Explore tweets tagged as #binaryninja
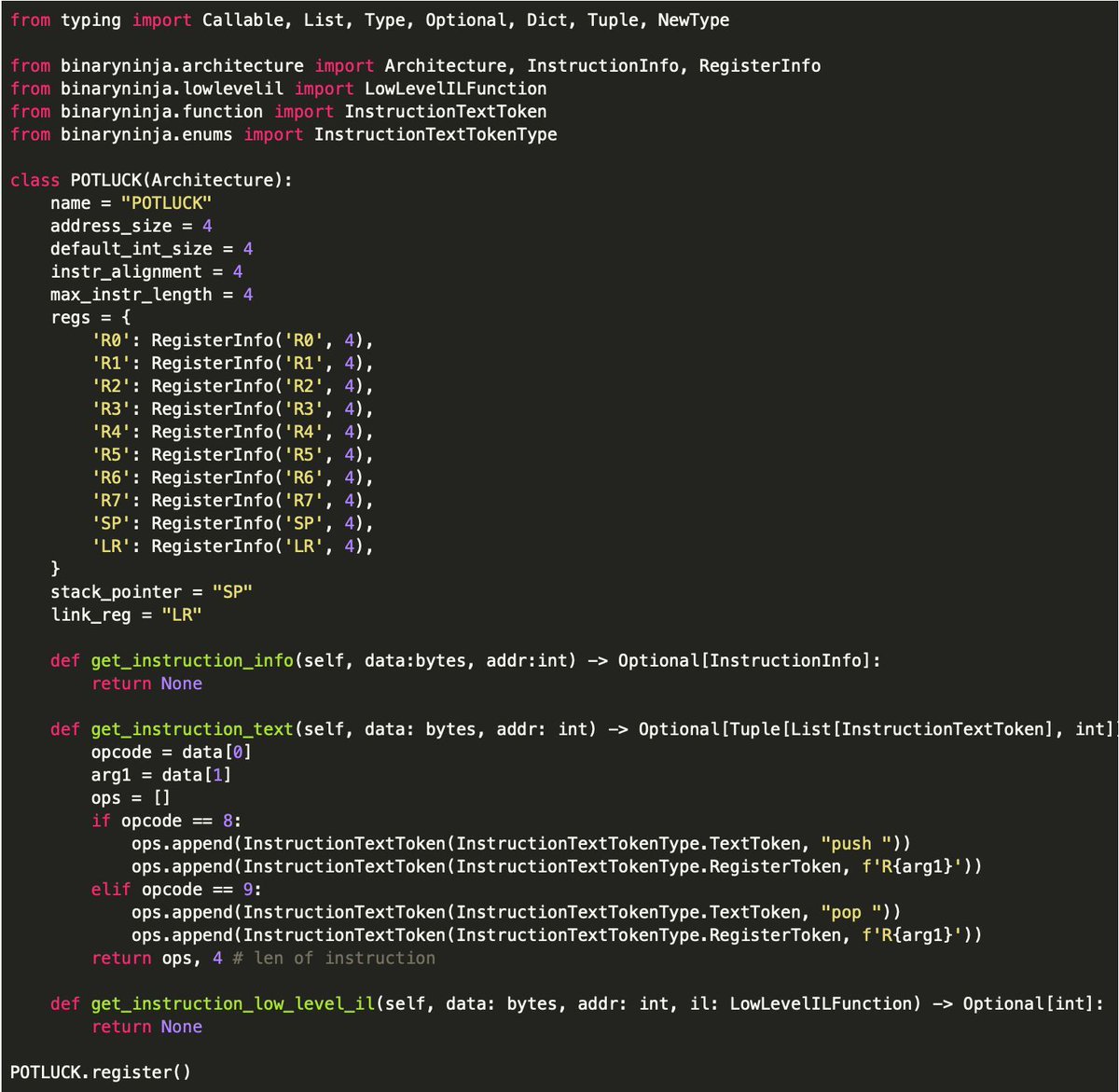
New #BinaryNinja plugin: ReverserAI. It uses local large language models (LLMs) to derive semantically meaningful function names from decompiler output, demonstrating the potential of local LLMs to support reverse engineering on consumer hardware. Link:
1
149
533
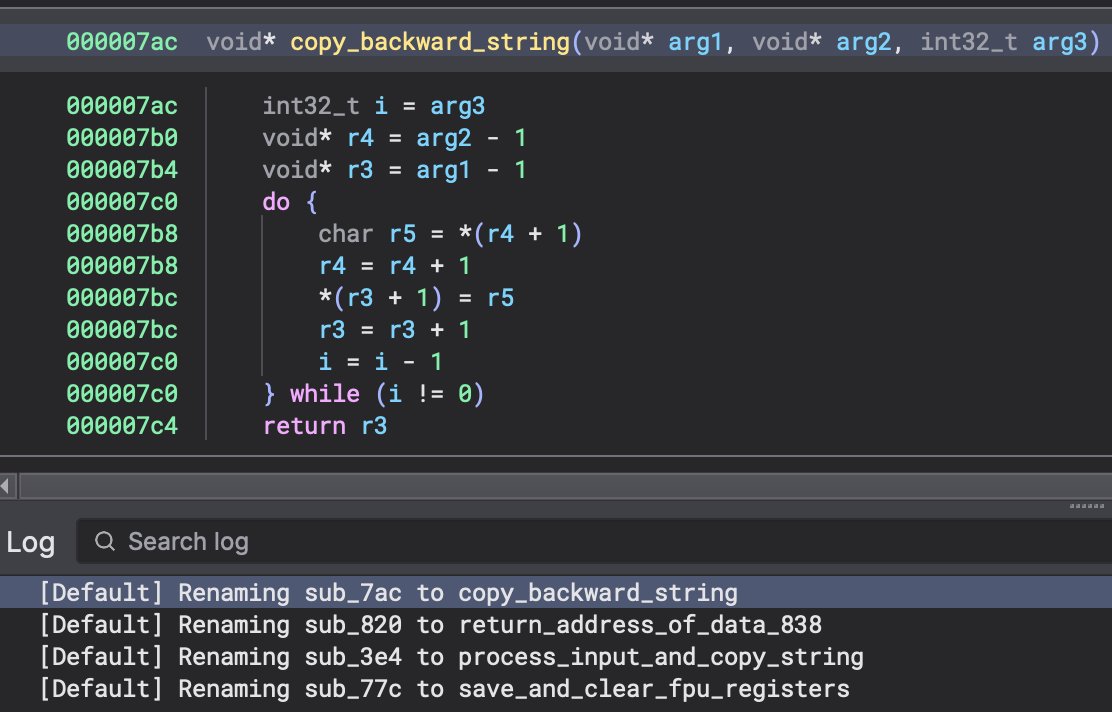
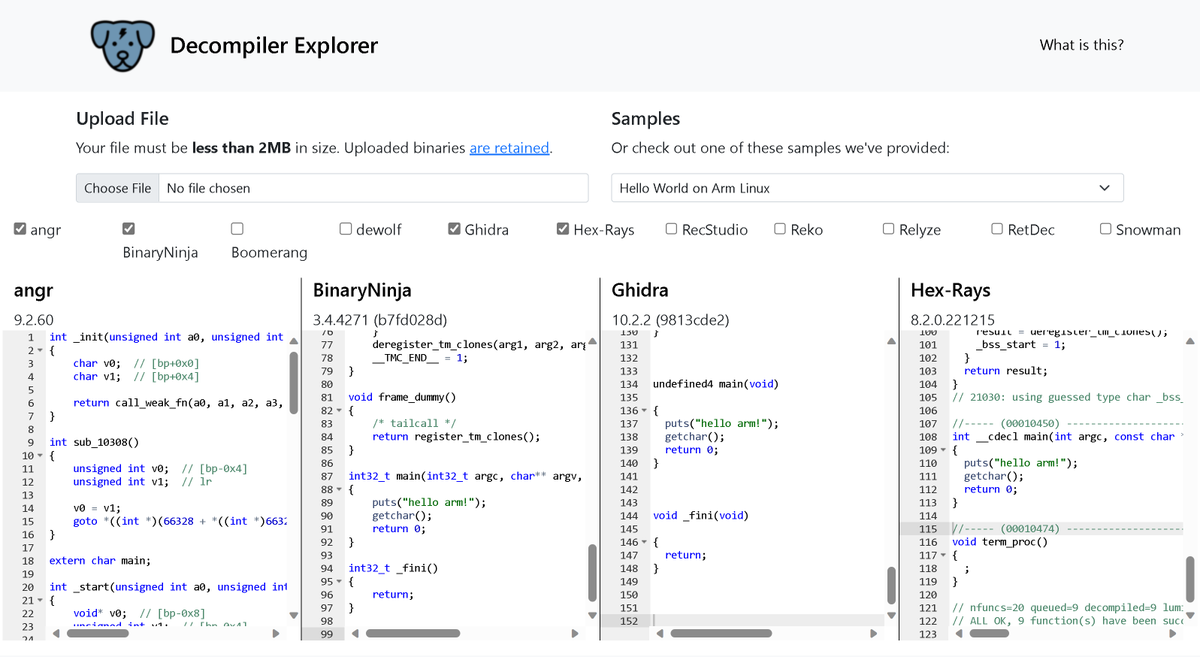
Interesting reading on reversing a custom Instruction Set Architecture (ISA) using Binary Ninja (37C3 CTF).Credits Thomas Imbert (@Synacktiv). #cybersecurity #reverseengineering #binaryninja
2
39
144
🧠 Top Reverse Engineering Tools Every Cybersecurity Researcher Should Know 🔍🛠️. #ReverseEngineering #CyberSecurityTools #InfoSec #MalwareAnalysis #EthicalHacking #Ghidra #IDAPro #BinaryNinja #EducationOnly #RedTeamTools #CyberAwareness
0
0
1
New version of my #binaryninja plugin to detect interesting code in binaries. I've added a new heuristic to detect simple XOR decryption loops. It can identify string decryption routines, code decryption stubs and cryptographic implementations. Code:
2
32
123
New major release of my #BinaryNinja plugin obfuscation_detection: Additional to code detection heuristics to explore unknown binaries, it now also includes analysis helpers such as entropy computation to detect packed/encrypted code & data. Code:
0
24
80
My new blog post introduces a heuristic based on call frequency to identify API functions in statically-linked executables & embedded firmware. It also detects API hashing routines in PlugX malware. Link: #binaryninja plugin:
0
35
102
New #BinaryNinja plugin: Obfuscation Analysis. Simplifies arithmetic obfuscation (MBA) directly in the decompiler (see demo below). Also identifies functions with corrupted disassembly. Co-authored by @nicolodev; available in the plugin manager.
1
45
177
New version of my #binaryninja to identify obfuscated code. Besides major performance improvements it includes a new heuristic to detect frequently called functions which identifies string decryption and API hashing routines in #malware. Code:
1
28
110
#100DaysofYARA Day 19 they're not all winners! But what I love about BinaryNinja is that a lowly analyst like me with no dev experience can create a quick little snippet to try and mine out all unnamed functions as YARA rules. crude: yes.effective: eh? . but have to try it right?
2
5
29
New version of my #BinaryNinja plugin obfuscation_detection. New features detect:.* RC4 implementations (KSA + PRGA).* functions with a high loop frequency (potential performance bottlenecks).* irreducible loops (aggressive optimizations & obfuscation).
0
29
114