Lucian Constantin
@lconstantin
Followers
3K
Following
86
Media
6
Statuses
759
Cybersecurity journalist and senior writer for https://t.co/y9moSKElY9. Past work featured in Forbes, Motherboard, The New Stack, PCWorld, Computerworld, others.
Iasi, Romania
Joined January 2010
Bug hunters and pentesters are already using LLMs to find new vulnerabilities and write exploits faster. It's fair to assume threat actors are doing the same, potentially leading to an increase in the number of zero-days orgs will have to deal with.
csoonline.com
Large language models (LLMs) are proving to be valuable tools for discovering zero-days, bypassing detection, and writing exploit code, thereby lowering the barrier to entry for penetration testers —...
4
1
2
RT @SecEvangelism: Booked a room with @IHGCorporate @IHGhotels @IHGService hotel in Bratislava pre-paid with my points. The hotel tried to….
0
181
0
Mitigating insider threats is not easy, but the hijacking of Twitter verified accounts should motive other companies and organizations to be better prepared; with input from @RachelTobac and @HackingDave .
csoonline.com
The account compromise raises questions about Twitter's controls. Experts weigh in on best practices for mitigating risk from malicious or accidental insider threats.
1
6
22
RT @fwosar: Any cities or companies who are affected by #PwndLocker please contact me either here or via fw@emsisoft.com. If you know someo….
0
30
0
RT @lorenzofb: New: the ultimate guide on how to wipe your computers and cellphones. Learn how to wipe Windows, MacOS, Android and iOS de….
0
17
0
RT @_j3lena_: #exploringRomania is going on. Fabulose place in Bucharest .Joben Bistro with #HackerFamily .@jaysonstreet @herrJesper @obiwa….
0
5
0
RT @KimZetter: Good interview with @securelyfitz about the Bloomberg chip hack story by @riskybusiness. Joe, a hardware hacking expert, was….
0
90
0
RT @peteherzog: People took notes! That's how you know your presentation did well. Moderated by the famous security journalist @lconstantin….
0
4
0
RT @arstechnica: The adventures of lab ED011—“Nobody would be able to duplicate what happened there”
arstechnica.com
One Romanian campus computer lab both pentested the world and eventually helped protect it.
0
16
0
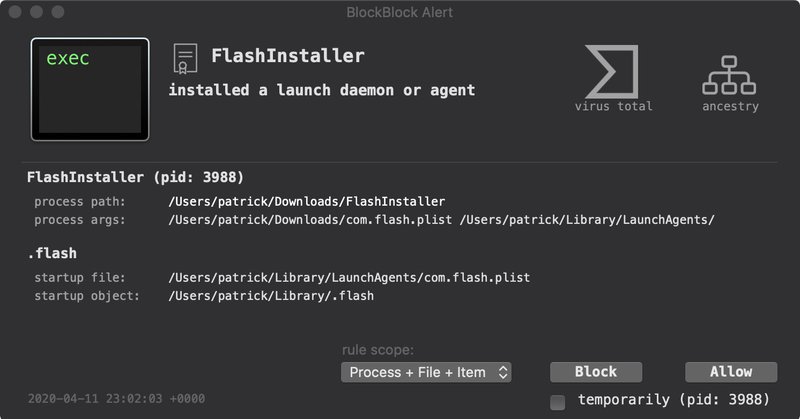
At a time when software supply-chain attacks and digitally signed Mac malware are common occurrences, this looks very suspicious. Thanks @patrickwardle for BlockBlock and other cool free Mac security tools
objective-see.org
Protection Against Persistent Mac Malware
1
6
14
RT @Jaymzu: Microsoft adopts a start-up mentality. Ain’t nobody got time to sign apps before publishing ;)
0
2
0
RT @lorenzoFB: In the wake of the CCleaner hack, @lconstantin explains what is a "supply chain" attack.
0
14
0
RT @motherboard: Researchers believe the CCleaner hack was done by a cyberespionage group backed by a nation-state:
0
35
0
RT @motherboard: A malware-infected CCleaner installer was distributed to users via official servers for a month ht….
0
95
0