CAPE Sandbox
@CapeSandbox
Followers
4K
Following
202
Media
252
Statuses
794
Payloads or it didn't happen. https://t.co/rAVsWT6dcl
Joined April 2017
New cmd.exe batch deobfuscation capability integrated in CAPE! FindFixAndRun hook😎 For example: https://t.co/CVPEHqPZil Thanks KingKDot https://t.co/LMMszQipLp🙏 and KillerInstinct for the integration!
1
1
11
Dropping a new malware config parser for #Amadey! Update your CAPEv2 parsers: > sudo -u cape bash -c 'cd /opt/CAPEv2 && poetry add CAPE-parsers@latest && systemctl restart cape cape-web cape-processor' Check it out here: https://t.co/tITnKwycLH
0
6
25
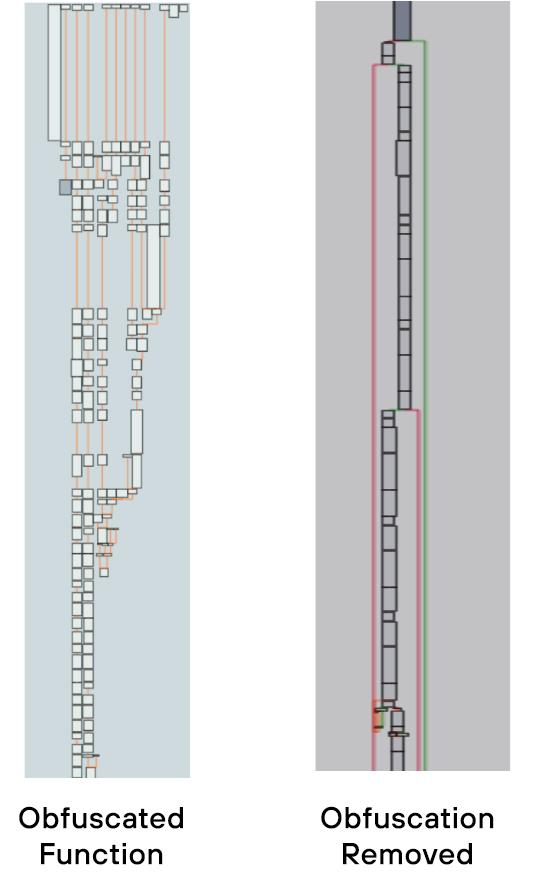
Palo Alto Networks researchers explore the obfuscation techniques employed by the malware authors in the SLOW#TEMPEST campaign and highlight methods and code that can be used to detect and defeat these techniques. https://t.co/Pz2a298Rbp
7
0
3
3
11
49
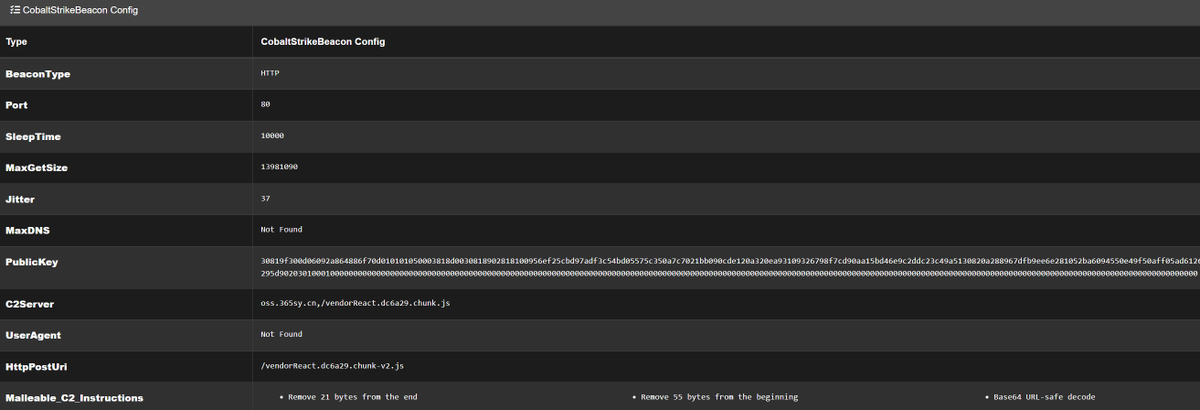
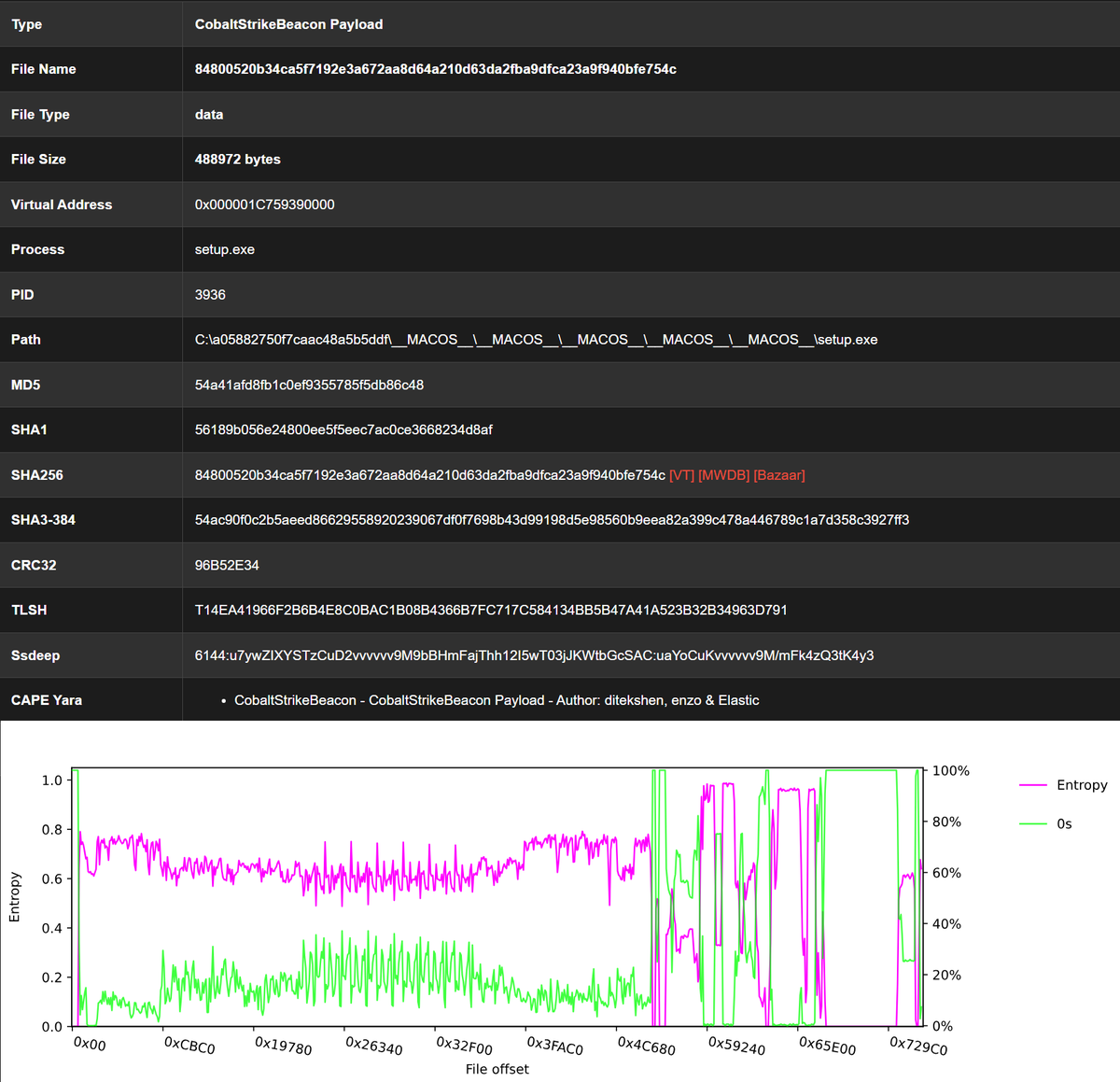
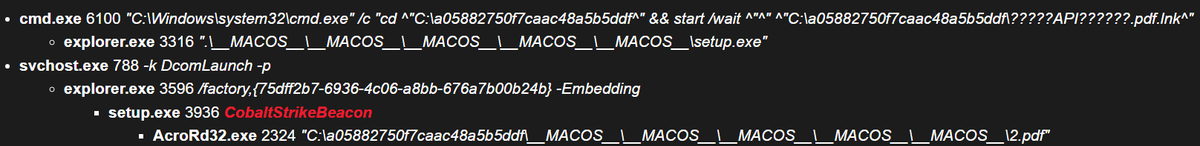
#Amatera payload extraction & direct syscall capture https://t.co/zzX2gPZuTi
New Octowave Loader sample > Amatera Stealer. 0 VT. Proofpoint rules detect the traffic. My Yara rule detects the installer. Adobe printer driver sideloads tbb.dll, tbb.dll loads app-2.3.dll which gets stego from blood.wav, uses zxing.presentation.dll. https://t.co/ITPIw1UKah
4
5
17
We're proud to announce our support for @CapeSandbox , a fully open-source malware sandbox developed and maintained by a dedicated group of volunteers. After almost a year of downtime, we are extremely happy that we were able to help CAPE get back online again! 🥳 👉
1
45
142
[1/n] In the hope that it might be useful to someone, I am happy to share with the community my basic (and cheap) implementation of a @CapeSandbox in physical machine config, integrating Elastic Stack and Elastic agents, Suricata, Aurora-Lite agent and Sysmon. #malwareanalysis
2
44
160
#Lumma config & payload extraction
It is really interesting to find anti-VM techniques being used by threat actors in the wild. This is a PowerShell script protecting a #Lumma Stealer build and being spread on YouTube videos. In this case, this was enough to make @anyrun_app to fail based on Screen Resolution
0
12
39
More #BruteRatel...
#BruteRatel #Latrodectus A New JS Nasty Obfuscation #TTPs & #IOCs - Multi-Line Comments🚨 [+] JS T1059.007 [+] Msiexec T1218.007 TA abuses multi-line (/* ,*/) comments to hide malcode and bypass detections - VT detections 20/62 Distro MSI IP: tp://95.164.17[.]212/BEST[.]msi
0
3
15
#BruteRatel config & payload extraction, syscall capture #BRC4
#Latrodectus - #BruteRatel - .pdf > url > .js > .msi > .dll 18.09.2024 👇 wscript.exe Document-21-29-08.js msiexec.exe /V MSI152A.tmp /DontWait rundll32.exe C:\Users\Admin\AppData\Roaming\x64_stealth.dll, clBuildProgram (1/3) 👇 IOC's https://t.co/n6EQNtxxiB
1
24
71
Apologies to users of https://t.co/u1Db15pUAo - unfortunately the server was water damaged in a data centre flood☹️ We appreciate your patience and understanding while we work on recovery🙏 Stay tuned for updates!
6
1
29
capa v7.0 dynamic output now fully integrated in CAPE Sandbox 🎉 For example: https://t.co/KfzJ9YnkFX
7
4
37
We've uploaded our lecture on Automating Malware Triage from our Introduction to Malware Binary Triage course. Huge shout out to @unpacme @anyrun_app @malpedia @abuse_ch @cybercentre_ca @CapeSandbox @hatching_io @R3MRUM for the amazing projects mentioned
0
13
35
Lightweight blog alert! This post goes over fast Bumblebee unpacking and configuration extraction. I've come across posts where authors do the unpacking manually. I use @CapeSandbox. Don't sleep on CAPEv2! https://t.co/iJEGXLBbbx
nikhilh-20.github.io
M&M: Malware and Musings
1
4
12
1/ You might have noticed that my area of interest is specifically stealers and RATs 😅 Wrote the configuration extractor for #Vidar stealer https://t.co/GA6bVlStHl
18
14
52