Marina Simakov
@simakov_marina
Followers
2K
Following
395
Media
9
Statuses
211
RT @snd_wagenseil: #blackhat2025 has spoken: AI security is so awful, it's like the '90s all over again! Comments from @beccalunch @wendyna….
scworld.com
The startling lack of good security practices around AI has cybersecurity veterans wondering which decade we're living in.
0
3
0
RT @wunderwuzzi23: 💥 Remote Code Execution in GitHub Copilot (CVE-2025-53773) . 👉 Prompt injection exploit writes to Copilot config file an….
0
215
0
RT @tamirishaysh: We got ChatGPT to leak sensitive data from your Google Drive data back to OUR servers. And you’ll never even know it happ….
0
18
0
RT @simonw: Apparently @cursor_ai's official position on MCP is "MCP servers, especially ones that connect to untrusted data sources, prese….
0
28
0
RT @mbrg0: next. we hijacked cursor via jira mcp by submitting a support ticket. cursor harvests and exfiltrate all creds from your dev ma….
0
269
0
RT @mbrg0: we got a persistent 0click on ChatGPT by sharing a doc. that allowed us to exfiltrate sensitive data and creds from your connect….
0
194
0
Connect your powerful AI agent to an MCP server. Enable auto-run. What could possibly go wrong? 😈.Turns out, when using Cursor with a Jira MCP, any local secret - API keys, AWS creds, SSH keys - is up for grabs.
labs.zenity.io
TL;DR: A 0click attack through a malicious Jira ticket can cause Cursor to exfiltrate secrets from the repository or local file system.
2
25
128
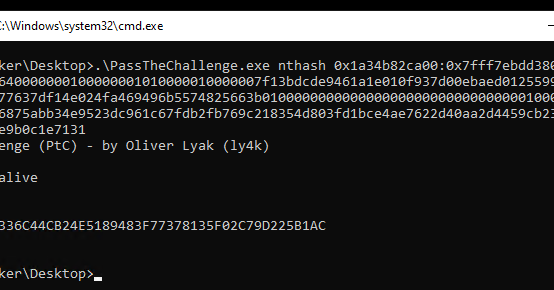
RT @ly4k_: Today we're publishing new techniques for recovering NTLM hashes from encrypted credentials protected by Windows Defender Creden….
research.ifcr.dk
In this blog post, we present new techniques for recovering the NTLM hash from an encrypted credential protected by Windows Defender…
0
686
0
RT @_dirkjan: I've added the material from my Black Hat US talk yesterday to my blog. If you are interested in Azure AD security, love acco….
0
304
0
1/2 Three years ago @YaronZi and I presented a generic NTLM relay detection at #BHUSA. Recently, we extended it to detect machine accounts relay, independent of the coercion tactic used (PetitPotam, ShadowCoerce, DFSCoerce, etc.).
crowdstrike.com
In this blog, we discuss the PetitPotam vulnerability, and an enhancement to Falcon Identity Protection’s existing NTLM relay detection.
1
8
15
RT @filip_dragovic: Spooler service disabled, RPC filters installed to prevent PetitPotam and File Server VSS Agent Service not installed b….
0
516
0
RT @gentilkiwi: We saw a lots of problem after KB5005565 patch (or others KB on September 2021 patch tuesday), thinking it was related to #….
0
37
0
RT @harmj0y: 5 months ago @tifkin_ and I started looking into the security of Active Directory Certificate Services. Today we're releasing….
posts.specterops.io
Active Directory Certificate Services has a lot of attack potential!
0
642
0
RT @eyal_karni: NTLM relay refuses to die! A new blog is alive with details about the cool vuln in Print Spooler we have found!.It was patc….
crowdstrike.com
On Patch Tuesday, January 12, 2021, Microsoft released a patch for CVE-2021-1678, an important vulnerability discovered by CrowdStrike researchers.
0
164
0
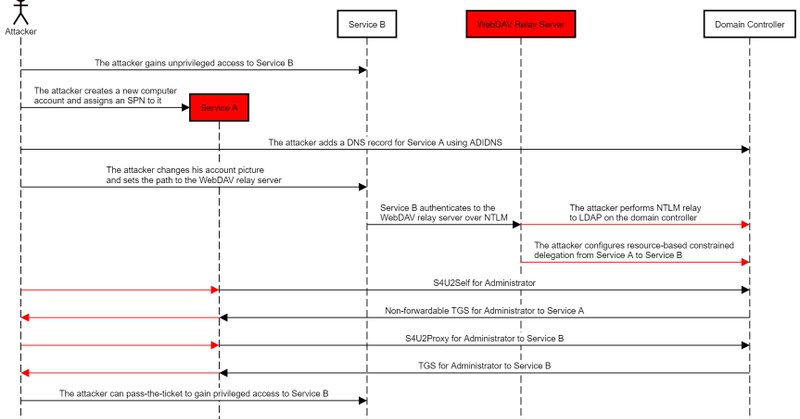
While the Bronze Bit vulnerability was patched, the ability to bypass the "Kerberos Only" protection in Kerberos Constrained Delegation was published 2 years ago by @elad_shamir and still works today against patched DCs 😇
shenaniganslabs.io
Back in March 2018, I embarked on an arguably pointless crusade to prove that the TrustedToAuthForDelegation attribute was meaningless, and that “protocol transition” can be achieved without it. I...
0
8
31
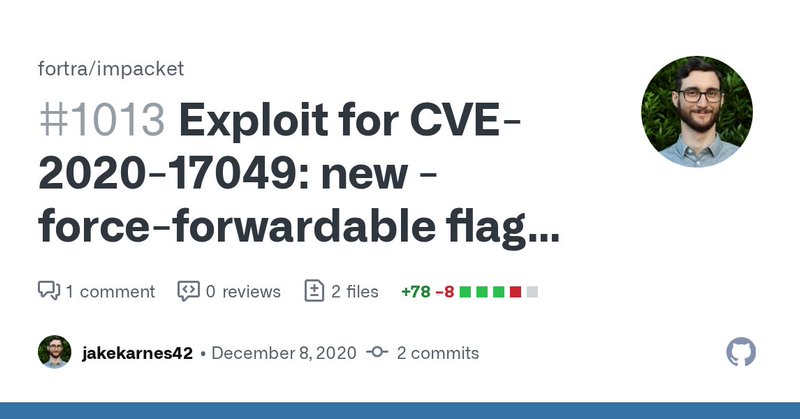
RT @agsolino: Just merged @jakekarnes42 implementation CVE-2020-17049 (aka Kerberos Bronze Bit Attack). Great stuff and thorough explanatio….
github.com
This pull request adds the exploit for CVE-2020-17049 the "Kerberos Bronze Bit" attack. An overview of the vulnerabiltiy is available here, and a deep dive into the issue is here....
0
109
0
Great write up on how any service account with Kerberos constrained delegation permissions can be used with protocol transition to get a ticket for any user (including "sensitive users which cannot be delegated") by flipping a single bit ("forwardable" flag of the service ticket).
All the details for CVE-2020-17049 are now available! The overview contains a summary of the vulnerability and its exploit, including links to 2 deep dive posts which cover much more.
1
0
4
Excited to join the @CrowdStrike team! 🎉.
Today, we are delighted to share that @CrowdStrike, a leader in cloud-delivered endpoint and cloud workload protection, announced that it has agreed to acquire @preemptsecurity and its industry-leading Conditional Access technology. Learn more here:
0
1
11