Explore tweets tagged as #CyberSecurityTools
🎙️ Following our live podcast launch….🚀 CloudCastle is now officially live on GitHub!. 🙏 To everyone who joined us live — thank you!.💙 Let us know how you’re using CloudCastle. #CloudCastle #SecurityJoes #AWSIR #ThreatHunting #OpenSource #CybersecurityTools
0
0
3
🚀 New Repository Alert! 🐞.I've shared my techniques to bypass 403 and 401 restrictions along with random bug bounty tips and tricks! 🛠️.🔗 Check it out: #bugbountytips #cybersecuritytools @Jayesh25_ @0x0SojalSec @0xTib3rius
1
14
69
🕷️ Nettacker: Open-Source Automated Penetration Testing Framework & Vulnerability Scanner 🔍💻. #Nettacker #OWASP #VulnerabilityScanning #PenetrationTesting #OpenSourceSecurity #CyberSecurityTools #EthicalHacking #InfoSec #RedTeamTools #EducationOnly #VulnerabilityManagement
0
1
5
Lock Down Your Windows Server: Easy Security with Microsoft's Secret Recipe!.#SecurityBaselines #MicrosoftSecurity #WindowsServer #ITPro #CybersecurityTools #PowerShell
0
1
7
🔎 Cybersecurity Search Engines: Recon Starts Here 🧠💻. #CyberSecurityTools #SearchEnginesForHackers #OSINT #ReconTools #EthicalHacking #InfoSec #RedTeam #Shodan #Censys #GreyNoise #EducationOnly #ThreatIntel #OffensiveSecurity
0
0
4
The Cyber Challenge has began. #DaysofCyberSecurity.#30DaysofSecurityWithNetisensICT.#TechWithNetisensICT.#cybersecuritytools
0
1
12
Super pumped about joining @Radiant_Sec .Whole new era of #agenticAI for the modern #SOC.#cybersecuritytools
0
0
0
🧠 Top Reverse Engineering Tools Every Cybersecurity Researcher Should Know 🔍🛠️. #ReverseEngineering #CyberSecurityTools #InfoSec #MalwareAnalysis #EthicalHacking #Ghidra #IDAPro #BinaryNinja #EducationOnly #RedTeamTools #CyberAwareness
0
0
1
From Network mapping to vulnerability scanning, Nmap is an essential tool for every cybersecurity professional. Whether you’re conducting recon, identifying open ports, or testing firewalls, Nmap has got you covered!. #cybersecurity #cybersecuritytools #cybersecuritytechniques
0
0
1
💻 Not all hackers wear hoodies… but they do use these OS!. From Kali Linux to Parrot OS, these are the top operating systems used by ethical hackers and cybersecurity pros. 🔐⚡. Which one’s your go-to tool? 👇. #HackersOS #CyberSecurityTools #KaliLinux #ParrotOS
4
3
13
🔍 Dive into the world of reconnaissance with these 8 powerful tools! From port scanning to information gathering, they uncover hidden gems. Discover their unique purposes and level up your security assessments. #Reconnaissance #CyberSecurityTools #InfoSec #cybersecurity
1
0
3
ControlCase’s Cybersecurity Certification Finder Tool will help you initiate the first steps toward IT certification and navigate your journey to compliance adoption success. Take the short online assessment today. #ControlCase #cybersecuritytools
0
0
0
Have you ever used @torproject browser❓. #onlineprivacy #PrivacyMatters #CyberSec #cybersecuritytools #zelena #chailenzo #sstvi #zeudi #tommavi #helevier
1
2
6
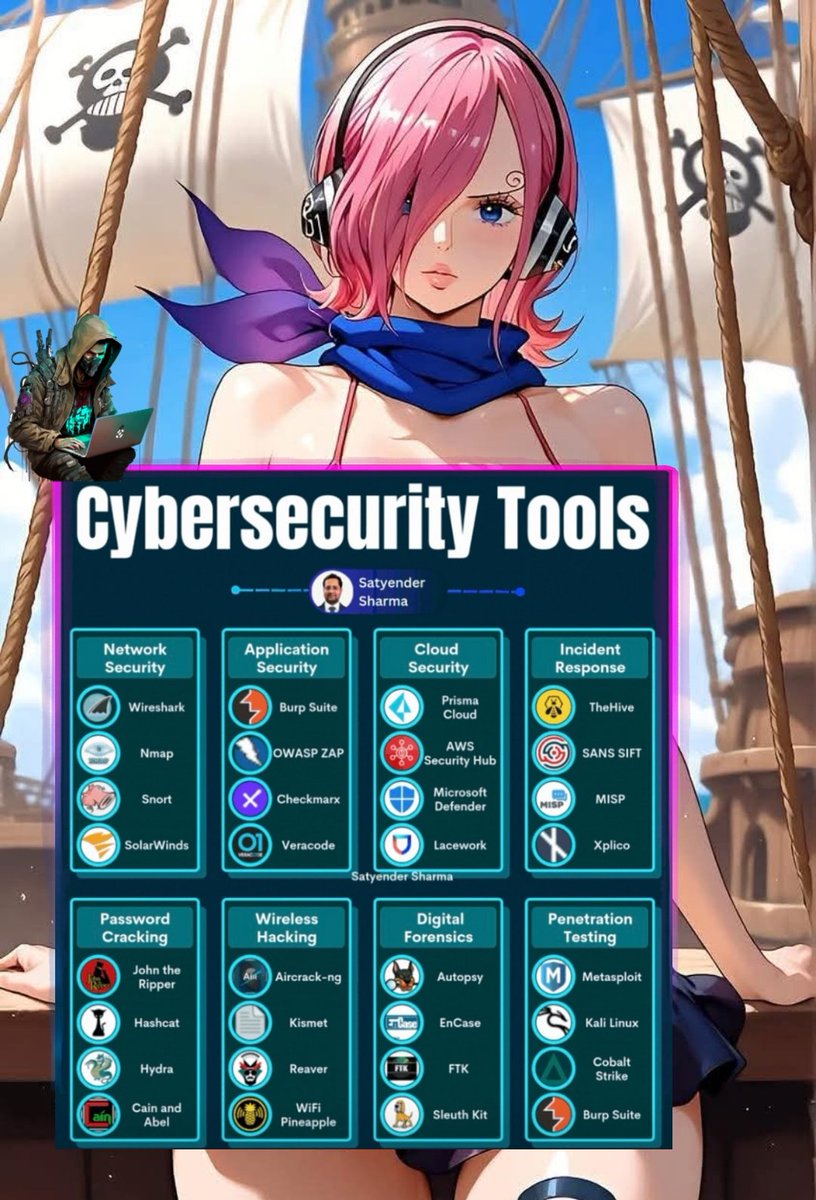
Cybersecurity Tools You Should Know 🔥🛡️💻. #CyberSecurityTools #EthicalHacking #InfoSec #RedTeam #BlueTeam #EducationOnly #SecurityToolkit #PenTestReady #CyberSkills
0
0
2
Testing password strength made easy with John the Ripper, because secure systems start with secure passwords. #CyberSecurity #EthicalHacking #cybersecuritytools #cyberday #cyber #cyberawareness
0
0
5
Got the new-age #cybersecuritytools, talent & resources—so why the #securitygaps? .It’s all about integration. In Edition 1 of our new series, Pavel Shepetina explores the hidden cost of misconfigurations & how to avoid them. Read now:
0
6
14
Protocols and Servers-. there are many different protocols and servers that are widely used, lets take a look. #100DaysOfHacking #buildinpublic #letsconnect #cybersecuritytools #Thread
1
0
4