Maxime Thiebaut
@0xThiebaut
Followers
721
Following
747
Media
27
Statuses
93
308 Permanent Redirect Location: https://t.co/xKLuDM5iDl 🇧🇪🕊🇺🇦
Joined January 2019
Received the NVISO #Innovation Coin joining a growing hall of fame 🎉 If you’re looking to work with #SANS legends, we’re #hiring in every field! Come have a chat & drink: https://t.co/hm2HC0jb3t 🍻
1
5
17
On September 29th, 2025, Broadcom disclosed a local privilege escalation vulnerability, CVE-2025-41244, impacting VMware’s guest service discovery features. NVISO has identified zero-day exploitation in the wild beginning mid-October 2024. All details -
blog.nviso.eu
NVISO has identified zero-day exploitation of CVE-2025-41244, a local privilege escalation vulnerability impacting VMware's guest service discovery features.
0
14
29
New blog post! Title: Hunting Chromium Notifications | By @0xThiebaut (Maxime Thiebaut) Link: https://t.co/kgG8pPqFaU
#ThreatHunting #Phishing #Chromium #Chrome #Edge #Forensics
0
5
20
New blog post! Title: MEGAsync Forensics and Intrusion Attribution | By @0xThiebaut (Maxime Thiebaut) Link: https://t.co/Gwat4vHy2J
#Forensics #MEGAsync #LockBit #Python #Statecache
blog.nviso.eu
MEGAsync forensics can be leveraged to identify exfiltrated files, additional victims and, subsequently, perform attribution.
0
5
9
Respectfully, your proposal does break encryption. I am happy to spend as much time as you need reviewing in as much detail as you are comfortable with exactly how it breaks encryption, and why this is so dangerous.
Let me clarify one thing about our draft law to detect online child sexual abuse #CSAM. Our proposal is not breaking encryption. Our proposal preserves privacy and any measures taken need to be in line with EU privacy laws.
74
949
4K
ScriptBlock Smuggling is a new technique, developed by @_Hubbl3 & @Cx01N_ that allows that allows for the spoofing of PowerShell security logs & bypasses AMSI without the need for reflection or memory patching. Learn all about in our new blog post! https://t.co/OPI7A9sK4f
6
187
416
Tune in now!
Join us today at 4:00 pm ET (8:00 pm UTC) at the #RansomwareSummit to discuss the "Evolution of Ransomware Tactics in 2023 - Insights from The DFIR Report" Shout-out to our analysts (@_pete_0 & @0xThiebaut) who have been working on this presentation for months!
1
13
50
We're closing out today's #RansomwareSummit w/ @_pete_0 & @0xThiebaut exploring the evolving landscape of #ransomware tactics and strategies, providing actionable insights for bolstering #cybersecurity defenses. Register Free to Join / Access Recordings: https://t.co/mtPudWN90Q
0
1
5
At #RansomwareSummit, @_pete_0 & @0xThiebaut will explore the evolving landscape of #Ransomware tactics and strategies, providing actionable insights for bolstering #Cybersecurity defenses. Register for Free Live Online: https://t.co/mtPudWN90Q
0
2
11
New blog post! Title: Covert TLS n-day backdoors: SparkCockpit & SparkTar | by NVISO Incident Response Link: https://t.co/Gmf1dHMs1j
#Forensics #ReverseEngineering #CVE #Ivanti #PulseSecure
blog.nviso.eu
This report documents two covert TLS-based backdoors identified by NVISO: SparkCockpit & SparkTar.
1
15
24
From ScreenConnect to Hive Ransomware in 61 hours ➡️Initial Access: ScreenConnect ➡️Defense Evasion: BITS Jobs, Embedded Payloads ➡️Lateral Movement: Impacket, RDP, SMB ➡️C2: ScreenConnect, Atera, Splashtop, Cobalt Strike, Metasploit ➡️Exfil: Rclone https://t.co/0rOKnoHnbR 1/X
thedfirreport.com
In 2022, The DFIR Report observed an increase in the adversarial usage of Remote Management and Monitoring (RMM) tools. When compared to post-exploitation channels that heavily rely on terminals, s…
2
168
420
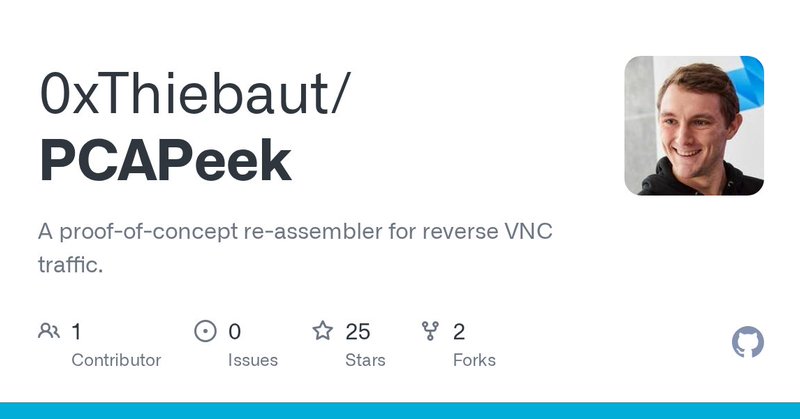
@JAMESWT_MHT Awesome article, and here is the tool that came with it put together by @0xThiebaut: https://t.co/ZuCa1shc1P Works like a charm; I used it more than once 🙂
github.com
A proof-of-concept re-assembler for reverse VNC traffic. - 0xThiebaut/PCAPeek
0
10
13
IcedID & Qakbot's VNC Backdoors: Dark Cat, Anubis & Keyhole
blog.nviso.eu
In this post we introduce Dark Cat, Anubis and Keyhole, three IcedID & Qakbot VNC backdoor variants NVISO observed. We'll follow by exposing TTPs and information leaked through the attackers'...
1
33
88
Got the account locked because of DMCA. 🤦♂️ Forget to screenshot the step after the first screenshot, but anyway, it did not include which tweet got reported and by who, should check emails it said. So going to check now...
5
16
63
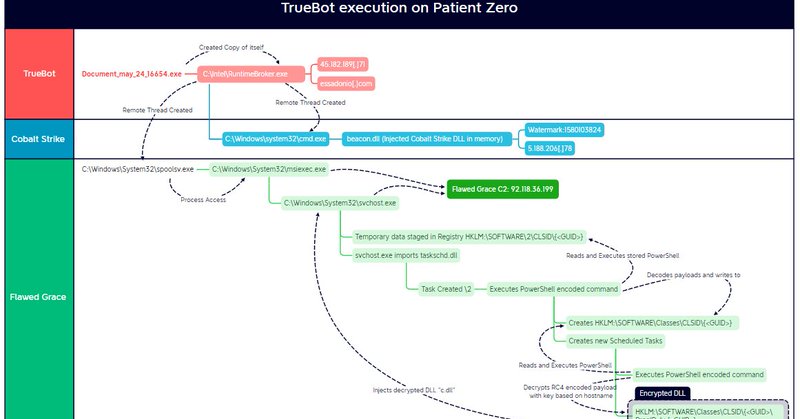
A Truly Graceful Wipe Out ➡️Initial Access: Email > TDS > Truebot download ➡️Credentials: LSASS & Registry Dump ➡️Persistence: Scheduled Task ➡️C2: Truebot, FlawedGrace, Cobalt Strike ➡️Exfiltration: FlawedGrace ➡️Impact: MBR Killer https://t.co/qcAYmPmSPB 1/X
thedfirreport.com
In this intrusion, dated May 2023, we observed Truebot being used to deploy Cobalt Strike and FlawedGrace (aka GraceWire & BARBWIRE) resulting in the exfiltration of data and the deployment of …
1
161
353
A new report will be out June 12th by @Kostastsale, @svch0st & @0xThiebaut! This report will have a few things we haven't covered before, you won't want to miss it! Want to receive an email when we publish the report? Subscribe below https://t.co/oPX1ir9O13
thedfirreport.com
If you would like to receive an email when we publish a new report, please type your email address below and press subscribe. If you do not receive the confirmation email within a few minutes, plea…
2
26
110
1
1
3
🔎 IcedID’s VNC Backdoors: Dark Cat, Anubis & Keyhole A summary of #VNC #backdoor capabilities @0xThiebaut reconstructed from network traffic. 👀 Screenshots, videos and clipboard data at https://t.co/GXiZ3nICTH
#Malware #PCAP #Reversing
blog.nviso.eu
In this post we introduce Dark Cat, Anubis and Keyhole, three IcedID & Qakbot VNC backdoor variants NVISO observed. We'll follow by exposing TTPs and information leaked through the attackers'...
2
56
97
A few weeks ago Microsoft released #CVE_2022_41120, a “Microsoft Windows #Sysmon Elevation of Privilege Vulnerability” reported by @filip_dragovic . With the #vulnerability and original #PoC released, I can now share the first time I #diff'ed a patch.
thiebaut.dev
My first BinDiff: Checking the Sysmon v14.11 patch to turn a ClipboardChange event into arbitrary writing.
Here is PoC for CVE-2022-41120 https://t.co/oXkBYi4bWk. I combined arb file delete and limited arb file write to get code execution as NT Authority\System.
2
1
11