pyn3rd
@pyn3rd
Followers
13K
Following
4K
Media
208
Statuses
843
Security Researcher&Red Team&Cloud Security. BlackHat&HITB&CanSecWest Speaker.
Leeds, England
Joined February 2016
RT @nirohfeld: We (+@sagitz_ @ronenshh @hillai) found a series of unauthenticated RCEs in core @KubernetesIO project "Ingress-NGINX". The….
0
157
0
It was a genuine pleasure meeting @infosec_au in Sydney and receiving your insightful advice and valuable information. Thank you! Hope to see you again soon!.
2
0
24
RT @artsploit: Last year, I committed to uncovering critical vulnerabilities in Maven repositories. Now it’s time to share the findings: RC….
0
84
0
I truly appreciate @albinowax's kind help in adding both my blog and slides to Web Hacking Techniques 2024.Thank you so much!.
0
1
16
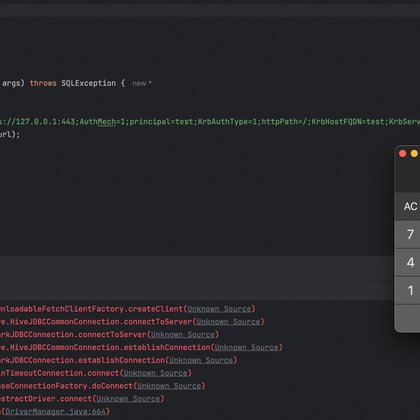
#CVE-2024-49194 Databricks JDBC Driver via JAAS, Make JDBC Attack Great Again!!. I’ve included the link to my write-up below. Enjoy!!.
blog.pyn3rd.com
Background StoryYesterday, I received a threat intelligence alert regarding the Databricks JDBC driver. After a quick review, I pinpointed the root cause of the issue. The vulnerability stems from imp
4
49
177
RT @tonghuaroot: Just read "Make JDBC Attacks Brilliant Again", a fantastic 3-year-old research piece that @pyn3rd recently recommended to….
0
4
0
Demonstration attached here.
#CVE-2024-21733, a Tomcat HTTP Request Smuggling vulnerability, reminds me of the HeartBleed vulnerability, which had a profound impact 10 years ago. In both cases, buffer over-reading is the root cause. Attacker is overwhelmingly likely to skim sensitive data from buffer cache.
0
2
11