Paweł Hałdrzyński
@phaldrzynski
Followers
772
Following
29
Media
2
Statuses
249
Researching web applications' security at daylight - auditing smart contracts at night
Poland
Joined November 2019
For the 2nd year in a row, my research was chosen for 'Top 10 web hacking techniques'. It's very encouraging that my 'WAF evasion techniques' is among other awesome researches and that I'm able to share my security thoughts with the #infosec community!
portswigger.net
Welcome to the Top 10 (novel) Web Hacking Techniques of 2020, our annual community-powered effort to identify the must-read web security research released in the previous year. Over the past few weeks
1
10
34
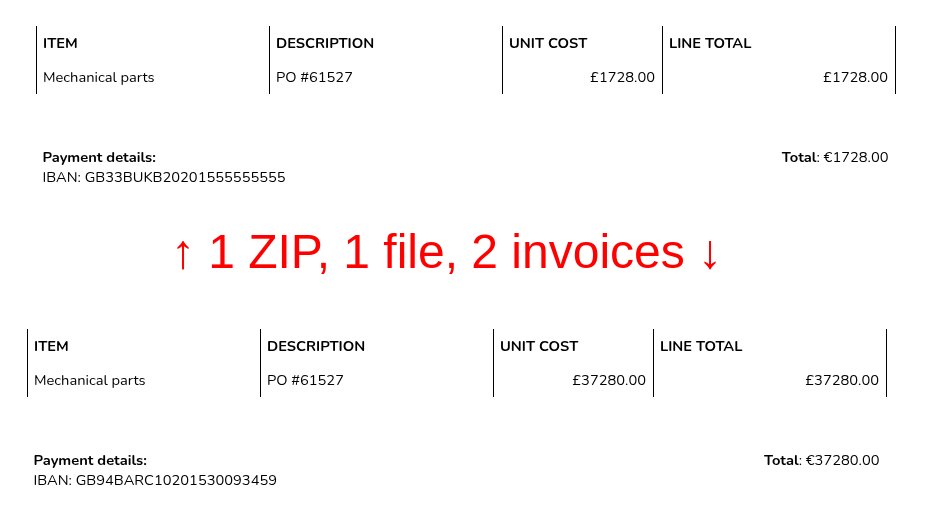
Nice trick showing that the very same zip can be seen differently by two different programs. I've examined how this quirk could help us in zip path traversal attacks:.
blog.isec.pl
Recently, I stumbled upon a very interesting article – Yet another ZIP trick. It demonstrates a concept called schizophrenic file – a file which is interpreted differently by two different programs....
0
25
83
You can confuse WAFs even more, by explicitly stating the number as positive or negative (and you can use multiple of + - characters)!. There's one weird oddity with BigInt, however. You can do: `let x = -0o1337n`, but - `let x = +0o1337n` leads to TypeError: can't convert BigInt
You can use big int after any number including octals, hex and binary. Oh JS I love your quirky nature ❤️. Might help bypass a flawed WAF regex.
0
2
10
Been doing web2/mobile bug bounties on and off. Recently, added web3 to my bug bounty routine. The platform choice was obvious - @immunefi .It's interesting how even Low severity issues in web3 can lead to 4-digits payouts.
7
4
70
RT @phaldrzynski: @nav1n0x Shaming some company for having vulnerabilities is absolutely wrong. Let's criticize the programs which purposel….
0
2
0
Many people who are complaining that you can do better (earn more) by doing competitions - do not realize that there's a huge difference between the audit and the competition. Competitions reward unique findings the most. It's more incentive to dig into some particular part of.
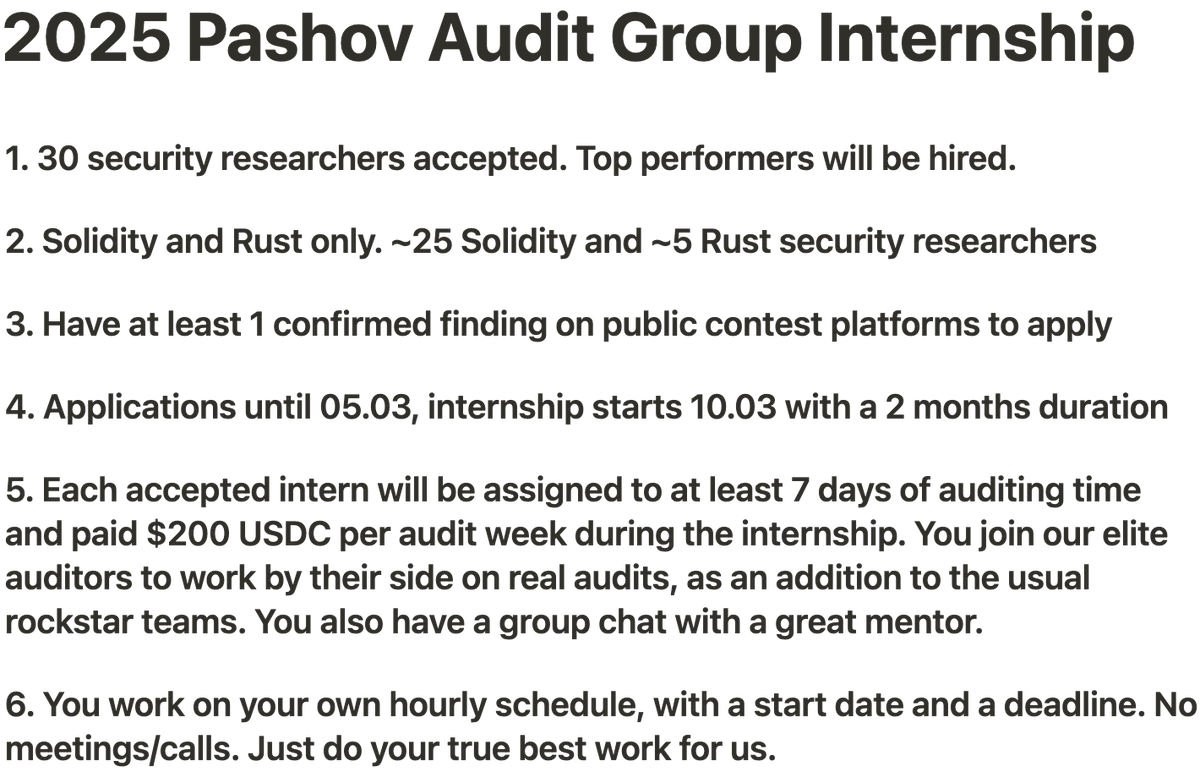
The 2025 Pashov Audit Group security researcher internship program is now official. This is not for 1st day beginners - real projects, real audits, pure practice. Like/RT this post, then apply in the form in first comment for a chance to join us🫡
0
0
2
In web2, more and more people start to understand the difference between an audit, pentest and vulnerability assessment. I'm glad this discussion finally starts to appear in web3 too. Using proper terminology will help everyone: Customer - who decides what model to evaluate the.
This is a good read. Bug bounty <> contests <> audits are related, but not the same. My hot take is many who primarily do bounties/contests don't transition well to audits, and vice versa. Credit to @0xalpharush, found this while scrolling through your feed.
0
0
4
Not only was it my first Live Hacking Event, but also the first time I have ever been on stage!.I was nominated to do a Show and Tell and talked about the vuln. I had found during #AmbassadorWorldCup #AWC2024 Elite Eight round. It was nice to meet so many amazing, skilled people,.
What a way to finish the Elite Eight round! 💪. Each of these amazing teams' incredible work over the last 11 days is something to be extremely proud of. On behalf of the entire HackerOne team and our #AmbassadorWorldCup partners @ASWatsonGroup and @okx--- THANK YOU! 🙌 . Stay
2
0
9
Cannot agree with this. If you want professionals, then you either open an invite-only program and spend time on selectively choosing the right bug-hunters for your target, or you request a pentest/vulnerability assessment. You can't have your cake and eat it too. Open bug bounty.
@DKidolle This is a platform to connect professionals, not a beginner playground. Locking accounts of low quality researchers for a few months + giving them some resources to learn is much better to let them consider the platform as their training resource.
0
0
0
Not only this. Hallucinations are even bigger concern. 1. AI hallucinates package name which does not exist. 2. Attacker creates that package with malicious code.3. Voilà - you have a backdoored code copy-pasted from LLMs.
As a hacker I am thrilled to see how often LLMs produce vulnerable code. 👏. As someone who cares about cybersecurity, I'm low-key terrified 😬.
0
0
2
This behavior can be easily explained, when we'll deep-dive into EVM storage. MAPPING.Let's consider a mapping declared at SLOT_X. Whenever we assign new value to key K of this mapping, its value is being stored at: `keccak256(K || SLOT_X)`. We can easily calculate where the.
So today I was not able to recall which data type does not revert on "out of bound" access ? 👀. You too are not able to ? ❗.- nevermind here you go 👇
0
0
0
This was fun web3sec competition! I missed a few rounds, yet I managed to get more points then the combined score of the next 3 players!.I've asked @Slavcheww to donate my reward to the children charity organization🙃.
🏆 Find the Bug - Results 🏆. 🥇 @phaldrzynski with 14 points - $100 💰.🥈 @Tigerfrake with 6 points - $50 💰.🥉 @AhmetSaidOuz1 with 4 points - $30 💰. @AhmetSaidOuz1 also won $30 from the #4 challenge. Thanks again to everyone involved. It has been a great experience for me to
0
0
0
Amazing research! Some of the payloads look crazy, yet they are still compliant with RFCs - this is insane! Using encoded-words seems like pretty novel technique, which will definitely lead to many interesting access-control findings!.
Everyone knows that the RFCs for email addresses are crazy. This post will show without doubt that you should not be following the RFC.
0
1
5
Another top-notch research - demonstrating how, even small time differences can lead to valuable info about the target! Absolutely a must-read for anyone who wants to know how much info we can predict from observing just the server response's time.
The whitepaper is live! Listen to the whispers: web timing attacks that actually work. Read it here ->.
0
0
2
During the hiatuses from researching web2 security, I've decided to deep-dive into web3 security. I've started my journey with amazing @RealJohnnyTime's course. Recently, I designed a new reentrancy challenge/exercise, which was published there!.
I often get asked, "Will the course be updated with new lectures?".My courses are constantly updated with new content and challenges. This time, SCH course is upgraded with a brand new Reentrancy exercise inspired by one of our students (@phaldrzynski) 💪.Live on SCH NOW 🔴.
2
1
5
Actually, tel: URI (according to RFC-3966) is not only limited to XSS. You can try:.a) SQLi: +123;phone-context='or1=1--.b) param pollution: +123;phone-context=x&phone-context=y.c) or even SSRF, if the library really parses that URI: +123;phone-context=server - this is even.
Target: "Please enter your phone number" 🤠 .You: +441134960000;phone-context=<script>alert(1)</script> 🤑.
1
0
1