Satya
@tines_io
Followers
68
Following
633
Media
13
Statuses
711
Security Researcher | Bug Hunter | Microsoft HOF
Ramachandrapuram, India
Joined July 2020
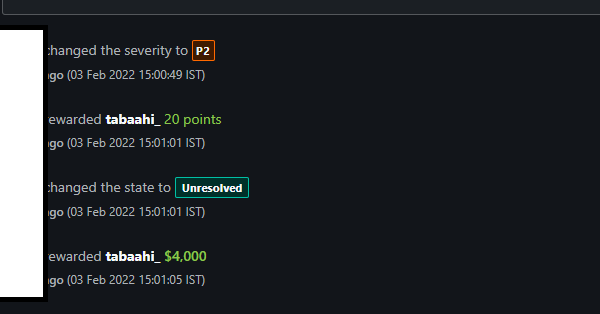
RT @tbbhunter: Bypassing 2FA in a Public Bug Bounty Program: A $6000 Journey.
mokhansec.medium.com
As a bug bounty hunter, uncovering vulnerabilities in public programs is both thrilling and rewarding. In this post, I’ll walk you through…
0
27
0
RT @hugopicanzo: Without any doubt, this must be the best resource out there about HTML/Javascript behaviors and discrepancies and how to e….
aszx87410.github.io
As a software engineer, you must be familiar with information security. In your work projects, you may have gone through security audits, including static code scanning, vulnerability scanning, or...
0
18
0
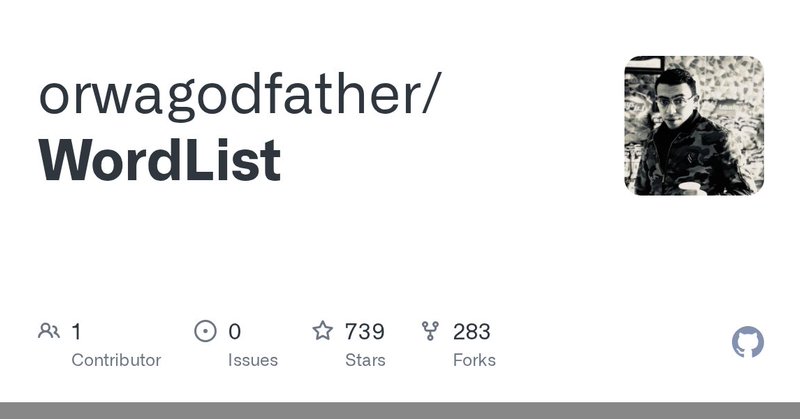
RT @h4x0r_fr34k: Fuzzing lists - Part 2.Wordlists for few specific Funtions you can use for Specific Purpuses. 1. WEB-INF..
github.com
Contribute to orwagodfather/WordList development by creating an account on GitHub.
0
173
0
RT @ynsmroztas: If you encounter the default IIS Windows window, do not forget to add /haproxy and /netdata to your wordlist and scan them,….
0
174
0
RT @thebinarybot: Here's a list of bug bounty tools that @GodfatherOrwa uses and shared in @NahamSec 's live stream. 🧵👇. #bugbounty #bugbo….
0
150
0
RT @drunkrhin0: Want to start bug bounties but don't know where to begin? 🕵️♀️💻. You're in luck! I get asked this question daily. So, I've….
0
187
0
RT @GodfatherOrwa: Burp Ex.403 Bypasser.5GC API Parser.Active Scan++.Backslash Powered Scanner.CO2.IP Rotate.J2EEScan.JS Link Finder.JS Min….
0
316
0
RT @0day_exploit_: Top Microsoft IIS . Thread 🧵:👇 Here is how to find IIS bugs . 1) Collect a huge number of targets, subdomains, and por….
0
139
0
RT @GodfatherOrwa: Slides of my talk in @bsidesahmedabad . I hope you like it and found it a little bit useful. .
docs.google.com
0
115
0
RT @GodfatherOrwa: Let’s made something new .Let’s keep this tweet for question’s. You can ask me here in a comment and will answers in a….
0
150
0
RT @ihteshamit: I created a complete FREE ChatGPT mastery guide. This guide will teach you how to unlock the full potential of ChatGPT and….
0
195
0
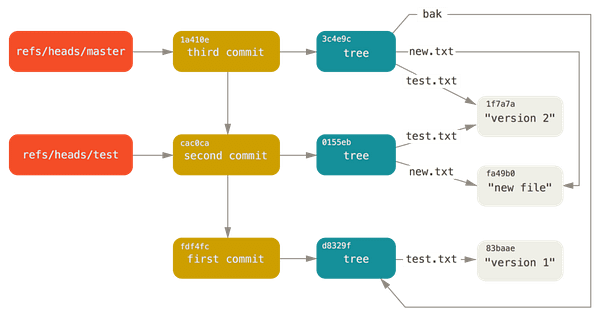
I just published How .git folder can be exploited to access sensitive data . #bugbounty #bugbountytip #cybersecuritytips #infosecurity #bug #hackers #hackerspace #cybersecuritynews #aws #informationsecurity #informationtechnology #cybersecurity #software.
link.medium.com
This is Satya, (Security Researcher/Bug Bounty Hunter). In this writeup, I’m going to show you how I was able to exploit .git to access…
0
0
0
RT @CyberWarship: "Microsoft SharePoint Server Elevation of Privilege Vulnerability Exploit (CVE-2023-29357)". #infosec #pentest #redteam….
0
43
0
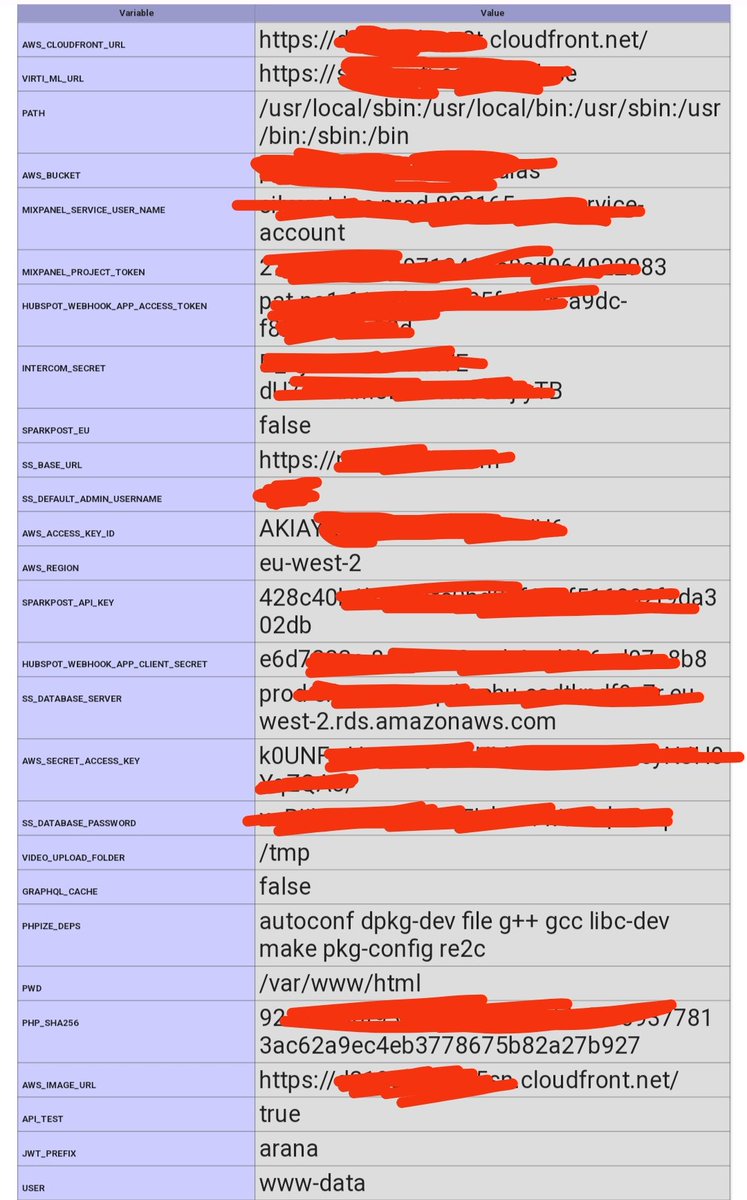
Bug Type : Sensitive Information Disclosure via phpinfo file. Tip : Never ignore the phpinfo files, You may get a lot of Juicy Information. #bugbounty #bugbountytips #bughunting #cybersecurity #cyberattack #cyberawareness #informationsecurity #hacker #hackerone #bugcrowd
0
1
4