LuemmelSec
@theluemmel
Followers
8K
Following
7K
Media
299
Statuses
4K
I speak BloodHound. Husband, Father, IT-Guy, Security-Noob Blog: https://t.co/PXB35KEqs6 GitHub: https://t.co/Unp9jZOpBn
Somewhere in your AD
Joined June 2019
I can finally release my work on Amazon Cognito Ratelimit Bypassing as the fix is now globally deployed. Huge shoutout to James Kettle who discovered this attack vector and made the info public. Let me know what you think in the comments.
4
22
102
RT @MsftSecIntel: We updated our blog with expanded analysis and threat intelligence from newly observed activity by Storm-2603 leading to….
microsoft.com
Microsoft has observed two named Chinese nation-state actors, Linen Typhoon and Violet Typhoon, exploiting vulnerabilities targeting internet-facing SharePoint servers. In addition, we have observed...
0
28
0
RT @HackingLZ: This might be useful for enumerating the SaaS products companies use, but it was more of an exercise in seeing how many DNS….
github.com
Contribute to HackingLZ/saas_enum development by creating an account on GitHub.
0
14
0
RT @stephenfewer: We now have a (draft) @metasploit exploit module in the pull queue for the recent Microsoft SharePoint Server unauthentic….
0
113
0
RT @leak_ix: As promised, our #SharePoint adventure with CVE-2025-53770 and CVE-2025-53771, including payloads and vulnerability checker!….
blog.leakix.net
Exploring our adventure while building detection for SharePoint exploitation and vulnerability.
0
59
0
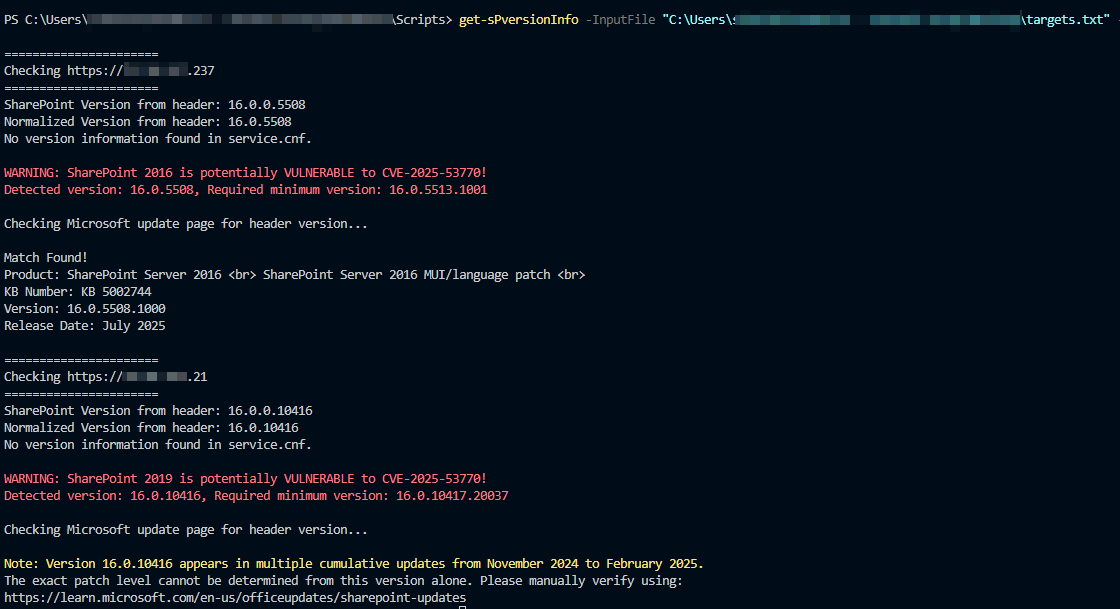
Update on the SharePoint saga:. First samples seen bypassing AMSI (. Fist samples seen completely operating fileless, still extracting your machine keys. Please do not rely on AMSI nor that files need to be dropped first before shit happens.
linkedin.com
🚨 Chinese hackers are actively exploiting new SharePoint flaws to bypass auth & run code remotely. Even Microsoft’s AMSI fix isn’t stopping them. The worst part? Many orgs aren’t patching. Details...
0
2
14
RT @Octoberfest73: My take on one of the new FileFix (DropFix?) MOTW bypasses. Awesome to collab with @mrd0x, exciting to see how TTPs can….
0
34
0
RT @leak_ix: Just a heads-up, attackers found a way to leak information, including keys entirely from memory. Checking for "the file" is no….
0
53
0
RT @_l0gg: My advice is temporary block ToolPane page. URL contain `ToolPane.aspx` and body contain `MSOTlPn_DWP` parameter. Remember to de….
0
7
0
RT @BlinkzSec: Personally, I am convinced that you should use something like active defense in a company - maybe there is already another n….
0
7
0
RT @irsdl: 🚨.1- CVE-2025-53770 is a variant of CVE-2025-49704 - a critical auth bypass in SharePoint's ToolPane.aspx endpoint. It lets atta….
0
47
0
RT @msftsecresponse: Microsoft has released security updates that fully protect customers using SharePoint Subscription Edition and SharePo….
0
46
0
RT @CISACyber: Malicious actors are exploiting RCE vulnerability CVE-2025-53770 to compromise on-prem SharePoint servers. See our Alert for….
0
65
0
RT @irsdl: Well it was possible to bypass the auth patch easily as even a slash after .aspx would jump the check but .
0
16
0