Explore tweets tagged as #shellcode
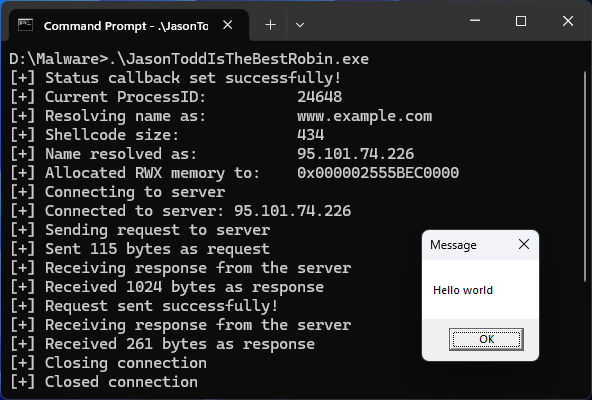
Do you want to trigger shellcode only when:.- Certain DNS resolution happens?.- Certain servers are reached out to?.- When you get a 112 byte long response?. etc. Meet InternetSetStatusCallback() for fine tuning execution (or if you are just bored): .
5
106
445
Exciting times. I'm publishing Dittobytes today after presenting it at @OrangeCon_nl ! . Dittobytes is a true metamorphic cross-compiler aimed at evasion. Use Dittobytes to compile your malware. Each compilation produces unique, functional shellcode.
7
25
83
ShadowPhish - APT Awareness Toolkit. Visual simulator for cybersecurity awareness, phishing, and APT-based social engineering. 🔥 Features.✅ Malicious PDF generator. ✅ Word macro with remote shellcode.✅ PowerShell obfuscation (Base64, IEX, compression, variables).✅ Remote
0
1
11
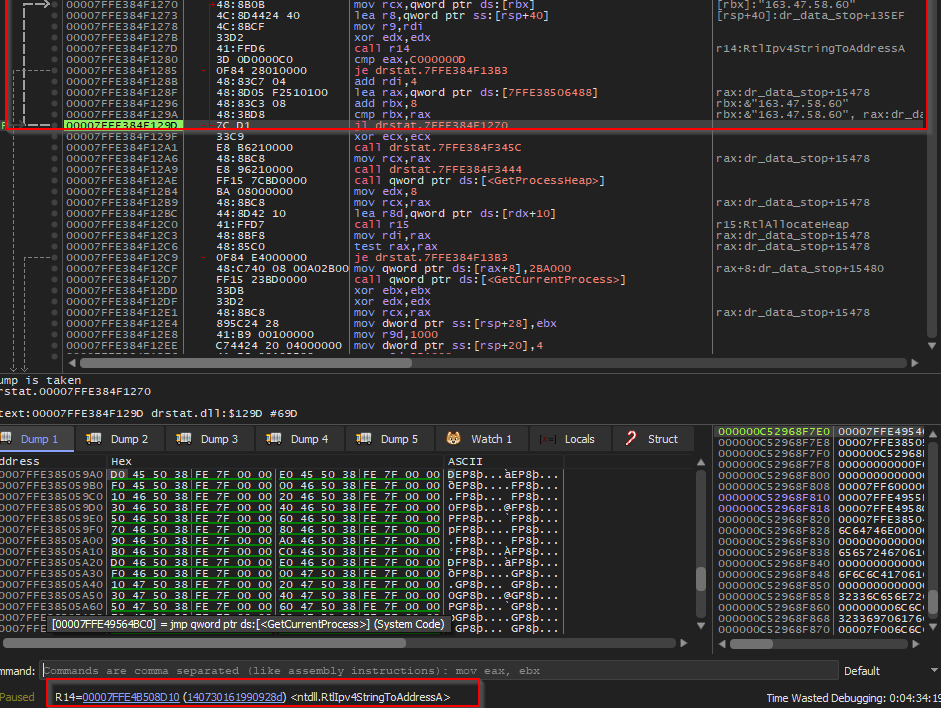
Just checking in: Has anyone talked about using LdrCallEnclave() to run shellcode before?. Technically you can also use CallEnclave() from Vertdll.dll or LdrpIssueEnclaveCall() from Ntdll.dll if you are about that unexported-function life. PoC:
6
58
229
Black Hat Bonus: Learn more about @kyleavery_ 's research on training self-hosted LLMs to generate evasive malware and creation of a 7B parameter model that generates evasive Cobalt Strike shellcode loaders able to bypass Microsoft Defender for Endpoint.
0
47
104
🚨 Underground sale spotted. Threat actor “mock” is selling the source code of a Windows bot for $2,000 on the Russian-speaking underground forum XSS. Below the main points 👇. 💰 Price: $2,000 (escrow available). 🧩 Bot components: Runner, Base, Shellcode, SSH. 🔄 Features:
1
3
9
🔥 Modern Initial Access 2.0 is here🔥. Long-awaited class finally opens for registration, but only three live classes & then it's gone. ✅ Modern Phishing Tactics.✅ Proven Payloads.✅ Effective Shellcode Loaders. ☢️Snatch your seat today:. So excited! 🔥
3
37
197
#ElasticSecurityLabs continues to observe phishing campaigns leveraging Cloudflare tunnels distributing multiple malware families (#VenomRAT, #DCRat, #XWorm) simultaneously. These threat actors are abusing LLMs to produce simple Python shellcode loaders for injection
2
27
119
New Research!. We have found an interesting campaign targeting an entity of Chinese telecom with VELETRIX implant. The implant uses anti-sandbox, shellcode obfuscation technique via IPV4 and execution via EnumCalendarInfo leading to Vshell implant.
4
67
241
NomNom’s gone full beast mode! :-).I've now integrated Havoc C2 into NomNom, I'm very stoked. After execution, it injects shellcode into Notepad to run a Havoc Demon which connects back to the Teamserver. Malware Development is so fun
1
14
113
New outfit.🙂♥️. I’ve never taken a full week off before; but boy was it good.🙂We had a great week with my step kids. Such a fun age.🙂♥️. Back to the grind tomorrow. I’ll be posting about making your own position independent shellcode. I’ll also be finalizing my @defcon
4
1
21
“AlphabeticalPolyGen” - generates and executes a polymorphic shellcode variant of a specified shellcode file:.
1
28
143
🚨#Opendir #Malware🚨. hxxps://144.172.116.103/. ⚠️#zgRat #Stealer.☣️db.exe➡️7fe1fe3722a9aaf4e0b882b574626b1f.📡144.172.116.103:8888. ⚠️#Shellcode autor:@m8sec .☣️huna➡️a267c778f9209c317f2591bfbb9463c9. ⚠️#Shellcode autor:@m8sec .☣️lunacacha➡️d7552e45830440a90ceacec8967e071b
1
5
9
Hey this is super cool, my @Unit42_Intel colleagues released this Malware analysis tutorial featuring Donut Generate Shellcode 🫶 . .
3
63
257
Just released a small project to create multi-bitness x86 shellcode :). Starting bytes as decoded by an x86 processor in IA-32 mode vs. IA-32e mode.
0
26
78
New blog post just dropped!. West Shepherd breaks down extending the Mythic Poseidon agent for ARM64 Dylib injection on Apple Silicon. Details include:. ✅ Shellcode construction.✅ Memory allocation .✅ Runtime patching.✅ Thread creation. Read more ⤵️
5
46
117