Spencer McIntyre
@zeroSteiner
Followers
3K
Following
734
Media
22
Statuses
639
Views are my own.
Cleveland, Ohio
Joined March 2011
New NTLM relay dropped for MSSQL. Should see some SCCM modules to use it next. @unsigned_sh0rt gave me all kinds of ideas.
0
17
85
Metasploit also has a merged exploit with check for react2shell. ⌨️ module: multi/http/react2shell_cve_2025_55182 📦 Dockerfile to test available in: Data\exploits\react2shell_unauth_rce_cve_2025_55102 https://t.co/B9cwDsj9ph
github.com
Vulnerability Details A critical unauthenticated Remote Code Execution (RCE) vulnerability exists in React Server Components (RSC) Flight protocol. The vulnerability allows attackers to achieve pro...
3
20
73
New Metasploit module for CVE-2025-54236 (SessionReaper) - Unauthenticated RCE in Magento https://t.co/mR8mSe1BSw
2
42
169
I've been hacking on a new Windows Named Pipe tool called PipeTap which helps analyse named pipe communications. Born out of necessity while doing some vulnerability research on a target, its been super useful in reversing it's fairly complex protocol. :)
18
150
1K
Come join @rapid7! I’m hiring for a Senior Security Researcher to join our team. You'll get to work on n-day analysis, zero-day research, exploit development, and more - focusing on enterprise software and appliances. Fully remote in the UK, details here:
4
16
61
Today @rapid7 is disclosing 8 new printer vulnerabilities affecting 742 models across 4 vendors. After 13 months of coordinated disclosure with Brother Industries, Ltd, we're detailing all issues including a critical auth bypass. Full details here:
rapid7.com
Multiple Brother Devices: Multiple Vulnerabilities (FIXED) - Rapid7 Blog
2
28
78
Our @metasploit auxiliary module for the new Brother auth bypass is available. The module will leak a serial number via HTTP/HTTPS/IPP (CVE-2024-51977), SNMP, or PJL, generate the devices default admin password (CVE-2024-51978) and then validate the creds: https://t.co/3uJG56aMx9
1
34
100
Today @rapid7 disclosed two vulns affecting NetScaler Console and NetScaler SDX, found by Senior Security Researcher Calum Hutton! 🎉 Our blog details the authenticated arbitrary file read vuln (CVE-2025-4365), and the authenticated arbitrary file write vuln (Which the vendor has
During root cause analysis for the #NetScaler Console vulnerability, CVE-2024-6235, Rapid7 discovered & disclosed to the vendor 2 additional high severity vulnerabilities. Find exploitation details, remediation advice & more in a new blog: https://t.co/RhKXUbgt82
1
11
46
Submitted a PR to enhance ReflectiveDLLInjection in @Metasploit: ✅ ARM64 reflective loading (using resolved APIs, not syscalls!) ✅ Refactored x86/64/ARM32 loader ✅ Major injector CLI & feature upgrades ✅ API to pass params to DllMain Details:
github.com
Description: This pull request introduces an enhancements to the ReflectiveDLLInjection library and its associated tooling, most notably adding support for the ARM64 architecture. It also includes ...
0
2
7
This week's wrap-up features support for the SOCKS5H protocol, some additional SOCKS lore, and modules for WordPress Depicter Plugin and Gladinet CentreStack/Triofox.
rapid7.com
Metasploit Wrap-Up: 05/30/2025 | Rapid7 Blog
3
31
113
🚀 I just released a new Metasploit module for Invision Community ≤ 5.0.6 (CVE-2025-47916)! 🔗 PR: https://t.co/VdTETvQXlS
0
33
123
Thanks to your help I donated £10,000 to mental health charities in the UK. I’m hoping to keep the ball rolling a little bit and fund raise using the pull of an exclusive signed print- you can support the fundraiser and get a print here, thank you - https://t.co/RLRuSaAYNY
4
111
628
🚨 CVE-2025-3102 Turned SureTriggers into SurePwned - unauth admin + RCE (≤1.0.78). PoCs have been out for a month, so I wrote the Metasploit module: https://t.co/huOZT4Ov7m
3
22
90
We now have a @metasploit exploit in the pull queue for that Oracle Access Manager vuln, CVE-2021-35587. You can check it out here: https://t.co/awXwpTq2wr
1
48
160
We recently noticed that impackets https://t.co/JtJF5f8aL1 example does not actually give you access control info about files, it is simply hard coded: 🤯
3
9
102
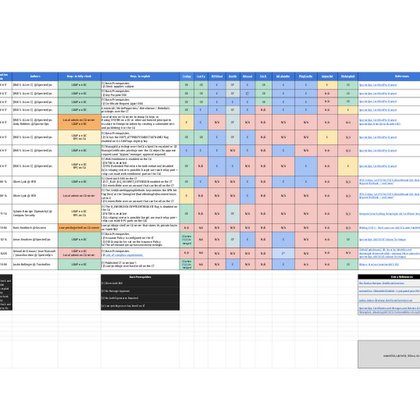
ADCS Attack Techniques Cheatsheet for all of you lazy folks who prefer colored tables over reading a bunch of articles just to find some specific information: https://t.co/HyvnCrBKnP
docs.google.com
6
177
499
...and we now have a @metasploit exploit module in the pull queue for the FortiManager vuln (CVE-2024-47575): https://t.co/dg1wMJLCuE
12
75
272
2008: Microsoft released a critical out-of-band patch via MS08-067 to close the vulnerability exploited by the Conficker worm.
6
74
311
An exciting week ahead... @the_emmons and I will be taking part at #Pwn2Own Ireland! Great to see so many hackers in Cork 🚀 ☘️
The draw is complete and now the schedule is out! You can check out the full schedule showing all four days of #Pwn2Own Ireland madness at https://t.co/UoIzGMrLP7
#P2OIreland
3
3
25
This week's wrap-up adds support for identifying and exploiting ESC15 👉👈 https://t.co/75VPJi3tok
rapid7.com
Metasploit Weekly Wrap-Up: 10/18/2024 | Rapid7 Blog
1
23
63