khr@sh
@khr0x40sh
Followers
280
Following
2K
Media
66
Statuses
2K
Aspiring, self-taught developer (C, C++, C#, VB.Net, Perl, Python, Java) with interests in Information Security, humor, and well when appropriate, both.
USA
Joined November 2010
RT @DirectoryRanger: One Tool To Rule Them All. AMSI, CLM and ETW – defeated* with one Microsoft signed tool.
0
40
0
RT @0x534c: 🚨 New Malware Alert 🚨. 🐔 Golden Chickens (aka Venom Spider🕷️) has unleashed TerraStealerV2 & TerraLogger, targeting credentials….
0
23
0
RT @DarkWebInformer: 🚨CVE-2025-3776: Full WordPress Takeover Without Login (Critical RCE Exploit). Credit: https://….
0
258
0
RT @hackerschoice: 1-line "Living Off The Land" persistent DNS-reverse backdoor. (now added to . .
0
67
0
RT @hackerfantastic: Example of 1-click Telnet client exploit, MS-TNAP will automatically send credentials to hosts in Intranet or Trusted….
0
96
0
RT @Dinosn: Wshlient - A Simple Tool To Interact With Web Shells And Command Injection Vulnerabilities
0
34
0
RT @zeifan: A quick writeup on potential security issue of Windows LNK that I reported to MSRC last month. They decided to not fix due to r….
0
112
0
RT @Dinosn: CVE-2025-21756: How a Tiny Linux Kernel Bug Led to a Full Root Exploit, PoC Releases
0
74
0
RT @Wietze: 🚀 Today I'm launching ArgFuscator: an open-source platform documenting command-line obfuscation tricks AND letting you generate….
0
185
0
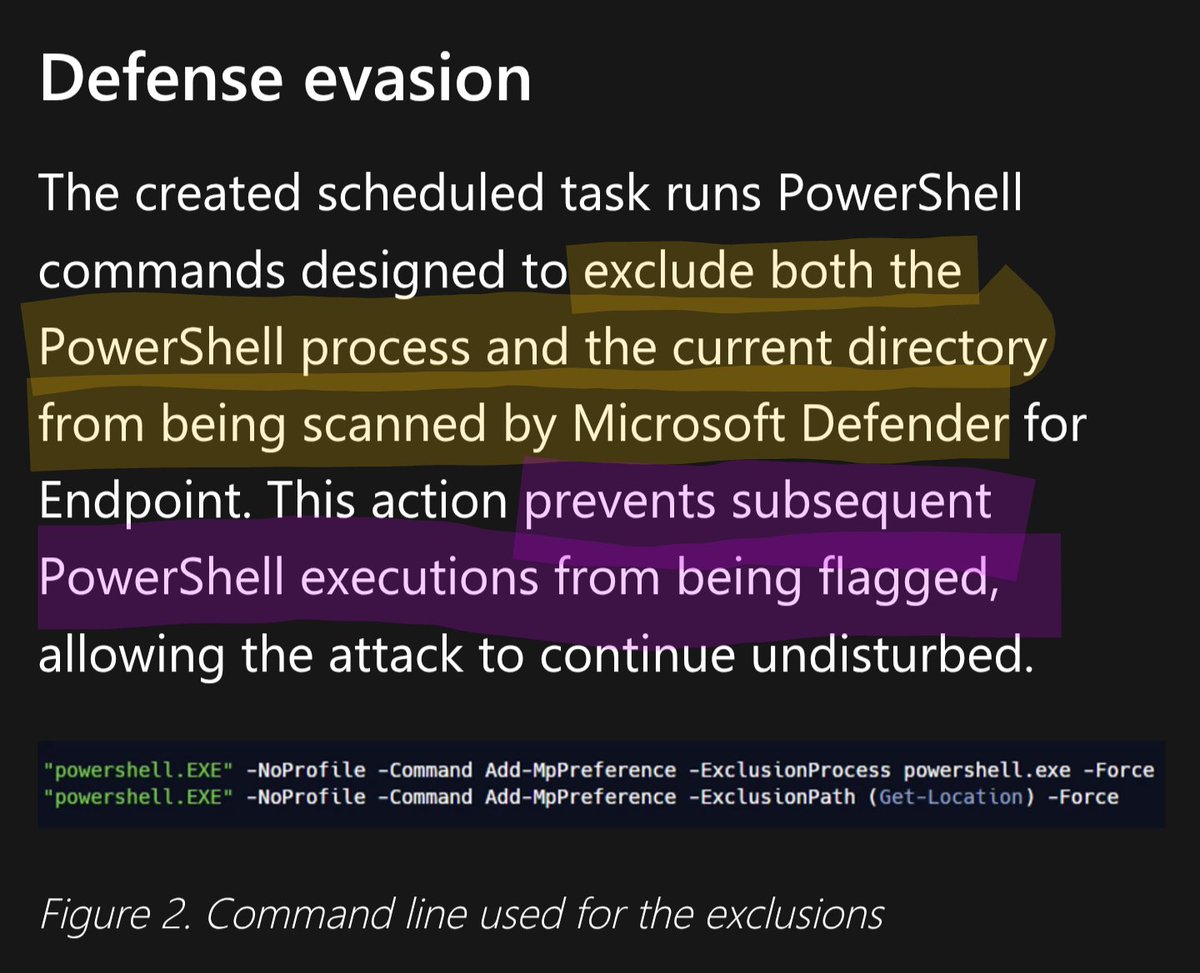
RT @binitamshah: Bypassing Windows Defender antivirus in 2025 : Evasion Techniques Using Direct Syscalls and XOR Encryption – Part 1 : http….
0
191
0
RT @0x64616e: NTLM Relaying with DCOM cross-session activation over an external OXID resolver. This variant has the advantage over regular….
0
77
0
RT @cyb3rops: In the past, you had to:.phish a user, drop malware, escalate privileges, pivot to servers, evade EDR, dump creds, move later….
0
178
0
RT @arekfurt: Oh come the f***🤬 on. You gotta be kidding. If an attacker can get a user to click a bloody WebEx meeting invite link they c….
0
84
0
RT @sensepost: The S is for Security. How to use WinRMS as a solid NTLM relay target, and why it’s less secure than WinRM over HTTP. By @De….
0
45
0