Antonio Cocomazzi
@splinter_code
Followers
9K
Following
3K
Media
150
Statuses
2K
offensive security - windows internals | BlueSky: https://t.co/ytvJCoaF2c | Mastodon: https://t.co/hNIHa6L14d
Italy
Joined August 2016
The slides of our joint research talk “10 Years of Windows Privilege Escalation with Potatoes” at #POC2023 are out! 👉 https://t.co/nowgGQHA73 cc @decoder_it
4
148
380
Just published a summary of "modern" Windows authentication reflection attacks. Turns out reflection never really died. 😅 https://t.co/2YxXlaRMMC
decoder.cloud
Authentication reflection has been around for more than 20 years, but its implications in modern Windows networks are far from obsolete. Even after all the patches Microsoft has rolled out over the…
3
78
223
Blog post about my recent CVE-2025-58726, aka “The Ghost Reflection” is out, read it here: https://t.co/KnuLXeNLUc 🙃
semperis.com
Understanding how attackers use Ghost Service Principal Names to initiate authentication reflection can help you avoid similar vulnerabilities.
3
77
153
Remember the CredMarshalInfo trick? If you hadn’t applied the June 2025 patch, CVE-2025-33073 would have been critical. We know that in NTLM local auth, msg 3 is empty:You can drop sign/seal -> from Domain User to DomainAdmin escalation. 😅
5
63
225
Why lock your coding agent to one model when you can use them all? Cline is the open-source coding agent that connects to any inference endpoint - Bedrock, Vertex, Azure, or on-prem. Works everywhere your developers do: VS Code, JetBrains, CLI, and CI/CD.
1
0
1
Coercing machine authentication on Windows 11 /2025 using the MS-PRN/PrinterBug DCERPC edition, since named pipes are no longer used. Kerberos fails in this case due to a bad SPN from the spooler, forcing NTLM fallback.
4
83
282
Better socket handle visibility coming soon to @SystemInformer 🔥 When viewing a process handle table, SI will recognize files under \Device\Afd and retrieve information about their state, protocol, addresses, and more. Also works on Bluetooth and Hyper-V sockets 🤩
2
21
115
Apply here → https://t.co/0bH9DST7Nc Happy to chat if you want to learn more.
sentinelone.com
Take a look at the open positions at SentinelOne. We're dedicated to defending enterprises across endpoints, containers, cloud workloads, and IoT devices in a single cybersecurity platform.
0
0
1
The role is opened in multiple locations in Europe (we’re hiring across Italy, Spain, Poland, Czech Republic, Slovakia and France), with optional relocation support to Czechia if you'd prefer to move (must be eligible to work in the EU already at the time of applying).
1
0
1
If you’re into Windows internals, reverse engineering, exploits and anti-tampering research, breaking and defending at kernel level and want your work to power detection at scale this is your chance to do hands-on impactful research with a passionate and highly skilled team.
1
0
1
I’m hiring Staff Windows Security Researchers to join my XAT (eXploits and Anti-Tampering) team at @SentinelOne! 🔥 👉 https://t.co/0bH9DST7Nc More details 👇
sentinelone.com
Take a look at the open positions at SentinelOne. We're dedicated to defending enterprises across endpoints, containers, cloud workloads, and IoT devices in a single cybersecurity platform.
1
3
10
In my long history of submissions, I think this is the first time one has been marked as critical😅
3
1
84
Another Monday. Another week of… endless emails, annoying meetings, and oh look, a three-headed monkey behind you! Now that we have your attention, we can unveil the agenda for #RomHack2025
https://t.co/P793dQAZdu
#infosec #securityconference
0
11
35
I just published a blog post where I try to explain and demystify Kerberos relay attacks. I hope it’s a good and comprehensive starting point for anyone looking to learn more about this topic. ➡️ https://t.co/OztMeuoU5L
decoder.cloud
While I was reading Elad Shamir recent excellent post about NTLM relay attacks, I decided to contribute a companion piece that dives into the mechanics of Kerberos relays, offering an analysis and …
2
150
351
Microsoft has discovered post-compromise exploitation of CVE 2025-29824, a zero-day elevation of privilege vulnerability in Windows Common Log File System (CLFS), against a small number of targets.
microsoft.com
Microsoft Threat Intelligence Center (MSTIC) and Microsoft Security Response Center (MSRC) have discovered post-compromise exploitation of a newly discovered zero-day vulnerability in the Windows...
8
120
305
NTLM relay is still a major threat and is now even easier to abuse. We just added new NTLM relay edges to BloodHound to help defenders fix and attackers think in graphs. Read my detailed post - the most comprehensive guide on NTLM relay & the new edges: https://t.co/6MnmlzVjNq
specterops.io
NTLM relay attacks have been around for a long time. While many security practitioners think NTLM relay is a solved problem, or at least a not-so-severe one, it is, in fact, alive and kicking and...
6
111
259
We (me + @2igosha) have discovered a new Google Chrome 0-day that is being used in targeted attacks to deliver sophisticated spyware 🔥🔥🔥. It was just fixed as CVE-2025-2783 and we are revealing the first details about it and “Operation ForumTroll”
securelist.com
Kaspersky GReAT experts discovered a complex APT attack on Russian organizations dubbed Operation ForumTroll, which exploits zero-day vulnerabilities in Google Chrome.
9
100
284
Check out our new blog post!
🍎🚨🕵️♂️ The notoriously elusive macOS malware, ReaderUpdate, is back — stealthier than ever. @philofishal and @syrion89 uncover how ReaderUpdate Reforged blends Go, Crystal, Nim, and Rust into a potent mix. 📄 This new research from SentinelOne exposes how these new variants are
1
5
13
new #elastic defend rules out : - PPL bypass via ComDotNetExploit - Execution via Windows-Run (trending delivery method ITW) https://t.co/YowLJu4IIJ
1
23
98
Do you want to invest like a champion? Get the best research tools available. Join @MarketSurge for the best trading platform —> https://t.co/M9dl0wflVQ
18
31
89
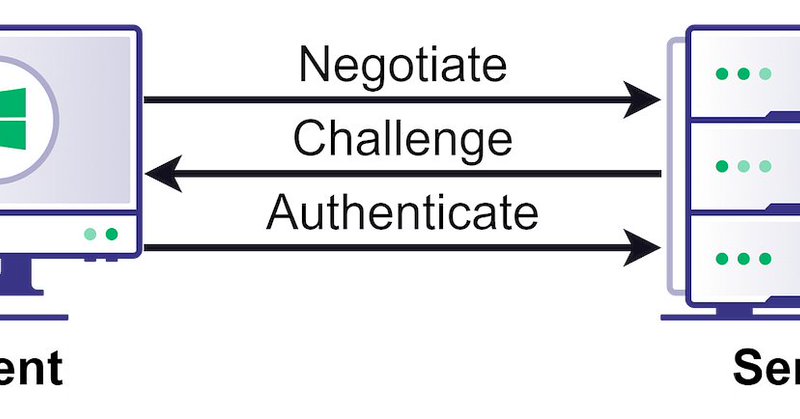
Hey, we should really switch from NTLM to something like Kerberos, yet another good reason, right? cc @ShitSecure @splinter_code 😂🤣
5
37
183
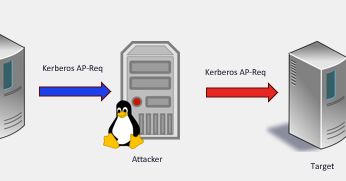
KrbRelayEx-RPC tool is out! 🎉 Intercepts ISystemActivator requests, extracts Kerberos AP-REQ & dynamic port bindings and relays the AP-REQ to access SMB shares or HTTP ADCS, all fully transparent to the victim ;) https://t.co/Aebt5iFIjC
6
161
393