L0Psec
@L0Psec
Followers
2K
Following
10K
Media
219
Statuses
2K
Father | macOS Security Researcher | RE | arm64 | InfoSec
NC
Joined October 2017
New RE Video:. In this video, I reverse engineer a malicious SwiftUI dropper. Swift is fun to RE so I thought it would be a good idea :) .Shout out to @txhaflaire for their recent blog post that covers this malware.
1
21
89
Appreciate the share as always @moonlock_lab! I feel it has been a while since we've seen such a readable Infostealer dropper. Unencrypted string commands passed to system() 4x and curl download output piped to osascript.
1/7: Our fellow researcher @g0njxa shared juicy info with us: a real #ClickFix-style find! A fake "Installation Instructions" pop-up pushes users to run a malicious bash command via Terminal. We couldn’t resist checking it, and what we uncovered? A multi-stage #macOS #stealer 👇
0
6
20
Appreciate y’all. Thanks for having me as a speaker and being a cool place to hang out at! Got to meet a lot of incredible people there :).
That wraps up #MalwareVillage.@DEFCON 33! 🥳. Special thanks to all the organizers, sponsors, volunteers, speakers, workshoppers, collaborators, attendees, and everyone involved, for making this event absolutely legendary! 🤩. Thank you all! 🙏
1
3
23
Got to talk about Swift RE yesterday at @MalwareVillage #defcon33 which was awesome! Decided to record an RE video while at DEFCON for fun, check it out :).
0
7
37
Time for my @MalwareVillage Swift talk tomorrow changed to 3:50pm. Come check it out if you want to see some live macOS malware reversing :) #defcon33
3
5
26
Definitely helps make the decompilation look much prettier :).
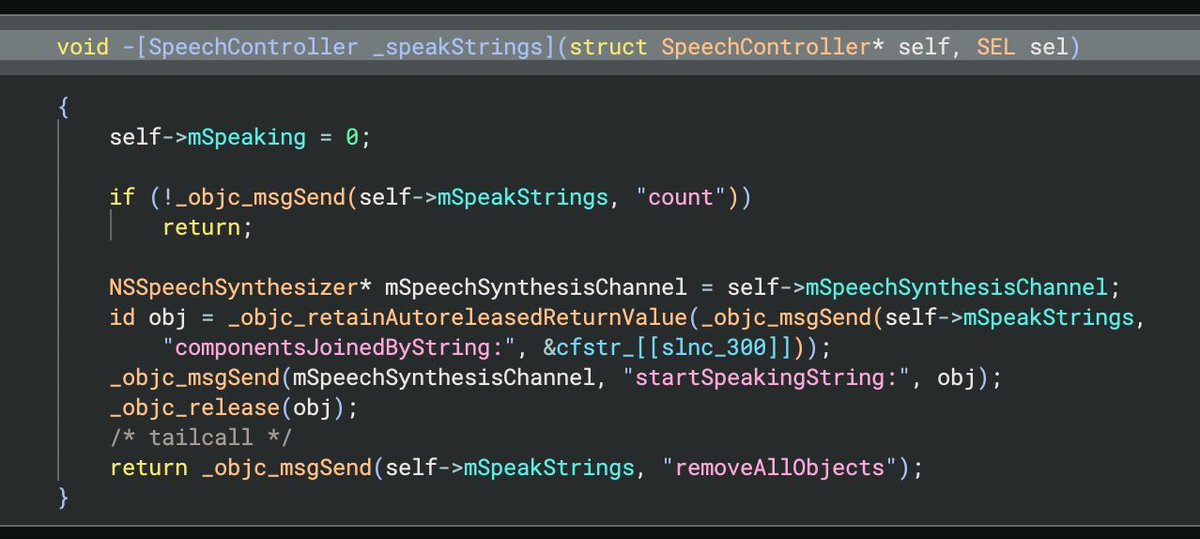
One of the coolest new things in Binary Ninja 5.1? Pseudo Objective‑C. Huge shoutout to @bdash, who actually wrote this before joining the team (talk about an overkill job application). If you’re digging into iOS, Swift, or kernelcaches, this one’s a game‑changer.
0
0
14
RT @motuariki_: macOS malware: Amos Stealer variants have been busy. Here are some malicious domains being used to spread them. Hashes conn….
0
14
0
Trip to London last week for @objective_see #OFTW. Taught an arm64 class and did a macOS malware reversing demo. Got to see/meet a lot of cool people! Thanks to @andyrozen and @patrickwardle as always. Shoutout to @vector35 for providing binja licenses to students :)
1
8
44
RT @theevilbit: 🍎🐛macos 15.6 is out, a few new CVEs and mentions. NetAuth.Impact: An app may be able to break out of its sandbox.CVE-202….
0
7
0