Snowscan
@snowscan
Followers
6K
Following
2K
Media
14
Statuses
373
Load "$",8; Red Team
Canada
Joined January 2009
My new blog for Check Point Research - check it out! 💙 // #ProcessInjection : #WaitingThreadHijacking
Thread Execution Hijacking is one of the well-known methods that can be used to run implanted code. In this blog we introduce a new injection method, that is based on this classic technique, but much stealthier - Waiting Thread Hijacking. Read More :
14
132
441
#pypykatz new version 0.6.11 is out on github and pip. Big thanks to all awesome contributors!! Besides the fixes, the two important things in this version: - Kerberos aes keys extraction is now supported - !!!!Windows 24H2 support is here!!!!! https://t.co/BFvq0VMkWD
github.com
What's Changed Supporting Windows 24H2 dumps @skelsec :) Fixing Service User Bug by @brettgus in #169 Fix Python 3.12 SyntaxWarning (use raw strings) by @X0RW3LL in #163 aesKey extraction by @...
5
51
144
Introducing PowerHuntShares 2.0 Release! NetSPI VP of Research @_nullbind introduces new insights, charts, graphs, & LLM capabilities that can be used to map the relationships & risks being exposed through the network shares: https://t.co/t04BNLmuot
3
36
109
CcmPwn is equipped with various modules. The “exec” module runs an AppDomainManager Injection payload for every logged-in user. The “coerce” module coerces SMB/HTTP authentications, which can then be used for password cracking or relay attacks. 👇 https://t.co/QrfZr4VGKB
github.com
Contribute to mandiant/ccmpwn development by creating an account on GitHub.
0
18
70
Found a flaw in NetBSD's utmp_update allowing injection of ASCII escape sequences into utmpx logs, leading to unexpected terminal emulator behavior and utmpx database integrity concerns. https://t.co/tNbdfD3zT3
#NetBSD #Security
1
14
21
Struggeling to get those precious certificates with #certipy and AD CS instances that do not support web enrollment and do not expose CertSvc via RPC? @qtc_de has you covered and added functionality to use DCOM instead of good old RPC #redteaming
github.com
In the last few months, we encountered more and more ADCS instances that neither supported web enrollment, nor exposed the CertSvc via plain RPC. The output of certipy req looks like this in that c...
3
70
154
It's been quiet for a while around bloodhound Python, however I'm happy to share that I am now maintaining the project at my personal GitHub. The latest version fixes many bugs/issues, also thanks to the many PRs that were submitted (thanks all!).
github.com
A Python based ingestor for BloodHound. Contribute to dirkjanm/BloodHound.py development by creating an account on GitHub.
11
201
631
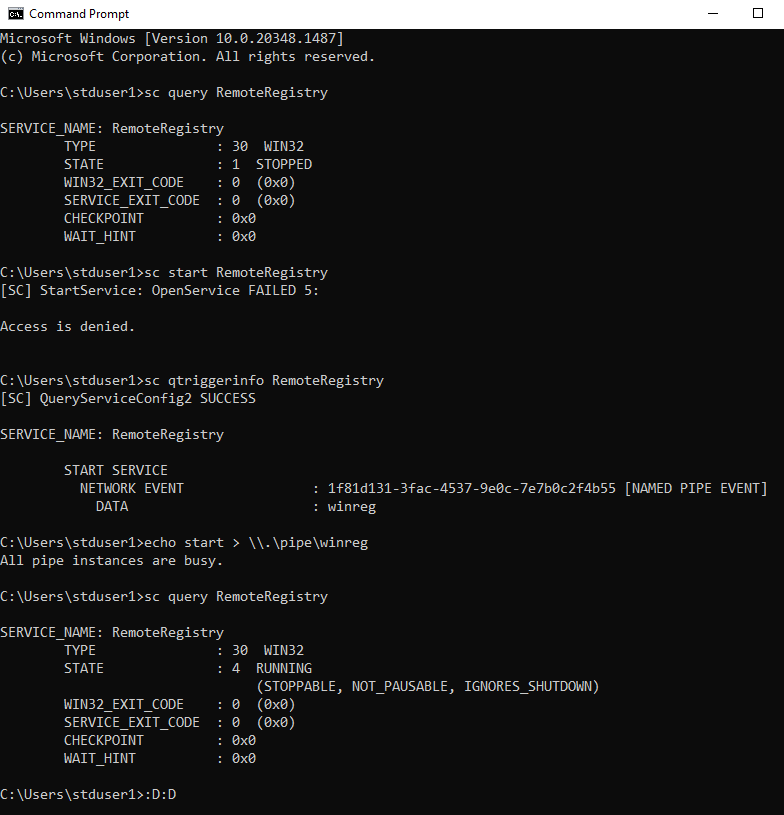
Do you want to start the RemoteRegistry service without Admin privileges? Just write into the "winreg" named pipe 👇
25
309
1K
Did Bethesda hire the Microsoft UX team to work on Starfield? This is so shit. Really disappointed with the game so far.
0
0
6
Thanks to the generous folks @bcsecurity @hackthebox_eu @SANSOffensive @sektor7net and @nostarch for sponsoring prizes at the DEF CON Red Team Village CTF!
0
1
10
You can use the Windows Search Protocol to coerce authentication from hosts running the Windows Search Service (Win10/11 only by default) as a regular domain user. Haven't been able to do WebDAV with it though so usefulness is limited. PoC:
github.com
PoC to coerce authentication from Windows hosts using MS-WSP - slemire/WSPCoerce
5
101
286
🔥 Excited to share my latest @Mandiant Red Team blog on "Escalating Privileges via Third-Party Windows Installers" https://t.co/01nYd4DmzJ Learn how attackers exploit this privilege escalation vector and ways to defend against it. Includes BOF release and a couple CVEs!
cloud.google.com
7
148
353
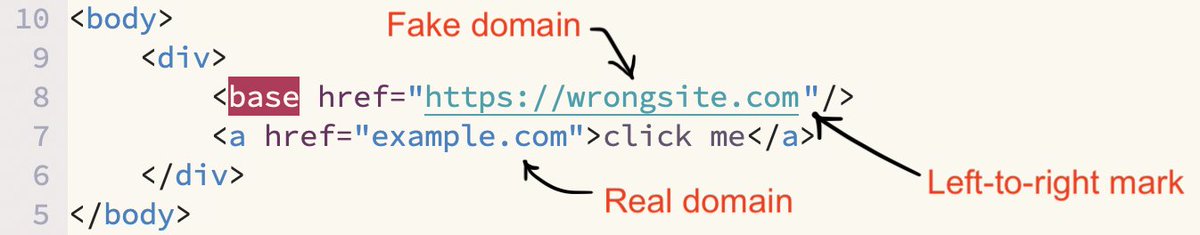
Been playing with the .zip TLD for phishing, apparently Outlook on Windows doesn't let you click links containing credentials, mitigating the "attack". haven't seen anyone talk about this, weirdly. after looking into this a bit, I found a way to bypass this behaviour!
1
9
17
Introducing ETWHash! ETWHash is a new method and tool by @lefterispan for consuming SMB events from Event Tracing for Windows (ETW) and extracting NetNTLMv2 hashes for cracking offline. https://t.co/wLmsQf71J8
lrqa.com
ETWHash is a small C# tool used during Red Team engagements, that can consume ETW SMB events and extract NetNTLMv2 hashes for cracking offline, unlike currently documented methods.
0
172
328
More quality video content by @xct_de. Those labs are really great.
I'm starting a new video series on pentesting the new lab (Wutai). In the first one, we'll start from the perspective of an unauthenticated, external attacker and will mainly focus on enumeration and getting initial access. https://t.co/2XvuKMM60e
0
0
3
Vulnlab just released a new Active Directory lab called Wutai! Like Shinra, it’s a simulated corporate environment with about 15 machines spread across multiple networks, domains & forests. The lab focuses on exploiting misconfigurations & users - not CVEs.
10
154
543