Explore tweets tagged as #ldap
knew win10 had the dsquery.dll laying around but never knew what to do with it. "rundll32.exe dsquery.dll OpenQueryWindow" will pop open a console for you and you can do some light LDAP recon. you can also open with with win + ctrl + f. probably useful for VDI/Citrix type tests
6
74
363
Powerview 2025.1.5:. Added --obfuscate flag to obfuscate ldap filters and base DN. This is heavily inspired by obfuscation logic by @MacmodSec . Credits to the original research "MaLDAPtive" by @sabi_elezi and @danielhbohannon
1
40
149
To trigger local SYSTEM authentication for relaying to ADCS or LDAP for LPE you would usually need the printer service or EFS service to be enabled (printerbug/petitpotam). Here is an alternative without this requirement 🤠.
3
108
326
🎯 SpearSpray. Advanced password spraying tool for Active Directory environments. Combines LDAP user enumeration with intelligent pattern-based password generation. Uses Kerberos pre-authentication and leverages user-specific data (pwdLastSet, displayName) to create personalized
2
58
250
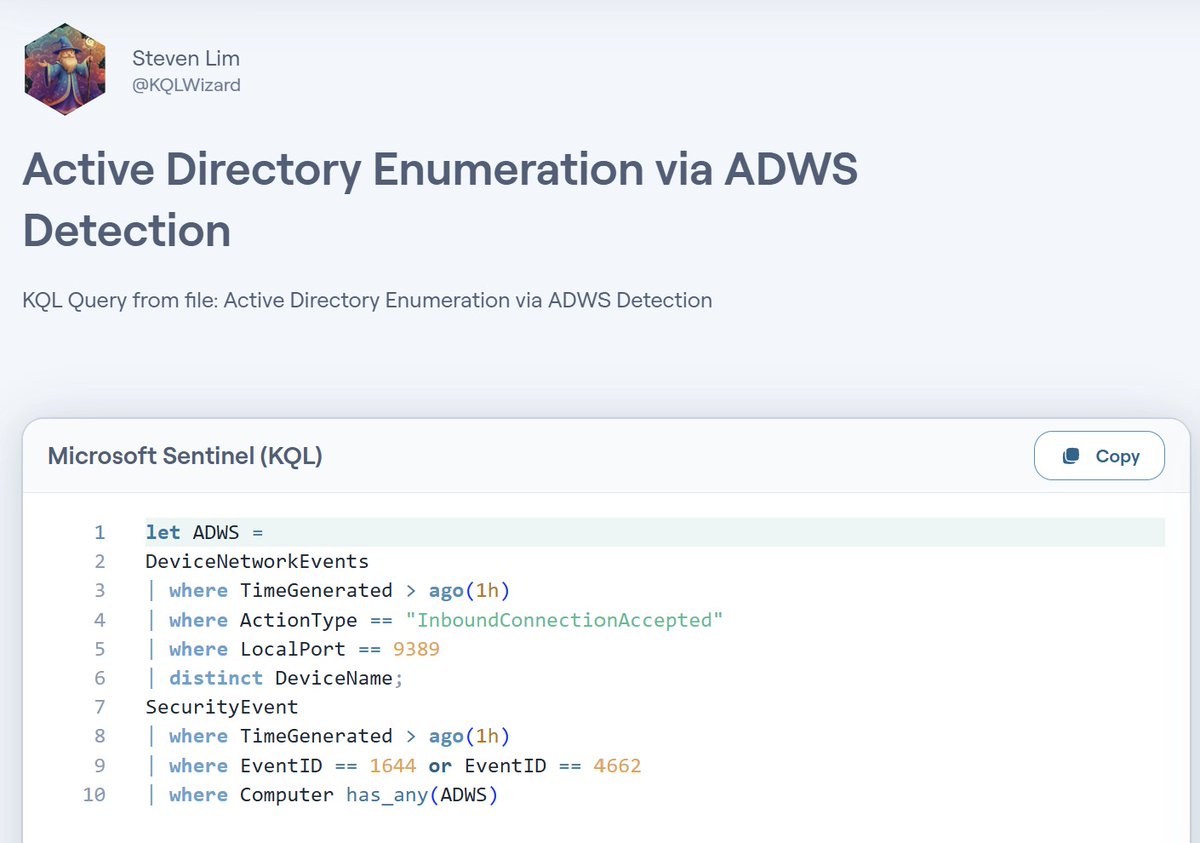
🧵 Red teams are shifting to stealthier AD enumeration via Active Directory Web Services (ADWS) over port 9389. Tools like SOAPHound, SoaPy & ShadowHound wrap LDAP queries in SOAP, bypassing traditional detections. A KQL to detect this type of AD
4
115
496
Operating Outside the Box: NTLM Relaying Low-Privilege HTTP Auth to LDAP.
0
22
135
Why oh why!!! does a build tool need to load code that can speak LDAP and parse ASN.1?.ldd of cmake vs. make.
1
0
5
This is so much! 🔥🔥😎. Found two new Potato triggers just today. Not only Potato but can also be used for LPE as remote auth is done which could be relayed to LDAP without Signing enabled. Or relayed to ADCS for a certificate.
5
181
583
🌟公式Youtubeおすすめ動画🌟. 【LPIC 202】実践LDAPサーバ構築🎥. 📝環境構築+ユーザーの追加と管理. 📝LDAP認証を実装しよう. #エンジニアと繋がりたい #IT転職
0
0
1
🔐 21 (FTP). 22 (SSH). 23 (Telnet).25 (SMTP). 53 (DNS). 80 (HTTP).110 (POP3). 135 (MS RPC). 137–139 (NetBIOS). 143 (IMAP). 161 (SNMP). 389 (LDAP).443 (HTTPS). 445 (SMB). 465 (SMTPS). 500 (IKE),. 514 (Syslog).587 (SMTP Auth). 993 (IMAPS). 995 (POP3S). 1433 (MSSQL)
1
0
2
Oh, that's nice! I've done something similar recently with a vibe coded HTTP proxy server run in context of the target user to access the needed web resource behind domain authentication instead of an LDAP relay 😁
I Just documented a cool way to authenticate proxied tooling to LDAP in an AD environment using C2 payload auth context, without stealing any tickets or hashes! . Keep tooling execution off-host and away from EDR on your Red Team assessments! .
1
31
141
ALAYINIZA, TOPUNUZA GÜNAYDIN ULAN. BÜTÜN DÜŞMANLARLA SAVAŞMAYA UYANDIK ACTIVE DIRECTORY, KERBEROS, LDAP HEPSİYLE ŞU ŞEKİL SAVAŞACAZ GELİN HEPİNİZİ CÜMBÜR CEMAAT DEBUG EDECEM DOMAIN TRUST BEKLE BENİ
3
0
26
🚨🇨🇳 Alleged Sale of Domain Admin Access: China-Based Furniture Company. A threat actor known as shine is allegedly selling SSH, Admin Panel, and Domain Admin LDAP credential access to a major Chinese furniture company with reported revenue of $3 billion. The listing specifies
1
1
12
I just updated SpearSpray, a password spraying tool that generates pattern-based passwords using user-specific info from LDAP. Some key features:.- Kerberos based.- Per-user password logic.- Lockout-aware (badPwdCount), PSO Detection.- Jitter, Threads, Rate Limit. 📽️ Quick demo
3
8
20
Active Directory Hardening Series.Part 1 Disabling NTLMv1 Part 2 Removing SMBv1 Part 3 Enforcing LDAP Signing Part 4 Enforcing AES for Kerberos
3
164
690
SpearSpray - an advanced password spraying tool designed specifically for AD environments. It combines user enumeration via LDAP with intelligent pattern-based password generation to perform controlled and stealthy password spraying attacks over Kerberos.
2
56
202
【公開するなよ】公開されたドメインコントローラ(DC)をDDoSのエージェントにすることが可能な脆弱性、CVE-2025-32724について。SafeBreach社報告。攻撃技法をWin-DDoSと命名。細工されたRPCコールをDCに送り、標的のIPアドレス/ポートにLDAP接続させる。
1
22
91
I Just documented a cool way to authenticate proxied tooling to LDAP in an AD environment using C2 payload auth context, without stealing any tickets or hashes! . Keep tooling execution off-host and away from EDR on your Red Team assessments! .
4
117
397
Trying to fly under EDR's radar?. @_logangoins explains how to use HTTP-to-LDAP relay attacks to execute tooling completely off-host through the C2 payload context. Perfect for when you need LDAP access but want to avoid being caught stealing creds.
2
74
225