1nternaut 🕵️
@1nternaut
Followers
1K
Following
648
Media
120
Statuses
4K
Hero without a KAPE🦸. Also known as the Gordon Ramsay of Digital Forensics 🕵️. #APT #DFIR #4n6 #Blueteam
Cyber Crime Scene
Joined December 2009
My fallback channel in case shit hits the fan @1nternaut@infosec.exchange.
0
0
2
RT @ITguySoCal: NEW Microsoft Entra SSE feature in public preview: ."IT Admins can now set detailed SPN-level policies, such as requiring M….
0
41
0
RT @fabian_bader: Wanna play around with #KQL and #Graph. Microsoft just released sample datasets to play around and look at this gorgeous….
0
21
0
RT @saber__rt: Phrack #72 release reveals TTPs, backdoors and targets of a Chinese/North Korean state actor mimicking Kimsuky. A copy of hi….
0
58
0
RT @Jon__DiMaggio: 🚨 Ransomware Diaries: Volume 7 is here!!! The story of Yaroslav Vasinskyi, the REvil hacker behind the Kaseya attack. Fr….
analyst1.com
Jon DiMaggio will explore a new relationship with Rabotnik the person, not the REvil criminal. Why did one young man take the fall?
0
77
0
RT @CERT_Polska_en: Today we released a new stable version of DRAKVUF Sandbox v0.19.0 🎉– a project that leverages the DRAKVUF system for ag….
0
47
0
RT @davevenable: Some CISOs and Chief Risk Officers have been doing this for years, but this makes a lot of sense in larger orgs. https://t….
weforum.org
With governments and international institutions acknowledging the fragmenting global order, the creation of a Chief Geopolitical Officer role is an urgent priority for business.
0
3
0
RT @bayraktar_1love: The aftermath of a cyber attack on Russia's largest passenger airline Aeroflot. What's happening now:. Aeroflot’s oper….
0
1K
0
RT @PwnieAwards: We are very happy to announce the nominees for the 2025 Pwnie Awards! . As a reminder, we will be presenting the winners a….
docs.google.com
Pwnie for Best Crypto Bug X.509DoS Exploiting and Detecting Denial-of-Service Vulnerabilities in Cryptographic Libraries using Crafted X.509 Certificates Bing Shi, Wenchao Li, Yuchen Wang, Xiaolong...
0
48
0
RT @RavivTamir: Active exploitation of on-prem SharePoint vulnerabilities by Storm-2603 now leads to deployment of Warlock ransomware https….
microsoft.com
Microsoft has observed two named Chinese nation-state actors, Linen Typhoon and Violet Typhoon, exploiting vulnerabilities targeting internet-facing SharePoint servers. In addition, we have observed...
0
1
0
RT @ellishlomo: Heads up, blue team: Microsoft just hardwired Defender Threat Intelligence (MDTI) into Defender XDR and Sentinel. --What’….
0
20
0
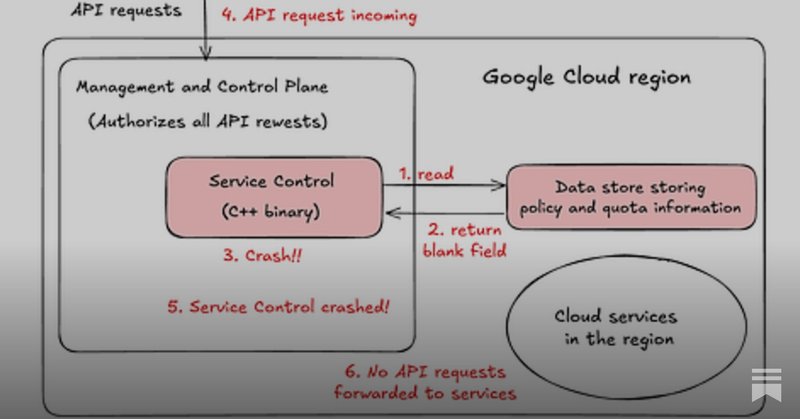
RT @GergelyOrosz: Mystery solved!!. Ubuntu 22.04 had an automatic update to systemd. This update restarted systemd that wiped IP rules and….
newsletter.pragmaticengineer.com
What are the lessons of large outages at Heroku, Google Cloud, and Neon? Plus, how responses to outages can be as informative as incidents themselves…
0
285
0
RT @MPECSInc: SHAREPOINT ZERO-DAY (HAFNIUM STYLE) RCE ATTACK MITIGATION: USE GROUP POLICY SOFTWARE RESTRICTION POLICIES TO BLOCK THE FILE(S….
0
44
0
RT @theluemmel: That is actually the real exploit. I went through all the decoding and stuff. It finally is the payload that creates spinst….
0
66
0
RT @TheDeadDistrict: Decoding Secrets Through Symbols: How Military Insignia Revealed Russia’s Hidden SIGINT Network. .
0
5
0
RT @PyroTek3: A while ago I published an article called "The Art of the Honeypot Account: Making the Unusual Look Normal". This covered som….
0
25
0
RT @DakotaInDC: The accompanying Wired piece by @KimZetter is here: .
wired.com
A new report traces the history of the early wave of Chinese hackers who became the backbone of the state's espionage apparatus.
0
1
0
RT @inversecos: Red teamers, no need to “pull” clipboard data when Windows already saves it all on disk for you in a neat little file 🗿. (i….
0
325
0
RT @nyxgeek: New research is wrapping up. Spoilers:. Microsoft Teams External Access is enabled in 973,328 out of 1,323,512 domains tested.….
0
108
0