sleirsgoevy
@sleirsgoevy
Followers
11,765
Following
0
Media
5
Statuses
121
Explore trending content on Musk Viewer
#Mステ
• 394828 Tweets
#Mステ
• 394828 Tweets
billie
• 285835 Tweets
CHASING THE SUN
• 131835 Tweets
Scottie
• 97954 Tweets
Valhalla
• 42825 Tweets
#のらりクラり呑もうの会
• 35886 Tweets
Louisville
• 31391 Tweets
ひーくん
• 28890 Tweets
ジュラシックワールド
• 16989 Tweets
トップバッター
• 15114 Tweets
しーちゃん
• 14549 Tweets
Mリーグ
• 12843 Tweets
Go City Go
• 12792 Tweets
ベビモン
• 11446 Tweets
NEW hair
• 10988 Tweets
佐々木朗希
• 10591 Tweets
西洸人くん
• 10402 Tweets
#大倉忠義オンライン飲み会
• 10120 Tweets
BACK TO THE BEGINNING
• 10006 Tweets
Last Seen Profiles
@SpecterDev
@tihmstar
select (f_poll) is a better target than ioctl (f_ioctl) imo. It only checks that the refcount is nonzero, while ioctl also checks that the mode allows either read or write.
7
8
186
@SpecterDev
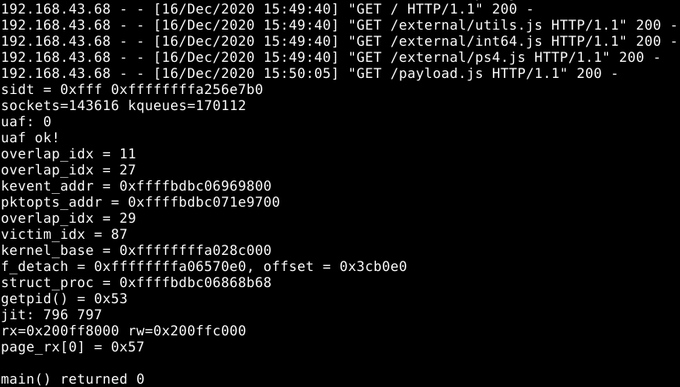
Regarding zone reclaim on PS4, in this specific exploit the PS4 (for some weird reason) allocates even small packets in mbufs with clusters, i.e. the mbuf_packet zone, and to drain that you need to exhaust all clusters. That is the only way to do it, uma_reclaim does not work.
9
8
171
@Goukifafa
The kernel exploit just completed. Now what's left is just to put mira on top of it.
11
12
135
@_AlAzif
It's not just dlsym. The payloads uses dlopen with just library name, not full path, and that fails.
1
5
115
@_AlAzif
Just tried to run the 7.02 Mira build. And you guessed it, it does not run. I can't even see the "waiting for payloads" popup. [Probably the boot patches are the cause.]
10
8
78
@PS4Trainer
I identified the problem with WebRTE on my exploit host. Your payload expects being loaded at a constant address (possibly 0x926200000), i.e. is not PIE, but MiraLoader maps the payload at a system-provided address, so it only works with PIE payloads.
3
7
61
@Goukifafa
contains the combined jb+netcat payload. You can try your luck with sending payloads to it, but Mira/HEN are not working yet.
2
7
43
@notzecoxao
Как померять высоту здания с помощью барометра? Бросить его с крыши и засечь, сколько он будет падать.
3
2
46
@notnotzecoxao
Or even better, run the porting tool and contribute the offsets for ps5-kstuff.
3
4
47
@Louzi19881279
I think no valuable improvement will be done unless a new bug surfaces (at least an infoleak).
3
4
40
@rasheed_daley
This one doesn't work, but it will once ported. It should say that it failed to guess.
2
2
39
@notzecoxao
Should be possible to chain with a SELF dumper. I've verified that mapping itself works.
2
2
34
@_AlAzif
The way it has been added is wrong. It is now broken due to exploit.js being minified. Please upload a non-minified version of exploit.js instead.
Also the success rate is more like 30%, 10 retries is my personal worst-case.
10
0
34
@Harsh83106577
No, I have 6.72 data myself. What i want to see is how 5.05 is different from 6.72, to get an insight into what how it changes between firmwares and what to expect on 7.02.
1
0
17
@rohanmannan
@notnotzecoxao
This is for the PS5 versions 3.00 to 4.51 that have a kernel exploit.
1
0
17
@AbubakarShnk
It does not need to. It will just need to replay the pre-created image, no need to understand its inner structure.
1
0
14
@AR_JRIDI
This is not an exploit. I am trying to collect statistics about how the unknown address changes between firmwares. I have the 6.72 data myself and am trying to collect some logs from 5.05 owners.
1
0
10