Anthony Weems
@amlweems
Followers
3K
Following
1K
Media
8
Statuses
178
Cloud Vulnerability Research • The opinions stated here are my own, not those of my company.
Joined April 2008
Learn how Google CVR could have potentially exfiltrated Gemini 1.0 Pro before launch last year. We describe the vulnz, the fix, and tips for bughunters. Also, shout-out to @epereiralopez for teaming up to adapt this work to another cloud provider.
bughunters.google.com
This blog post describes Google's approach to vulnerability research on our Cloud AI Platform, Vertex AI. We're sharing this so that external researchers can learn from our work and to help them...
Today our Cloud Vulnerability Research (CVR) team shared this research into LLM security, which is broadly applicable to AI domain security practitioners working in this rapidly evolving space. Learn more:
2
16
62
🕺"Leaving tradition" is one of the best parts of Google's security culture and has led to some of the most interesting attack chains I've gotten to work on. There's nothing quite like starting with a blank slate and ending with a root shell.💃.
Celebrating 15 years of password hacking 💻 🔑, Swiss Army knives (and sometimes even chainsaws or swords) included! 😲 . Discover how Google's security teams turn employee farewells into security tests.
0
1
12
Effective today, Google will issue CVEs for critical vulnerabilities in Google Cloud that are fixed internally and do not require customer action or patching.
cloud.google.com
As part of our commitment to security and transparency on vulnerabilities found in our products and services, we now will issue CVEs for critical Google Cloud vulnerabilities.
2
25
84
RT @natashenka: Exciting update on Project Zero’s LLM research:
0
38
0
Before joining Google, I submitted some Cloud bugs to the Google Vulnerability Rewards Program (VRP). Today, we announced a dedicated Cloud VRP and I'm so excited to be a part of the program that got me into Google in the first place. Send us vulnz 🙂.
cloud.google.com
2
12
73
RT @philvenables: Cloud CISO Perspectives Blog for mid-October ‘24 is up covering:. - Sharing AI vulnerability research.- Virtual red teams….
cloud.google.com
We recently found, fixed, and disclosed vulnerabilities in our Vertex AI platform. Google Cloud CISO Phil Venables explains why all AI vendors should share their vulnerability research.
0
5
0
Excited to share this blog post about server-side memory corruption that my team exploited in production. Shout-out to @scannell_simon, @epereiralopez, and @thatjiaozi - this was a very fun project. :-).
bughunters.google.com
In this document, Google's Cloud Vulnerability Research team (CVR) presents vulnerabilities in a third-party JPEG 2000 image library called Kakadu. Exploiting memory corruption vulnerabilities...
0
40
152
RT @offensive_con: The Mines of Kakadûm: Blindly Exploiting Load-Balanced Services by @scannell_simon and @amlweems is now live! https://t.….
0
7
0
RT @scannell_simon: Very excited to present this with @amlweems! See you in Berlin!. (@epereiralopez and @thatjiaozi) were also working on….
0
6
0
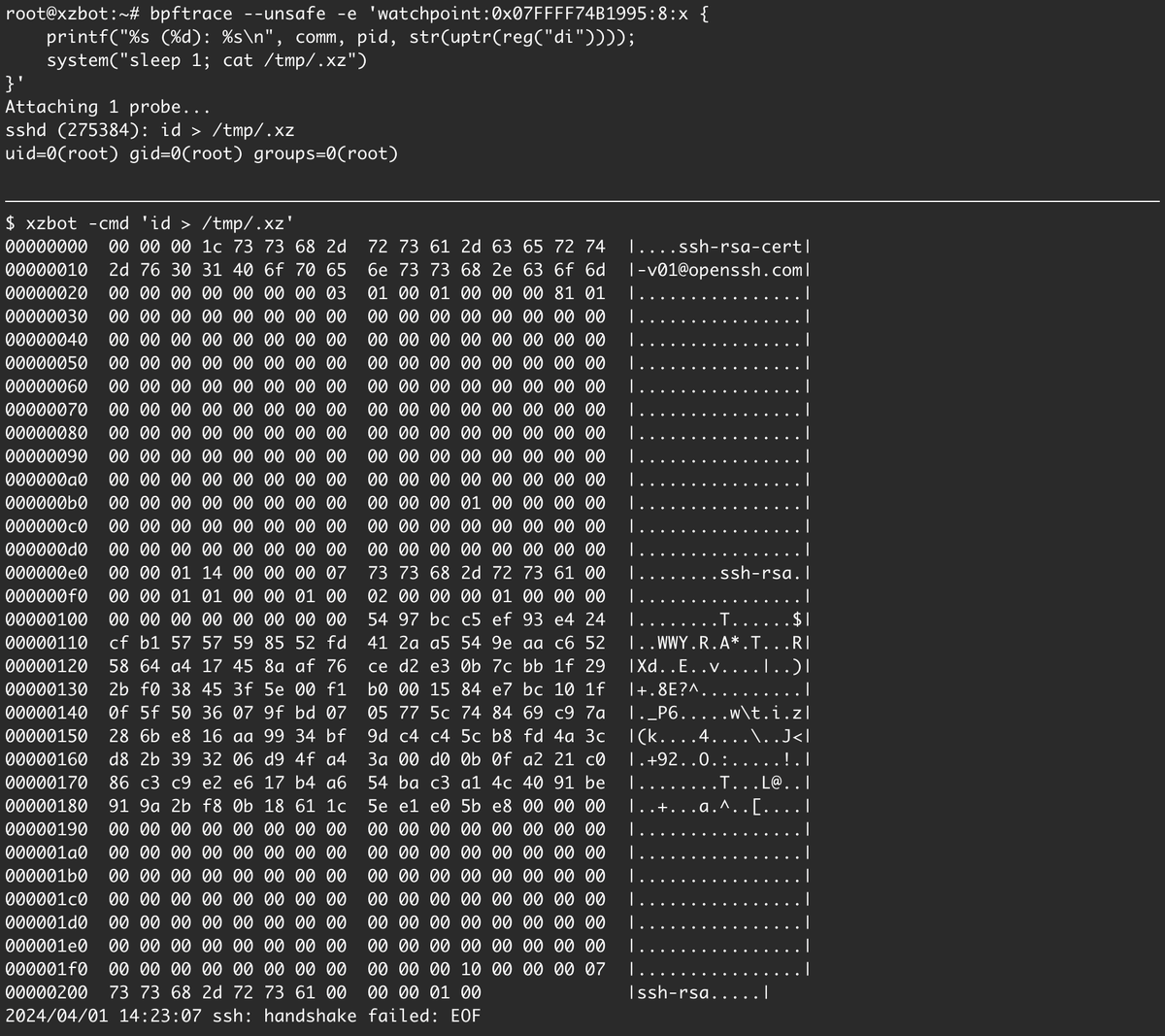
I've been reverse engineering the xz backdoor this weekend and have documented the payload format and written a proof-of-concept exploit for the RCE. The payloads are signed with an ED448 key, so I patched my own key into the backdoor for testing. :-).
51
849
4K
RT @thatjiaozi: Our research on the deep mines of the JPX standard is now public. I had the pleasure and the privi….
github.com
### Summary Rec. ITU-T T.801 | ISO/IEC 15444-2 specifies the JPX file format, which can store images encoded using a variety of image codecs. The Fragment List (flst) box is optional feature of J...
0
6
0
RT @ProjectZeroBugs: containerd: Insecure handling of image volumes
0
22
0
I'm really excited for this video! I got a chance to collab with @LiveOverflow and share the process for discovering the localhost bypass for CVE-2021-45046 with code review and differential fuzzing. :).
After the log4shell vulnerability was patched with version 2.15, another CVE was assigned. Let's have a closer look at the localhost JNDI connections bypass and learn about fuzzing Java applications.
1
2
18
Just finished Portswigger's new Burp Suite Certification. I've always been a huge fan of the @WebSecAcademy and this is an excellent capstone on the labs. Thanks @PortSwigger for all the educational content! #burpsuitecertified.
2
3
54
Thanks for the seamless contribution process! Cheers to @BouncyHat and @dallasl1200 😄.
Thanks to @amlweems, Michael Weber, and Dallas Kaman for performing an analysis on CVE-2021-26855, the Microsoft Exchange SSRF vuln!.
0
0
5
My team @praetorianlabs just published our work in reverse engineering the Proxylogon patches for CVE-2021-26857, CVE-2021-26855, and CVE-2021-27065. I learned a lot more about Exchange than I thought I'd ever need, but had a blast.
praetorian.com
Introduction In recent weeks, Microsoft has detected multiple 0-day exploits being used to attack on-premises versions of Microsoft Exchange Server in a ubiquitous global attack. ProxyLogon is the...
0
5
15
Also, some great new labs on @WebSecAcademy to go along with the research. Thank you for continuing to create free educational content like this.
portswigger.net
In our previous labs, you learned how to exploit web cache poisoning vulnerabilities by manipulating typical unkeyed inputs, such as HTTP headers and ...
1
0
2