Juliano Rizzo
@julianor
Followers
9,638
Following
1,947
Media
396
Statuses
15,333
Explore trending content on Musk Viewer
Taylor
• 755466 Tweets
Leverkusen
• 405725 Tweets
hailey
• 269080 Tweets
TTPD
• 168887 Tweets
Whindersson
• 163101 Tweets
Selena
• 79234 Tweets
Celtics
• 66705 Tweets
Xabi Alonso
• 65370 Tweets
Maranhão
• 60755 Tweets
メイドの日
• 60538 Tweets
#虎に翼
• 54284 Tweets
Eddie
• 43008 Tweets
Garland
• 30924 Tweets
Endrick
• 29299 Tweets
Cavs
• 28081 Tweets
Tatum
• 26597 Tweets
メイド服
• 23837 Tweets
ドラマ化
• 21988 Tweets
Palacios
• 21310 Tweets
Cano
• 18321 Tweets
Cleveland
• 16911 Tweets
Galactus
• 15659 Tweets
PRISCILLA
• 15620 Tweets
#911onABC
• 15363 Tweets
San Lorenzo
• 14744 Tweets
Veiga
• 13401 Tweets
Canes
• 13176 Tweets
Last Seen Profiles
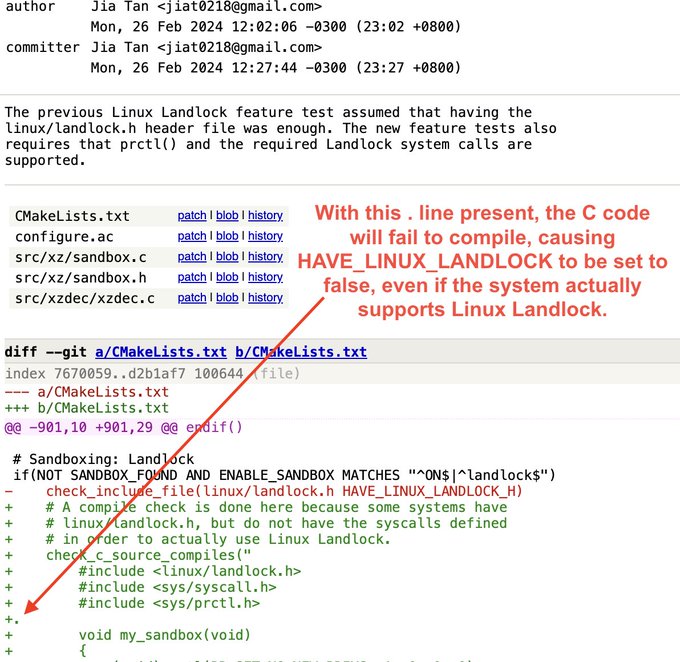
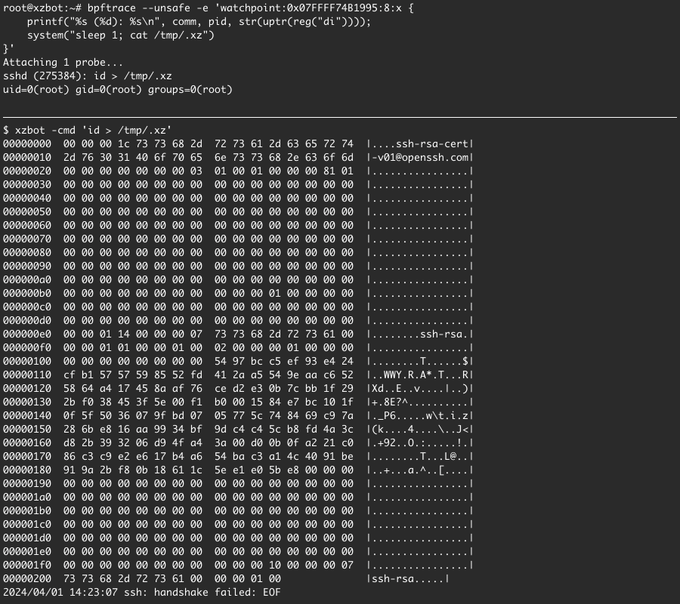
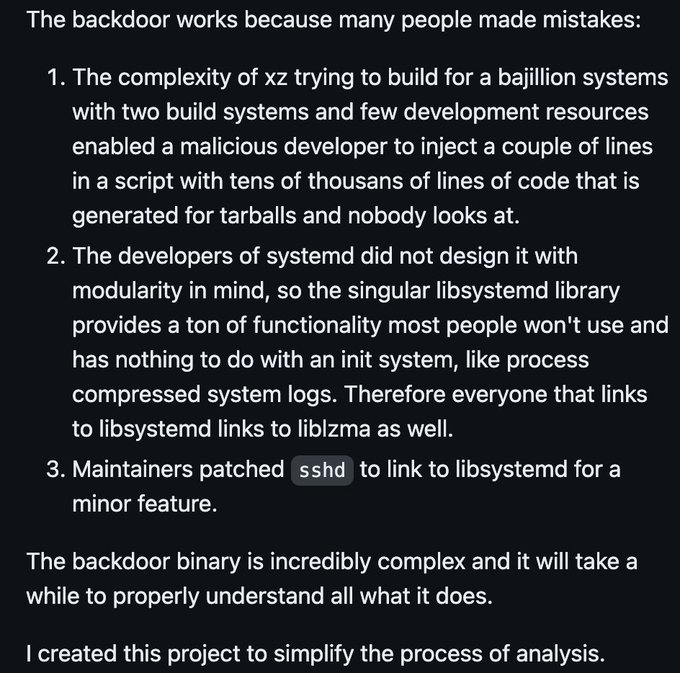
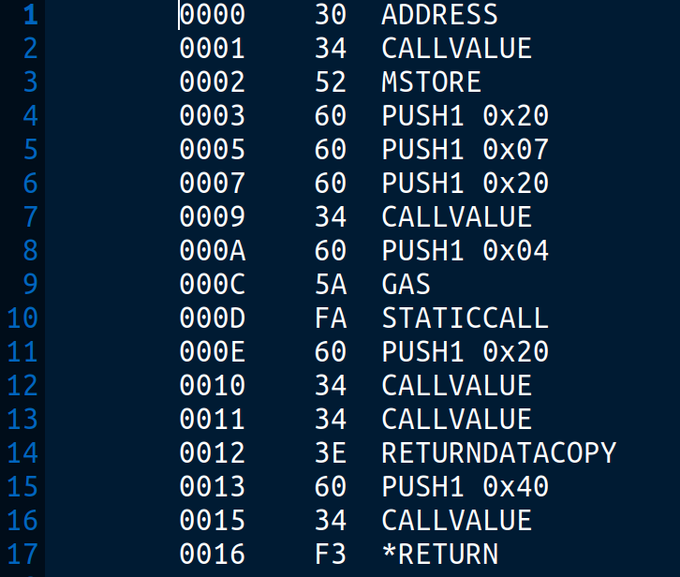
xz/lzma backdoor:
🔬 Discovered and analyzed by Andres Freund while investigating performance issues
🔎 GitHub "JiaT75" contributions now being audited
🐧Affected distros: Debian sid, Fedora 41/Rawhide, Arch Linux (5.6.1-1), NixOS unstable
☠️ Narrowly avoided wider impact
9
184
561
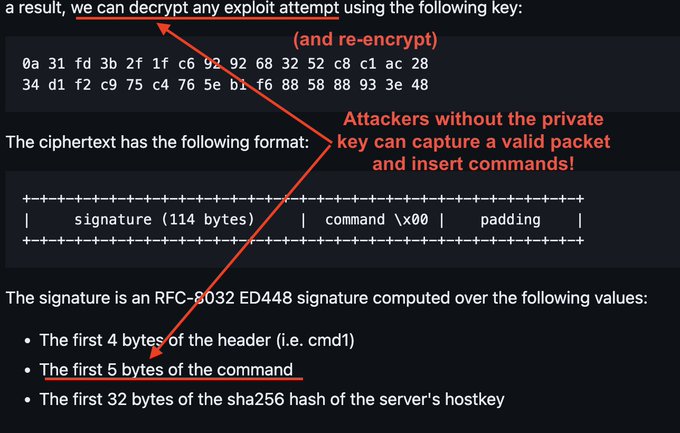
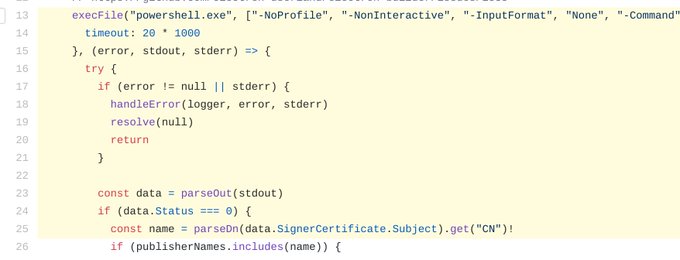
Reverse engineering by
@amlweems
reveals 3 flaws that allows attackers to use the backdoor without the private key, using only a captured message signed for the target host:
1. Lack of replay protection
2. Symmetric encryption with a hardcoded key,
3. Partially signed commands
6
105
389
CVE-2023-38408: Remote Code Execution in OpenSSH's forwarded ssh-agent
2
108
210
"100% reliable and portable exploit for MobileSafari on IOS7.1.x. can be downloaded from github" CVE-2014-4377
#ios8
http://t.co/dGWm5V7h4L
5
138
115
The Volkswagen attack but for apps!
"For example, an app could determine whether it was in Apple's review process, changing its UI so as not to fall foul of any App Store guidelines before unleashing popups asking for money on unsuspecting users. "
3
54
118
🤔🤥
The analysis Andres Freund did was without reading the source code, observing the system using tools like perf and gdb that do not require source code.
🗨️From his email:
"most of what I observed is purely from observation."
2
13
86
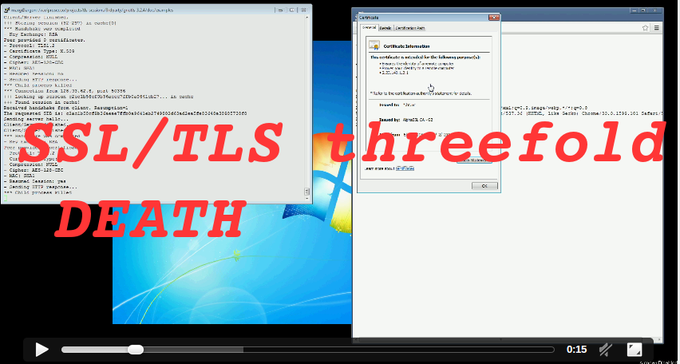
SSL/TLS Triple Handshake Attack Demo client cert authentication broken. Web exploit.
http://t.co/OHxx0u9XCi
4
91
80
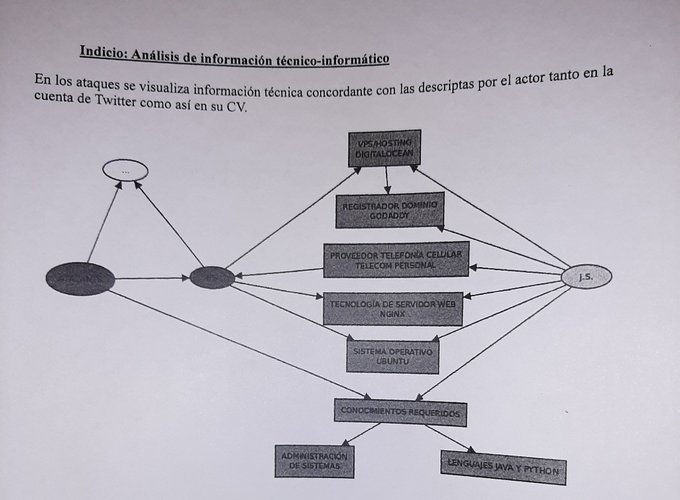
🤦♂️😳😥 Programmer was spied, raided, computer devices taken to examine personal files. Reasons provided by police "investigation" about an email leak? tweets about Java, Python, nginx, electronic voting systems, and being critic about the security of gov systems. Argentina.
Y hablando de cuestiones técnicas, parece que la
@PFAOficial
hasta hizo un diagrama con mis supuestas habilidaded. (Aclaro: no programo en java ni que me corten un brazo).
28
54
251
0
43
81
Jared Allard, 1Password employee, GitHub's account made a PR to update a dependency to the backdored version:
3
11
77
@julitolopez
Recuerdo de chico ver una noticia sobre un pueblo y que la explicación era pesticida:
7
14
71
1/ 🧵Recently, I've come across rumors about security issues at
#Cloudflare
, and it's really worrisome. High-impact attacks have been reported, somehow abusing their API. I can't believe this has been circulating for so long without any clarification.
4
25
62
SSL/TLS Checklist for Pentesters -Manual Configuration Tests Cheatsheet
http://t.co/RA7jPFfUL2
0
52
57
"For ECDSA signatures, the nonce K becomes significantly biased with up to 80 of the 256 bits being static, resulting in weakened signatures. This could allow an attacker who gains access to several signatures to reconstruct the private key."🤔
0
42
57
🎻 Spoiler: new post-quantum (🤌) code is packed with bugs that turn your private conversations into an open book for memory corruption exploit artists.
🪄But fear not, you're protected against adversaries wielding imaginary computers.
4
13
54
"Use Signal " the twitter security expert said. 2 wormeable remote code execution bugs in less than a week.
New variant of our vulnerability found in signal-deskop, already patched in v1.11.0
Here's the write-up w/ messages exfiltration PoC:
And the advisory:
Found by
@IAmMandatory
cc
@ortegaalfredo
@julianor
#CVE
-2018-11101
1
63
63
7
29
45
impressive exploit for nginx<=1.4.0 CVE-2013-2028 by sorbo
http://t.co/8qWNYF2T1z
64bit,finds canary byte by byte,blind rop, tcp frag,8-o ..
0
48
48
#BoletaUnicaPapelYa
No poner computadoras donde no hacen falta. Todavía no podemos ni lograr que estas hagan sólo lo que el dueño quiera.
2
40
45
@dystopiabreaker
I suspect it is hallucinated but it should be easy to trigger it with a fame moon if that is the case
1
0
47
The agile scam: it solves everything if 'properly implemented'
7
13
48
'I was an idiot and assumed that the "random" button on
http://t.co/5BG14kGfwU
was truly random" $20k life lesson
http://t.co/Q4nU2XSWMI
8
64
46
EASTER attack: Even More Critical Bugs in SSL/TLS impl.(Java)
http://t.co/DXOifYTIjX
"only about 73710 queries in mean for a 4096 RSA"
3
93
44
Current Internet threat level after
#ShadowBrokers
dump + Linux UDP RCE
#internetthreatlevel
HIGH RISK
3
37
39
reprogram 4G modems via SMS, make them act as keyboard -> reboot -> act as storage -> install bootkit. 8-o
http://t.co/mcnj0WOLHU
3
69
39
RIP Condor. When I was ~11 years old I collected newspaper clippings about hacking (no Internet yet 👴) and many were about his story (at least a version of it). Around 2002 he emailed me asking for sendmail exploit (
@lcamtuf
bug) Treasured mail, printed and saved but lost now.
We've lost a true pioneer of the digital world, Kevin Mitnick. His ingenuity challenged systems, incited dialogues, and pushed boundaries in cybersecurity. He will remain a testament to the uncharted power of curiosity.
#RIPKevinMitnick
80
861
3K
1
7
39
Hackers having fun with .ar electronic voting system. Cool demo today at Congress (if gov.ar doesn't find a way to cancel or delay it again)
0
28
37
Learn and save the world: The Layman's Guide to IC Reverse Engineering
http://t.co/7SS0d1pJra
0
19
35
"It is worth noting that even though the project was coded in Rust, the audit team found vulnerabilities that resulted in remote code execution and memory corruption." 🎤
Results from Grin's 2nd security audit are now published. A big thanks to
@coinspect
, j01tz, and all the 💛Grin donors💛 who made this work possible. ツ
16
8
46
2
12
36
free crypto course with certificate: Cryptography from
@UofMaryland
on
@Coursera
!
#cryptography
(Sep 15th 8 weeks)
3
22
36
James Iry’s history of programming languages (illustrated with pictures and large fonts)
http://t.co/KTzEmgj4SU
http://t.co/0Vp11pLawb
0
38
35
some believed cryptocurrency incentives were going to make p2p networks like Tor better: "They replaced bitcoin addresses in HTTP traffic to redirect transactions to their wallets instead of the user provided bitcoin address"
2
19
33