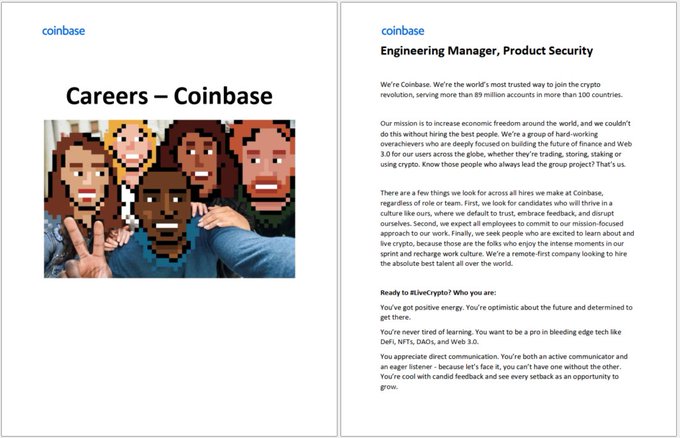
#ESETresearch
#BREAKING
A signed Mac executable disguised as a job description for Coinbase was uploaded to VirusTotal from Brazil 🇧🇷. This is an instance of Operation In(ter)ception by
#Lazarus
for Mac.
@pkalnai
@dbreitenbacher
1/7
10
140
279
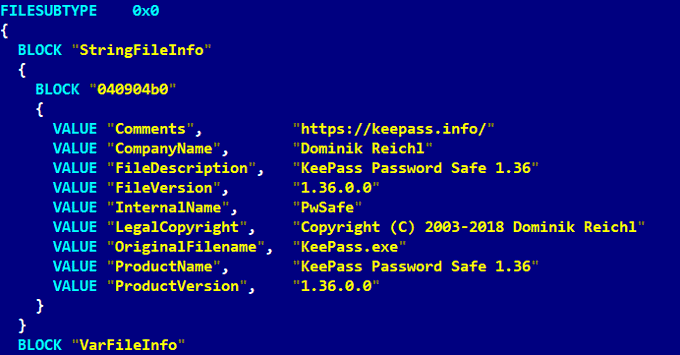
#ESETresearch
#Lazarus
Several trojanized KeePass 1.36 applications submitted to Virustotal recently: C696AEA7E90EF6A555F7037CBA5DE4F9D2169A2D, ECC340A650661FA4948E0306E652DDCE4018825D and 388DE03D60BC7DBFF6AD8ACFD69FF63A7172ECFE. All have a low detection rate.
@pkalnai
1/6
2
125
254
The recently reported breach of
#SFO
airport websites is in line with the TTPs of an APT group known as Dragonfly/Energetic Bear. The intent was to collect Windows credentials (username/NTLM hash) of visitors by exploiting an SMB feature and the file:// prefix
#ESETresearch
1/2
7
132
253
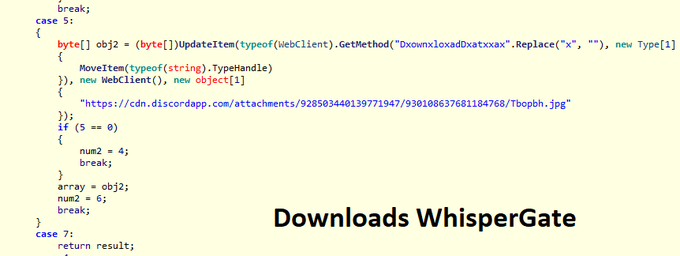
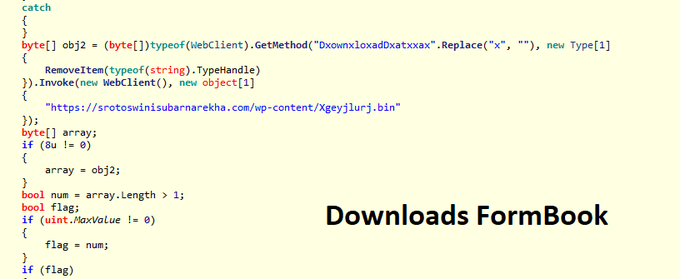
The
#WhisperGate
malware discovered by Microsoft contains MSIL stub commonly used by commodity e-crime malware. We observed samples using the same stub that drop different malware families such as Remcos RAT, FormBook and others.
#ESETresearch
1/5
3
133
251
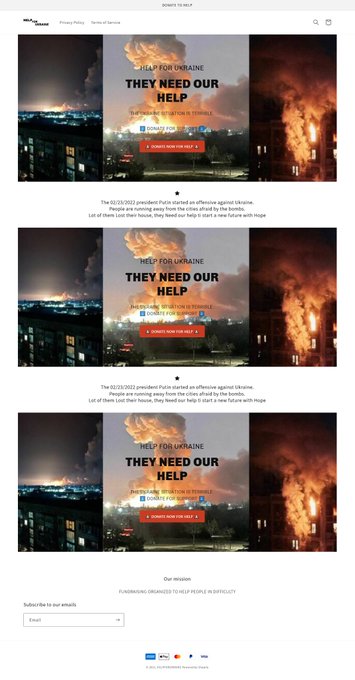
#ESETresearch
#BREAKING
Cybercriminals have no shame. With no humanitarian organization and only generic purpose mentioned, scammers try to lure out money from people trying to help
#Ukraine
during the
#war
. 🇺🇦
IoC:
help-for-ukraine[.]eu
tokenukraine[.]com
8
157
242
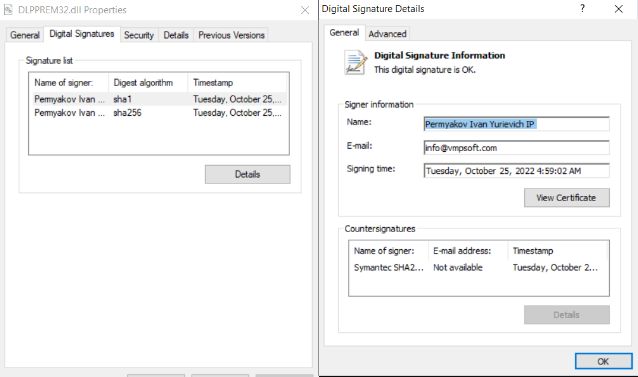
#ESETResearch
discovered that
#LuckyMouse
/
#APT27
used a code-signing certificate belonging to VMPsoft, the developer of the VMProtect packer. The signed file is a loader for the SysUpdate backdoor (aka Soldier). We notified VMPSoft of this compromise 1/4
2
115
253
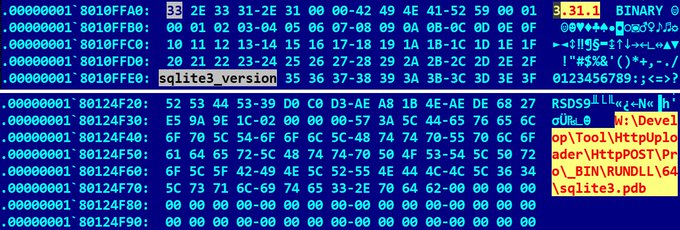
#ESETresearch
In November 2020, a Windows executable called mozila.cpl was submitted to VirusTotal from Germany 🇩🇪. At that time, it had zero detection rate and it is still very low now. The file is a trojanized sqlite-3.31.1 library and we attribute
it to
#Lazarus
.
@pkalnai
1/4
1
89
236
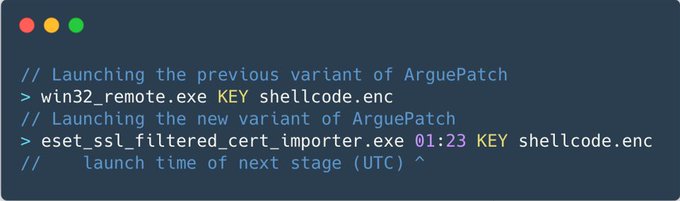
#BREAKING
#Sandworm
continues attacks in Ukraine 🇺🇦.
#ESETresearch
found an evolution of a malware loader used during the
#Industroyer2
attacks. This updated piece of the puzzle is malware
@_CERT_UA
calls
#ArguePatch
. ArguePatch was used to launch
#CaddyWiper
.
#WarInUkraine
1/6
2
157
236
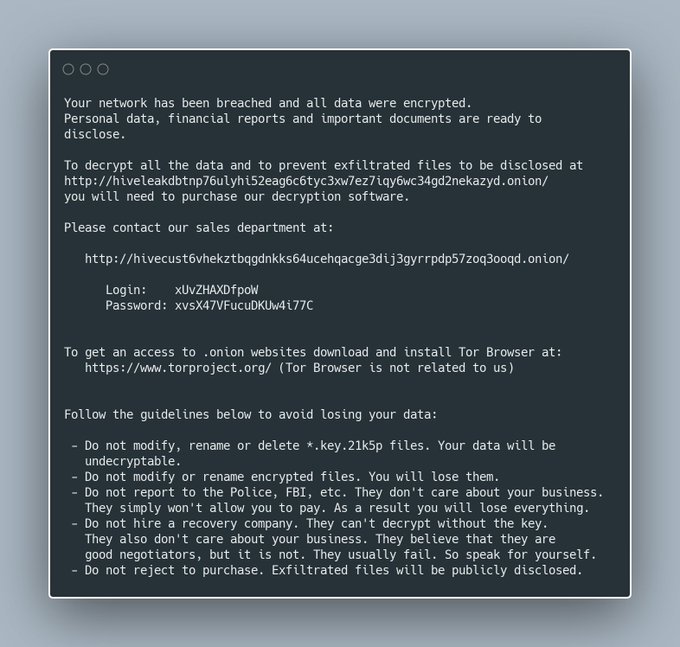
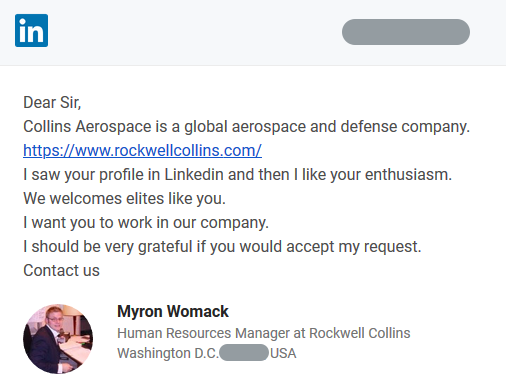
#ESETresearch
uncovered a
#Lazarus
attack against an aerospace company in 🇪🇸, deploying several tools, most notably a publicly undocumented and sophisticated RAT we named LightlessCan. The attack is part of Operation DreamJob.
@pkalnai
1/6
4
121
240
#ESETresearch
has identified Linux and FreeBSD variants of the
#Hive
#Ransomware
. Just like the Windows version, these variants are written in
#Golang
, but the strings, package names and function names have been obfuscated, likely with gobfuscate. 1/6
5
97
223
#ESETresearch
can confirm this great find by
@opa334dev
. The mentioned dylib binary is indeed malicious iOS tweak that allows the attacker to execute shell commands on a jailbroken and compromised iOS device
@cherepanov74
1/5
5
73
215
#ESETresearch
discovered three high-impact UEFI vulnerabilities affecting Lenovo consumer laptops. Their exploitation would allow attackers to deploy and successfully execute UEFI malware, such as LoJax or ESPecter, on the affected devices.
@smolar_m
1/7
2
135
214
#ESETresearch
has discovered a new cyber-espionage framework dubbed Ramsay, tailored for stealing Word documents from air-gapped networks.
@ulexec
1/7
1
136
214
#ESETresearch
A year ago, a signed Mach-O executable disguised as a job description was uploaded to VirusTotal from Singapore 🇸🇬. Malware is compiled for Intel and Apple Silicon and drops a PDF decoy. We think it was part of
#Lazarus
campaign for Mac.
@pkalnai
@marc_etienne_
1/8
3
82
201
#ESETresearch
documents its findings following recent pre-auth RCE vulnerability impacting Exchange servers globally. We identified at least 10 APT groups using exploits for CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065. Read more: 1/5
3
116
198
#ESETresearch
discovered BlackTech APT's TSCookie malware for FreeBSD platform
638cfbe609d7f3e88767133be5ea5f9a75f1d703275f38eb9ec2414e179483b9
C&C: 220[.]135[.]71[.]92:443
@cherepanov74
1/2
2
95
188
#Emotet
’s operators were busy updating their systeminfo module, with changes that enable malware operators to improve the targeting of specific victims and distinguish tracking bots from real users.
#ESETresearch
1/7
2
102
195
#ESETResearch
confirms Lazarus is linked to the recent
#3CX
supply-chain attacks. Based on code similarities and network infrastructure, we connect the 3CX incident with a Linux case of DreamJob, a long-term Lazarus operation using job offer as lures. 1/6
3
101
178
#ESETResearch
discovered and reported to the manufacturer 3 vulnerabilities in the
#UEFI
firmware of several Lenovo Notebooks. The vulnerabilities allow disabling UEFI Secure Boot or restoring factory default Secure Boot databases (incl. dbx): all simply from an OS.
@smolar_m
1/9
3
73
171
#ESETresearch
discovered and reported to the manufacturer three buffer overflow vulnerabilities in UEFI firmware of several
#Lenovo
Notebook devices, affecting more than 70 various models including several ThinkBook models.
@smolar_m
1/6
2
88
164
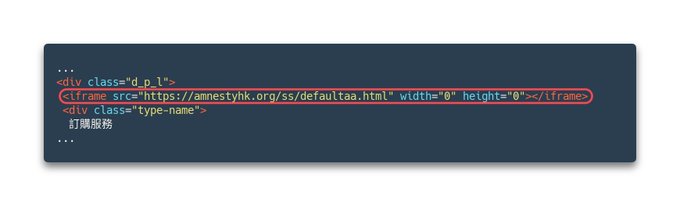
#ESETresearch
discovered a new supply-chain attack against HK 🇭🇰-based BigNox's NoxPlayer, an Android emulator for PC, Mac. We discovered that malicious NoxPlayer updates were being used to deliver malware to a selected pool of victims in Asia.
@ulexec
1/5
2
118
162
#ESETresearch
has discovered a unique and undescribed
#loader
for Windows binaries that, unlike other such loaders, runs as a server and executes received modules in memory. We have named this new malware
#Wslink
after one of its DLLs. 1/7
@HrckaVladislav
2
92
159
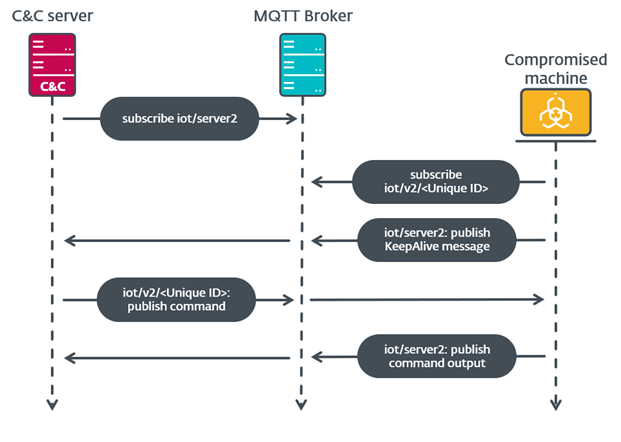
#ESETResearch
analyzed a new
#MustangPanda
backdoor. Its C&C communications is done over
#MQTT
using the open-source QMQTT library, so we named it MQsTTang. This library depends on parts of the Qt framework, statically linked in the PE. 1/5
2
83
163
#ESETresearch
found new weaponized Word document by
#Lazarus
– Operation In(ter)ception that surfaced on VirusTotal.
1/3
4
59
155
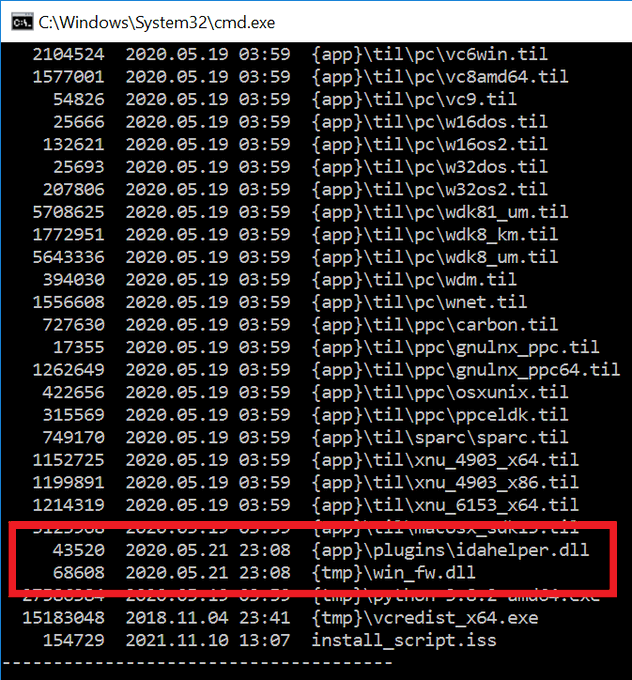
IoCs
📄:
win_fw.dll A8EF73CC67C794D5AA860538D66898868EE0BEC0
idahelper.dll DE0E23DB04A7A780A640C656293336F80040F387
🚨:
Win32/NukeSped.KZ
Win64/NukeSped.JS
🌐:
devguardmap[.]org
#ESETresearch
5/5
5
26
150
#ESETresearch
has analyzed the latest version of ComRAT, a backdoor operated by the
#Turla
#APT
group and used to steal documents from government networks. It is a descendant of the infamous Agent.BTZ, allegedly used to breach the US military in 2008.
1/4
4
93
155
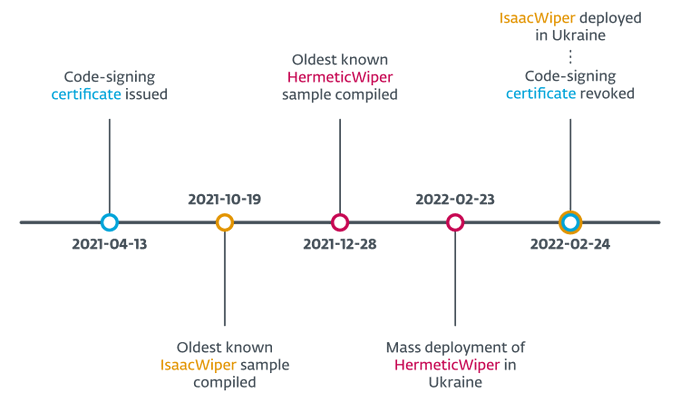
Based on the discussion on Twitter by fellow researchers and discussing this naming at
#ESETresearch
, we will continue to call this malware
#HermeticWiper
7/n
Ok, folks, we're clearly missing the *MOST* important part of all of this. Seeing as neither
@threatintel
nor
@ESETresearch
have named this monster, let's call this
#HermeticWiper
5
17
82
4
29
150
#ESETresearch
reveals new findings about POLONIUM, an APT group that has targeted more than a dozen organizations in Israel 🇮🇱 since at least September 2021, using at least seven different custom backdoors.
1/6
3
78
154
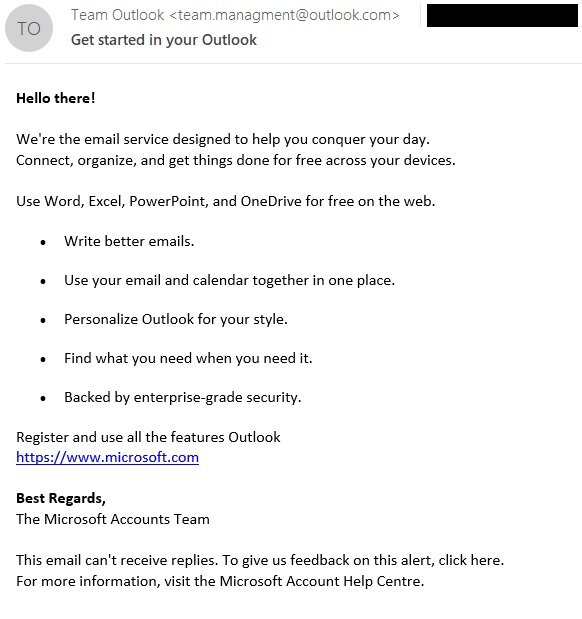
#ESETResearch
discovered a zero-day XSS vulnerability (
#CVE
-2023-5631) in Roundcube Webmail servers. It is actively used in the wild by
#WinterVivern
to target governments and a think tank in Europe. The exploit was contained in a legitimate-looking email about Outlook. 1/4
2
87
159
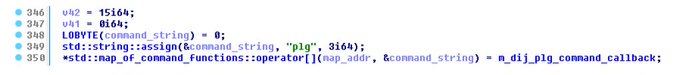
The authors of
#BumbleBee
released a new version of their bot, which includes a new command: “plg” (plug-in?). For now, it has the same functionality as command “dij” (download, inject). We suspect that this malware family is being modularized like
#TrickBot
.
#ESETresearch
1/5
3
58
149
#ESETresearch
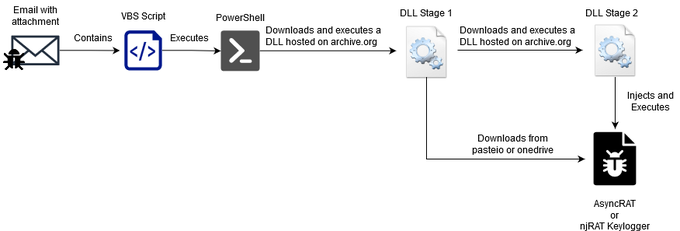
discovers a malicious campaign targeting governmental and education entities in Colombia using multiple stages to drop AsyncRAT or njRAT Keylogger on their victims. 1/4
1
64
141
#ESETresearch
discovered a new supply-chain attack against a certification authority in Southeast Asia. Installers of the GCA software, distributed on , were modified to deliver
#PhantomNet
(aka
#SMananger
)
@ulexec
@matthieu_faou
1/4
1
84
144
#ESETresearch
has discovered a new undocumented UEFI bootkit,
#ESPecter
, persisting as a patched Windows Boot Manager (bootmgfw.efi) on the Efi System Partition (ESP). 1/5
@smolar_m
@cherepanov74
3
93
138
#ESETresearch
confirms in-the-wild use of the PRIVATELOG/STASHLOG malware reported by
@Int2e_
and
@MalwareMechanic
from
@FireEye
earlier this week. Findings 👇
@0xfmz
1/11
2
66
141
#ESETesearch
discovered Dolphin, a sophisticated backdoor extending the arsenal of the
#ScarCruft
APT group. Dolphin has a wide range of spying capabilities and is deployed on selected targets only.
1/6
1
72
142
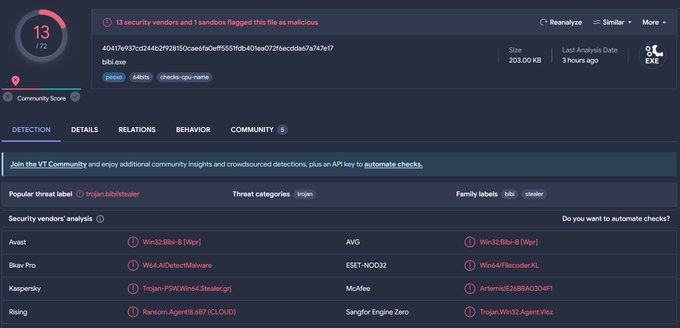
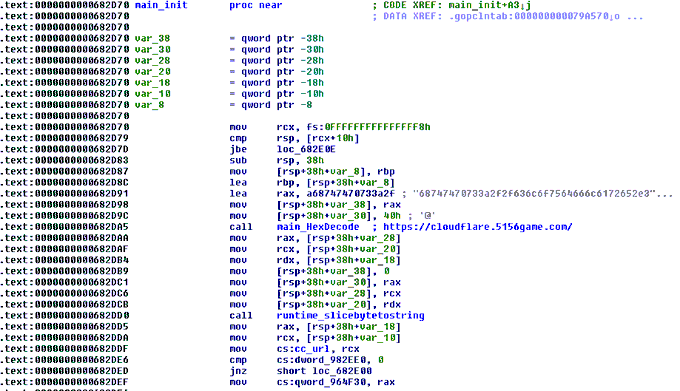
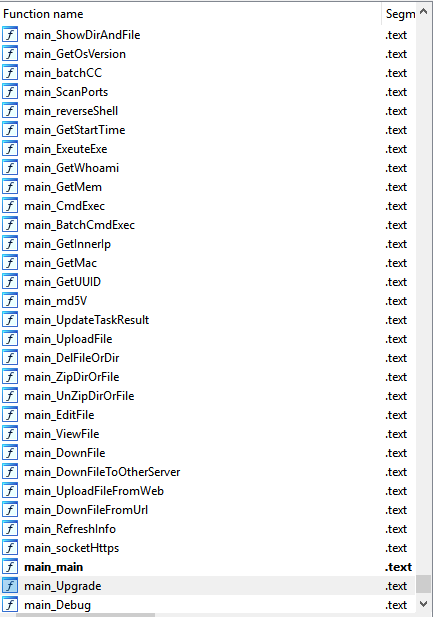
#ESETresearch
found a Windows version of the Bibi Wiper by BiBiGun – a Hamas-backed hacktivist group that first appeared during the Israel-Hamas conflict of 2023. The Linux version was first discussed by
@SecurityJoes
yesterday. 1/6
3
61
144
#ESETresearch
discovered a new backdoor used by
#Turla
to exfiltrate stolen documents to Dropbox. Named Crutch by its developers, we were able to attribute it to the Turla APT group thanks to several similarities with
#Gazer
/
#WhiteBear
.
@matthieu_faou
1/4
1
84
135
#ESETresearch
has discovered
#Lazarus
attacks against targets in 🇳🇱 and 🇧🇪, spreading via spearphishing emails and exploiting the CVE-2021-21551 vulnerability to disable the monitoring of all security solutions on compromised machines
@pkalnai
1
58
138
#ESETresearch
found a new currently live
#FreeBSD
#GoLang
backdoor; retrieves commands from a C&C, its capabilities include: upgrade itself, reverse shell, download/upload/view/edit files, execute shell commands/files, port scanning, send machine information.
@michalmalik
1/4
1
53
126
#ESETresearch
unearths modus operandi of the elusive
#InvisiMole
group, digging up their arsenal used to stay invisible. Our investigation also shows previously unknown ties between InvisiMole and
#Gamaredon
groups
@cherepanov74
@zuzana_hromcova
1/9
4
89
129
We have received a lot questions about the Silver Sparrow malware for macOS after a publication by
@redcanary
.
#ESETresearch
has investigated and found that, far from speculations about nation-state malware, it is likely related to adware and pay-per-install schemes. 1/10
2
64
128
#ESETresearch
discovered an SFile
#ransomware
variant for the FreeBSD platform, targeting a partially state-owned company in 🇨🇳
#China
. It encrypts files with the following file extensions
@cherepanov74
1/3
1
61
124
#ESETresearch
stumbled upon strange samples which use the packer we described in publications on the
#Winnti
Group. The payload in these samples is an implant attributed to Equation. It is known as PeddleCheap according to the project names seen in the Shadow Brokers leaks. 1/8
1
60
131
#ESETResearch
discovered an attack by APT group Tick against a data-loss prevention (DLP) company in East Asia and found a previously unreported tool used by the group.
@0xfmz
1/6
3
65
128
#ESETresearch
has discovered a new backdoor, PipeMon, used by the
#Winnti
Group to compromise several video-game companies and persisting as a Print Processor.
@smolar_m
@mathieutartare
1/7
1
78
130
#ESETresearch
has recently discovered a new undocumented modular backdoor, SideWalk, that was used by an APT group we named SparklingGoblin during one of its recent campaigns targeting a US-based computer retail company 🇺🇸.
@passil_t
@mathieutartare
1/6
2
67
128
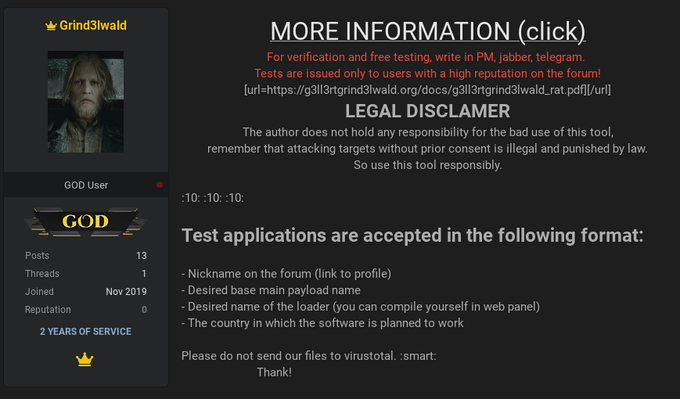
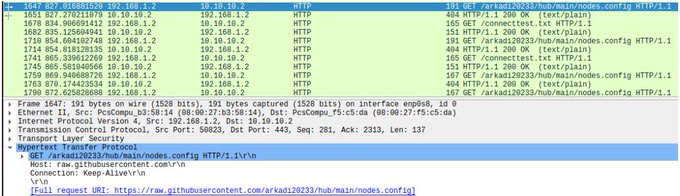
#ESETresearch
discovered a new campaign distributing the G3ll3rt Grind3lwald RAT using compromised
#GitHub
repositories. This malware is advertised in underground forums.
@0xE9FBFFFFFF
1/6
3
58
121
New
#ESETresearch
blogpost discusses vulnerabilities among kernel drivers, provides several case studies of malware utilizing such drivers, shows examples of discovered CVEs, and outlines mitigation techniques. 1/5
1
75
127
#ESETresearch
discovered a supply-chain attack performed by
#Lazarus
APT group against South Korean 🇰🇷 internet users.
@cherepanov74
@pkalnai
1/7
1
74
125
#BREAKING
Another day at
#ESETresearch
, another
#Emotet
campaign with a new technique. Instead of the usual Office macros, operators use PowerShell in LNK attachments - filename “form.lnk”. If the victim runs the file, Emotet binary (.DLL) is downloaded and executed. 1/4
4
52
126
The “
#WhatsApp
Pink” trojan can now auto-reply to received messages not only on WhatsApp, but also Signal, Skype, Viber and Telegram. The replies link to a malicious website further distributing the malware.
#ESETresearch
@LukasStefanko
1/3
4
71
121
#ESETresearch
uncovered previously unknown group
#Worok
, targeting high-profile users mostly in Asia. The group uses steganography to hide malicious payloads in PNG files and a custom PowerShell backdoor doing C&C via ICMP or HTTP protocols.
@passil_t
1/5
3
65
122
#ESETresearch
discovered a
#backdoor
we have named Sponsor, used in a
#BallisticBobcat
(aka Charming Kitten,
#TA453
,
#APT35
, or
#PHOSPHORUS
) campaign targeting various entities in Brazil 🇧🇷, Israel 🇮🇱, and the United Arab Emirates 🇦🇪. 1/5
3
45
124
#ESETresearch
has published a comprehensive guide to detecting,
#reversing
and mitigating native
#IIS
malware – a class of threats implemented as extensions for Microsoft web server software IIS.
@zuzana_hromcova
@cherepanov74
1/9
3
62
111
#ESETresearch
identified multiple malicious EFI bootloader samples. The malware displays a ransom message and prevents the computer from booting. It can compromise computers with disabled
#UEFI
Secure Boot feature
@cherepanov74
@smolar_m
1/4
2
66
112
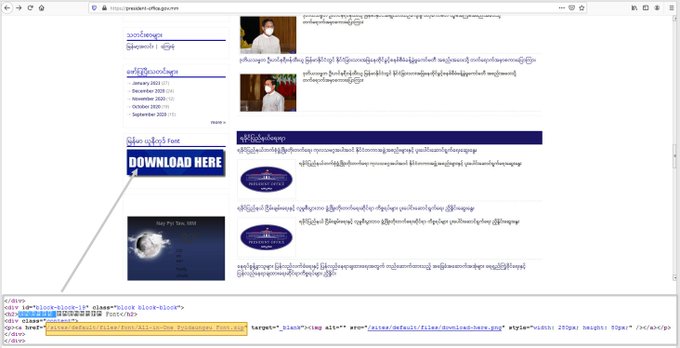
#ESETresearch
uncovered a supply chain attack on the Myanmar president office website ([.]mm). Attackers trojanized an archive containing fonts available for download on the homepage. 1/7
4
63
112
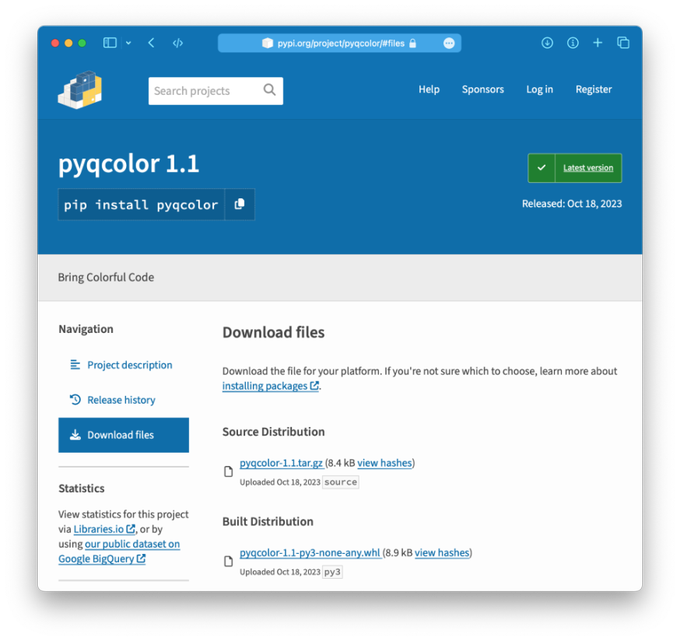
#ESETresearch
warns about malicious Python packages in the official
@PyPI
repository that target Windows and Linux. This cluster shares metadata or has similar payloads, and seems different from the one we reported in May: .
@marc_etienne_
1/6
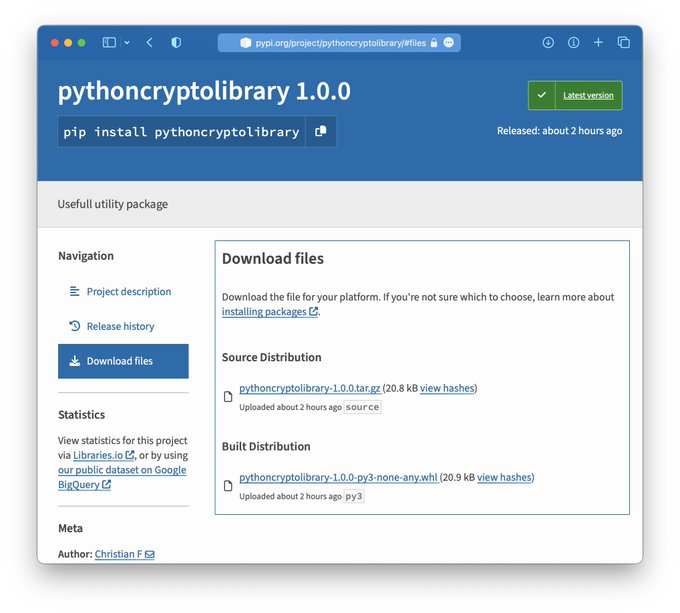
#ESETResearch
warns about an ongoing campaign distributing password and cryptocurrency stealing malware via
@PyPI
.
#Python
#Stealer
#Malware
@marc_etienne_
1/8
4
59
107
3
56
120
#BREAKING
#ESETresearch
discovered an ongoing
#MustangPanda
campaign using new
#Korplug
variant deployed with elaborate custom loaders. Every stage of the deployment process uses anti-analysis techniques and control-flow obfuscation 1/6
@barberousse_bin
2
57
118
During routine monitoring of suspicious activities on the systems of high-profile customers,
#ESETresearch
discovered a sophisticated and previously undocumented
#StealthFalcon
backdoor that we named
#Deadglyph
.
2
52
119
#ESETreasearch
has analyzed a new
#Lazarus
backdoor we’ve dubbed Vyveva, which was deployed against a South African company. The backdoor communicates with its C&C server via the
#Tor
network. More in the blogpost: 1/5
2
71
112
#ESETresearch
analyzed operation
#Interception
, a new espionage campaign targeting aerospace & defense companies in Europe and the Middle East. Initial contact was made via
#LinkedIn
, where attackers approached targets with fake job offers
@jiboutin
1/5
2
77
109
#ESETresearch
publishes new details on the
#TA410
umbrella. We believe it's composed of three groups: LookingFrog, FowingFrog and JollyFrog. They're engaged in targeted cyber-espionage using complex custom Windows implants. 1/5
1
57
110
#ESETResearch
released its latest APT Activity Report, covering the period from September until the end of December 2022 (T3 2022). Take a look ➡ 1/4
1
61
113
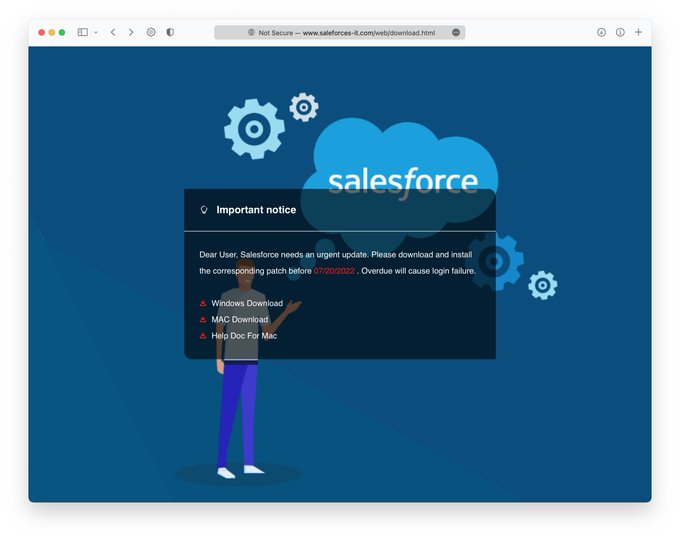
#ESETResearch
warns of a new campaign using a fake Salesforce update as a lure to deploy the Sliver malware for macOS and Windows 1/9
2
65
111
@ESETResearch
discovered that two vulnerable UEFI binaries revoked in August 2022 DBX update were revoked incorrectly (CVE-2022-34302/34301) – thus allowing anyone to use them for bypassing UEFI Secure Boot even on fully patched systems
@smolar_m
1/5
1
61
112
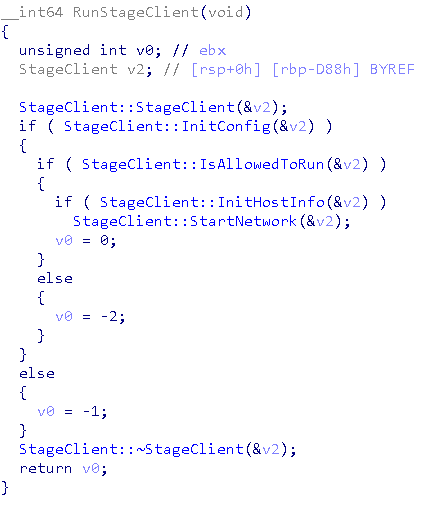
#ESETresearch
discovered inconspicuous Linux samples written in C++ which serve as configurable modular backdoors. They are referred to as StageClient throughout the code
@HrckaVladislav
1/8
3
51
109
#ESETresearch
published details about unique malware we’ve named Kobalos targeting multiple operating systems including Linux, FreeBSD and Solaris, and perhaps even AIX and Windows.
#KobalosMalware
@marc_etienne_
@ulexec
1/6
5
73
106
Introducing brand new ESET APT Activity Report: an overview of the latest activities of selected APT groups analyzed by
#ESETresearch
. T2 2022 saw no decline in APT activity, with aerospace and defense industries among the targets. Read more in the report:
1
59
109
#ESETResearch
, with the help of
@github
, has temporarily disrupted the operations of
#RedLineStealer
. During a collaborative investigation with
@flaresystems
into the infamous stealer, we discovered that the control panels use GitHub repositories as dead-drop resolvers. 1/4
3
42
106
#ESETresearch
dissects
#Evilnum
#APT
group operations as its malware targets
#fintech
companies. Its arsenal consists of homemade malware, and tools purchased from the
#GoldenChickens
MaaS provider, whose other customers include
#FIN6
and
#CobaltGroup
1/6
1
78
100
#ESETResearch
warns about an ongoing campaign distributing password and cryptocurrency stealing malware via
@PyPI
.
#Python
#Stealer
#Malware
@marc_etienne_
1/8
4
59
107
#ESETresearch
The developers of
#Bumblebee
, a
#downloader
that is a contender to become
#BazarLoader
’s successor, started implementing code
#obfuscation
. They are now encrypting key code strings, such as the list of C&C servers or the name of the campaign (aka “group_name”). 1/5
3
43
99
#ESETresearch
analyzed
#FontOnLake
, a previously unknown
#malware
family that utilizes custom and well-designed modules, targeting
#Linux
systems.
@HrckaVladislav
1/6
3
64
104
#ESETResearch
has discovered a new watering hole campaign targeting Armenia. We attribute it to the
#Turla
APT group. Two new payloads, we dubbed
#NetFlash
and
#PyFlash
, were used after they stopped using
#Skipper
in August 2019.
@matthieu_faou
1
66
105
#ESETresearch
uncovers
#CloudMensis
, spyware for macOS using cloud storage as a way to communicate back and forth its operators.
@marc_etienne_
1/7
2
58
104
In the last few days,
#ESETresearch
has detected multiple attack attempts by the
#Dark
.IoT botnet – yet another derivate of
#Mirai
– targeting the recently reported critical Azure vulnerability CVE-2021-38647
#OMIGOD
1/5
3
48
100
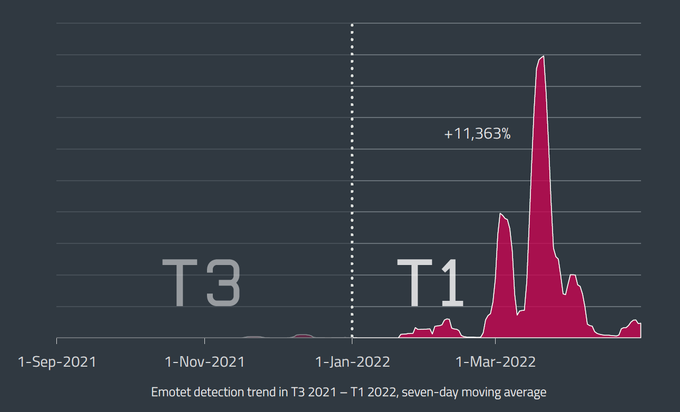
#Emotet
botnet shifted to a higher gear in T1 2022, with its activity growing more than 100-fold vs T3 2021.
#ESETresearch
detected its biggest campaign on March 16, targeting Japan 🇯🇵, Italy 🇮🇹, and Mexico 🇲🇽. 1/4
2
26
99
#ESETResearch
discovered a previously unknown
#Belarus
-aligned cyberespionage group that we named
#MoustachedBouncer
. Active since 2014, they are spying on EU, African and Asian diplomats stationed in 🇧🇾 🇧🇾 1/5
2
56
104
Starting with the telemetry data gathered by ESET’s
#UEFI
scanner,
#ESETresearch
machine learning specialists and malware researchers devised a method to spot rare UEFI/based
#malware
.
#cybersecurity
0
69
98
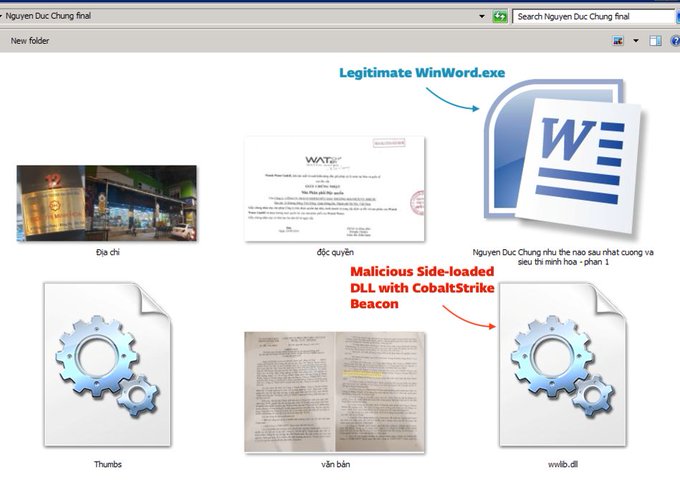
#OceanLotus
(
#APT32
) campaign spreading via FB. Post or DM contains link to a malicious archive hosted on Dropbox. First stage is executed upon opening the decoy “document” seemingly related to Vietnam. Beacons to opengroup.homeunix[.]org via HTTPS.
@marc_etienne_
#ESETresearch
1
53
96