m00ndie
@_m00ndie
Followers
402
Following
30K
Media
103
Statuses
2K
Malware Development | Reverse Engineering | Penetration Testing | Red Teaming | Bug Bounty
Accra, Ghana
Joined November 2017
https://t.co/9LxZSQVu3Q next one from my blog. straightforward bind shell for macOS on Apple Silicon. Clean, minimal, no libc. Pure syscall style. #hacking #malware #purpleteam #redteam #blueteam #apple #macos #research #maldev #threatintel #cybersecurity #cybercrime #apt
7
16
47
I've started working on the 2025 edition of "Hacking: The Art of Exploitation", a beginner-friendly guide to binary exploitation. Wish me luck! https://t.co/KnJqHr2yrn
r1ru.github.io
This blog series is still a work in progress. The content may change without notice.
9
95
710
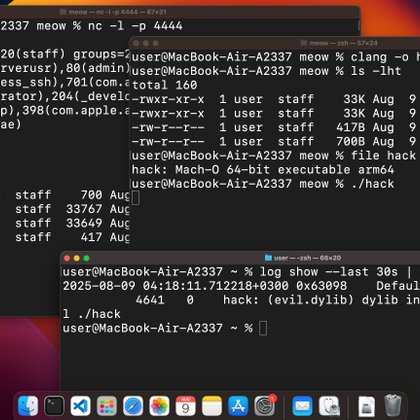
https://t.co/j0YMJPiumX next one from my blog. instead of hijacking an existing thread, we’ll create an entirely new thread in the target process. #malware #cybersecurity #hacking #purpleteam #maldev #cybercrime #asm #apple #macosx #threatintel #research #programming #book
0
2
10
Back to working on NomNom, my ransomware PoC. Currently working on Implementing exfiltrations of keys to a C2 server. The keys were originally saved in a file on disk which isn't the best. Like always, I have a lot of debugging to do :-)
0
0
1
Implemented TLS/SSL in my custom C2 to enable HTTPS communications :-) Used the OpenSSL Library for this
0
0
3
Wanted Raspberry Pi, so I hacked them (reported vuln)... and they sent me all this cool stuff🍓 Thanks @Raspberry_Pi :)
44
44
2K
Doing a bit of learning on the Native Windows API. Thinking of using it in my Ransomware PoC as it’s potentially stealthier and better for evading AVs and EDRs https://t.co/DnnUlKEHk4
0
0
2
Implemented a method in my custom C++ c2 to fetch already stored keys :-). This should be enough for me to continue building my Ransomware PoC I will however be implementing some new functionality soon.
0
0
3
Implementing some anti-debugging techniques in my Ransomware PoC. Instead of using the usual 'IsDebuggerPresent()' which tends to be very suspicious, I implemented my own function. Learning about Windows Internals is definitely paying off :-)
0
0
3
Getting some work done on my custom C2. Just implemented an SQLite database to store encryption keys for later retrieval
1
0
4
Learning about Windows Internals so I can write better and stealthier malware 😇
0
0
2
https://t.co/qHyoWmNnTM next one from my blog. no exploits here - just clean mechanics you can reuse in #redteam/#blueteam practice/#exercises. #cybersecurity #hacking #malware #macos #apple #programming #research #purpleteam #maldev #malwareanalysis #arm #intel
cocomelonc.github.io
﷽
1
34
156
Back to building a light weight C2 for my projects. This time, I'm using Crow, a C++ framework for creating HTTP or Websocket web services. It's really similar to Python's Flask.
0
0
2
Just got another opportunity to mentor hackers in the @thechaincademy Chainkathon starting on the 28th July. We will be supporting brilliant minds, sharing insights, and contributing to groundbreaking projects ! Join as a hacker here https://t.co/9dCu4LX7eO
5
12
88
Working on my last remote buffer overflow exploit before moving on to advanced techniques. Currently looking for bad characters which is giving me some headache :-/
0
0
2
Currently working on another buffer overflow exploit. I'm now fuzzing the application and I was able to overflow the buffer and overwrite the value of EIP
0
1
2
Working on writing an exploit for the Free CD to MP3 application from scratch in python. The screenshot is me controlling EIP to execute shellcode that opens CALC.exe
1
0
4